访问今麦郎饮品有限公司官网,http://www.jmlyp.com/,右上角信息门户系统。
http://home.jmlyp.com/login/Login.jsp?logintype=1
登陆页面测试一下是否有注入,然后跳转到存在注入页面;
http://home.jmlyp.com/wui/theme/ecology7/page/login.jsp?templateId=101&logintype=1&gopage=&languageid=7&message=55
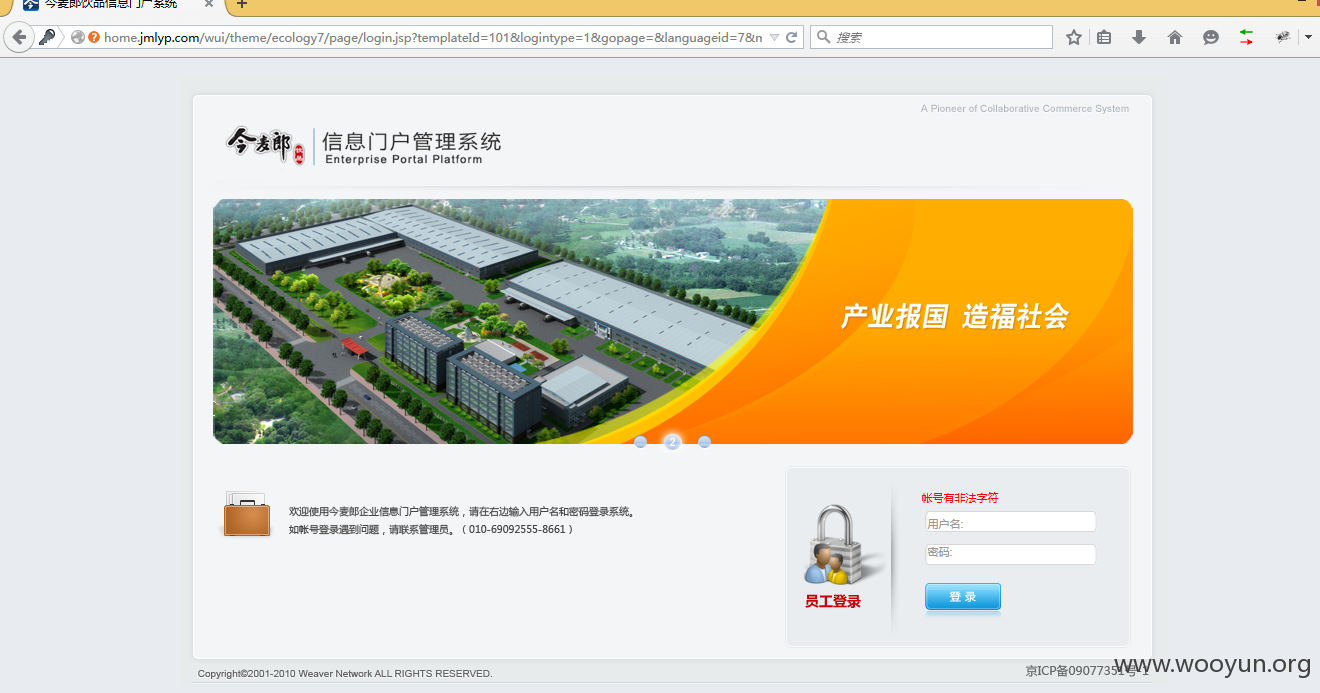
用的系统实际是泛微E-COLOGY,templateId参数存在SQL注入,直接放到sqlmap里面跑即可。
oracle盲注,跑起来很慢。
sqlmap信息。dba权限,Oracle Database 10g Enterprise Edition Release 10.2.0.1.0 - 64bi版本,
database management system users
数据库信息,后面没再跑,太慢了
验证到此为止,应该可以说明问题了




