漏洞概要
关注数(24)
关注此漏洞
漏洞标题:留了一年的中科院分站注射
提交时间:2012-11-16 11:53
修复时间:2012-12-31 11:53
公开时间:2012-12-31 11:53
漏洞类型:SQL注射漏洞
危害等级:中
自评Rank:5
漏洞状态:已交由第三方合作机构(cncert国家互联网应急中心)处理
Tags标签:
无
漏洞详情
披露状态:
2012-11-16: 细节已通知厂商并且等待厂商处理中
2012-11-20: 厂商已经确认,细节仅向厂商公开
2012-11-30: 细节向核心白帽子及相关领域专家公开
2012-12-10: 细节向普通白帽子公开
2012-12-20: 细节向实习白帽子公开
2012-12-31: 细节向公众公开
简要描述:
刚翻出来的,看了文件时间,一年零6天。
现在服务器装有安全狗...安全狗...全狗...狗.....
哇咔咔。还是能射的
详细说明:
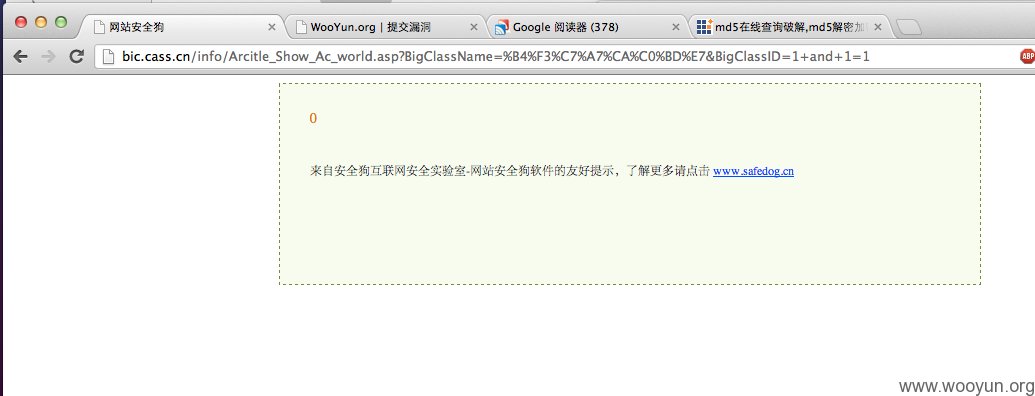
安全狗
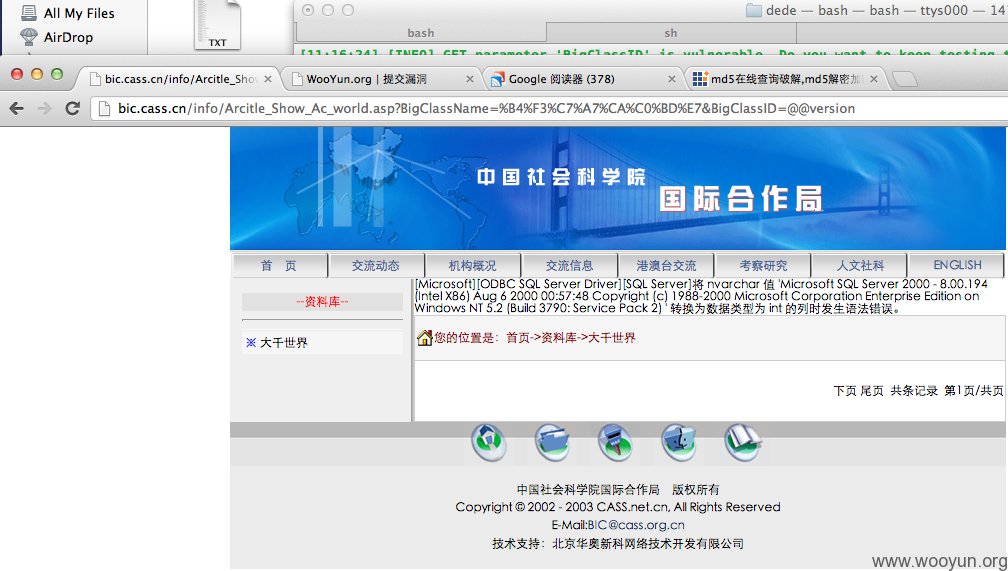
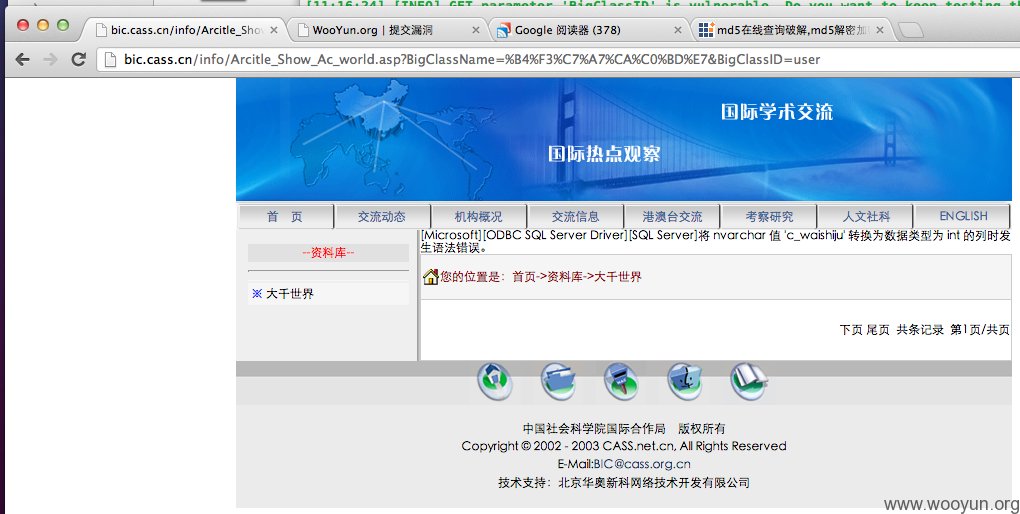
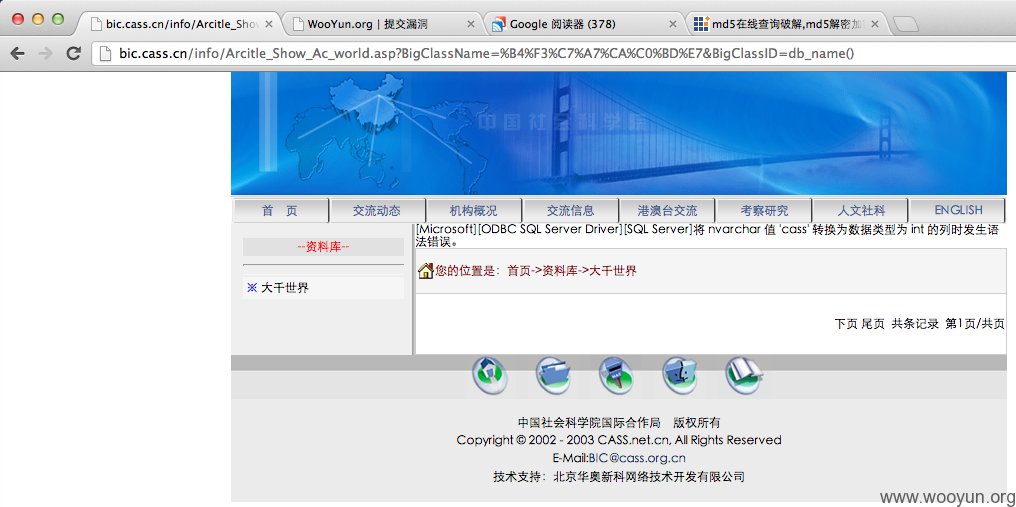
漏洞证明:
详细说明里贴图了
修复方案:
版权声明:转载请注明来源 Wdot@乌云
漏洞回应
厂商回应:
危害等级:中
漏洞Rank:8
确认时间:2012-11-20 13:43
厂商回复:
CNVD确认漏洞风险点,可以实施注入得到后台数据库实例信息,近几日暂未手工测试未进得到进一步可渗透结果,转由CNVD直接联系网站管理方处置。
按部分影响机密性进行评分,基本危害评分4.96(中),技术发现难度系数1.3,涉及行业或单位影响系数1.3(注:为社科院,非中科院),综合rank=4.96*1.3*1.3=8.382
最新状态:
暂无






