中兴通创业于1994年,经过21年不懈努力,现已成为具有一定规模的综合性企业集团。截至2015年中,中兴通持有2家新三板上市企业,拥有净资产约40亿元,在北京等地拥有3万平方米物业,员工约六百人。
随着互联网革命的深入,中兴通再度拥抱变革,重踏创业之路。在做优做强财税信息化的基础之上,集团内升外延,战略性的布局互联网+经营,形成了一体(互联网+经营)两翼(股权投资和物业经营),三轮驱动的全新发展格局。
互联网+经营代表着中兴通的战略转型方向,包括中兴通财税、中兴通金融、互联网+诚信体系和网商创业孵化等板块。依托百万家税务企业客户资源,中兴通通过服务升级继续深耕财税信息化领域,并面向中小企业客户推出金融服务,帮助企业成长发展,形成财税与金融的良性互补。在多年从事密码服务的基础之上,中兴通推出旨在推广正品和诚信服务的德码平台,并通过创业孵化培育平台卖家,进而打造本土化电子商务生态圈-德码圈。
中和致远,兴业通达。达则兼济天下。回顾历史,中兴通的每一步发展,都以拥抱时代为主题,都以贡献社会为目标。展望未来,中兴通将坚持初心不改,变中求进,为成为永续经营、奉献社会的百年企业而不懈努力!
漏洞网站:http://yfgl.chinazxt.com
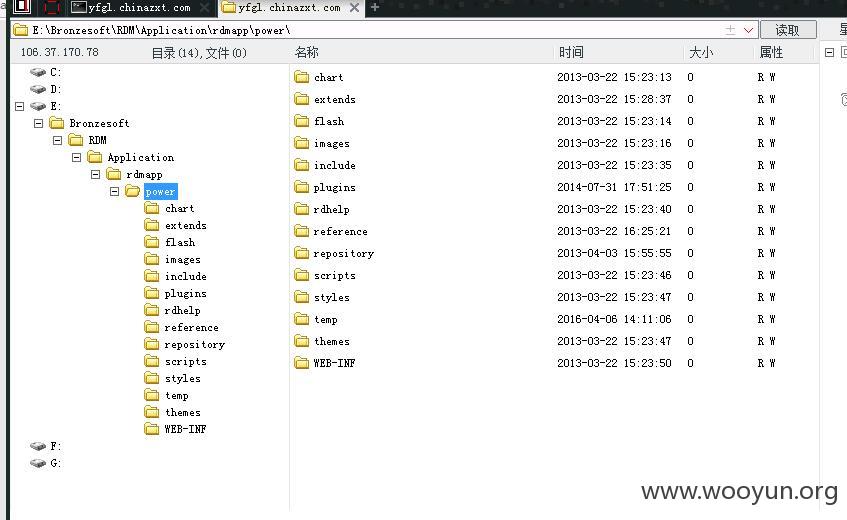
为RDP系统,里面有多个重要内部资料。GETSHELL
base64后的自定义目录和上传后的文件名,代码生成的文件名是一串uuid
构建语句:
得到上传文件
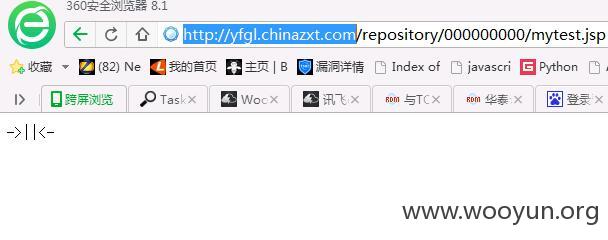
http://yfgl.chinazxt.com/repository/000000000/mytest.jsp
威胁内网安全
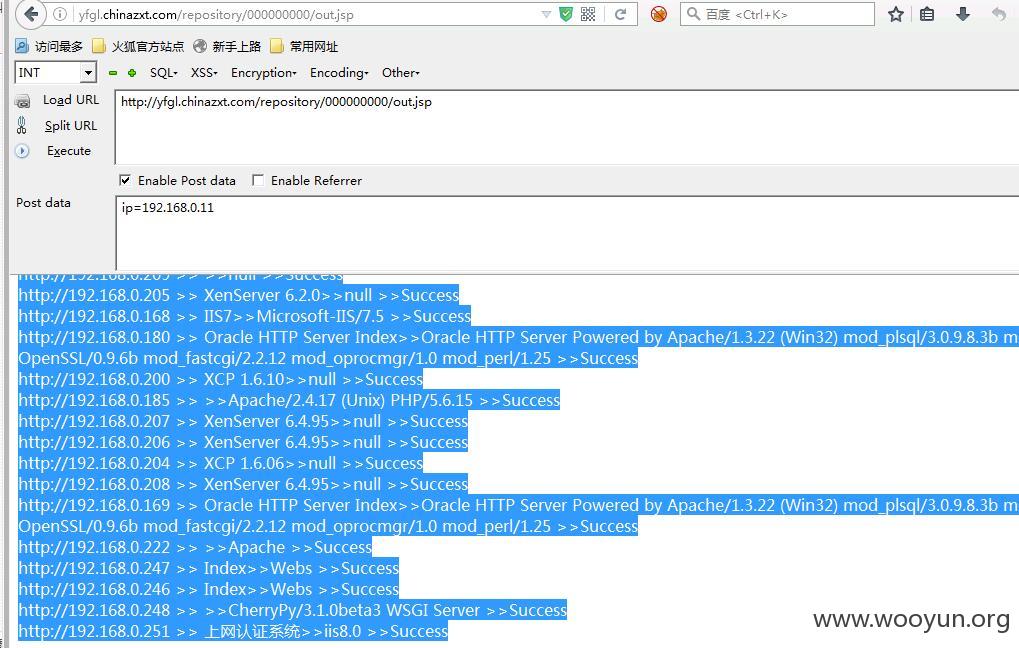
威胁内网多个系统:
漏洞网站:http://yfgl.chinazxt.com
为RDP系统,里面有多个重要内部资料。GETSHELL
base64后的自定义目录和上传后的文件名,代码生成的文件名是一串uuid
构建语句:
得到上传文件

http://yfgl.chinazxt.com/repository/000000000/mytest.jsp
威胁内网安全

威胁内网多个系统:






