这里为了保护厂商知识产权,隐去大部分代码
漏洞利用前提:
1、有登陆SSL VPN控制台的权限
2、可以SSL VPN修改邮件服务器配置
问题出在sysCfgController.class.php 147行(邮件服务器设置的发送测试邮件功能)
file_put_contents在file_exists前执行,而$conf_file来源于cookie参数sinfor_session_id
那么我们提交的时候修改cookie sinfor_session_id为:
即可在/tmp/目录下创建一个1.txt文件
如何getshell呢?向web根目录下写个php就行了呀
但这里会碰到问题:新建的文件权限是-rw-------,也就是说web容器不能执行新建的文件
为了突破这个问题,需要覆盖掉一个已存在的php文件,利用其x权限来达到getshell的目的
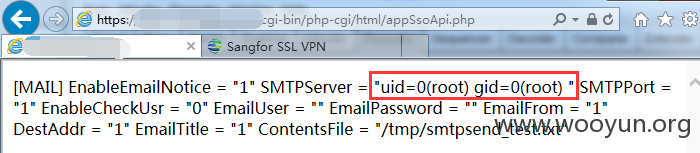
就拿这个php开刀吧:/app/usr/sbin/webui/html/appSsoApi.php
那么将cookie sinfor_session_id修改为:
注意!此操作会覆盖上面的php文件
最终POC:
提交后访问https://***/cgi-bin/php-cgi/html/appSsoApi.php,可看到php代码执行: