漏洞概要
关注数(24)
关注此漏洞
漏洞标题:宜搜多台服务器沦陷
提交时间:2015-01-16 11:52
修复时间:2015-03-02 11:54
公开时间:2015-03-02 11:54
漏洞类型:系统/服务运维配置不当
危害等级:高
自评Rank:20
漏洞状态:厂商已经确认
Tags标签:
无
漏洞详情
披露状态:
2015-01-16: 细节已通知厂商并且等待厂商处理中
2015-01-16: 厂商已经确认,细节仅向厂商公开
2015-01-26: 细节向核心白帽子及相关领域专家公开
2015-02-05: 细节向普通白帽子公开
2015-02-15: 细节向实习白帽子公开
2015-03-02: 细节向公众公开
简要描述:
早些时候的漏洞补丁不及时,getshell and getsystemroot,后期运维检查不到位,一直没发现。
详细说明:
早些时候 www2.easou.com s2漏洞 getshell 获取root权限
翻看.ssh/ 目录下文件 破解shadow文件,普通用户密码通用,成功登录多台服务器,由于内核版本过低,均成功提权。
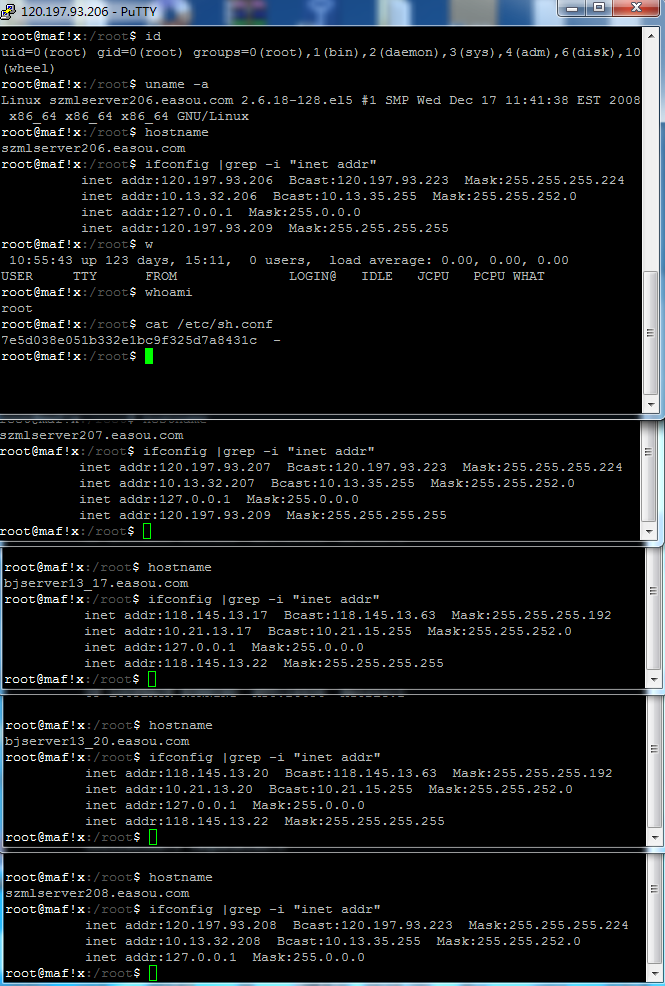
涉及到机器:
root@maf!x:/root$ hostname
szmlserver208.easou.com
root@maf!x:/root$ ifconfig |grep -i "inet addr"
inet addr:120.197.93.208 Bcast:120.197.93.223 Mask:255.255.255.224
inet addr:10.13.32.208 Bcast:10.13.35.255 Mask:255.255.252.0
inet addr:127.0.0.1 Mask:255.0.0.0
root@maf!x:/root$ hostname
bjserver13_20.easou.com
root@maf!x:/root$ ifconfig |grep -i "inet addr"
inet addr:118.145.13.20 Bcast:118.145.13.63 Mask:255.255.255.192
inet addr:10.21.13.20 Bcast:10.21.15.255 Mask:255.255.252.0
inet addr:127.0.0.1 Mask:255.0.0.0
inet addr:118.145.13.22 Mask:255.255.255.255
root@maf!x:/root$ hostname
bjserver13_17.easou.com
root@maf!x:/root$ ifconfig |grep -i "inet addr"
inet addr:118.145.13.17 Bcast:118.145.13.63 Mask:255.255.255.192
inet addr:10.21.13.17 Bcast:10.21.15.255 Mask:255.255.252.0
inet addr:127.0.0.1 Mask:255.0.0.0
inet addr:118.145.13.22 Mask:255.255.255.255
root@maf!x:/root$ hostname
szmlserver207.easou.com
root@maf!x:/root$ ifconfig |grep -i "inet addr"
inet addr:120.197.93.207 Bcast:120.197.93.223 Mask:255.255.255.224
inet addr:10.13.32.207 Bcast:10.13.35.255 Mask:255.255.252.0
inet addr:127.0.0.1 Mask:255.0.0.0
inet addr:120.197.93.209 Mask:255.255.255.255
root@maf!x:/root$ hostname
szmlserver206.easou.com
root@maf!x:/root$ ifconfig |grep -i "inet addr"
inet addr:120.197.93.206 Bcast:120.197.93.223 Mask:255.255.255.224
inet addr:10.13.32.206 Bcast:10.13.35.255 Mask:255.255.252.0
inet addr:127.0.0.1 Mask:255.0.0.0
inet addr:120.197.93.209 Mask:255.255.255.255
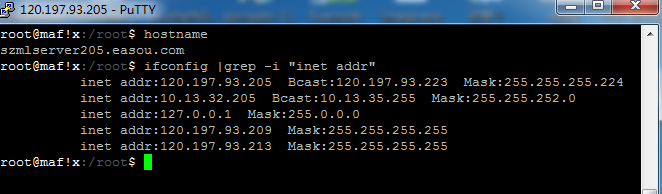
root@maf!x:/root$ hostname
szmlserver205.easou.com
root@maf!x:/root$ ifconfig |grep -i "inet addr"
inet addr:120.197.93.205 Bcast:120.197.93.223 Mask:255.255.255.224
inet addr:10.13.32.205 Bcast:10.13.35.255 Mask:255.255.252.0
inet addr:127.0.0.1 Mask:255.0.0.0
inet addr:120.197.93.209 Mask:255.255.255.255
inet addr:120.197.93.213 Mask:255.255.255.255
内核版本:rhel4 2.6.18-128.el5
漏洞证明:
共计6台服务器:
120.197.93.208 19643 root:asdfasdfasdfasdfasdfasdf
120.197.93.205 6033 root:whoami.so
118.145.13.20 6033 root:whoami.so
118.145.13.17 6033 root:whoami.so
120.197.93.206 6033 root:whoami.so
120.197.93.207 6033 root:whoami.so
修复方案:
修改弱口令,升级服务器内核 清除后门 rkclean 附上脚本
这其实也是一种提示,漏洞修复后,要进行深入检查(服务器有没有被提权,有没有殃及其他服务及应用 是否会引起连锁反应?)。
版权声明:转载请注明来源 我了个去@乌云
漏洞回应
厂商回应:
危害等级:高
漏洞Rank:15
确认时间:2015-01-16 11:56
厂商回复:
谢谢指出,我们会及时改正
最新状态:
暂无




