今天闲的蛋蛋疼,看了ChinaGFW.Org的一篇老文章,发现了几个牛逼的IP地址
219.142.121.211 —— Ministry-Of-Public-Security-Information-Communication-Agency
222.66.235.172 —— BAOSHAN-POLICE
121.10.215.35 以及 218.66.36.226
这些牛逼的IP地址有什么特点呢?
统一为 en-us
不过当我看到第一个IP地址的WHOIS信息居然为Ministry-Of-Public-Security-Information-Communication-Agency的时候,我——震惊了。
收好震碎的蛋,拿起了古董箱里的X-Scan对219.142.121.208 - 219.142.121.223一顿扫描过后,得到了一个牛逼的IP地址219.142.121.212
这个IP地址开了80端口,23端口,于是在web端尝试了admin / admin成功了(密码我改成了admin / admins 因为让别人帮忙渗透结果他乱发密码来的~)
于是尽最大可能收集信息

(这个看起来像采集中心服务器的IP地址,不过因为对这种协议不太了解,无法进行下一步渗透)
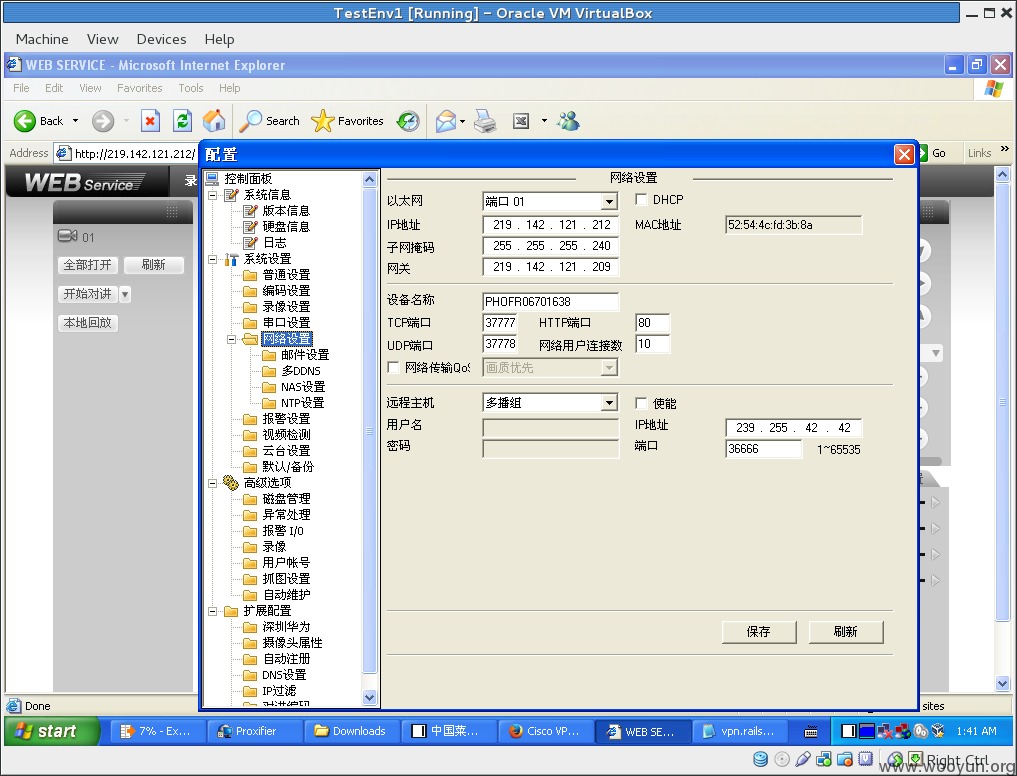
(网关地址)
然后又尝试对telnet端口进行进入,试了admin/admin admin/12345 admin/123456
admin/[null] 都不对,怎么办呢?既然连web默认口令都没改肯定是telnet都没改,那么来找下厂家~
打开web后,查看源代码,居然连个copyright都没有,js文件中注释里也没有copyright,这厂商是多么的大无畏精神啊~
突然想起,加载这个监控系统要一个ActiveX插件,那么来看看插件名称吧~
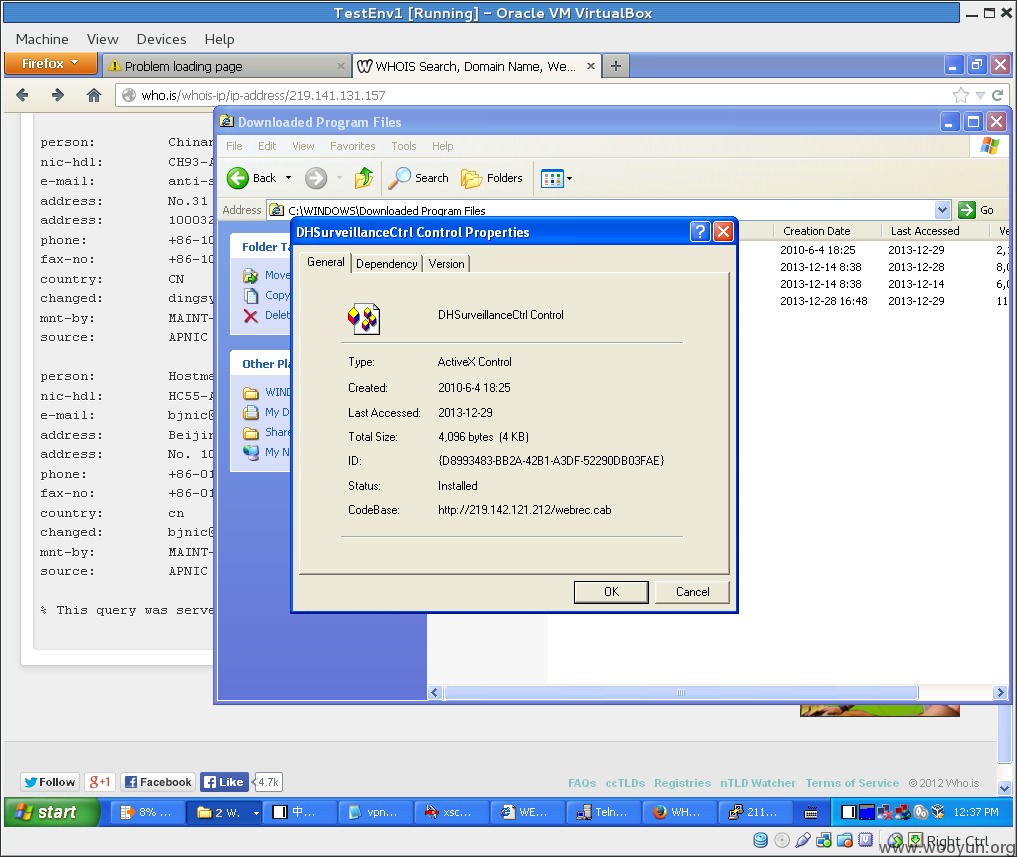
谷歌了一下DHSurveillanceCtrl居然没有,于是又谷歌了一下webrec.cab
根据谷歌牛逼的结果,老夫找到了该监控系统叫大华硬盘录像机
也找到了密码 用户名:root 密码:vizxv
多么牛逼的密码?还好当初老夫没爆破,不然这辈子也破不开。
于是果断尝试ssh转发,弹出了ssh命令不存在,不过老夫也没很震惊,因为这种busybox-based系统很少有ssh命令,于是老夫又进行了
于是netstat -l 没开ftp端口,之后
telnet x.x.x.x >> /tmp/1.sh , wget , ftp , curl , scp , ………… 最终在尝试tftp的时候终于有了反应,诶?怎么是系统信息。
之后才发现busybox可以看指定的函数的。。
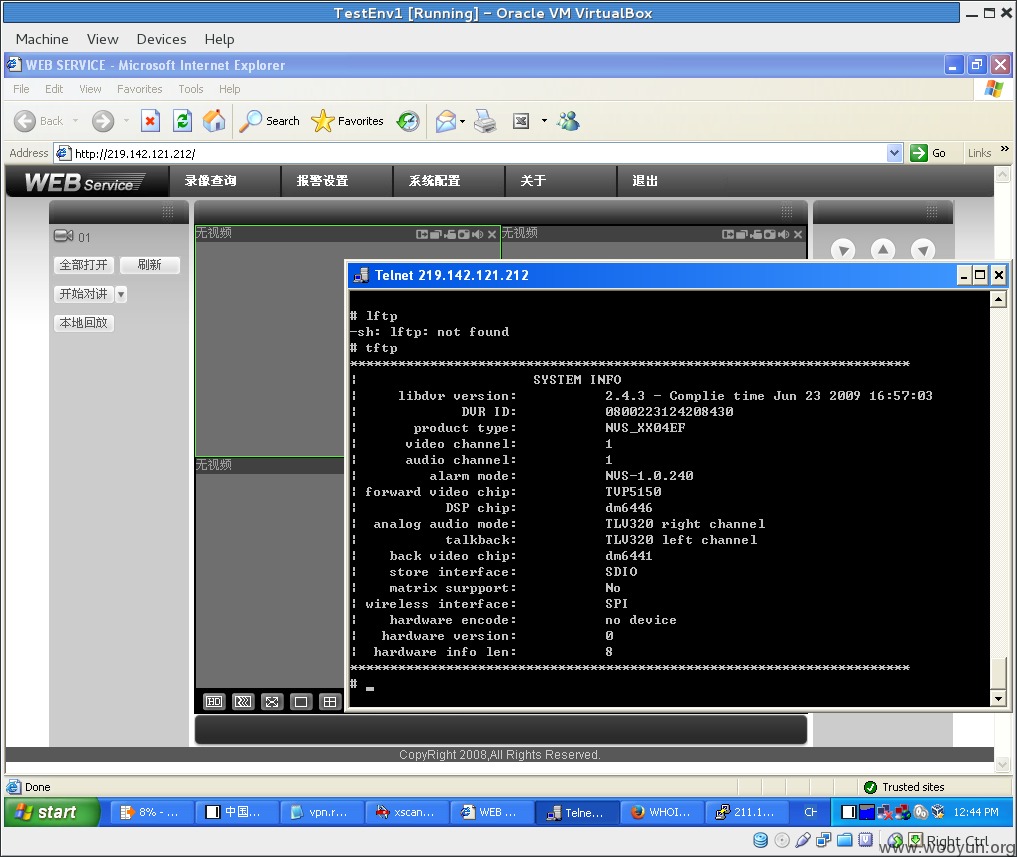
不管了,先找个服务器搭建个tftp
搭建好之后,tftp获取ssh以及ssh_config,诶?还是系统信息,看来这个tftp是被阉割过了。
怎么办呢?凉拌炒鸡蛋吧~
之后又收集了一圈信息
# cat Account1
// 默认的帐户配置,默认的组包含组名和组描述等必填项,默认的用户包含用户名,用户
// 描述,所属组名,密码,是否共享等必填项。default用户不用写在下表中。
{
密码不知什么方式加密的
看起来这个出口是直接接入电信骨干网的
公安部,你为何这么屌?






