漏洞概要 关注数(24) 关注此漏洞
缺陷编号:wooyun-2016-0208983
漏洞标题:wiz笔记泄漏信息之空中网某站数据库泄露
相关厂商:空中网
漏洞作者: 我在不想理你
提交时间:2016-05-20 18:16
修复时间:2016-07-07 15:40
公开时间:2016-07-07 15:40
漏洞类型:系统/服务运维配置不当
危害等级:中
自评Rank:5
漏洞状态:厂商已经确认
漏洞来源: http://www.wooyun.org,如有疑问或需要帮助请联系 [email protected]
Tags标签: 无
漏洞详情
披露状态:
2016-05-20: 细节已通知厂商并且等待厂商处理中
2016-05-23: 厂商已经确认,细节仅向厂商公开
2016-06-02: 细节向核心白帽子及相关领域专家公开
2016-06-12: 细节向普通白帽子公开
2016-06-22: 细节向实习白帽子公开
2016-07-07: 细节向公众公开
简要描述:
程序员的错,不要把敏感信息存在云笔记不加密!!!
详细说明:
http://wooyun.org/bugs/wooyun-2016-0205007
利用撞出来的帐号登陆
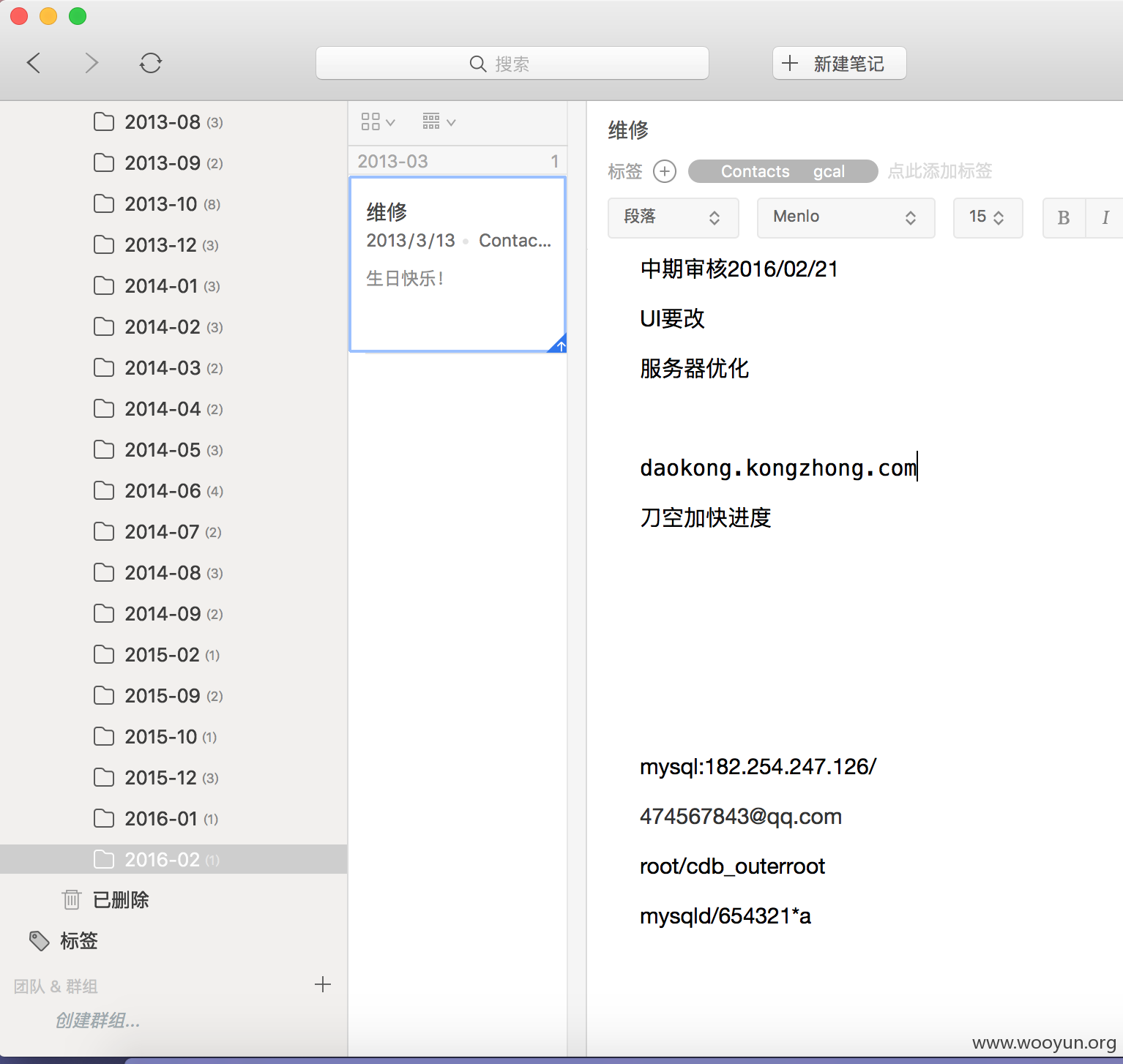
看了看,有个笔记比较新,吸引人
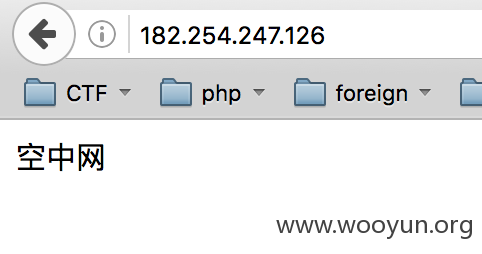
看到了配置信息,是空中网的子站,访问182.254.247.126
百度了下空中网
流量挺大
root无法远程登陆
试试看另一个帐号
成功登陆了
漏洞证明:
但是无法查看内容
修复方案:
敏感信息加密存放
版权声明:转载请注明来源 我在不想理你@乌云
漏洞回应
厂商回应:
危害等级:低
漏洞Rank:5
确认时间:2016-05-23 15:34
厂商回复:
合作商业务,已经通知相关部门处理,谢谢关注。
最新状态:
暂无