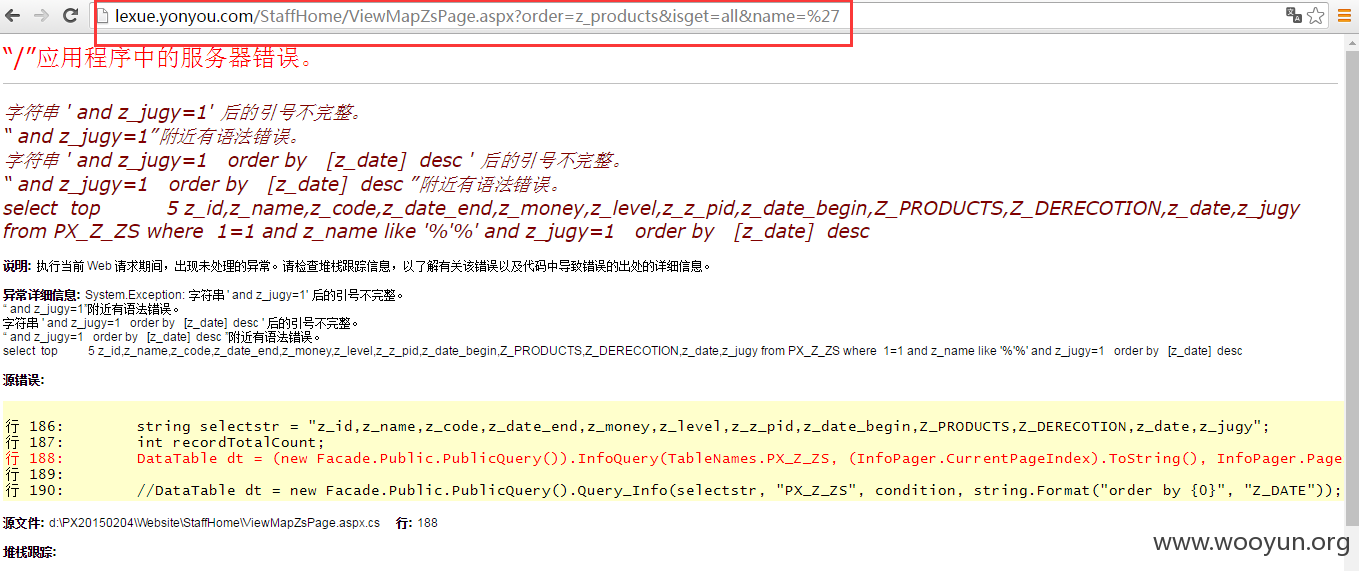
3.个人资料头像处存在文件任意上传
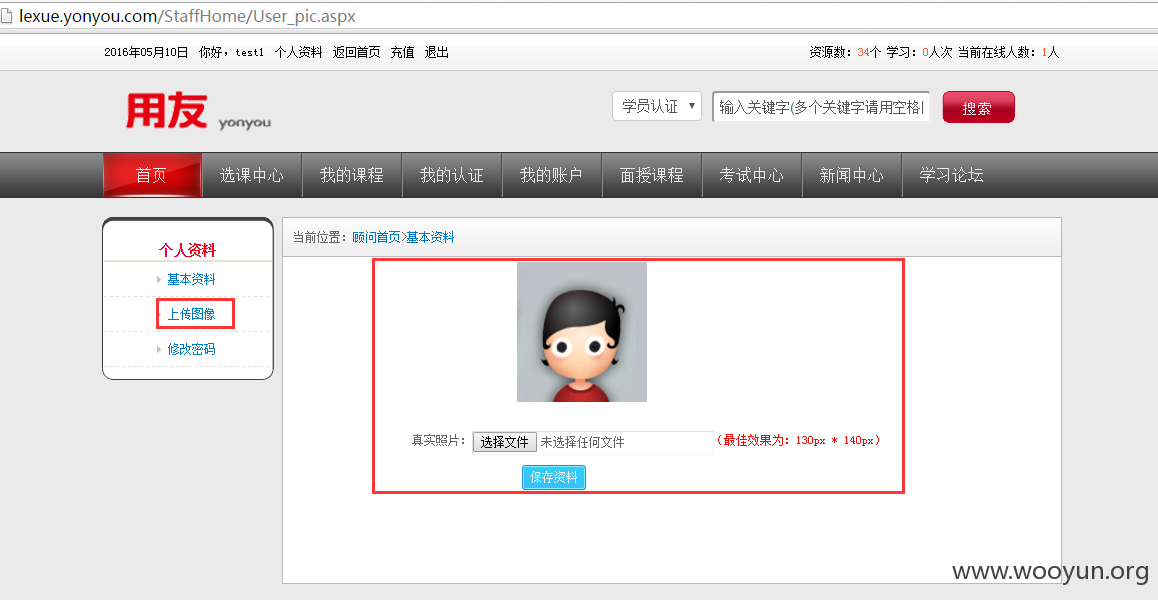
经过测试后发现,上传正常的菜刀马会出现错误报错,无法正常解析aspx。
上传后,通过抓包可得到完整上传路径:
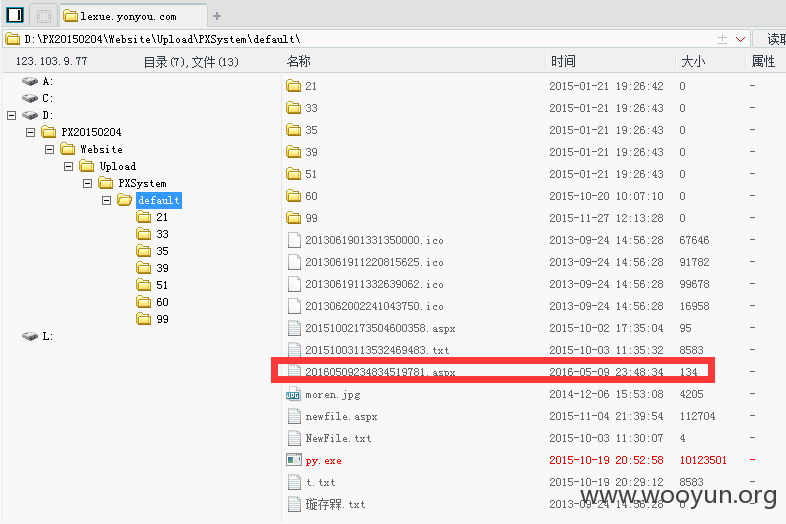
发现该服务器与内网相通:
4.发现入侵痕迹:
同目录下发现文件:20151002173504600358.aspx
可确定入侵时间点为:去年10月2号。
发现提权神器:
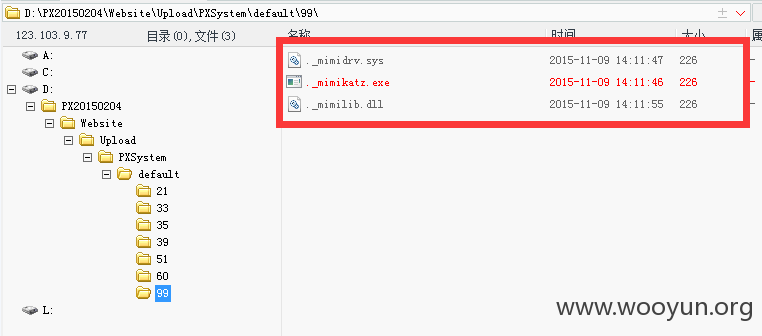
通过查找目录,发现
D:\PX20150204\Website\Upload\Log\tunnel.ashx
根据时间点分析:该文件创建于去年10月27日,可能该入侵者,上传文件并隐藏于log目录下,进行内网反弹,可深入进行内网渗透。
由于未得到厂商允许,未进行深入渗透!