http://123.127.110.171:8001/sireports/login.do?method=indexpage
广电总局统计分析系统
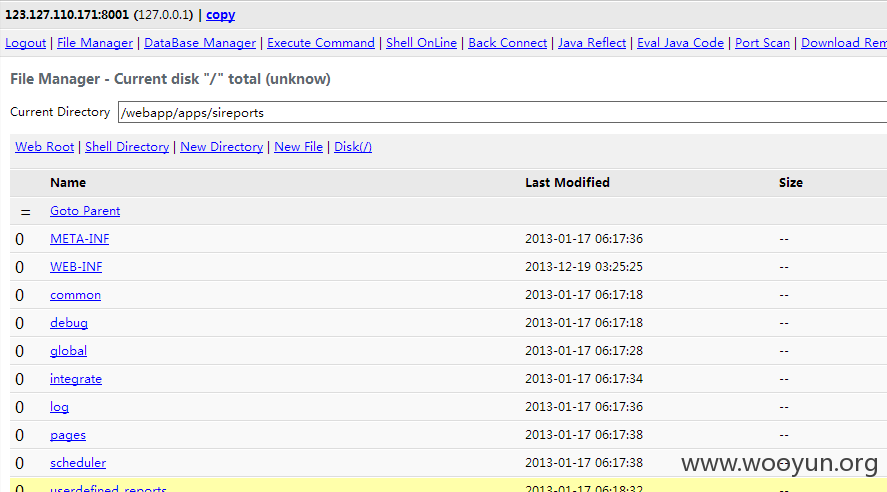
存在Java反序列化漏洞,直接getshell(shell文件测试完毕已经删除)
三个内网ip段,内网应用应该挺多的
内网中的部分应用地址
找到一个网站,很头疼的是没有找到配置文件,或者其他更多端口对应的web应用,这时候就需要脑洞开一下了
配置文件可以从root文件夹下的.bash_history文件中寻找,里面一般都存在管理员进行编辑文件的路径什么的,很可能有意外收获
找到了一个后台登录
http://123.127.110.171:8001/sireports/login.do?method=login
密码全是111111
后台没有什么重要内容,因为不是管理员权限,admin密码没有解密成功
不过还是能影响巨大内网中的安全的





