#1 github泄露:
用户名:root
密码:2Ls56VwEK2wUuYDV
IP地址:115.29.228.53 端口:4453
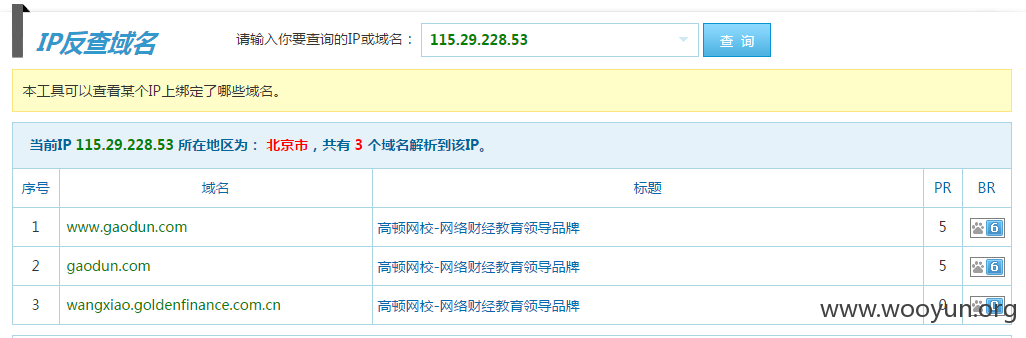
#2 IP反查
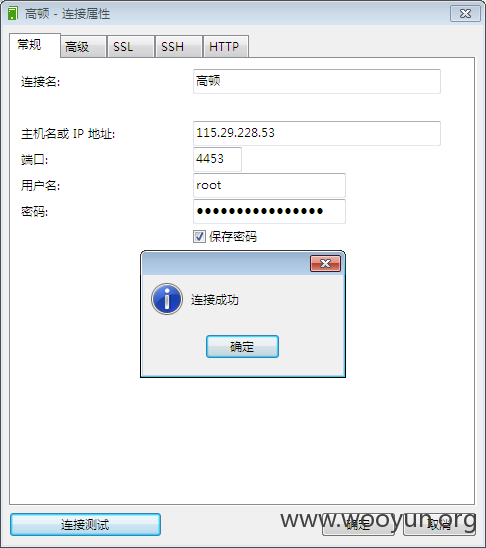
#3 连接成功
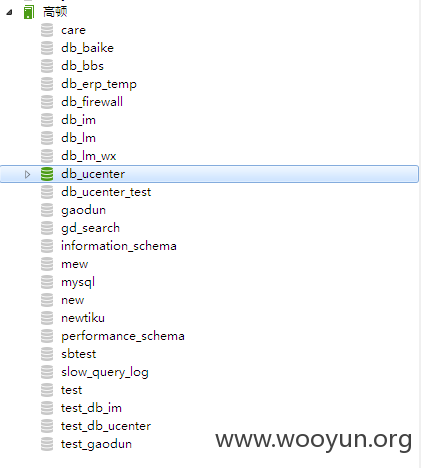
#4 28个库
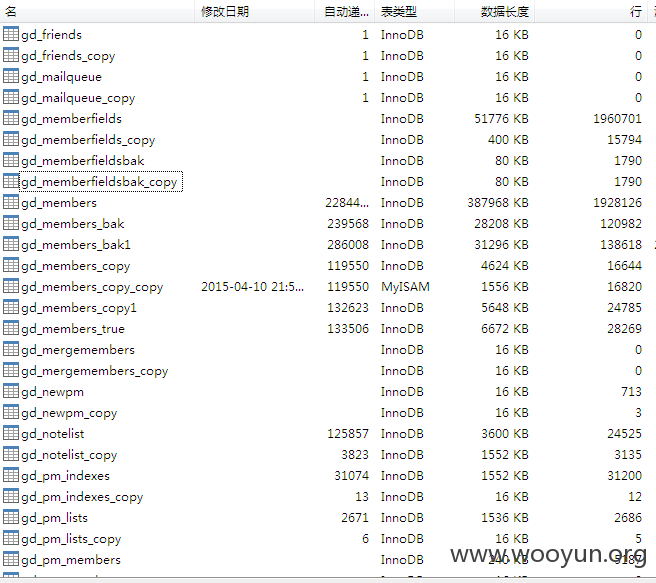
#5 192万用户
#6 root权限不再深入
#1 github泄露:
用户名:root
密码:2Ls56VwEK2wUuYDV
IP地址:115.29.228.53 端口:4453
#2 IP反查

#3 连接成功

#4 28个库

#5 192万用户

select count(*) from `gd_members`
1999559
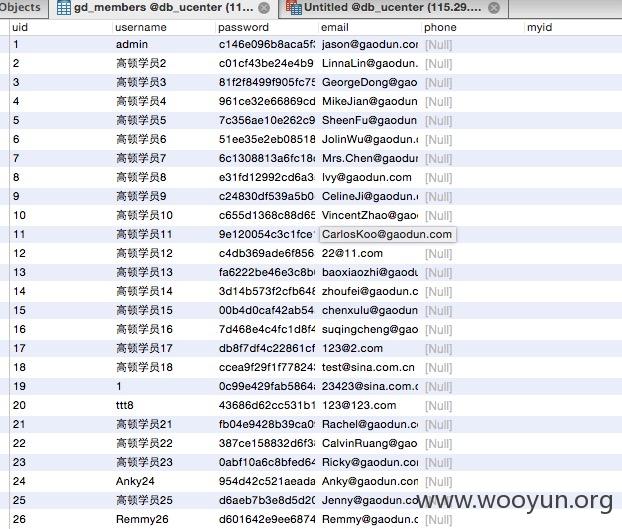
#6 root权限不再深入







