首先,看到 WooYun: TCL某网络分销平台弱口令致海量订单泄露,包括用户姓名、身份证、电话、家庭住址等敏感信息 这个洞,随便看了看,觉的应该有戏.于是.....
先从IP着手,120.132.154.5/120.132.154.17 恩?原来是个电子商务网络分销云平台,各大企业把二级域名指向了这个IP,IP对应的还有个etwowin.com.
启动猪猪侠的神器,开始扫描,一天以后......etwowin.com域名下的二级域名就出来了,都是些企业名命名的二级域名,
太多了,就不一一列举了.
接下来,发现http://120.132.154.5:8080/web/SubmitLogin.do 存在POST注入.参数value(userName)
用SQLMAP一跑,数据就出来了
数据库名都是企业名的缩写
让我们来看看有多少表和数据量
800多个表.........
各大企业的平台数据一览无遗,还没完,我们不能到这里就打住了,继续挖掘
既然是云,那么可能C段还有点东西.
在http://120.132.154.7:88/上发现同样的系统,于是,依葫芦画瓢,在SQLMAP上直接把命令里的IP换成这个..结果又出来了
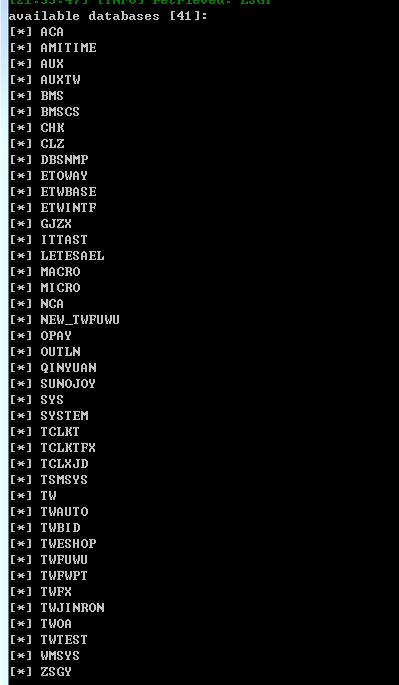
数据库的数量少了点,只有41个.企业名有些不一样.



