由于上次的SVN泄露 然后翻文件的时候进行了进一步的检测。
http://wooyun.org/bugs/wooyun-2015-096890
当我直接用IP访问的时候发现进入了另个WEB目录下 试了试同样存在SVN的泄露问题
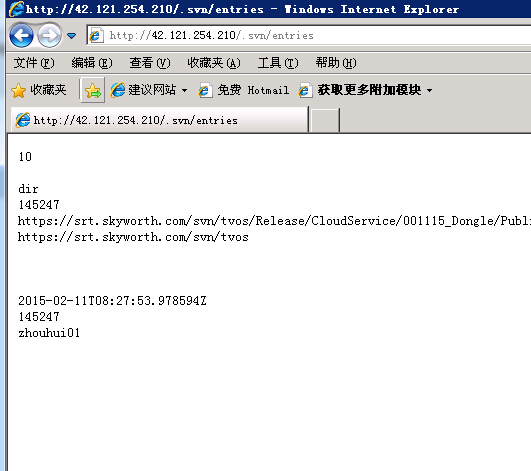
整站下载 翻了翻源码发现了FTP账号。
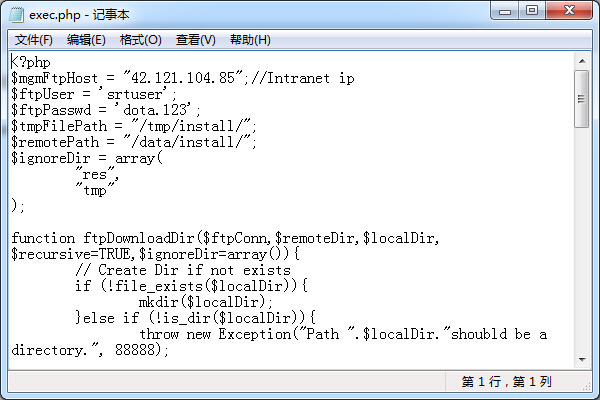
果断连接FTP 扔个SHELL上去 但是发现貌似服务器上装了安全防护 访问SHELL就被拉入黑名单
然后传了个加密的就搞定了
然后找到了个这个文件
这是外网IP对应内网IP的节奏?
然后试了几个 一样存在SVN泄露,这是作死的节奏。
请自行删除SHELL 在APK 和RS目录里
由于上次的SVN泄露 然后翻文件的时候进行了进一步的检测。
http://wooyun.org/bugs/wooyun-2015-096890
当我直接用IP访问的时候发现进入了另个WEB目录下 试了试同样存在SVN的泄露问题

整站下载 翻了翻源码发现了FTP账号。

果断连接FTP 扔个SHELL上去 但是发现貌似服务器上装了安全防护 访问SHELL就被拉入黑名单
然后传了个加密的就搞定了
然后找到了个这个文件
这是外网IP对应内网IP的节奏?
然后试了几个 一样存在SVN泄露,这是作死的节奏。
请自行删除SHELL 在APK 和RS目录里




