rt.
中国科学技术信息研究所(简称中信所)是在周恩来总理、聂荣臻元帅等党和国家领导人的指示和关怀下,于1956年10月成立的,是科技部直属的国家级公益类科技信息研究机构。定位于“为科技部等政府部门提供决策支持,为科技创新主体(企业、高等院校、科研院所和科研人员)提供全方位的信息服务;成为全国科技信息领域的共享管理与服务中心、学术中心、人才培养中心和网络技术研究推广中心,成为国家科技创新体系的重要支撑,并在全国科技信息系统中发挥指导和示范作用”。
中信所首页:http://**.**.**.**
0x01.先从中信所首页进入该机构下属的科技情报与服务研究平台—中国科技情报网
http://**.**.**.**/
根目录下有个login.aspx:
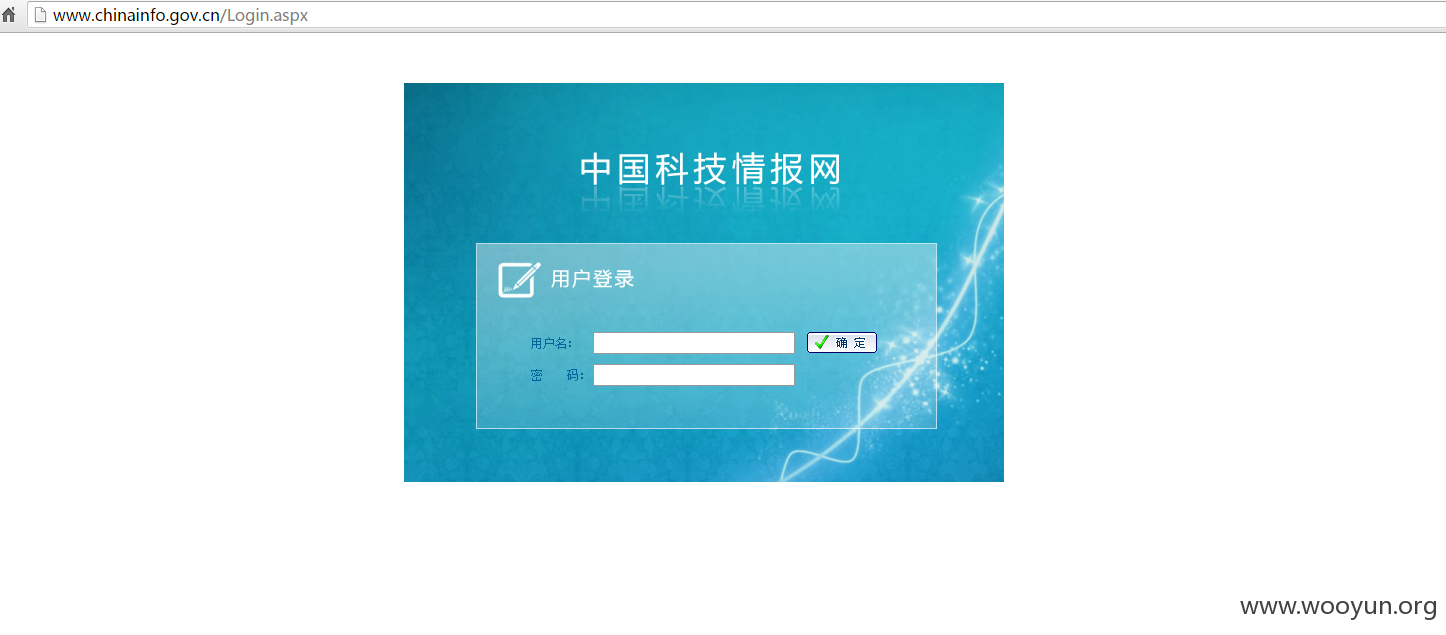
此处的认证存在SQL注入:
注入类型和服务器配置:
数据库共16个,且权限为sa:
在当前库共有216张表,可看到六千多用户资料:
管理员邮箱:
其他库没去看。
0x02.从中信所首页进入全国科技查新网
http://chaxin.**.**.**.**/
根目录下也有个login.aspx:
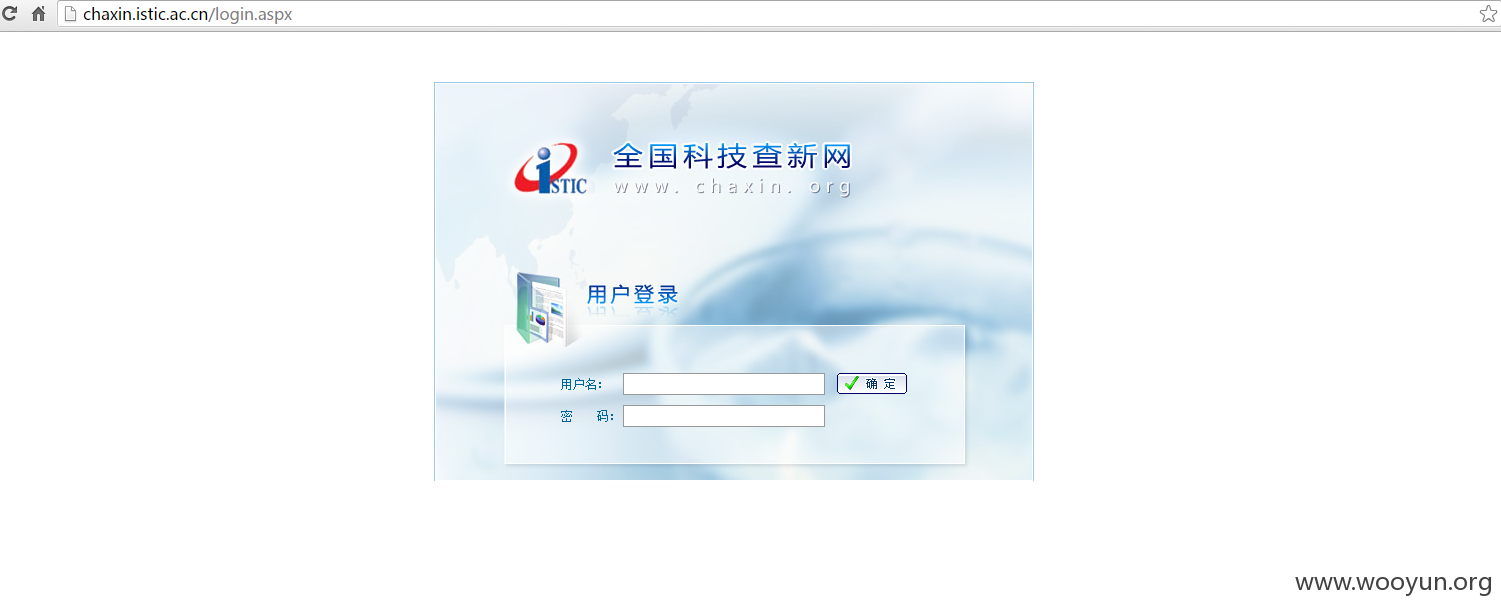
依然是POST类型的SQL注入:
其中的name参数和password参数均可注入,拿name参数来说:
使用union共跑出36个库,并且也是sa权限:
数据太多,就再不往下进行了,两个平台愣是没找着后台账号密码在哪。
可能作为研究机构的话,这里面包含有很多项目之类的敏感信息,请贵所给予重视。
存在漏洞的地方可能不止这两处,看情况应该用的是同样的查询方式,虽然有waf,我用了tamper绕过了。





