擦 一步留神 被人提交了一个,这个应该不重复吧?
我直接给你打包
===============================================
注入点1:
在首页内容搜索处有post注入
post包
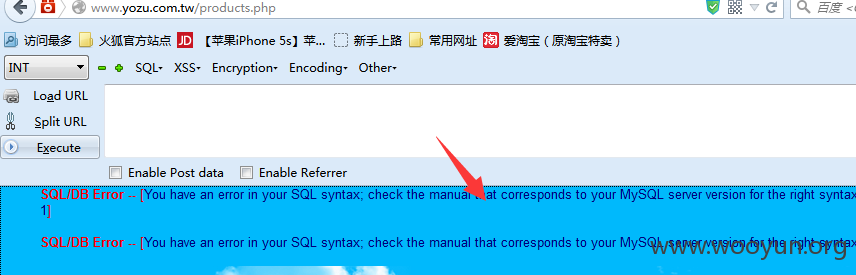
注入点2:
cid存在注入
数据:
注入点3:
pid存在注入
注入点4:
http://**.**.**.**/modules_page.php?class=1&num=3
class和num都存在注入
系统管理员:
去cmd5解密了
yozu
aol0xh08
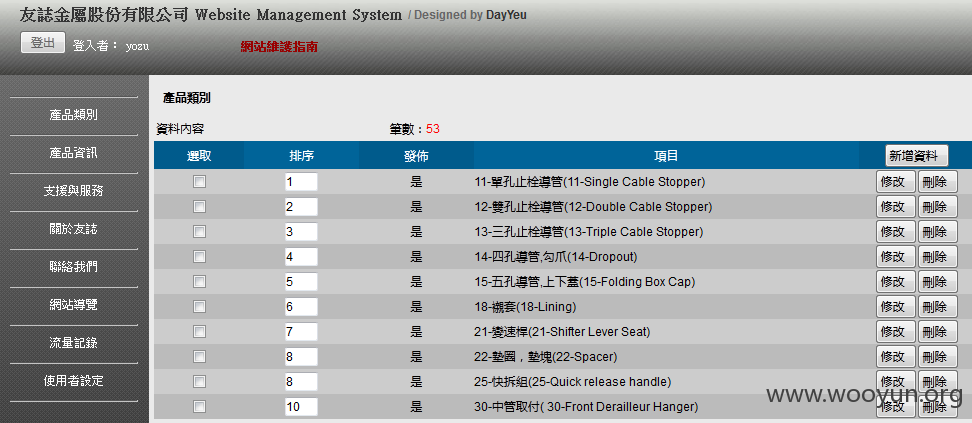
后台登入地址:
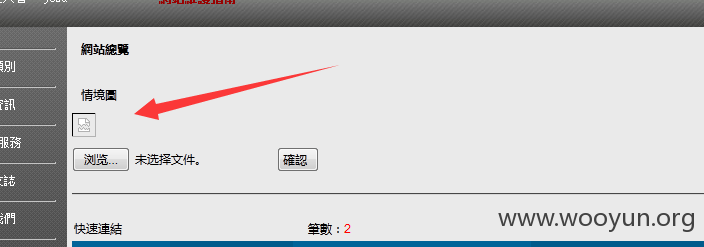
背景上传getshell
一句话:http://**.**.**.**/images/123dorr.php xiao
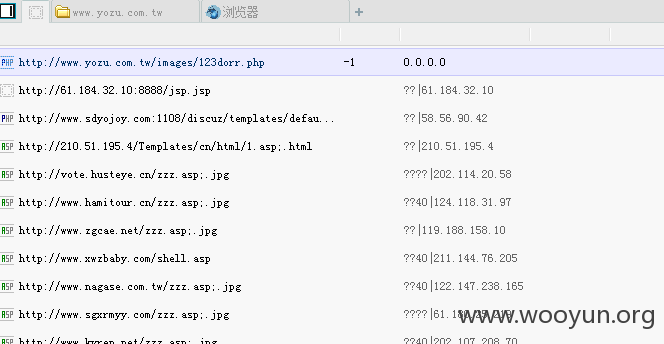
可影响内网:






