鄂汇金融服务(武汉)有限公司(ehjinrong.com)成立于2013年,注册资金2000万,地址位于武汉江汉区淮海路CBD泛海国际SOHO城"华中互联网金融产业基地"。是集小额贷款行业投资、小微贷款咨询服务与交易促成、信用风险评估及管理于一体的综合性金融服务公司,致力于P2P网贷运营服务。(官网介绍)
1、注入点:
2、所有数据库:
3、当前库是ehui_online,看一下这个库的表及数据量:
4、看一下用户表eh_user中的字段:
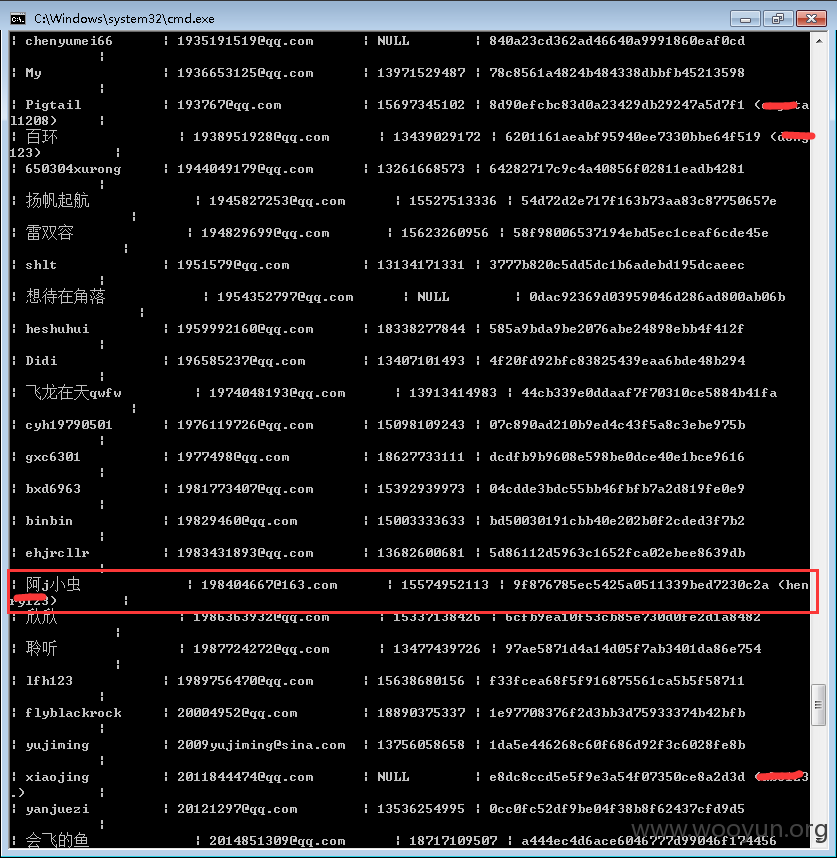
5、字段username,email,mobile,password的数据(部分):
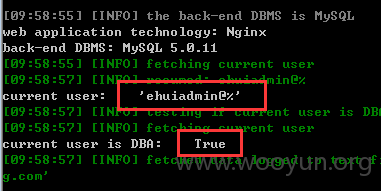
6、数据库权限:
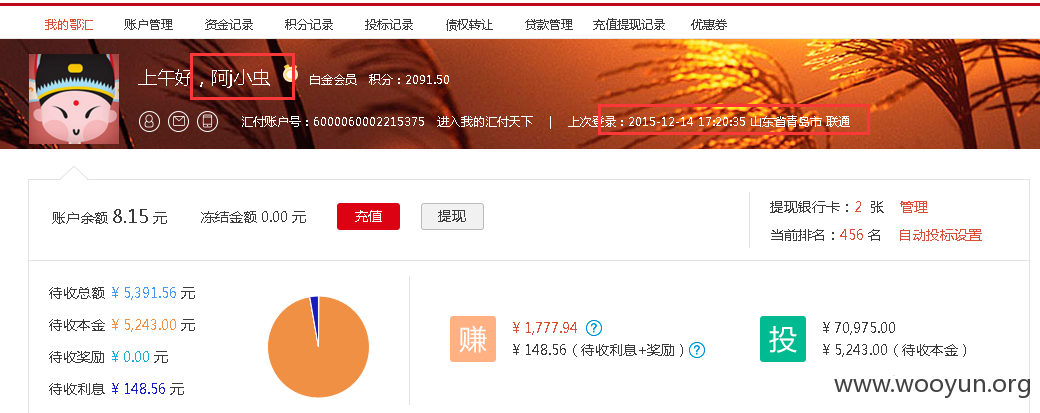
7、登录一下用户信息看一下:
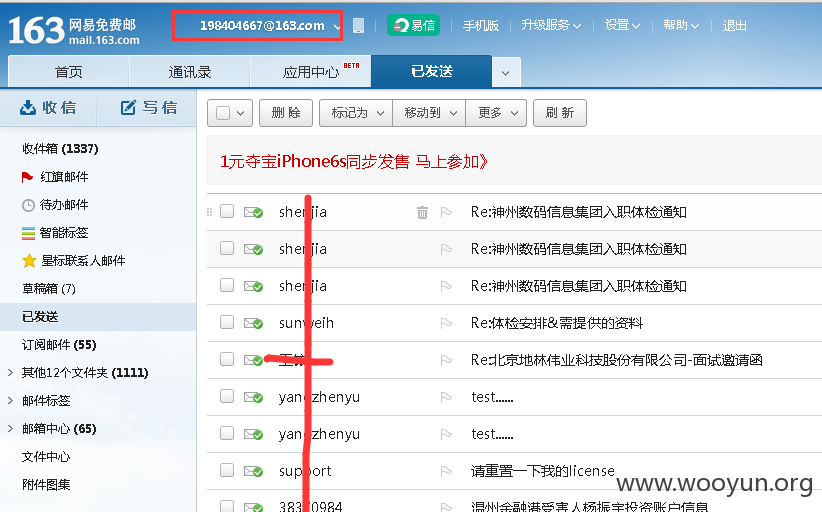
8、这个用户的163邮箱: