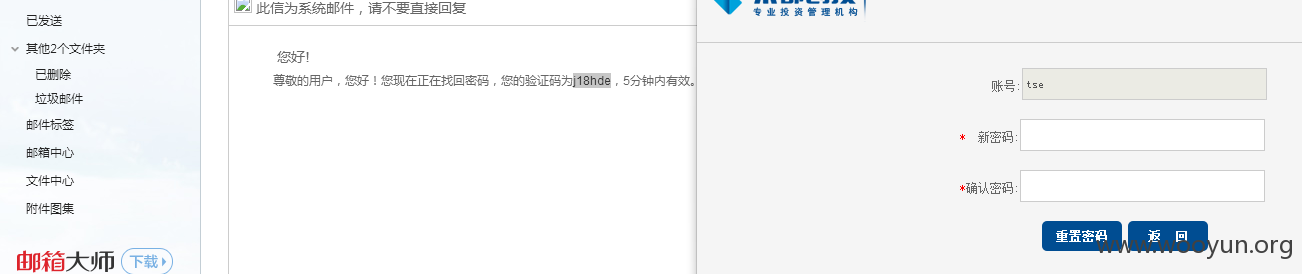
你贷款我知道?0x01:getshell 0x02:信息泄露(包含身份证等)0x03:默认配置(包括病毒系统)0x04:数据库泄露(所有数据库)0x05:密码重置(注册过的所有用户)
所属厂商:上海集都创投
网站:集都创投风险控制系统
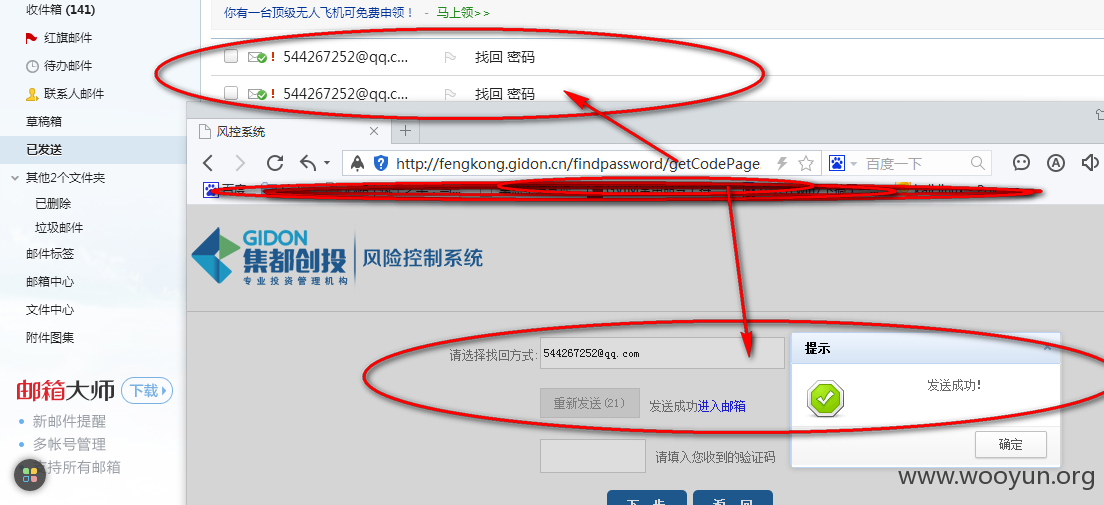
http://fengkong.gidon.cn/findpassword/getCodePage.action
0x01:getshell
站点存在Struts2命令执行导致getwebshell
目录:D:\apache-tomcat-7.0.59-risk\webapps\RiskControl\
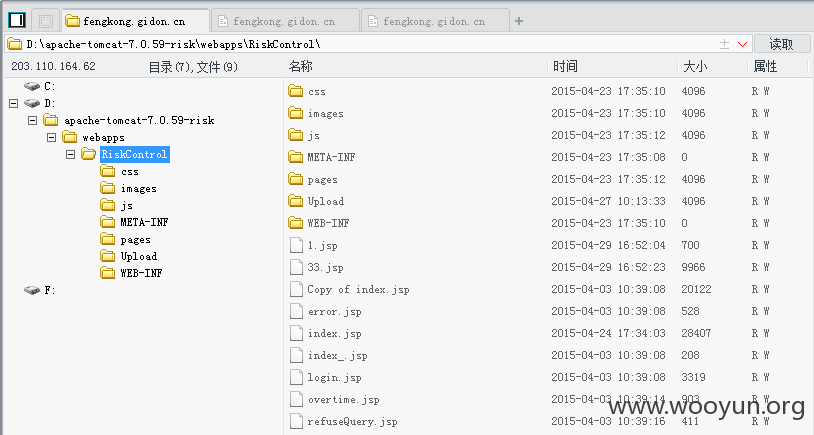
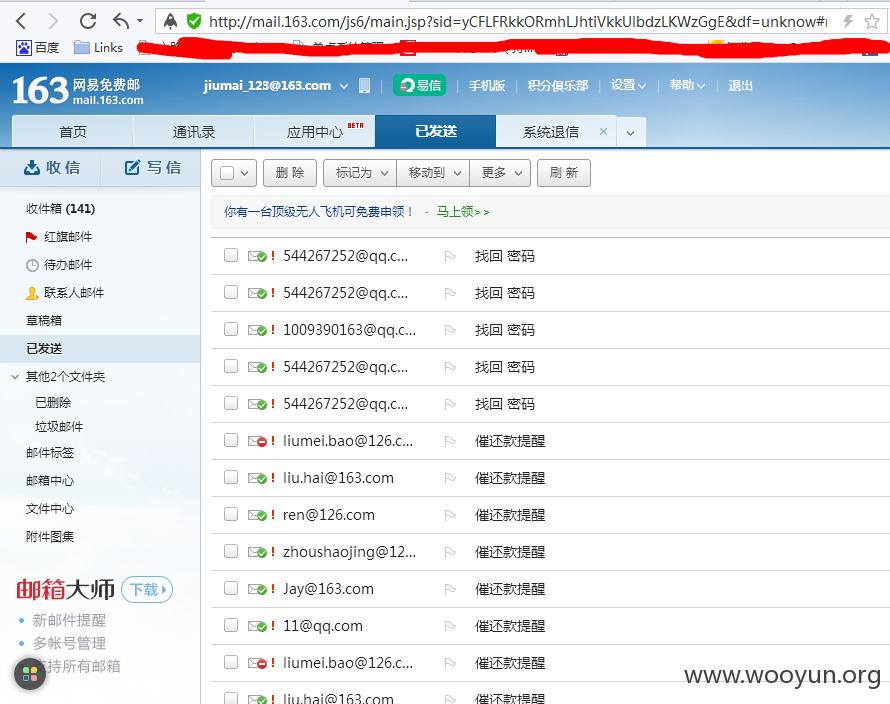
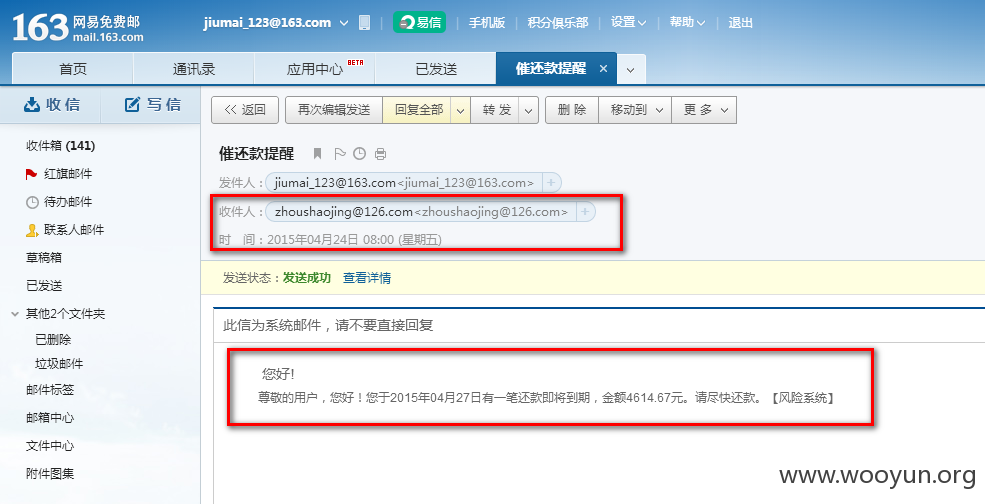
0x02:信息泄露
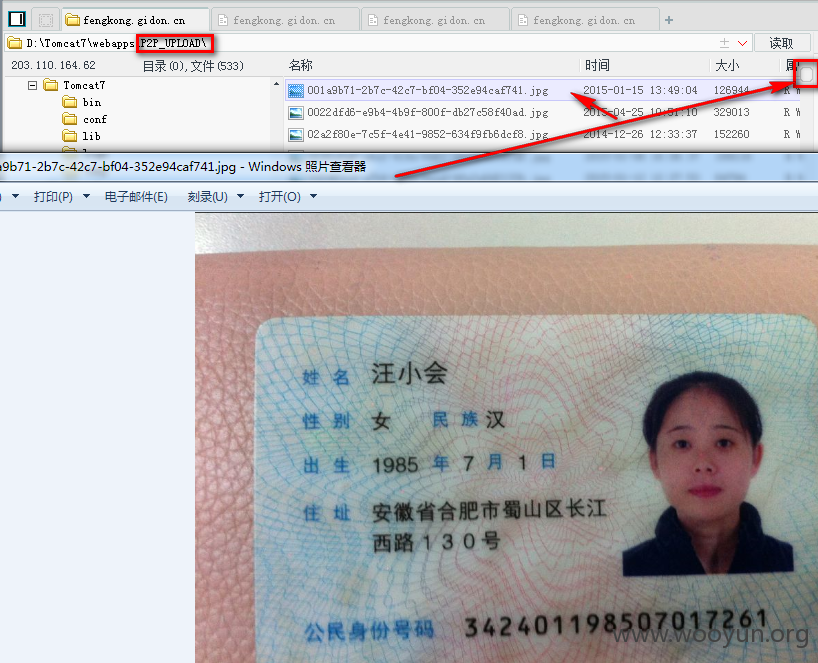
0x03:默认配置
第二处:
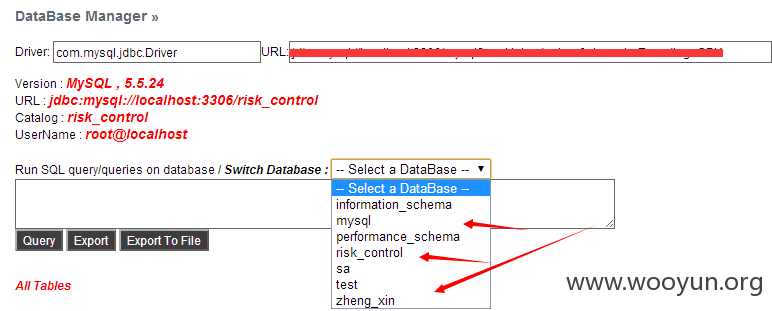
0x04:数据库一大堆