rt.
漏洞存在于大通旅游后台管理系统:
http://datong.china51766.com
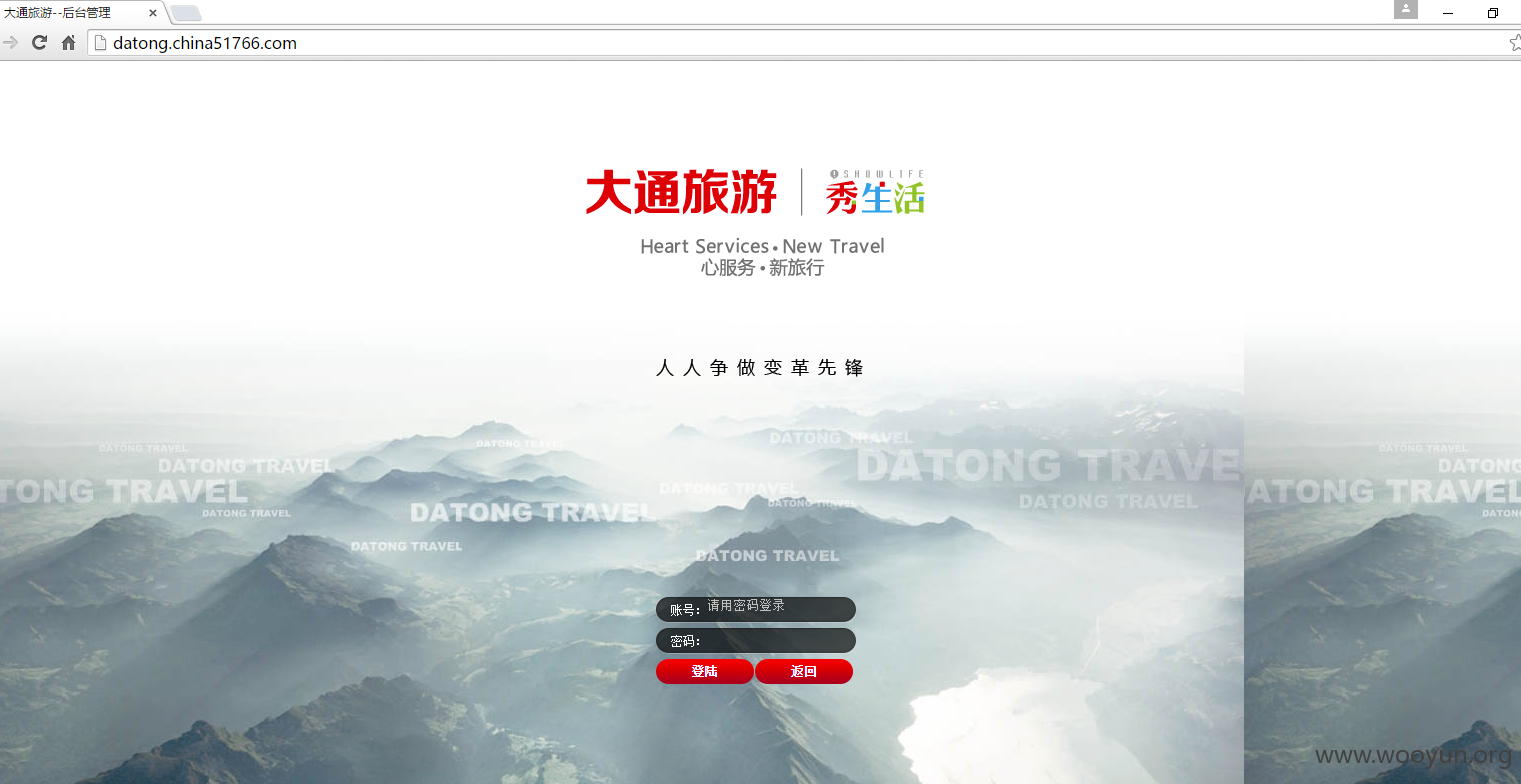
此处的登录验证处存在注入:
参数text_Name、text_Pwd均可注入。
注入类型及配置:
数据库:
数据库用户:
当前数据库和用户:
DBA权限:
NEWTRAVEL中共266张表:
位于NEWTRAVEL中的CLIENT表和CLIENTACCOUNT表:
CLIENT中的部分字段:
以及该数据库中的USERS表(该表为员工信息表)和TOUR_GUIDE(导游信息)表:
点到为止,不在深入。
望贵公司尽快整改,这么多数据还是重视一下。



